What Exactly is CTEM?
Back in 2022, Gartner came up with this idea called continuous threat exposure management, or CTEM. It is basically a five-step process that helps organizations identify, analyze, and manage their cybersecurity risks. It’s not a one-time thing or a set-it-and-forget-it solution. Instead, it’s a constant cycle of monitoring, assessing, and improving your security posture.
Think of it this way: Your company’s digital front is always changing. New software, devices, and employees can introduce new vulnerabilities. CTEM is about keeping tabs on these moving parts and making sure nothing slips through the cracks.
The “continuous” part is key here. Unlike traditional security assessments that might happen once a year, CTEM is always on. It’s about real-time awareness and rapid response to potential threats.
The “threat exposure” bit refers to any weak spots in your system that could be exploited by cybercriminals. This could be anything from outdated software to misconfigured servers or even human error.
Finally, “management” is all about taking action. Knowing your vulnerabilities is not enough—you need to have a plan to address them.
In a nutshell, CTEM is your ongoing strategy to stay ahead of cyber threats. It’s about being proactive rather than reactive, and always staying on your toes when it comes to security.
Traditional Vulnerability Management Vs CTEM
Alright, let’s break this down with a scenario to really highlight the difference between traditional vulnerability management and CTEM.
Imagine you’re running a medium-sized e-commerce company. You’ve got a website, a mobile app, and a bunch of internal systems for inventory, customer data, and finances. Here’s how things might play out under each approach:
Traditional Vulnerability Management:
You run a security scan every quarter. During your latest scan, you find out that your payment processing system has a critical vulnerability. Turns out, it’s been there for two months. In that time, hackers could’ve easily exploited it and stolen customer credit card info. You patch it immediately, but you’re left wondering what damage might’ve already been done.
The problem here? You’re always playing catch-up. By the time you find issues, it might be too late.
CTEM Approach
Now, let’s rewind and see how this plays out with CTEM in place.
Your CTEM system is constantly monitoring all your systems. One day, it flags that a new vulnerability has been discovered in the software your payment system uses. Within hours, your team is alerted. They quickly assess the risk, prioritize it based on its potential impact, and deploy a patch before any hackers can exploit it.
But it doesn’t stop there. Your CTEM system also notices that traffic to your mobile app has spiked unusually. It turns out you’re running a big promotion, and the influx of users is putting strain on your servers. The system flags this as a potential risk – if the servers crash, you could lose sales and damage your reputation. Your team quickly scales up server capacity to handle the load.
Meanwhile, CTEM is also keeping an eye on your employees’ behavior. It notices that a new hire in accounting is accessing customer data they shouldn’t need for their job. This gets flagged for HR to investigate – turns out it was just a mistake in setting up their permissions, but it could’ve been a serious insider threat.
The key difference here? With CTEM, you’re not just fixing problems – you’re anticipating and preventing them. You’re constantly aware of your security posture, able to prioritize risks in real-time, and capable of responding quickly to changes in your digital environment.
Five Steps of CTEM
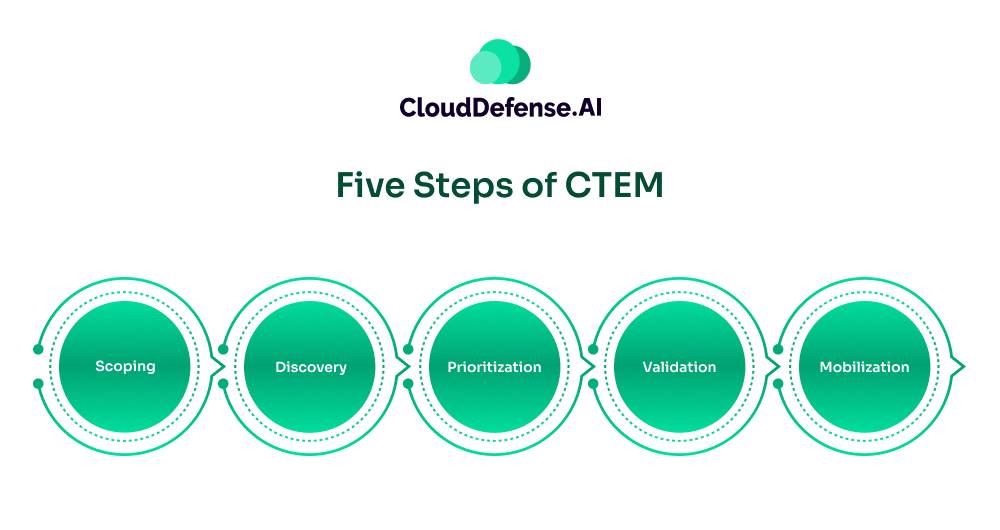
1. Scoping
This is where you figure out what you need to protect. It’s not just about listing your computers and software anymore. You need to think bigger.
First, look at your external attack surface. That’s fancy talk for all the ways someone could try to break in from the outside. Think about your website, email servers, even your company’s social media accounts.
Then, there’s your SaaS security posture. With everyone working from home these days, we’re using a ton of cloud services. You need to make sure those are locked down too.
2. Discovery
Once you know what to look at, it’s time to really dig in. This isn’t just about finding the obvious stuff. You need to look for hidden weak spots too. Check out your code repositories like GitHub. Look at your social media accounts. Don’t forget about third-party software and cloud platforms. The key here is to be thorough. Don’t just count how many things you find. Really understand each one and how it could be a risk.
3. Prioritization
You can’t fix everything at once, so you need to figure out what’s most important. This isn’t just about what’s most broken. You need to think about:
- Which assets are most valuable to your business?
