What is 802.1X Authentication?
802.1X authentication is an IEEE standard that ensures that devices or users attempting to connect to an organization’s network are properly authenticated. 802.1X authentication is a part of the IEEE 802.1 working group that defines the working of port-based access control for all wired and wireless networks.
802.1X creates an authentication framework that operates at the link layers and ensures any unauthorized users or devices are prevented from gaining access. The authentication process is carried out by authenticating the client to a network device through a RADIUS or AAA security server.
The RADIUS server is responsible for carrying out the authentication mechanism of all the requests and directing servers whether they should give access or not. The primary aim of the 802.1X authentication standard is to allow only reliable clients to the network resources.
Any unknown users or devices trying to access the network have to go through thorough checks. In this standard, the clients trying to access the network are denoted Supplicant while the WAN or ethernet switch is called Authenticator.
The RADIUS or AAA (authentication, authorization, and accounting) servers are identified as Authentication Server. The IEEE 802.1X initially came out as an authentication standard for LAN networks in 2001. But later it was also used for wireless networks along with the capability to control network usage and bandwidth allocation.
When is 802.1X Used?
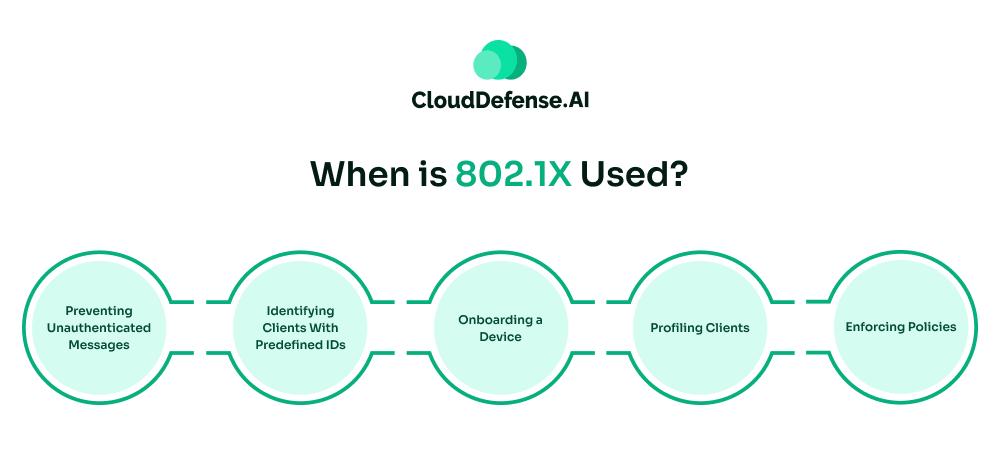
802.1X network authentication protocol is used for authorizing access of a user or device to an organization’s network when their identity is properly authenticated. Usually, 802.1X is utilized by organizations when they are running a network with a large pool of clients or building a new network.
The 802.1X standard also plays a major role when an organization’s network needs to adhere to stringent information security. When an employee needs to access the office network, the organization needs 802.1X authentication to provide access to the employee.
However, for authentication, the employee needs to install the 802.1X client software on the terminal. Along with authentication, many organizations also utilize 802.1X to set restrictions on network usage and prevent any user from exploiting it. Here are some other scenarios where the 802.1X authentication standard is often utilized:
Preventing Unauthenticated Messages
802.1X plays a crucial role in blocking any unauthenticated messages originating from devices that lack authentication or PKI certification. It is really useful in preventing hackers from entering the network.
Identifying Clients With Predefined IDs
Another situation where this standard is used is when a client with predefined credentials tries to access the network. When it identifies such clients, it provides the necessary credentials to enable them to get access.
Onboarding a Device
802.1X authentication is needed during the onboarding of a device to the organization’s network. It puts the devices through all kinds of checks and ensures the device is what it is.
Profiling Clients
The authentication process of the 802.1X standard involves many thorough checks and one of them is profiling. 802.1X helps in extracting information regarding the device it will authenticate to ensure it is providing entry to the right one. It gets information about its identity, the total number of ports it uses, and its MAC address.
Enforcing Policies
You can even enforce policies in your network using 802.1X authentication. It allows you to define an individual’s access or permission-based access to the network. As a result, it helps in limiting the chance of breaches or unauthorized users exploiting the resources.
How Does 802.1X Work?
