World's Top CNAPP that Secures from Hacker Recon to Cloud to Your Code
CloudDefense.AI is an industry-leading multi-layered Cloud Native Application Protection Platform (CNAPP) that safeguards your cloud infrastructure and cloud-native apps with unrivaled expertise, precision, and confidence.
As Seen On


From Code-to-Cloud, Stay Secured with one of the Industries Best CNAPP
Elevate your Code-to-Cloud experience with the excellence of our industry-leading CNAPP, delivering unmatched security to ensure your business’s data integrity and confidentiality.

Why we are the Best CNAPP
Your Safety, Our Priority! From advanced threat detection to real-time monitoring and rapid incident response, our platform delivers complete protection, providing you with the confidence to navigate today’s complex security challenges.
Powerful Agentless CNAPP
A Unified Solution for Your Cloud and Applications
Effortlessly Remediate in Minutes
Robust Shift Left Security
Proactively Detect and Analyze Real-Time Threats
Boosted Collaboration Across Teams
Powerful Agentless CNAPP

Powerful Agentless CNAPP
Seamlessly connecting with your Cloud and Kubernetes landscape, our revolutionary CNAPP ensures lightning-fast infrastructure scans and delivers comprehensive vulnerability reports in mere minutes. No extra resources, no maintenance hassle.A Unified Solution for Your Cloud and Applications

A Unified Solution for Your Cloud and Applications
Imagine having all your cloud protection needs in a single, easy-to-use platform. From tackling vulnerabilities to ensuring multi-cloud compliance, safeguarding workloads, and securing containers – we’ve got it all covered.Effortlessly Remediate in Minutes

Effortlessly Remediate in Minutes
Say goodbye to time-consuming fixes! Address security concerns effortlessly with our prebuilt auto-remediations, guided steps, and instructive videos. Gain comprehensive insights through in-depth root cause analysis and dynamic guardrails, empowering your team to achieve unparalleled remediation speed.Robust Shift Left Security
Robust Shift Left Security
With over 140 MM+ code commits processed, we offer unparalleled Shift Left Security for IaC templates and container images – all within a unified platform. Detect vulnerabilities and rectify misconfigurations at the earliest stages, ensuring a development journey that’s not only efficient but also highly secure.
Proactively Detect and Analyze Real-Time Threats

Proactively Detect and Analyze Real-Time Threats
Leverage the power of advanced AI to swiftly pinpoint IoBs (Indicators of Behavior) with unparalleled speed and precision. Transition from post-incident IoCs (Indicators of compromise) to proactively identified IoBs, reshaping the landscape of threat discovery and investigation.Boosted Collaboration Across Teams

Boosted Collaboration Across Teams
Empower your security, Devs, and DevOps teams to seamlessly unite for rapid and secure cloud-native app development. With CloudDefenseAI, amplify teamwork via Slack, Jira, Webhooks, Email, and beyond. Elevate your workflow with tailored integrations, fostering collaboration and accelerating application deployment while ensuring top-notch security at every step.Cloud-Native Application Protection Platform
CSPM
CIEM
CWP
Vulnerability Management
Compliance
EASM
SAST
DAST
API Security
Container Security
CSPM
Cloud Security Posture Management (CSPM)
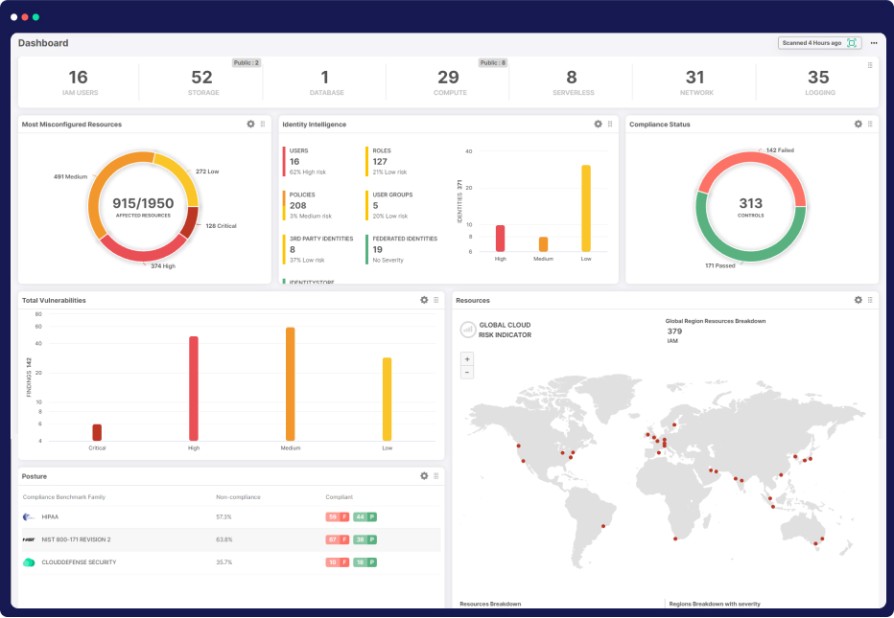
Imagine having a bird’s-eye view of your entire cloud landscape, where every deployed resource is at your fingertips, all in one place. With over 700 powerful policies at your disposal, you’re not just setting up guardrails; you’re forging an ironclad fortress of protection.