- How bad would it be if something went wrong?
- What security measures do you already have in place?
Remember, a low-severity bug in a critical system might be more important than a high-severity bug in a less important system.
4. Validation
Now it’s time to see if your security actually works. This is where you try to break into your own systems
You’re checking two things here:
- Can your current security catch and stop these attacks?
- Are these vulnerabilities real threats, or just false alarms?
This step is crucial because it helps you prove to the higher-ups that these security issues are real and need attention.
5. Mobilization
This is where you turn insights into action. It’s not just about fixing technical issues, but about creating a culture of security. You need to:
- Get everyone on the same page about what needs to be done
- Make it easy for teams to actually fix these issues
- Make sure your security efforts fit with your business goals
The goal here is to create a smooth process that becomes a natural part of how your company operates.
Remember, CTEM isn’t a one-time thing. You’ll keep cycling through these steps, always improving and adapting to new threats. It’s a bit of work, but it’s way better than dealing with a major security breach.
Benefits of CTEM
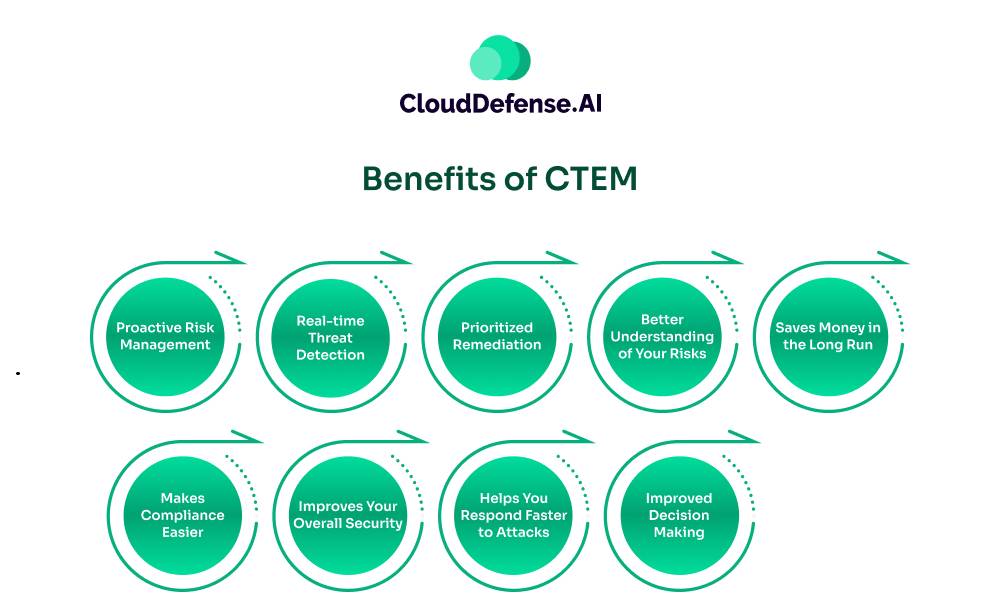
Proactive Risk Management
CTEM flips the script on traditional cybersecurity. Instead of waiting for attacks to happen, you actively seek out weaknesses. This proactive approach means you fix vulnerabilities before attackers even know they exist. You’re not just putting out fires—you’re fireproofing your entire organization.
Real-time Threat Detection
CTEM helps you spot threats as they happen. Instead of finding out about a problem weeks or months later, you’re seeing it unfold in real-time. This means you can jump on issues quickly, before they turn into major headaches.
Prioritized Remediation
Not all vulnerabilities are created equal. CTEM helps you sort the critical issues from the minor ones. Such prioritization is crucial when you’re dealing with limited resources. You can focus your efforts where they’ll have the biggest impact, rather than spreading yourself too thin.
Better Understanding of Your Risks
With CTEM, you get a clear picture of where your weak spots are. It’s not just guesswork anymore. You’ll know exactly which parts of your system need the most attention, so you can focus your efforts where they count.
Saves Money in the Long Run
Yeah, setting up CTEM costs money upfront. But think about how much a big data breach would cost you. Not just in terms of cash, but also lost time, damaged reputation, and potential legal issues. CTEM helps you avoid these costly problems.
Makes Compliance Easier
If you’re in an industry with strict security rules, CTEM can be a lifesaver. It helps you keep track of all the security measures you need to have in place, making audits and compliance checks way less stressful.
Improves Your Overall Security
CTEM isn’t just about fancy tech. It also helps your whole team get better at security. Everyone becomes more aware of potential threats and knows how to respond. It’s like your entire organization levels up in cybersecurity skills.
Helps You Respond Faster to Attacks
When (not if) an incident does occur, CTEM ensures you’re not caught flat-footed. You’ll have a clear understanding of your environment and well-practiced response procedures. It’s like a fire drill for your cybersecurity team. When a real threat emerges, everyone knows exactly what to do, reducing panic and minimizing damage.
Improved Decision Making
CTEM provides a wealth of data about your security posture. This information can inform strategic decisions about IT investments, resource allocation, and risk management. You’re not just guessing where to focus your efforts—you have hard data to back up your decisions.
Final Words
Gartner says that by 2026, organizations using continuous exposure management will be three times less likely to get breached. Three times! Can your business afford to ignore those odds?
Modern security solutions like CTEM aren’t a luxury; they’re a necessity. They’re about constant vigilance, always testing, and always improving. Without them, you’re basically leaving your digital front door wide open. Don’t wait for a catastrophic breach to take action. Implement them now, or risk becoming the next headline cautionary tale.







