Recently, Infrastructure as Code (IaC) practices have been transforming the way we build and manage cloud environments, making infrastructure deployment faster and more consistent. But, as IaC practices gain momentum in 2025, the risks are higher than ever—cloud misconfigurations and vulnerabilities are top targets for cybercriminals.
To stay ahead, developers and security teams need tools that catch issues before they reach production. Here’s a look at the 10 best IaC scanning tools that are helping teams prevent security slip-ups, automate compliance checks, and build confidently in the cloud.
What is Infrastructure as Code (IaC)?
Infrastructure as Code (IaC) scanning is all about catching security issues in your infrastructure code before they become big problems. In other words, IaC scanning is the process of analysis and securing the scripts that define and automate cloud environments, like setting up servers, storage, or networks. When you use IaC, you’re essentially writing the blueprint for your cloud infrastructure in code.
It’s fast, efficient, and helps keep things consistent across different environments. But, just like any code, IaC scripts can have errors or security gaps that can leave your system vulnerable. This is where IaC scanning steps in.
Want to Know More about IaC Scanning? Read here to learn more about how Infrastructure as Code scanning can enhance your security practices and streamline your DevOps workflow. |
What are IaC Scanning Tools?
IaC scanning tools automatically review your code to find misconfigurations, vulnerabilities, or any security policies you might be overlooking. Catching these issues early—before your code is deployed—means you can fix problems when they’re easiest and cheapest to address.
Plus, it helps ensure that you’re staying on top of compliance requirements, so your infrastructure isn’t just functional, but secure and up to standard. Making IaC scanning a regular part of your development process helps catch risks before they hit production, especially when using the best IaC scanning tool for the job. This way, you’re not just catching risks before they hit production—you’re also setting the tone for proactive security.
What should you look for in an Infrastructure such as Code (IaC) Scanning Solution?
When it comes to selecting the best IaC scanning tools, it’s essential to have a keen eye for features that not only detect vulnerabilities but also integrate with your existing workflows like butter and enhance your overall security infrastructure. Here are all the key features that you need to keep in mind:
Integration with IaC Frameworks
Seek out the best IaC scanning tools that easily mesh with commonly used IaC frameworks such as Terraform, Azure Resource Manager, and AWS CloudFormation. This creates a smooth environment where security measures can be beefed up without putting the brakes on development.
Custom Security Rule Creation
Being able to craft personalized security rules that fit your infrastructure perfectly can be essential for you. This way, you can tackle specific threats head-on, ensuring your defense is as unique as your system.
Static and Dynamic Analysis
Make sure the best IaC scanning tool you choose covers both SAST and DAST. This ensures thorough security checks throughout every stage of the software development life cycle.
Auto-Remediation
Pick the best IaC scanning solution that does more than just find vulnerabilities; it should also offer auto-remediation. This means it not only spots issues but also fixes them right away, cutting down the time for potential attacks and boosting your overall security strength.
Risk Prioritization
Focus on solutions that have strong risk prioritization features. These let developers easily see the most critical risks and make smart decisions. Visual representations of risks in context make this even easier.
Integration with CI/CD Pipelines
Make sure the IaC tool you pick fits smoothly into your Continuous Integration/Continuous Deployment (CI/CD) pipelines. This means security checks become part of your regular workflows, giving you timely feedback and suggestions.
Compliance
Put findings into context by checking how well they meet industry standards like SOC 2, PCI-DSS, GDPR, and NIST. Make sure the IaC scanning solution can also handle custom benchmarks based on your organization's specific regulatory needs.
Integrated Application Lifecycle Platform
Think about choosing an IaC scanning solution that's part of a larger Cloud-Native Application Protection Platform, or CNAPP. These platforms include integrated risk intelligence and fixes, along with other security features like CWP, CIEM, CSPM, KSPM, SAST, DAST, and SCA. This gives you a complete security solution for your whole setup.
10 Best IaC Scanning Tools in 2025
There are hordes of IaC scanning tools available in the market, which results in confusion among buyers. With a number of features to keep in mind and checking one of them to see if it is compatible, it is very time-consuming.
To assist you with just that, we bring you the top 10 best IaC scanning solutions that you can pick from to get the best IaC security service available in 2025.
CloudDefense.AI

