In modern software development, managing all the secrets and building secure software has become a paramount aspect. It is not just about managing secrets or preventing them from being hardcoded in the codebase; it is about securely managing and storing various digital credentials associated with the software.
The best way to do it is by implementing a centralized secret management tool that not only helps you secretly manage credentials but also prevents secret sprawls. Whether you are a developer or admin, navigating the market and selecting the right secret management tool can be daunting.
We have come up with this article to simplify your decision making and guide you to the right tool. After comprehensive research, we have come up with a list of the 10 best secret management tools in 2025 that can help you securely manage all your digital credentials.
Through this article, we will not only provide our experience with all the tools but also put forward a lot of information to give you in-depth knowledge. Without further ado, continue reading through the following.
Let’s dive in!
What is Secret Management?
Secret management refers to the method or practices that enable developers or sysadmins to securely store sensitive digital authentication information in a safeguarded environment with stringent access control.
The primary aim of this practice is to ensure that sensitive digital credentials like passwords, API keys, certificates, tokens, and other secrets that are used in day-to-day operations are safeguarded. It helps fortify your security in the development and production environment without reducing the productivity of DevOps workflow.
It is a common practice to store secrets in scripts, source code, or plain text, making them easily exploitable by malicious actors. Secret management makes sure the digital credentials are never embedded into artifacts and ensures a proper audit trail for all access activity.
It is a combination of different security approaches like role-based access control, the principle of privilege, authenticated access and tracking, and various other techniques.
Nowadays, most organizations are using secret management tool to help ensure all secrets remain confidential by transforming them from simple text to cryptic data.
This solution plays an instrumental role in reducing the risk associated with manual secret management and weak passwords. Most of the secret management tools available in the market are SaaS based platforms that streamline password management and protect digital credentials from unauthorized access.
What to Look for in Secret Management Tools?
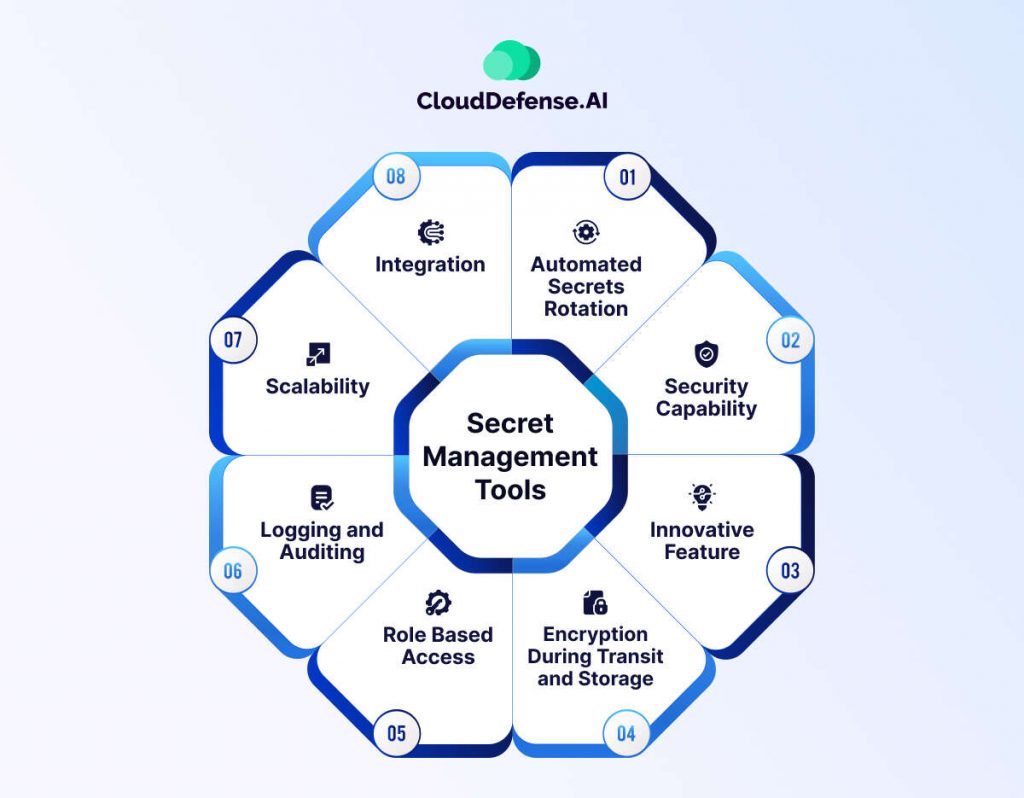
Secret management is not all about providing ways to securely store and access secrets; it is more than that. When looking for a secret management tool, you will have to consider a lot of factors that will guide you to the right tool. Let’s check them out:
Automated Secrets Rotation
An efficient secret management tool can perform automated secret rotation by requesting to change the secret. It should be able to update the secret within the stored environment through automation at a user-defined time frame.
Security Capability
It is always best to evaluate the security capability of the tool you are about to choose. A secret management tool with a good suite of secret features and encryption methods will be ideal for your organization.
Innovative Feature