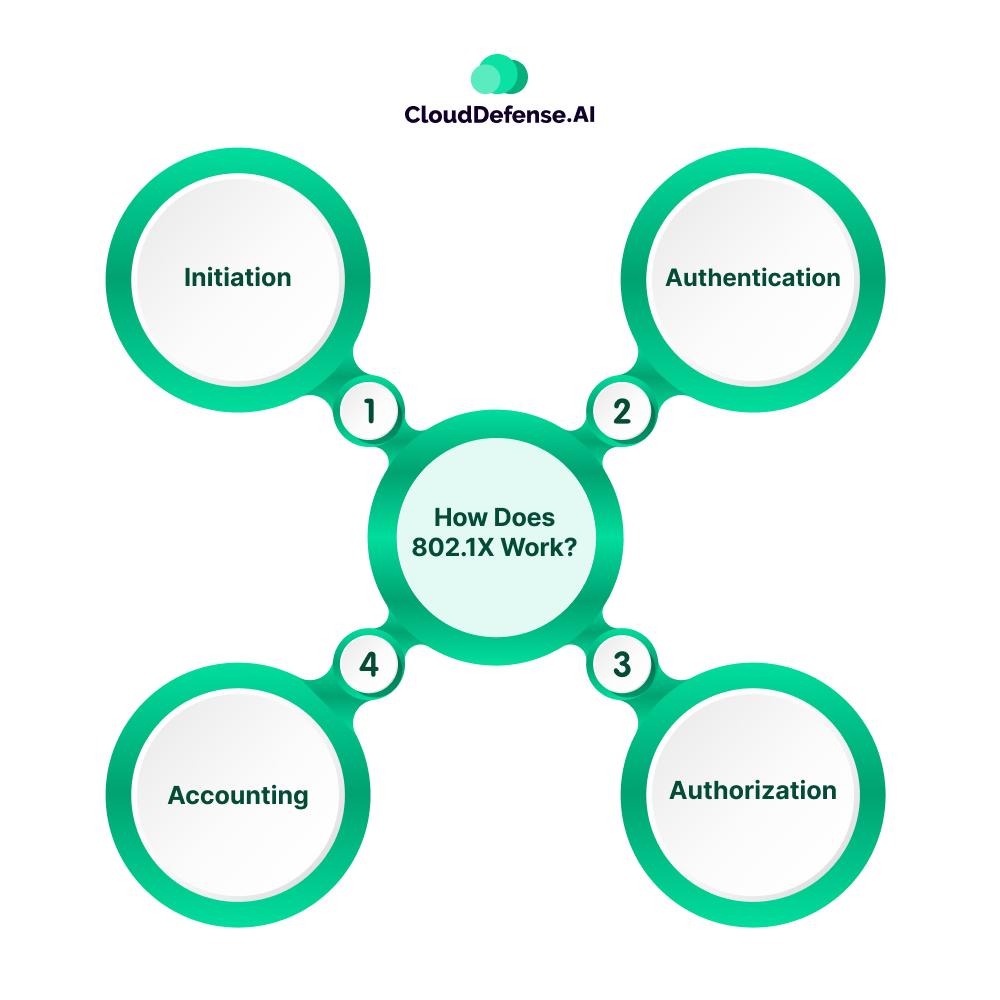
The 802.1X authentication process works by involving five primary steps and they are:
Initiation
It serves as the initial stage in the 802.1X authentication process where the authenticator (LAN or WAN) transmits the EAP request to the new device or client. EAP requests are usually used to send requests to identify the new device requesting to connect to the network.
The requests are specifically sent to the Layer 2 address of the network which is the data link layer. Usually, it is sent to the point-to-point protocol layer.
Authentication
It is an important phase in the 802.1X authentication process where EAP responses and requests are then relayed to the authentication server. The EAP responses usually contain identification information which will help the authentication server to identify the supplicant.
The authenticator first receives the response and then sends it to the authentication server in a request packet. If the supplicant passes the authentication process it receives a success message and the specific port gets authorized status.
However, if the supplicant doesn’t pass the authentication process, the authentication server replies with a failure message. The port in the network remains unauthorized and prevents the movement of non-EAP traffic.
Authorization
When the client or device’s credentials get validated or request for a public key infrastructure, the device gets access to the network. In this authorization process, RADIUS or AAA servers assess everything to ensure that the server holds the right certificates whenever it accesses the network.
This authorization process is done to prevent any malicious users from gaining entry after a particular device has been authorized for the network.
Accounting
Accounting is an important step in the 802.1X authentication process where the RADIUS server keeps a log of all the information of the device that has been authenticated. It also accounts for the complete time period of the session.
The complete device information is relayed to the accounting server when the devices access the network. Whenever the device disconnects from the network, the accounting server is informed accordingly.
How Secure is 802.1X?
802.1X is considered to be a top choice when it comes to network authentication security. It performs a thorough assessment of the credibility, source, and client information before authorizing it to the organization’s network.
From safeguarding the network from unauthorized access, intrusion, and data interception to MITM attacks and Evil Twin proxies, 802.1X can help you build robust network security.
Many network security experts prefer 802.1X authentication over others like Pre-Shared Key due to its dynamic nature. However, the effectiveness of 802.1X isn’t constant and entirely depends upon the configuration process and use of the authentication process used by the organization.
The configuration process of 802.1X plays a determining role. The configuration should be done using a certified 802.1X onboarding application as a simple mistake can make the whole network vulnerable.
Moreover, the configuration requires deep knowledge of network security so the end-user should be guided during the configuration process. They should try to manually configure them.
Along with the configuration process, the type of authentication process used by the organization also plays a crucial role. Usually, organizations use either certification-based or credential-based authentication for the authentication of a device.
Certification-based authentication serves as the best way to utilize 802.1X as it prevents the chance of any credential theft by attackers. Authentication through certification compels the device to go through the enrollment process during authorization and ensures the device is properly configured.