CloudDefense.AI 
CloudDefense.AI is the best CNAPP in the market that companies trust to secure their cloud infrastructure. As part of the holistic, code-to-cloud CNAPP, our IaC scanning tool is packed with cutting-edge features that keep your systems safe. It smoothly fits into your workflow, giving you clear insights and fixes for any vulnerabilities. With CloudDefense.AI, you can stay ahead of threats and keep your cloud environment secure without the hassle. Here is more to why you should choose CloudDefense.AI.
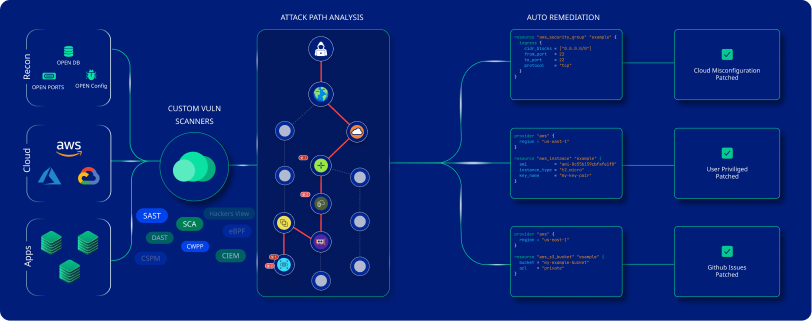
Features
Complete IaC Security Assurance
CloudDefense.AI's automated IaC security scanning keeps your projects safe by constantly checking for misconfigurations and secrets. It makes sure your DevOps workflows run smoothly, quickly resolving any issues that arise. With CloudDefense.AI, you can maintain continuous governance and keep your projects secure effortlessly.
Integrated Development Lifecycle
Easily integrate security into your development environments, CI/CD tools, repositories, and runtime environments with CloudDefense.AI. This means security is always a part of your software development process, from start to finish.
Code-Level Remediation
CloudDefense.AI offers code-level remediation for a wide range of IaC misconfigurations, ensuring that security issues are resolved to maintain a strong security posture.
Automated Misconfiguration Fixes
CloudDefense.AI automatically resolves misconfigurations by generating pull requests, making it easier to fix security issues without needing manual intervention. This ensures your infrastructure stays secure with minimal effort.
Centralized Security Hub
Gain a unified view of all IaC security concerns across repositories, with detailed filtering and searching capabilities. This allows for swift identification and remediation of vulnerabilities.
Real-Time Policy Drift Monitoring
CloudDefense.AI monitors policy drift in real-time, allowing for the identification and remediation of deviations from established security policies.
Support for DevOps Tools
CloudDefense.AI supports integration with DevOps tools like GitHub, Jenkins, and more, ensuring smooth collaboration and workflow integration within your DevOps environment.
Auto Remediation
Get straightforward, actionable guidance for every policy violation, making it easy to quickly resolve misconfigurations in your cloud infrastructure. This means you can tackle security issues quickly and efficiently, keeping your projects safe without the usual security headaches.
Advanced Reporting and Analytics
Stay in the know with our intuitive reporting and analytics. You’ll have a clear picture of your security status, making it easier to track vulnerabilities and make informed decisions about your security strategy.
Pros

Complete IaC security coverage, from code to runtime environments.

Automated fixes for misconfigurations speed up issue resolution.

Smooth integration with CI/CD pipelines for ongoing security checks.

A centralized security hub offers a single view of vulnerabilities across repositories.

Clear guidance for efficient resolution of security issues.