CIEM
Cloud Infrastructure Entitlement Management (CIEM)
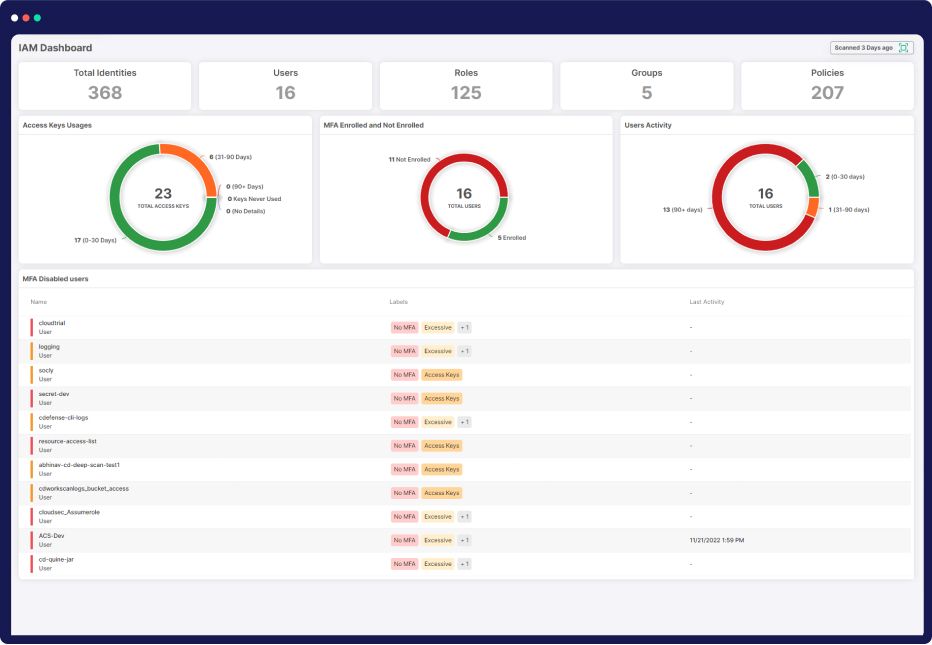
Revolutionize your cloud security with our advanced Cloud Infrastructure Entitlement Management (CIEM) capabilities. Safeguard your cloud infrastructure by swiftly identifying identity misconfigurations, guaranteeing least privilege compliance, and meticulously tracking identity hygiene metrics. Elevate your cloud environment’s safety with continuous audits of identities, policies, roles, and entitlements.
