Auto Remediation Solution
Seamless Auto Remediation Solution
Achieve Instant AI-based Auto Remediation for a Hassle-Free, Secure, and High-Performing Cloud and Application Environment.
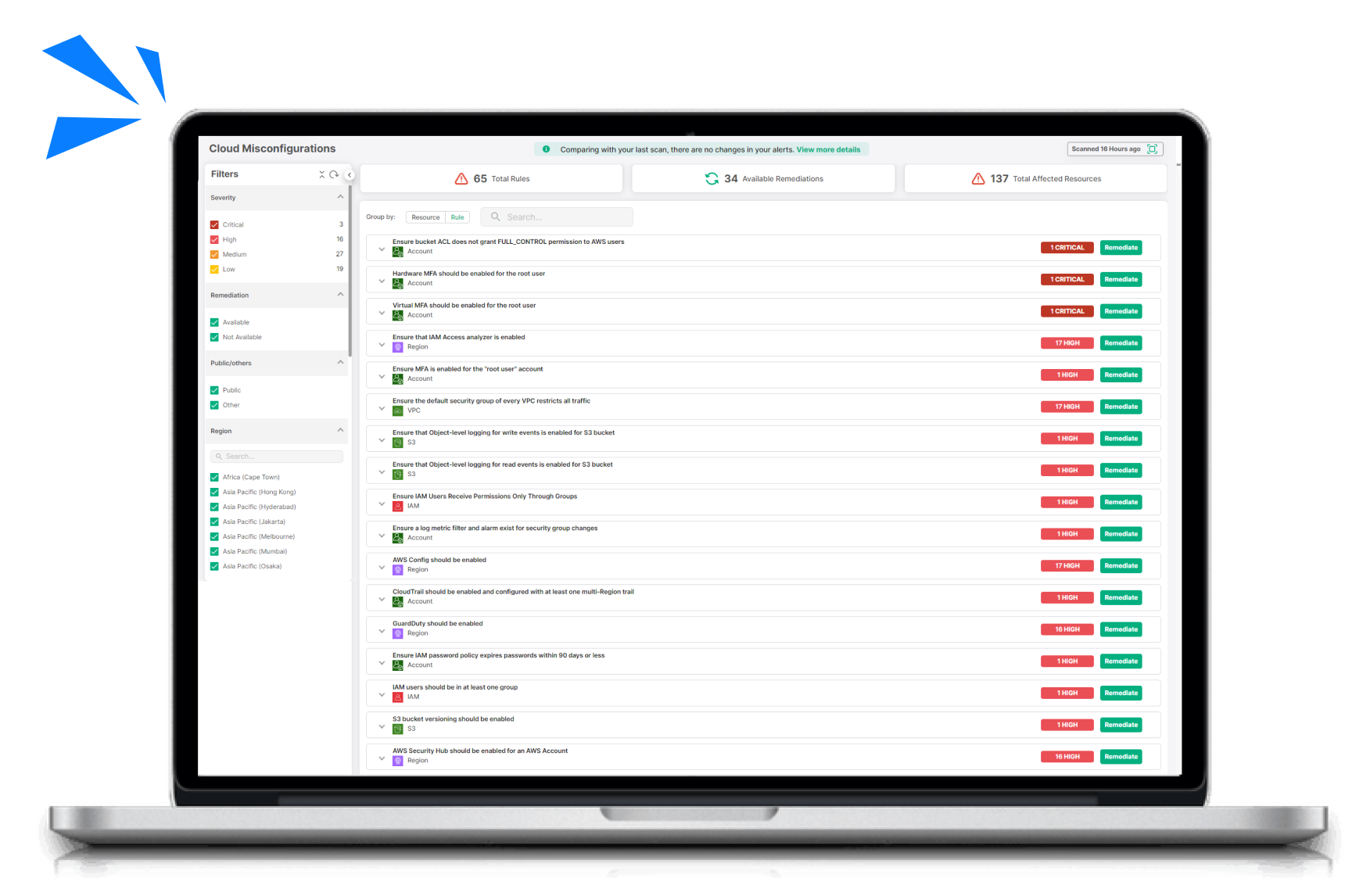
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
Auto Remediation Solution
CloudDefense.AI's Automatic Remediation: Empowering Your Cloud with Smarter, Swifter, Stronger Defense!
Our automated remediation feature empowers you to actively protect your cloud infrastructure with proactive monitoring and lightning-fast, intelligent security fixes
Smart Threat Detection
Our advanced AI-based auto remediation feature actively identifies and addresses vulnerabilities in your cloud and application infrastructure, reducing vulnerability exposure.
Instant Response
Whenever our system detects any vulnerabilities in your code or cloud infrastructure, it provides timely recommendations and actionable solutions for immediate resolution.
One-click remediation with AI
Achieve instant remediation through AI with just one click, simplifying the process of resolving vulnerabilities in both your app and cloud ecosystem.