Another aspect that makes certification-based authentication vital is that it prevents credentials from transferring over the air which leads to interception by attackers.
The Components of 802.1X?

802.1X is composed of four primary components that enable it to work effectively. It is important to have all four components; otherwise, it won’t provide the authentication needed. Here are four components of 802.1X:
Supplicant
Supplicants are an important aspect of 802.1X which is basically software that needs to be present in the device requesting for authorization. Supplicants are crucial in the authentication process because they take in the negotiation process of the EAP transaction with that of a network switch or controller.
In addition, it is also responsible for packaging all the users’ or device’s information that can be utilized during 802.1X authentication.
The absence of supplicant in the device will cause EAP frames relayed from the switch or controller to be bypassed and it will not be authenticated. Nowadays almost all devices with wireless connectivity come with 802.1X supplicants.
Switch or Controller
Another important component of 802.1X is the switch or controller that usually serves as a broker in the transaction of the switch and client. The communication in the 802.1X exchange begins when the switch sends the EAPOL-Start packet to the client.
After that, the response from the client is relayed to the RADIUS server present in the Wireless Security Settings. Then the RADIUS server sends an Access_Accept packet containing various user’s information along with attributes.
The attribute carries information to directly switch on how it connects the client’s device to the organization’s network. Either it directs which VLAN to offer or a set of ACLs that should be assigned when the user connects.
The switch/controller also takes part in the decision-making process of whether to authorize a specific depending upon the status.
RADIUS Server
The RADIUS server is an important part of 802.1X because it decides whether to authorize access requests to a device. It is responsible for authenticating and authorizing a device to the network.
Whenever an authorized device connects to the network, the RADIUS server assesses the certificate and credentials and approves accordingly.
This server is also responsible for server certification validation which ensures the client is only connected to the network they need to connect. By checking the server certificate, the RADIUS server helps in enhancing network security and prevents attacks like Evil Twin proxy.
Identity Providers (IdPs)
The job of IdPs in an 802.1X authentication process is to manage and assess the identity of the client’s device trying to connect to the network. IdP is usually a part of the RADIUS server.
When a device requests to connect to the network, it assesses the credentials present in the packet against the centralized identity directory like AD or LDAP. Identity verification usually involves certificate validation and password authentication.
How To Configure 802.1X on Devices?
Configuring 802.1X on your device is a slightly challenging task. However, we have come up with an easy way that will help you configure it on your device without requiring in-depth knowledge:
Windows Based Device
When you want to configure 802.1X on a Windows device, it is quite easy. You can either do it using an onboard application or manually. However, to configure it manually, the user requires some network knowledge as it involves many complex steps.
Not only will you have to set up a security type and manage the network settings but also set the authentication process and other complicated steps.
However, configuring an onboarding application makes things easy and convenient. To start the process you first need to connect to SSID and then open the browser. Once you open, you will be directed to the onboarding software.
You will be navigated through various configuration processes. At the end, you will have to provide all the credentials, and once matched, the device will be authenticated. Your device will also get an authentication certificate.
Configuring on macOS Based Device
You can also configure 802.1X on your macOS device either manually or using onboarding software. For manual configuration, you need to know about verifying certificates, generating enterprise profiles, managing settings, and many other complicated processes. If you have sound IT knowledge, then you can easily navigate through the configuration process.
But, if you want to do it conveniently, then you should use the onboarding software. The process is easy where you will have to connect to the SSID and then start the browser.
You will be automatically redirected to the onboarding software’s page and there you will have to enter all the credentials. The authentication process requires users to input some inputs and the device will be configured automatically.
Configuring on Android Based Device
Like Windows and macOS, 802.1X configuration also involves two ways. You can configure 802.1X manually on your Android through Wi-Fi settings. However to do that you need to configure Server Certificate Validation, generate a profile, and select the authentication method.
To configure it through an onboarding application, you just need to download the necessary app from the Play Store. The process is pretty simple and you will just have to enter some credentials to authenticate the device.
Configuring on iOS Based Device
The configuration of 802.1X on iOS is quite straightforward and you can easily do it using onboarding software. You can download any relevant configuration app from the App Store and you will be automatically guided.
The app will basically deliver a mobile configuration file to the iOS device and the system will automatically configure the network settings. Like others, manual configuration will be tough as you will have to configure the Server Certificate Validation.
Configuring on Linux-Based Device
Unlike other devices, the configuration of 802.1X manually is pretty simple. First, you need to go to Network Manager and look for your access point from the Edit Connection option.
You need to click the Edit tab and a new page will open up where you will have to select the 802.1X settings. In the settings section, you need to put all the information of the network and then it will be configured. However, when you want to onboard many devices, it is better to use the onboarding software.
Final Words
Network security is an important aspect of modern cybersecurity strategy and 802.1X plays a major role in ensuring optimum network security. It not only ensures the device accessing the network is actually what it is but also prevents the network from various types of attacks. It only allows devices or clients to have the right certificates and credentials.
802.1X has emerged as an important authentication process that is applied in various aspects of the network. This article guides you through different aspects of 802.1X authentication and lets you understand how it can be useful for you.







