Application security in today’s world is constantly under threat from cyber attackers exploiting every possible vulnerability in the application source code. Organizations require advanced and AI security testing methodologies within the SDLC to identify and mitigate vulnerabilities, including zero-day attacks.
Among all, AI SAST and AI DAST serve as essential tools for all development and security teams. AI SAST examines the codebase for vulnerabilities while AI DAST simulates an attack on the application to uncover vulnerabilities that might occur after deployment. Since the SAST vs DAST comparison has been a prominent debate, professionals often ask if AI SAST and AI DAST are friends or foes.
Well, both AI SAST and AI DAST are allies that form the foundation of modern applications. This article will provide an overview of AI SAST vs AI DAST comparison and how organizations can use them to build a comprehensive testing strategy.
Understanding AI SAST
AI SAST is an AI-powered static application security testing tool that accurately identifies security vulnerabilities by leveraging AI and ML. It serves as an improvement of traditional SAST by understanding the code context and going beyond standard rule-based assessment approaches.
It integrates directly into the CI/CD pipeline and uncovers both known and unknown vulnerabilities in the source code, binary code, or bytecode of the application. AI SAST tools like QINA Clarity AI are always learning from secure codebases, live data streams, libraries, and datasets, making them more capable against evolving threats. AI SAST is making application development safer and robust through:
- Predictive Analysis: AI SAST utilizes predictive models that are always evolving, enabling the tool to catch vulnerabilities with high accuracy.
- Smart Prioritization: Thanks to intelligent prioritisation like QINA Clarity AI’s 4-stage security finding analysis that filters out all false positives and highlights only the severe threats.
- Deeper Analysis: AI-powered SAST tools understand the logic behind the code and analyse the data flow. It enables the tool to identify nuanced and embedded vulnerabilities that might severely impact the application.
AI SAST, by integrating early in the development environment, enables developers to identify threats in the code before they are committed. It helps in streamlining the remediation process and swift up the development process.
How Does AI SAST Work?
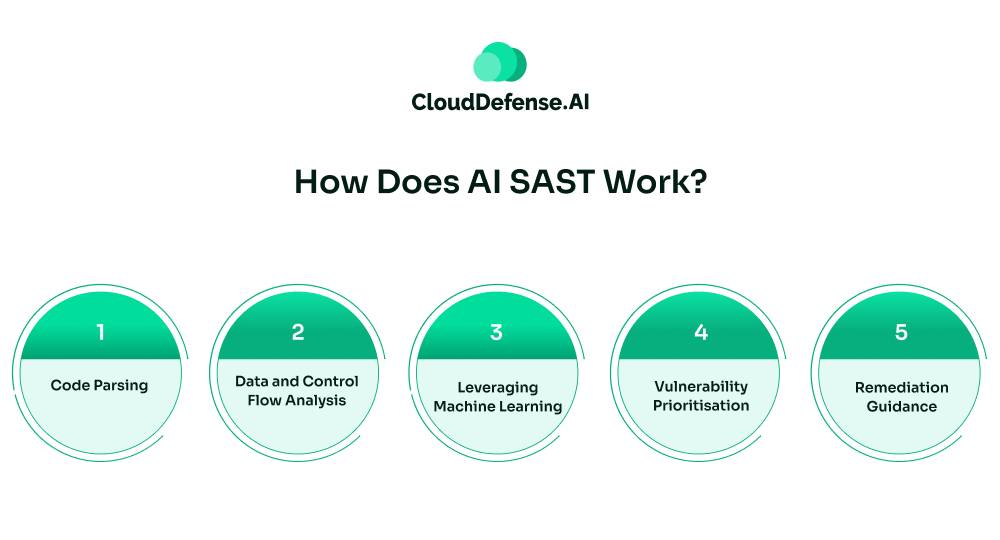
The core working mechanism of AI SAST is based on its continuous learning ability from various sources and utilizing it to detect complex vulnerabilities. Typically, in a dynamic vs static analysis comparison,an AI SAST works by:
- Code Parsing: AI SAST mainly analyzes code by parsing the source of the application. It creates an Abstract Syntax Tree, which provides the logical structure of the code.
- Data and Control Flow Analysis: Besides parsing, AI SAST also performs data and control flow analysis. It helps the mechanism to understand the movement of the data and different execution paths. It is highly useful in identifying vulnerabilities that originate from flawed inputs.
