In the wake of evolving supply chain attacks and other cyberattacks, staying ahead of vulnerabilities has become a necessity for organizations. However, organizations can’t protect components that they can’t see.
SBOMs enable organizations to get an inventory of all the components associated with the application, providing a detailed insight into everything. Modern software bill of materials(SBOM) has transformed from being just an inventory of software components to a critical asset of modern AppSec.
It not only enables an organization to manage the safety of the dependencies and libraries, but also to power vulnerability management and supply chain integrity. Thus, organizations need to implement SBOM best practices that will help with improved risk management and application security.
In this article, we will explore SBOM best practices that organizations can deploy for their AppSec.
SBOM and Its Key Components
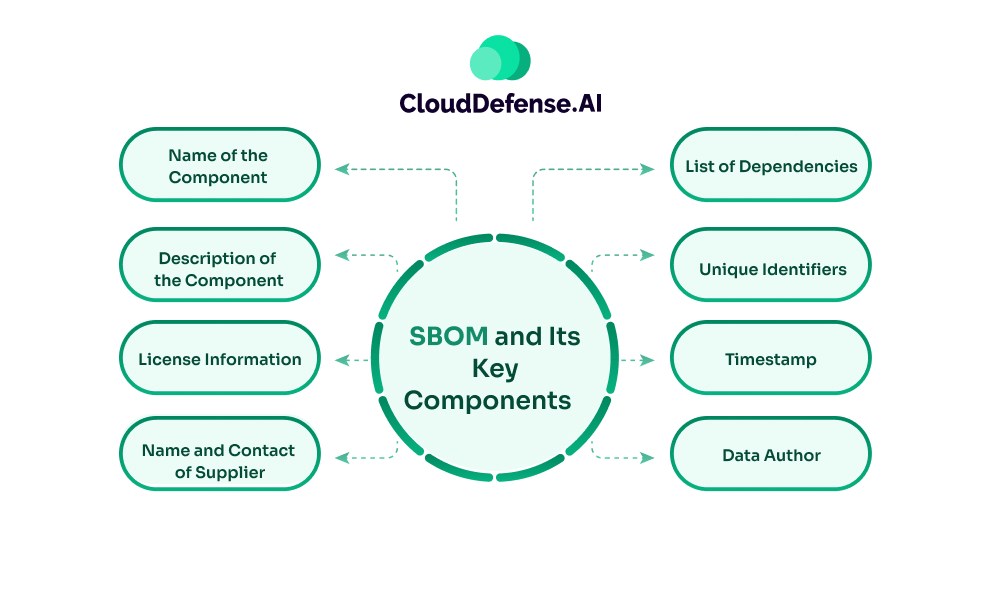
A software bill of materials is a comprehensive inventory of all the dependencies, metadata, and third-party components associated with the application. Additionally, SBOM also helps in listing all the licenses, versions, and patch status associated with those components.
Basically, it acts as a complete list of all the components that help in building an application. The typical components included in SBOM are:
- Name of the Component: The name of the application component serves as the primary base of the SBOM. It should also include the details of the release date and version number.
- Description of the Component: It also carries a brief description of all the components associated with the application. The description highlights the functionality and purpose of each component or library.
- License Information: It provides the license information associated with any of the components. It usually provides details about copyright information and usage guidelines.
- Name and Contact of Supplier: In SBOM, security teams will also find the name and contact information of the supplier or author of the application component. It provides details to the team about whom to contact for support or information.
- List of Dependencies: It provides detailed information on all the dependencies that are required by the components or library to work properly. It also defines the dependencies between different components.
- Unique Identifiers:It is a crucial part of SBOM that lists all the standardized code of each software component. It usually stores the SWID tags or CPE associated with the software components, which helps in continuous identification and tracking.
- Timestamp: This section highlights the initiation and update time of the SBOM. It is highly useful for security analysts to determine whether the relevant information is current or not.
- Data Author: A SBOM also carries the details of the author or person who is responsible for creating and maintaining the SBOM. It is useful for organizations as it helps them to contact for any kind of update or information.