Another aspect you need to take into consideration is the number of innovative features and technologies it has on offer. As security challenges are evolving with time, having a modern secret management tool with innovative features will help you stay ahead of the threat.
Encryption During Transit and Storage
The secret should be properly encrypted when it is in transit or at rest. The tool must implement the best encryption method to secure the secret during transmission or storage and protect it from exploitation.
Role Based Access
Role or identity based access is vital for this tool as it ensures devices or users are given access to only a specific secret they need for their operation. The tool must help in ensuring the principle of least privilege and make sure users can only access specific secrets and not the ones they are authorized with.
Logging and Auditing
The secret management tool must offer logging and auditing capabilities where logging would help keep track of all the periodic system scanning. Significantly, in an occasion of hacking, the audit trail will help you track how the attackers got access to the secrets.
Scalability
In modern times where every organization is growing at a rapid rate, the tool must be able to accommodate and manage secrets according to the requirements of the organization. Whether the organization is small or large, it should accommodate the needs according to growing change.
Integration
It is important for the secret management tool to integrate properly with the existing development and deployment platform. Having APIs will enable the tool to integrate common resources like CI/CD systems or provide access to specific frameworks. You should also make sure that it is compatible with different systems.
10 Best Secret Management Tools in 2025
We understand choosing the perfect secret management tool in 2025 is a lot more tricky than it appears. That is why we have come up with a comparison table and list that will ease up your task and help you find the right secret management tool for your organization:
This list simplifies your selection process, focusing on tools that align with key principles that have been mentioned above, ensuring technical compatibility without unnecessary complexity in 2025
Here is a handy list for you to review quickly if you are short on time.
Tools | Centralized Storage | Secret Rotation | Key Features | Price |
CloudDefense.AI | Limited to scanning | Available | 1. Real-time scanning. 2. Holistic secret detection suite. 3. Contextual validation. 4. Code risk prioritization. | The price is quoted after you book a demo. |
AWS Secret Manager | Available | Available | 1. Fine grained IAM and resourced-based policies. 2. Secret replication. 3. Secret monitoring. | The price starts at $.40 per-secret per month. |
1Password | Available | Available | 1. Easy secret sharing. 2. Integration with existing security stack. 3. Customizable policies. 4. Streamlined provisioning. | The base price starts at $7.99 for businesses. |
HashiCorp Vault | Available | Available | 1. Dynamic secret generation. 2. Identity-based access. 3. Automated PKI infrastructure. | The price is quoted after you apply for a trial.
|
Doppler | Available | Available | 1. Mask secrets. 2. Identification of missing secrets. 3. Secret referencing. 4. Real-time reporting. | The price starts at $18 per-month per-user. |
Bitwarden | Available | Limited | 1. Collaborate securely. 2. SSO integration. 3. Open source codebase. | Free. |
CloudDefense.AI