- Leveraging Machine Learning: To identify threats proactively, this mechanism utilizes machine learning models. The models are trained extensively on secure coding practices and vulnerable code. As a result, it is able to understand the context of the code, predict the probability of threats, and identify complex vulnerabilities.
- Vulnerability Prioritisation: AI SAST not only identifies all the vulnerabilities but also prioritises them. It thoroughly understands the context of the code to evaluate whether the code is a real threat or a false alarm. Further, it also analyzes the severity and potential impact, allowing developers to remediate threats accordingly.
- Remediation Guidance: Once a threat is alerted, it also provides remediation guidance to developers directly into the IDE. It provides a step-by-step guide to help developers fix it quickly. Some modern AI SAST also enables developers to automate the fixing process.
Understanding AI DAST
In an AI-based SAST vs DAST comparison, AI DAST takes a different approach, where it utilizes black box testing methodology to uncover vulnerabilities. In this application security testing type methodology, the tool simulates real-world attacks on the application in the test or production environment.
This methodology is highly useful in identifying security threats that might emerge in the runtime. Unlike AI SAST in AI-powered dynamic vs static analysis, AI DAST doesn’t have access to the source code. It mainly targets security threats that might occur from the application’s runtime behavior, API, or endpoints. The integration of artificial intelligence in DAST enhances its capabilities by providing:
- Intelligent Attacks Simulation: AI DAST holds the capability to simulate advanced and context-aware attacks on the application. Based on the latest threat intelligence and the application’s current response, it can dynamically adjust the testing process. This helps the tool to identify threats smartly and efficiently.
- Business Log Flaw Detection: A huge advantage of this application security testing type is its ability to understand the business logic of an application. Based on its understanding, it can identify vulnerabilities that can be exploited by attackers.
