Traditional methods to secure cloud environments have been rendered ineffective in recent days as threat actors and their attack techniques continue to evolve. One such sophisticated attack method is to misuse the access privileges of insiders in a company.
According to Cybersecurity Insiders, 74% of enterprises face insider threats that can devastate business. With traditional access control methods failing to address this issue, a new effective approach has been welcomed with open hands — AWSZeroTrustPolicy.
Zero trust policy is a stringent access control methodology that ensures no individual on a network is given access to resources that they have no use for, regardless of them being from external or internal sources.
A quick read of this blog post will help you understand this effective security framework and how it can ensure the security of your digital assets. Other than that we will also take a look at AWSZeroTrust Policy, a FastAPI that CloudDefense.AI is working on to help you leverage zero trust architecture in your AWS cloud environment.
What Is Zero Trust Policy?
Zero Trust Policy is a modern network security model that exceeds usual network security methods. Instead of relying on where users are, it focuses more on making sure they are who they say they are. It doesn’t assume trust from the start and insists on constantly checking and confirming the identity of all users and systems, no matter where they come from or what role they hold in the company.
By implementing the Zero Trust policy, you manage to keep things simple yet secure. Users only get access to what they need, thanks to the least privilege concept. Networks are divided into smaller parts using micro-segmentation, making it tough for hackers to slide in. With a Zero Trust model, you maintain continuous monitoring of your systems to ensure 360° visibility. In case something goes off track, the security framework is always ready to respond and recover, ensuring organizations are prepared for potential security incidents.
Case Study: Capital One Breach
Capital One, a renowned player in the U.S. financial market, made headlines in July 2019 when it revealed that its perimeters were breached. The data breach was said to affect about 100 million individuals in the United States and 6 million in Canada. When an investigation was carried out, it was derived that the breach was made possible by a misconfiguration in the company’s cloud infrastructure, where a former employee of a cloud hosting provider exploited improperly configured firewall rules.
This individual, with excessive permission privileges, used the misconfiguration to gain unauthorized access to sensitive data stored on Capital One’s AWS server. Once inside, the attacker extracted a trove of personal information, including social security numbers, credit scores, and other financial data.
The Capital One incident highlights the necessity of an impenetrable cloud security infrastructure and rigorous practices. It also emphasizes the need for effective configuration management and least privilege access principles in companies storing large amounts of data. Capital One could have averted this mishap if it had conducted regular audits of its cloud infrastructure, promptly identifying and addressing vulnerabilities to strengthen its cybersecurity defenses.
Why Zero Trust Policy Is Needed?
Without a Zero Trust Policy, organizations face major security hazards when dealing with network activity. This is exactly what happened in the Capital One breach as well. The routine practice of continually granting access, known as Seniority-Based Access Control (SBAC), leads to expanding cloud access, creating a breeding ground for threats.
This carelessness opens the door to unauthorized access, compromised credentials, and threats from insiders, significantly increasing the risks of security breaches. This is visible in the Yahoo! data breach that saw 500 million users have their data stolen. The breach, which was caused by a compromise of access, is known to incur significant financial and reputational damage for Yahoo!
The urgent need for a Zero Trust Policy is clear—it’s a vital protection, preventing security breaches and offering a strong defense against changing cyber threats.
Meet AWSZeroTrustPolicy
With cybersecurity threats continually rising, organizations must rethink their security approach to protect important assets in the company. This is where AWSZeroTrustPolicy can help build a culture of strong access controls, allowing users to access only what they need to work with. AWSZeroTrustPolicy is an opensource AWS Policy Generator API developed by CloudDefense.AI that harnesses AWS CloudTrail logs to craft IAM policies with the principle of least privilege
AWSZeroTrustPolicy is tailored to actual user activities within a specified timeframe, effectively shrinking the attack surface, minimizing risks, and enhancing overall security. The policies help empower companies to work with a Zero Trust security model, building a culture of security awareness and protecting the sensitive data of their clients.
Understanding the AWSZeroTrustPolicy Architecture
To help you deal with the issue of heightened user privileges in AWS, CloudDefense.AI has created an open-source project called AWSZeroTrustPolicy. This is an access control AWS policy generator that will help you manage user access in your AWS cloud environment effectively. Check out our repo to learn more about the API and also understand how you can implement it in your company.
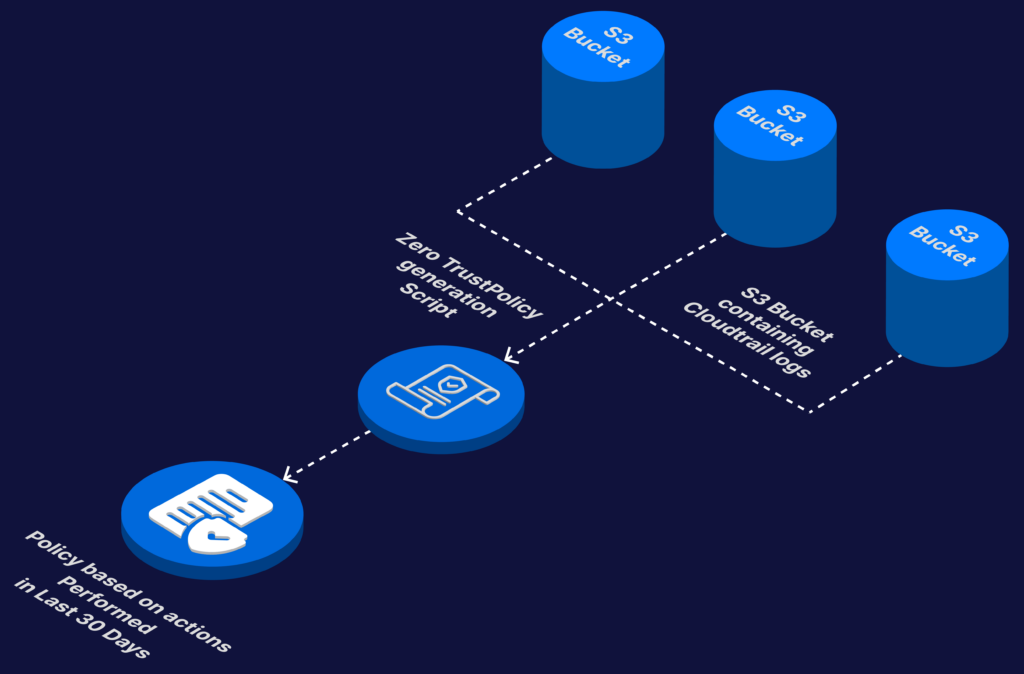
The tool goes through all S3 buckets in an AWS account connected to CloudTrail, gathers events, and creates a policy based on the collected information. To make it faster, it uses Redis as a cache to speed up policy generation. You can run the tool by sending a POST request to the /run endpoint. Here’s a simplified file structure of the project.