CWP
Cloud Workload Protection (CWP)
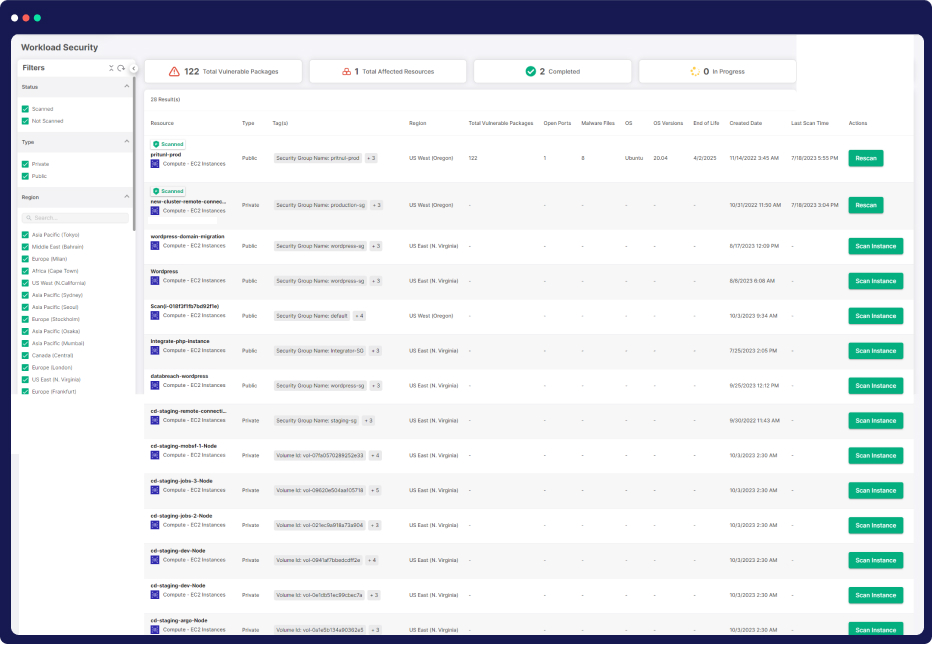
Modern applications thrive in diverse landscapes—VMs, containers, Kubernetes®, and more. Securing each of these layers presents a significant challenge. But, with CloudDefense.AI, you gain the ability to effortlessly identify vulnerabilities, protect sensitive data, eliminate malware, and effectively manage misconfigurations. Strengthen your security posture with continuous real-time scans and intuitive visualizations that provide valuable insights
Vulnerability Management
Cloud Vulnerability Management
Gain a comprehensive overview of your cloud setup and harness data from 20+ vulnerability sources for meticulous threat assessment. Unlike conventional solutions, we contextualize cloud assets, connections, and risks to drive targeted remediation. Experience swift response capabilities, swiftly mitigating high-risk vulnerabilities such as Log4Shell.