- Accurate Runtime Vulnerability Detection: With the AI support, dynamic analysis can uncover varied types of runtime flaws that originate only when the application is running. It can accurately identify vulnerabilities related to server configurations, session management and session management.
AI DAST serves as one of the crucial application security testing types as it helps organizations get the actual perspective of their application security posture. It provides details on the loopholes and how the security guardrails are effective against real-world attacks.
How Does AI DAST Work?
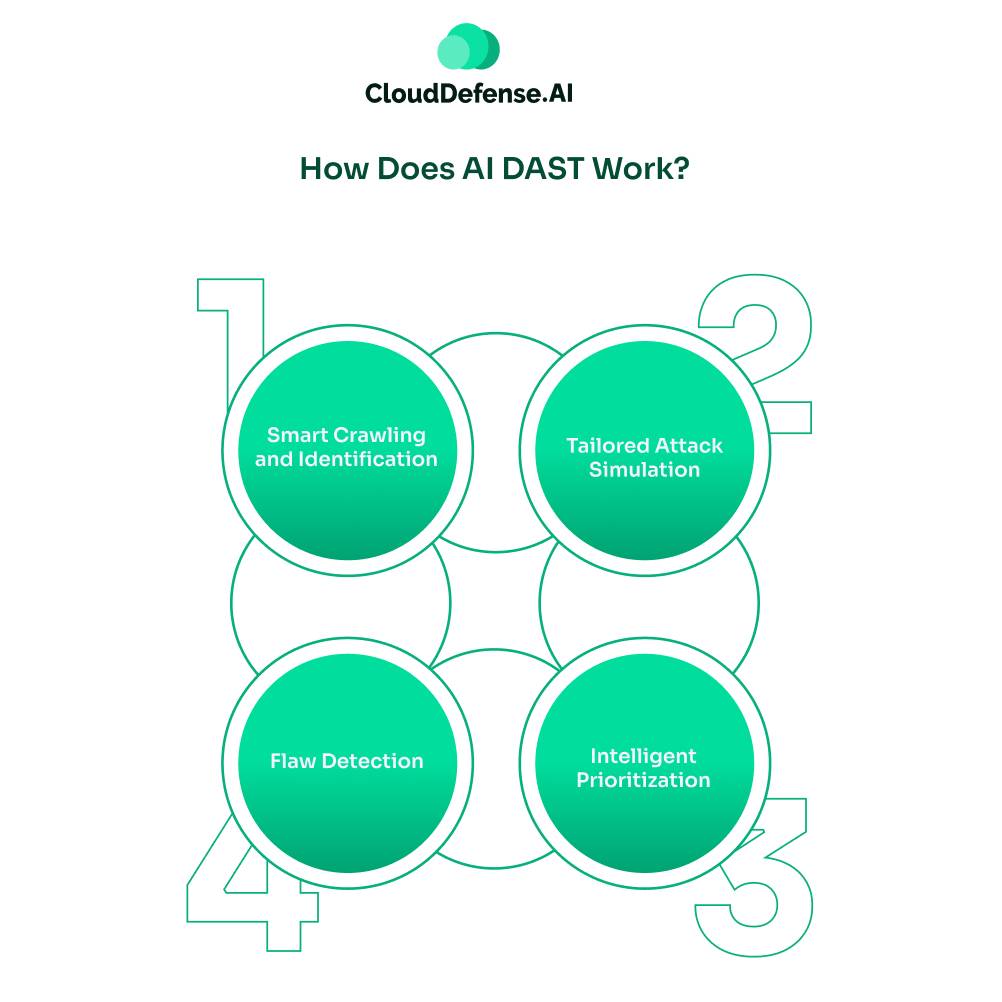
AI DAST is designed to simulate attacks on applications to uncover vulnerabilities. A lot of key steps take place to accomplish the complete process:
- Smart Crawling and Identification: In the beginning, AI DAST first performs crawling to understand the structure of the application, which includes API endpoints. Through crawling, AI DAST learns about the workflow of the application. Besides, it also assesses the traffic and various behaviors of the application to uncover any hidden API endpoints.
- Tailored Attack Simulation: After crawling, AI DAST launches a tailored attack simulation on the application. It analyzes the technology and framework and launches attacks accordingly. Once the tool simulates the attack, with the help of ML, the tool learns from the application’s response. It enables the tool to understand what works and modify its strategy accordingly. Based on the response, it can also simulate a chain of attack, including sophisticated techniques to identify more nuanced flaws.
- Flaw Detection: AI DAST, after understanding the application, creates a baseline for the standard behavior of the application. After the attack has been simulated, when the application deviates from the baseline, it identifies all the vulnerabilities. It not only uncovers known vulnerabilities and business logic flaws but also focuses on flawed behaviour to find zero-day vulnerabilities.
- Intelligent Prioritization: The tools also analyse the context of all the identified vulnerabilities to identify exploitability and impact. It also assesses the severity of the vulnerabilities and intelligently prioritises them.
AI SAST vs AI DAST: Friends or Foes?
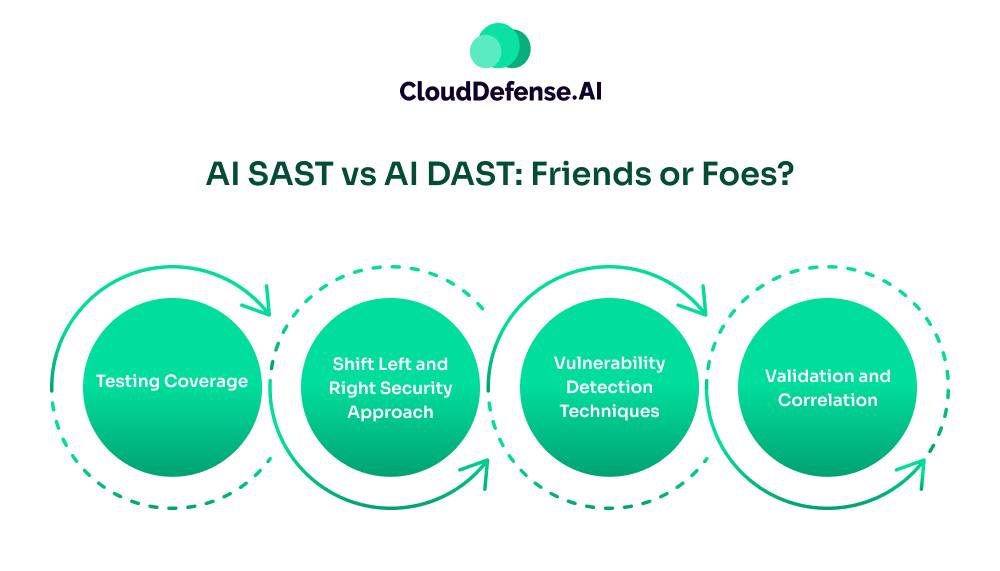
When it comes to AI-based SAST vs DAST comparison, many often think there is a competition between the two due to different methodologies. However, in reality, these two methods are friends, not foes.