Context-driven insights aid in informed decision-making and resource allocation.
Cons

Teams that are new to IaC security might require some time to master the console.
KICS by Checkmarx

KICS by Checkmarx
KICS is a powerful security tool with extensive support for platforms like Terraform and Kubernetes, boasting over 2400 queries for identifying vulnerabilities and misconfigurations. It’s known for its user-friendly installation process, intuitive results interpretation, and seamless integration with CI workflows. Jit can effortlessly pair with KICS to automate SAST checks IaC, ensuring ongoing security with every commit.
Features
With over 2400 queries, KICS offers a vast array of checks to detect vulnerabilities and misconfigurations, allowing for thorough security assessments.
KICS provides clear and concise results, making it easy for users to understand and address security issues effectively.
KICS enables automated and continuous security testing within DevOps workflows, ensuring strong security measures with each code commit.
Checkov

Checkov
Checkov is an open-source solution for eliminating cloud misconfigurations by analyzing static code in IaC. Checkov scans your cloud infrastructure to detect vulnerabilities and ensure compliance with built-in policies covering best practices for Google Cloud, Azure, and AWS. Being Python-based, it simplifies writing, managing, and version-controlling codes.
Features
Checkov comes with a library of built-in policies covering best practices for Google Cloud, Azure, and AWS, ensuring compliance and security.
Being Python-based, Checkov simplifies writing, managing, and version-controlling codes, enhancing the development process.
Checkov allows for inline suppression of accepted risks, enabling teams to manage and prioritize issues according to their risk tolerance.
Accurics

Accurics
Accurics is your ultimate defense against cloud misconfigurations, data breaches, and policy violations. With Accurics, you can proactively scan Kubernetes YAML, Terraform, OpenFaaS YAML, and Dockerfile to detect issues before they impact your infrastructure. By ensuring continuous checks and enforcing compliance, security, and governance, Accurics helps future-proof your DevOps lifecycle and protect your cloud stack.
Features
Accurics performs code scanning for Kubernetes YAML, Terraform, OpenFaaS YAML, and Dockerfile, enabling comprehensive detection of misconfigurations across your cloud infrastructure.
By continuously monitoring infrastructure configuration, Accurics detects any drift and ensures that changes align with defined code, preventing posture drift and maintaining security.
Accurics seamlessly integrates with popular workflow tools such as Slack, webhooks, email, JIRA, and Splunk, allowing for efficient notification of issues to developers and enabling swift remediation.
Accurics offers both cloud-based and self-hosted versions, providing flexibility to choose the deployment option that best suits the requirements of your organization.
TFLint

TFLint
TFLint is your go-to Terraform linter for checking errors and enforcing best security practices. While Terraform is powerful for IaC, it may overlook provider-specific issues, making TFLint an essential addition to your toolkit. With support for various providers like AWS, Google Cloud, and Microsoft Azure through plugins, TFLint ensures the reliability and security of your cloud architecture.
Features
TFLint focuses on detecting possible errors in Terraform code, ensuring the reliability and stability of your infrastructure configurations.
It enforces best security practices for Terraform, helping to mitigate potential vulnerabilities and ensure a secure cloud environment.
TFLint addresses provider-specific issues that may be overlooked by Terraform, enhancing the overall reliability and effectiveness of your infrastructure code.
It supports several providers through plugins, including AWS, Google Cloud, and Microsoft Azure, allowing for validation and security checks across various cloud platforms.
Aqua Trivy

Aqua Trivy
Trivy is a regularly updated security scanning tool focused on providing comprehensive coverage in vulnerability detection. With new versions released monthly targeting various operating systems and programming languages, Trivy is known for its reliability, speed, and user-friendly interface. This versatile open-source scanner effortlessly identifies vulnerabilities, IaC misconfigurations, SBOM discovery, and cloud scanning.
Features
Trivy expands its capabilities by incorporating the ability to scan IaC configurations, effectively identifying common misconfigurations in popular tools like Terraform, CloudFormation, Docker, Kubernetes, and other configuration files.
It is a versatile multi-container scanning solution with no external dependencies. It scans both local and remote images, works with multiple container engines, and is compatible with archived/extracted images, raw filesystems, and git repositories.
Trivy runs on any operating system or CPU architecture, ensuring quick and effective scans. Its portability makes initial scan times efficient while delivering fast recurring scans.
Spectral by Check Point