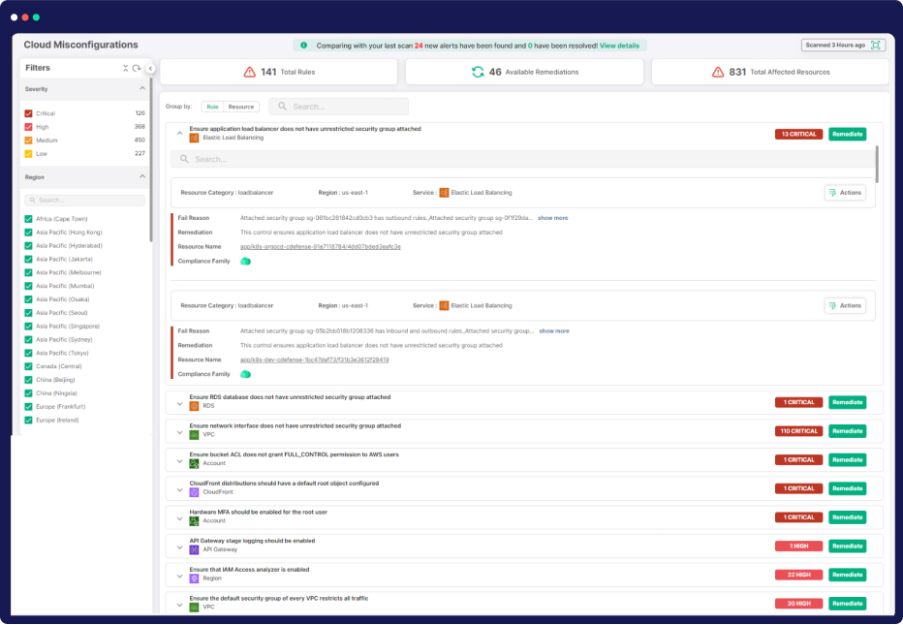
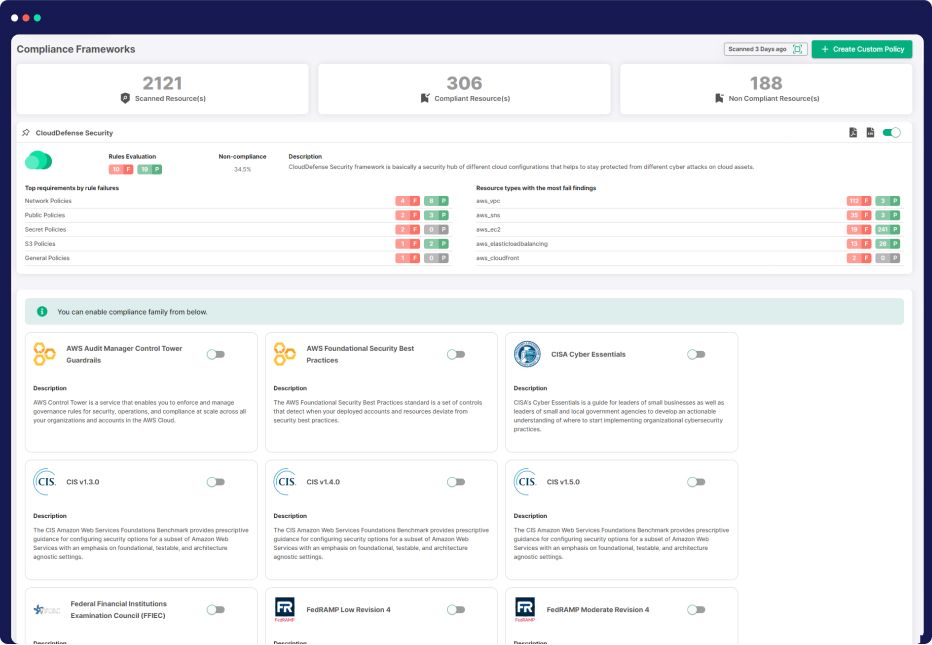
Compliance
Holistic Multi-Cloud Compliance
Ensure seamless regulatory compliance across 65+ frameworks, including CIS benchmarks, and tailor-made checks on diverse cloud platforms—all through a unified, agentless cloud security marvel. We’ve got your entire cloud setup covered, instantly flagging the big stuff and helping your security pros strategically sort out compliance gaps.
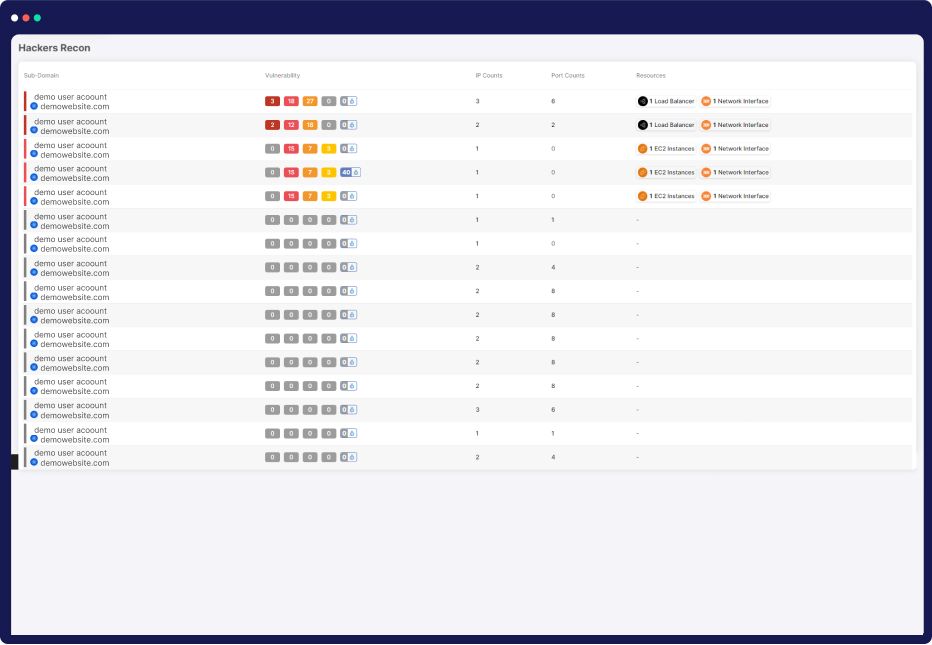
EASM
Hacker ReconTM (EASM)
Elevate your security proactively—anticipate, strategize, and triumph. Our breakthrough HackerView empowers you to get deep insights into attackers’ tactics, anticipate their moves, and fortify your cloud against critical vulnerabilities, thereby staying steps ahead of breaches.