Our Comprehensive Approach to Auto Remediation
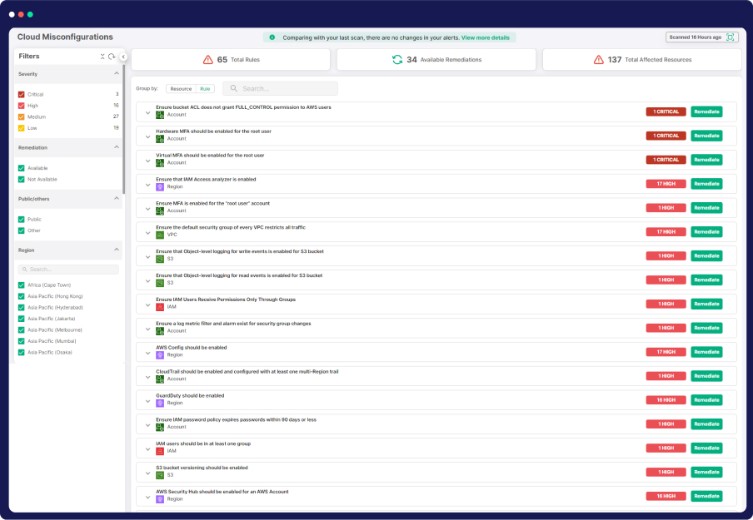
Swift and Intelligent Auto-Fixing
Achieve instant auto-fixing with CloudDefense.AI’s Auto Remediation feature, ensuring both application and cloud security. Our system intelligently identifies and resolves issues, streamlining workflows, cutting costs, and ensuring robust security and governance.
Expert Auto Remediation
Proactively manages dynamic cloud environments, initiating instant alerts and resolving issues behind the scenes without disrupting workloads.
Intelligent Analysis
Analyzes data to pinpoint root causes and automatically applies precise solutions, eliminating the need for human intervention.
Cost Mitigation
Our platform, equipped with automated remedial actions, efficiently reduces time and expenses while enhancing operational efficiency, ensuring utmost security of both applications and cloud infrastructure.
Next-Gen Remediation for App Security
Our AI-driven auto-remediation feature strengthens your application security posture by proactively identifying and rectifying vulnerabilities across SAST, DAST, and SCA scans, ensuring robust protection with ease.
Effortless Resolution
Say goodbye to manual efforts. Our platform provides clear, step-by-step guidance and automated actions to swiftly tackle identified vulnerabilities, optimizing your app security effortlessly.
Seamless Integration
Easily incorporate CloudDefense.AI into your existing workflow. Our solution seamlessly integrates with your development and security tools, ensuring a smooth and efficient application security process.
Reduced vulnerability Exposure
Minimize vulnerability windows by automating remediation processes. Protect your applications in real-time, strengthening their resilience against potential threats with CloudDefense.AI.

Rapid Remediation of Cloud Vulnerabilities
Boost your cloud security with our advanced auto remediation feature, which quickly detects and rectifies cloud misconfigurations and vulnerabilities. Bolster your defenses, streamline your operations, and achieve compliance with great confidence.
Comprehensive Coverage
Our tailored auto remediation extends across the key components of your Cloud Security Stack, encompassing CSPM, CIEM, and workload security, thereby strengthening and safeguarding your cloud infrastructure.
Remediation Prioritization
Our system classifies vulnerabilities into distinct severity levels – Critical, High, Medium, or Low. This categorization empowers your organization to allocate resources effectively, ensuring that the most pressing security concerns receive immediate remediation while optimizing efforts for comprehensive protection.
Step-by-Step Remediation Guides
Our auto-remediation feature goes beyond detection and prioritization. We provide detailed, user-friendly guides that walk you through the remediation process for each identified vulnerability in your cloud security stack.
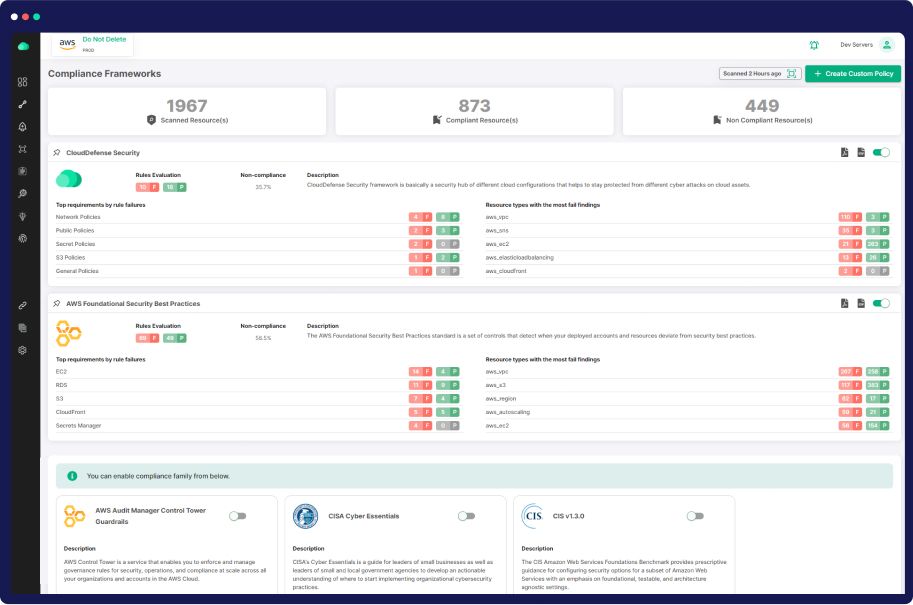
Achieve Regulatory Compliance
Since CloudDefense.AI provides auto-remediation as a core component of both our application and cloud security solutions, achieving compliance becomes effortless.
Detect and Resolve Compliance Issues
Our platform identifies deviations from compliance standards in cloud resources and automatically rectifies them, keeping your security team informed and your organization compliant.
Compliance Standards Verification
Cloud services and applications are rigorously checked against regulatory compliance standards, providing peace of mind that your organization meets necessary compliance requirements.
One-Click Remediation
With our "click-to-fix" solution, you can take immediate action to remediate security issues, simplifying the compliance journey and ensuring you're ready to meet regulatory requirements.