Spectral by Check Point
Introducing Spectral: a developer-first IaC scanning tool designed to uncover misconfigurations and secrets sprawl. By integrating seamlessly with developers’ workflows, Spectral offers a unique approach to security scanning. It provides continuous visibility into public exposures and supply chain vulnerabilities, along with the ability to enforce custom security policies, making it ideal for developer teams seeking to enhance security without disrupting their existing processes.
Features
Spectral prioritizes developers' workflows, ensuring that security scanning seamlessly integrates into their daily routines without causing disruptions.
The platform enables the integration and enforcement of custom security policies, ensuring that teams can tailor security measures to align with their specific requirements and standards.
Spectral conducts daily scans of all repositories, helping teams identify and address important security issues in their code promptly.
Terrascan by Tenable

Terrascan by Tenable
Terrascan is an IaC solution for ensuring the security and compliance of your cloud-native infrastructure. With over 500 ready-to-go policies, including CIS Benchmarks, Terrascan scans IaC to verify that it meets security best practices and compliance standards. It’s ideal for organizations and teams striving for high-security standards in their cloud-native deployments, especially those using a variety of IaC tools and cloud providers.
Features
Terrascan comes with over 500 ready-to-go policies, including CIS Benchmarks, ensuring comprehensive coverage of security best practices and compliance standards.
Terrascan scans Infrastructure as Code (IaC) to verify that cloud-native infrastructure meets security standards, allowing for proactive identification and remediation of security issues.
Terrascan supports multiple cloud providers, making it suitable for organizations with diverse cloud deployments across different platforms.
Terrascan seamlessly integrates with various IaC tools and workflows, allowing for easy incorporation into existing development pipelines.
PingSafe

PingSafe
PingSafe is a strong shift-left security enforcement platform. Ideal for organizations with a larger budget seeking a comprehensive cloud security solution, PingSafe goes beyond IaC with advanced features like automated threat remediation, intuitive data visualizations, and seamless CI/CD integration.
PingSafe is a strong shift-left security enforcement platform. Ideal for organizations with a larger budget seeking a comprehensive cloud security solution, PingSafe goes beyond IaC with advanced features like automated threat remediation, intuitive data visualizations, and seamless CI/CD integration.
Features
PingSafe offers automated threat remediation, enabling swift response to security incidents and minimizing the impact of potential breaches.
PingSafe provides helpful data visualizations, making it easier for users to understand complex security issues and take informed actions.
PingSafe integrates with CI/CD pipelines, ensuring that security checks are seamlessly integrated into the development workflow without causing disruptions.
Jit

Jit
Jit is the ultimate DevSecOps platform that simplifies the implementation of security measures in infrastructure coding. It is ideal for organizations seeking an all-in-one platform for IaC security and remediation. It works effortlessly with popular development environments like GitHub or AWS and enables the management of security tools across the entire CI/CD pipeline.
Features
Jit provides easy orchestration with security scanning tools like KICS, enabling organizations to efficiently identify and address potential security vulnerabilities in their infrastructure code.
Jit seamlessly integrates with popular development environments like GitHub or AWS, allowing developers to incorporate security measures into their existing workflows without disruptions.
Jit provides clear, actionable guidelines that empower developers to adopt a foundational security framework tailored to organizational demands, fostering a culture of security awareness and compliance.
Conclusion
Given the rate at which cloud-native infrastructure grows, securing it through Infrastructure as Code (IaC) becomes more than crucial. The right tools don’t just guard your systems, they create smoother, more collaborative workflows between development and operations.
Among the 10 best IaC scanning tools listed out here, CloudDefense.AI doesn’t just lead the pack—it transforms how security integrates into modern infrastructure. If you’re ready to rethink your approach to IaC security, schedule a free demo and discover how CloudDefense.AI can transform your strategy. Let’s take your security to the next level!