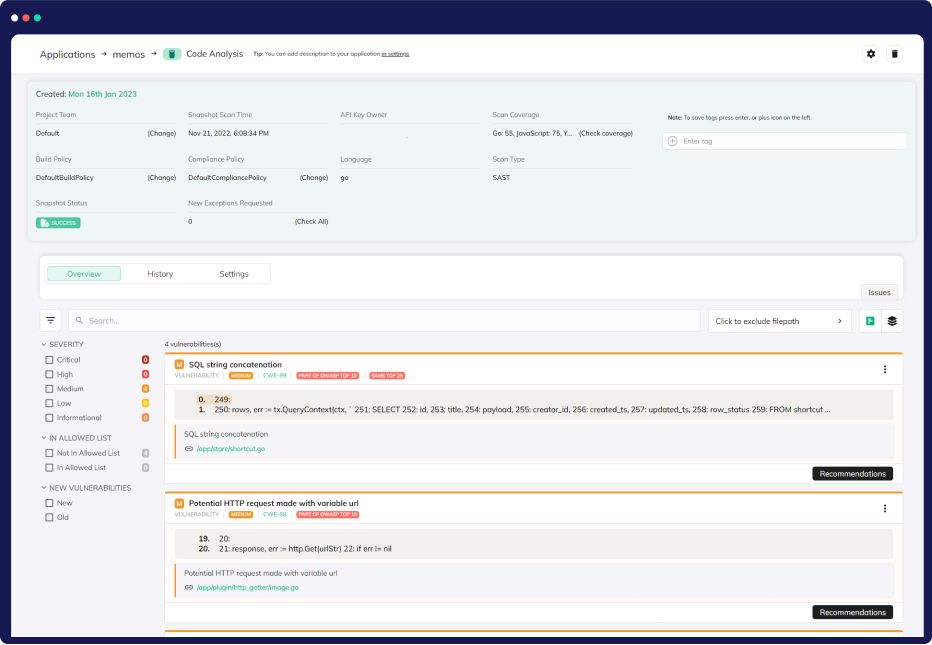
SAST
Static application security testing (SAST)
Elevate your code security with a cutting-edge feature: SAST. Dive into meticulous source code analysis, uncovering vulnerabilities and rule breaches. Our SAST doesn’t just stop there – it cleverly compares security issues between source and target branches, fortifying your codebase.
DAST
Dynamic Application Security Testing (DAST)
Discover Software Vulnerabilities Ahead of Threat Actors – Experience the power of DAST, a cutting-edge black-box application testing technique that exposes vulnerabilities while your applications are live. With DAST, you can identify vulnerabilities without the hassle of accessing source codes.
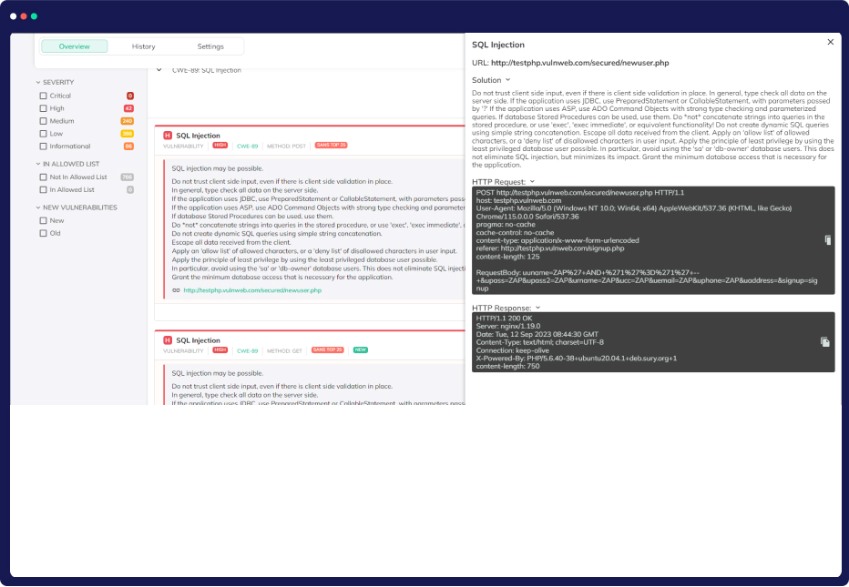
API Security
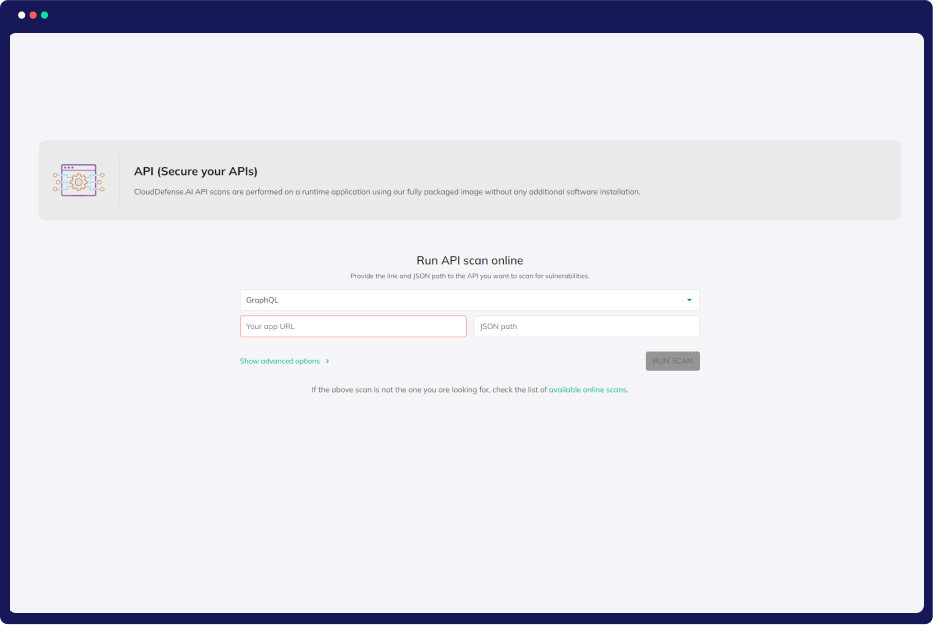