Installation Guide for AWSZeroTrustPolicy
We have prepared this guide for you to help you install AWSZeroTrustPolicy in your system.
Prerequisites
Before you get on with the installation process, you need to ensure the following prerequisites are met:
- Python 3.6 or Higher: Verify that Python 3.6 or a later version is installed on your system.
- Required Python Packages: Install the FastAPI and Uvicorn packages using the following command:
pip install fastapi uvicorn
- Redis Server: Set up a Redis server. You can follow the official documentation for installation instructions: [Redis Downloads](https://redis.io/download)
Installation Steps:
Here is how to install AWSZeroTrustPolicy on your system.
- Clone the Repository: Clone the AWSZeroTrustPolicy GitHub repository to your local system using the following command:
git clone https://github.com/CloudDefenseAI/AWSZeroTrustPolicy
- Navigate to the Repository: Change to the repository directory:
cd AWSZeroTrustPolicy
- Install Python Libraries: Install the required Python libraries by running:
pip install -r requirements.txt
- Run Redis Server: Start the Redis server by running:
redis-server
- Run the Uvicorn Application: Launch the Uvicorn application with the following command:.
uvicorn app:app –reload –host 0.0.0.0 –log-level debug
- Generate Zero Trust Policy: Use cURL to send a POST request and generate the Zero Trust Policy. Replace the placeholders with actual values:
curl -X POST -H “Content-Type: application/json” -d ‘{
“accountType”: “Credential”,
“accessKey”: “accessKey”,
“secretKey”: “secretKey”,
“externalId”: “externalId”,
“roleArn”: “roleArn”,
“accountId”: “accountId”,
“days”: 30,
“bucketData”: {
“us-east-1”: “aws-cloudtrail-logs-bucketid”
}
}’ http://localhost:8000/run
By following these steps, you can successfully install and run AWSZeroTrustPolicy on your system. Make sure to replace the placeholder values with the actual credentials and information specific to your AWS environment.
Best Practices for Implementing Zero Trust Policies in Your Company
After having a policy generator in place, you need to make sure that your policies are being implemented effectively in your workplace. There are a range of best practices that you must follow to ensure seamless operation.
Introduction to Zero Trust Policy:
You need to recognize the importance of implementing a Zero Trust Policy for comprehensive security. Use a layered security approach, integrating multiple measures to protect against threats around your business.
Granular Access Controls and Least Privilege:
Implementing meticulous access controls can be a savior for you. Adhere to least privilege principles, allowing your staff access only to what is essential for their role. Define and restrict permissions based on your staff’s specific job responsibilities.
User Activity Monitoring:
Your security team needs to regularly monitor your company’s user activities to detect and respond to potential threats. Utilize tools like CloudTrail logs for visibility into your actions. Have your team analyze data to identify anomalies and suspicious behavior in real time to enhance your overall security awareness.
Educating Users on Cybersecurity Best Practices:
Start by educating yourself and then your staff on the importance of strong password management. This helps in heightening your team’s awareness of phishing attempts and social engineering.
Have them participate in training programs to create a security-conscious culture and enhance your overall cybersecurity preparedness. Most importantly, teach them the principles of Zero Trust. This will greatly help your staff to cope with the stringent access controls.
Endpoint Security Measures:
Strengthen your endpoint security by ensuring you have up-to-date antivirus software and firewalls. Implement device encryption to enhance your company’s overall protection and enforce secure configurations on your devices for an upright security posture.
Continuous Security Audits:
Conduct regular security audits on your organization to assess the effectiveness of your implemented measures. This will help you to identify and address vulnerabilities promptly to stay ahead of potential risks.
Incident Response and Recovery Planning:
Lastly, develop a strong incident response plan for swift action in case a security incident occurs. Start by establishing recovery procedures to minimize downtime and potential data loss. Your preparedness and well-defined procedures will play a key role in effectively responding to and recovering from security incidents.
Conclusion
Implementing a Zero Trust Policy in your company can help you tackle your woes related to user access privileges. With threats evolving every day, it is high time that strict access policies are adopted in all companies handling sensitive user data. By adopting granular access controls, encryption, and continuous monitoring, organizations can strengthen their security framework and keep their network impenetrable.
Do not forget to check out the open-source project AWSZeroTrustPolicy on GitHub for a practical way to set up a Zero Trust Policy in your AWS cloud environment. Contributing to projects like this helps us work together to boost our security and build a community committed to protecting important assets. Embrace AWSZeroTrustPolicy to actively shield your organization’s cloud infrastructure from external and internal threats.