These application security testing types serve as a powerful ally that takes different testing approaches to maintain an optimum application security posture:
- Testing Coverage: In AI-based dynamic vs static analysis, the tools might work differently, but they work towards a single goal in securing the application. AI SAST performs deep analysis of the codebase to detect vulnerabilities early in the SDLC. It scans static code that is yet to be committed.
AI DAST, on the other hand, tests the running application by simulating real-world attacks and identifying any security threats. It uses blackbox methodology to identify issues originating from the runtime environment or external dependencies. Together, they provide a comprehensive security coverage of the application. - Shift Left and Right Security Approach: Both AI SAST and DAST help in embedding security gates throughout the DevSecOps. AI SAST integrates early in the IDE, especially in the development stage, to catch vulnerabilities in the code before they are committed. It helps with the shift left approach and ensures safe coding practice.
AI DAST is integrated in the latter part of the dev stage, where it performs the final check. It assesses the complete security posture of the application in a real-world environment before it has been deployed. - Vulnerability Detection Techniques: AI SAST utilizes behavioural analysis, deep code analytics, and predictive assessment to identify vulnerabilities in the codebase. It also makes use of data flow analysis to identify the impact of vulnerabilities.
Whereas the AI DAST utilizes AI and ML-based simulated attacks, and adaptive crawling to uncover vulnerabilities in runtime. It also performs risk-based prioritisation to ensure the actual threat is presented to developers. - Validation and Correlation: AI SAST and AI DAST work together in many instances to find and validate any security findings. All the security findings are fed to AI DAST so that it can validate the presence of the vulnerability in the runtime environment. If an XSS vulnerability is identified by AI SAST, AI DAST can validate it by simulating an attack accordingly to confirm its presence.
Building a Comprehensive Testing Strategy
In AI AI-based SAST vs DAST comparison, the tools aren’t competing against each other. Both tools serve as a complementary methodology that helps in achieving maximum application security posture.
To build a comprehensive application security testing strategy, organizations can implement the following:
- Integrating AI SAST Early: An Organization must integrate the AI SAST tools like QINA Clarity early in the CI/CD pipeline and developers’ workflow. It enables developers for early detection and remediation of vulnerabilities in the codebase. The real-time feedback in the IDE with risk-based prioritisation directs the team to solve the security threats with high severity. SCA can be integrated with AI SAST to automate all the scanning of code changes and block the complete build if a vulnerability is detected.
- Automating AI DAST in Staging Environment: After integrating the AI SAST, it is time to integrate the AI DAST in the staging environment. It would automate the application security testing types scan and provide information regarding runtime exploits, configuration errors, or other vulnerabilities. It also serves as the final scan before the application is deployed.
- Correlating Security Findings: There are platforms that help in integrating the scan output of both AI SAST and AI DAST and correlate the findings. Correlating will help in prioritising the findings and provide a more accurate outcome of the vulnerability. Although tools like QINA Clarity AI already provide intelligently prioritised security alerts to developers. AI SAST results can be used for enriching AI DAST to help developers easily identify any nuanced vulnerabilities. On the other hand, AI DAST results can be utilised to strategize AI SAST scans and identify vulnerabilities that are exploitable in the runtime environment.
- Continuous Monitoring in Production: A continuous AI DAST scan should be implemented in the production environment to identify any new vulnerabilities that may occur due to changes in the environment. The product environment should be continuously scanned and monitored for exposed APIs or vulnerable endpoints.
Conclusion: A Combined Approach
In the AI-based SAST vs DAST comparison, both tools aren’t foes; rather, they are complementary scanning tools with specific vital roles in application security. These application security testing types are primary pillars of a modern AppSec strategy that organizations need to use in different stages of the SDLC. Embracing a comprehensive strategy with AI SAST, providing deep code analysis, and AI DAST, providing a real-world attacker’s view, an organization can build a robust security guardrail.
DevSec teams should go beyond the comparison of AI-based dynamic vs static analysis and orchestrate them together in their modern application security testing strategy. They are indispensable testing tools that, upon integration in the DevSecOps pipeline, can help in building a robust defense.