API Security
Quickly identify, prioritize, and mitigate API misconfigurations and vulnerabilities across multi-cloud landscapes. Our cutting-edge technology scans runtime applications seamlessly, leveraging fully packaged images—no need to install extra software.
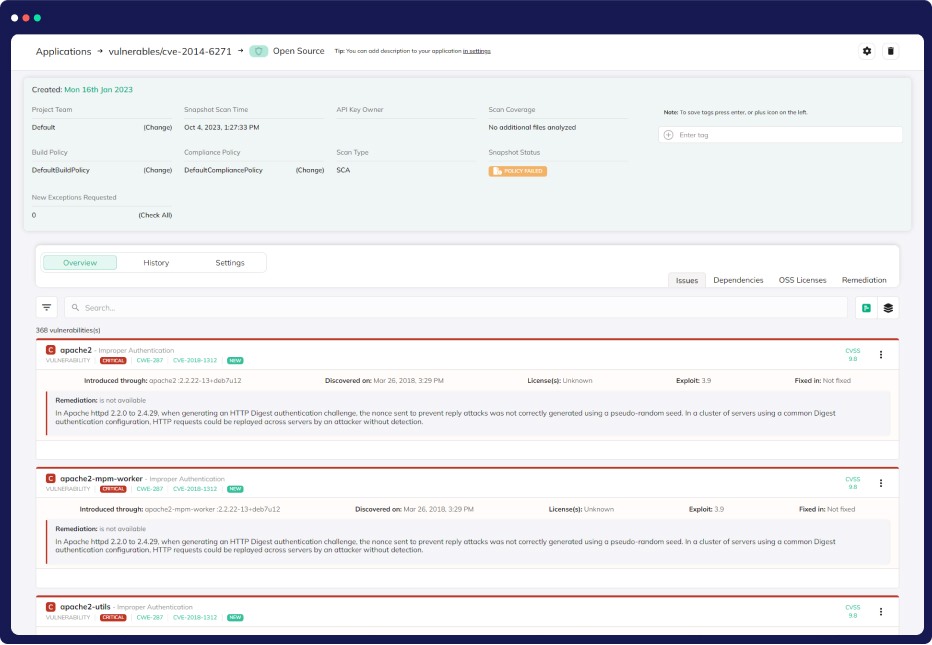
Container Security
Container Vulnerability Management (CVM)
Boost your container security with ease! Our Advanced Container Scanning feature ensures robust protection by swiftly detecting vulnerabilities and malware in your Docker images. No extra tools needed—just one command initiates thorough scans.
Trusted by the most innovative companies in the world
Ready to see us in action? Schedule a time
to speak with our team!
Ready to see us in action? Schedule a time to speak with our team!