SBOM not only helps organizations to manage their application but also identifies any vulnerabilities in the supply chain and ensures optimum security. Modern SBOMs have become a crucial aspect for modern AppSec as they help security teams to actively identify threats and mitigate them across the supply chain.
It is also highly instrumental for security teams to quickly respond to a vulnerability when it emerges. When a security vulnerability comes up in a third-party dependency or package, a detailed SBOM allows the team to quickly locate its position and act accordingly.
Significance of SBOMs in Modern AppSec
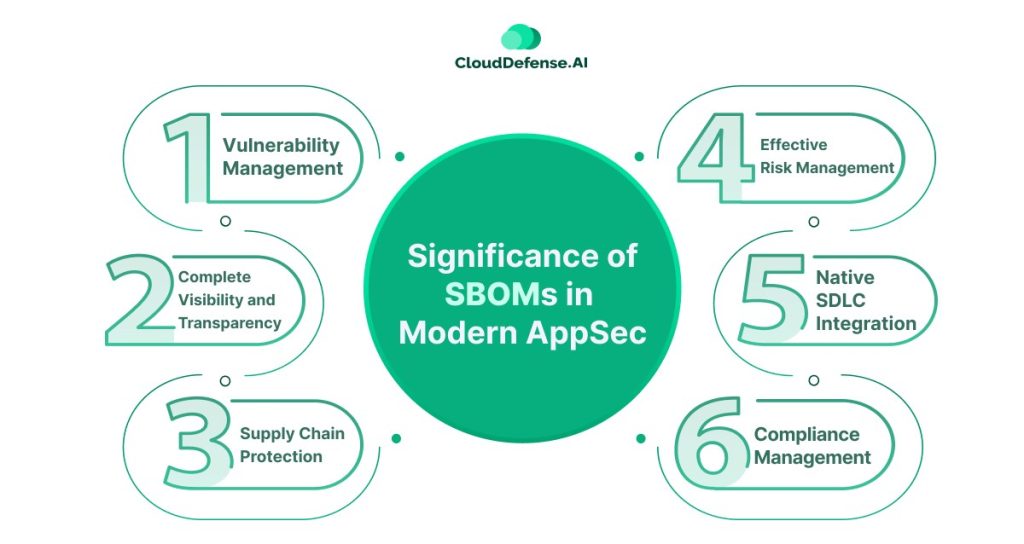
Over the years, SBOMs have become an integral part of modern AppSec. It offers security analysts the precise location and information of components in an application. It provides the team with a detailed insight into the working of the application.
But what makes them vital in an organization’s AppSec strategy?
Here are the key reasons:
- Vulnerability Management: SBOMs are highly effective when it comes to vulnerability management. It provides the security team with a complete view of all the components used in the application. With a clear view, it provides a guide to analysts to accurately identify potential vulnerabilities and mitigate them before they make an impact.
- Complete Visibility and Transparency: As a detailed inventory, an SBOM lists all the components, dependencies, libraries, and versions associated with the application. It reveals both open source and third-party components for visibility. As a result, DevSec teams can accurately understand the attack surface and minimize all the loopholes.
- Supply Chain Protection: Modern applications are built on multiple third-party components, introducing a complex supply chain to protect. So a SBOM allows the organization to track the component and assess its security posture. Security teams can assess the origin of all the components and make sure they have an unbroken chain of trust with proper information and time stamps.
- Effective Risk Management: SBOM establishes effective risk management by helping teams to discover all the risk components and track any issues with the supplier. It plays a vital role in identifying all the instances of vulnerable components. Thus, it streamlines the incident management process to quickly identify and remediate it.
- Native SDLC Integration: A great aspect of SBOMs is that they natively integrate into the SDLC of any application development program. It streamlines the application security process by allowing the AppSec tools to accurately identify security threats at the beginning. It not only ensures quick incident management and effective security but also cost effectiveness.
- Compliance Management: Every organization that stores and processes customer data for its application has to adhere to certain regulatory standards. Most industry standards require organizations to have an SBOM. So, it helps organizations to adhere to all standards and regulations through auditable proof of inventory. Having a signed SBOM enhances the trust and audit process as it assures the integrity of dependencies.
SBOM Best Practices Organizations Should Follow

Generating an SBOM of the application is not a straightforward task. Organizations need to follow certain best practices that will offer better management and maintenance, ensuring a robust and better AppSec.
The best practices an organization should follow are:
Creating Transparent Policies and Procedures
Establishing a robust SBOM for AppSec requires the implementation of transparent and structured policies and procedures. Having a clear framework will enable the organization to establish the appropriate procedures for generating and maintaining SBOMs for every application.
The policies should clearly define all the processes in detail so that everyone in the organization can follow them properly. It will not only help in improving the AppSec but also minimize the chances of errors from the security teams’ side.
Generating a Streamlined Inventorying Process
Another vital SBOM best practice organizations must follow is generating an inventory process. Having a complete list of components enables security professionals to have complete visibility and maintain detailed insight into all the components in the application. It is important that the organization create an automated process that will constantly identify, track, and log all the details regarding components used in the application.
A streamlined inventorying process will provide the AppSec team with details like license, origin, and associated vulnerabilities. The inventorying process should be reviewed and updated regularly to make sure it aligns with the AppSec program.
Complete Visibility into Supply Chain
As applications are getting complicated with time and so is the supply chain. So it has become vital for every AppSec program to have visibility into the origin of components associated with the supply chain. A transparent supply chain will enable the security team to identify and determine all the security issues related to the third-party component.
All the vendors associated with the SBOMs must be assessed and validated based on their security practices. It not only reinforces the guardrails to SBOMs but also adds an additional security layer to application security by minimizing supply chain attacks.
Utilizing an AI-Powered Automation Tool
Automation is the answer to modern application development’s need for speed, agility, and security. Leveraging AI-based automated tools like QINA Clarity will enable security teams to efficiently and continuously identify security threats.
QINA Clarity can act as a comprehensive tool that will analyze all the building blocks of SBOM and discover all the related issues. Integrating the SBOM with the automated tool will help the AppSec team to continuously address threats associated with the third-party components and enhance the defense.
An organization should also focus on utilizing automated SBOM-generating tools. It will not only reduce the chance of error but also help security teams to manage updated views regarding all components for their AppSec strategy.
Strategizing Storage and Access Of SBOMs
Securing the SBOMs has become a critical aspect of the modern AppSec program. Organizations, when making the SBOMs accessible, must carefully strategize the storage policy and access control. Even though they are accessible to relevant personnel, it is important that organizations store them securely with limited access.
The access control to the SBOMs should be configured so that it can show who has accessed the SBOM data and how they use it. Access to SBOM should be limited and restricted, limiting the chance of threat actors gaining access to the vital SBOM data.
Continuously Reviewing and Updating
The security and software development scenario is evolving regularly. So it is important that the organization should be continuously reviewed and kept up-to-date according to all the changes.
The update should be done according to the version so that it is easier for the security team to identify to mitigate any vulnerability when it arises. Automating the reviewing and updating process for SBOM will streamline the workflow and enhance the accuracy.
Ensuring SBOMs Adhere to Regulatory Requirements
Making sure SBOMs are aligned with the regulatory standards followed by the organization will enhance the defense guardrails.
All the SBOMs should be configured in accordance with the compliance needs, with a detailed origin of each component. It should also highlight all the information regarding the license and how the SBOMs’ data are stored to make it audit-ready.
Bottom Line
The time for treating SBOM as just a requirement for application security and compliance artefact is over. In today’s time, SBOM is considered a crucial part of the AppSec program. It delivers crucial intelligence needed to accurately identify any vulnerability in the application.
It also helps the development to eliminate the friction to achieve development velocity while maintaining an optimum security posture. SBOM best practices not only allow organization to improve their AppSec approach but also improve visibility across all the components in application development. Introducing SBOMs in the development environment and automated analysis will greatly improve the supply chain security.