CloudDefense.AI 
Protect your organization’s secrets and discover exposed ones using CloudDefense.AI’s secret management tool. It is a powerful full-stack solution that scans your source code in real time to identify secrets in the CI/CD pipeline and repositories.
CloudDefense.AI enables you to take a comprehensive approach where it protects your passwords, encryption keys, API keys, and other secrets. It is one of those tools that empowers the team with a suite of advanced features like threat analysis, contextual remediation, modern algorithm-based automated code scanning, and data insight.
The simple interface and well-laid-out features make this tool extremely easy to use and streamline the process of detecting exposed secrets.
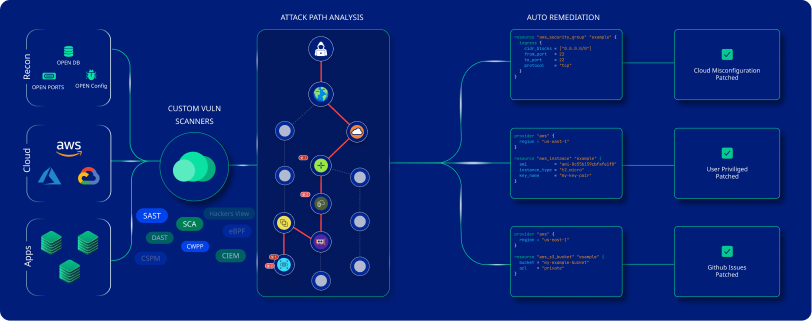
Features
CloudDefense.AI is an all-in-one solution that makes it easy for you to find exposed secrets and protect your application from getting exploited. It comes with many key features that enable this solution to be effective in its performance, and they are:
Precise Detection
CloudDefense.AI offers a precise detection feature by leveraging advanced algorithms and 100+ domain-specific detectors to accurately identify and ensure protection against vulnerability. Importantly, it performs thorough scanning across repositories and CI/CD pipelines to leave no secret undetected and protect them at all cost. Moreover, the domain-specific detectors alert the team within both build and runtime to uncover exposed secrets.
Contextual Alert
One of the areas where CloudDefense.AI excels from others is by providing contextual alerts. This solution automatically validates to ensure the detected secrets are valid in your production code and then correlates the issues with other risk factors before providing alerts. With contextual alerts, it becomes easy for the developers and security team to understand the depth of the issue.
Contextual Remediation Action
In addition to contextual alert, this solution also offers the developers with contextual remediation actions to help remediate the secret issue immediately. The quick remediation with context helps in enhancing the overall code security by a large margin.
Secret Scanning Integration
The secret scanning integration feature infuses seamlessly in your developer workflow and identifies hard coded secrets to eliminate them. It is really useful in eliminating vulnerability at the root and preventing the habit of hardcoding.
Real-Time Threat Analysis
The real-time threat analysis of this tool not only detects exposed secrets in private and public code in real time but also helps the AppSec team to remediate them instantly. It utilizes graph analysis that identifies suspicious behaviors and patterns in secret access and prevents secret exposure.
Pros

Performs thorough and automated scanning in your repositories and CI/CD pipeline to uncover exposed secrets.

CloudDefense.AI provides you with real-time threat detection and mitigation capability to ensure code remains safe all the time.

It makes use of advanced algorithms and domain-specific secret detectors to enable in-depth secret analysis.

Reduces secret exposure risk by assessing and prioritizing secret risks using Code Risk Score and enables the AppSec team to target the vital issue.
Cons

The initial investment can be slightly pricier for smaller organizations.

New users might have to go through a steeper learning curve to use some advanced features.
What Sets CloudDefense.AI Apart?
Here are some key aspects that make our tool one of a kind solution for organizations of all sizes:
Secret Scanning Integration
One of the highlighting features of this solution is the secret scanning integration where it eliminates hard coded secrets and enables the AppSec team to uproot vulnerabilities.
Real-Time Threat Mitigation
CloudDefense.AI does more than automated code scanning and helps your team to remediate secret issues in real-time to ensure minimal impact on application.
Graph Analysis
Graph analysis empowers our secret management tool to detect unusual behavior and provide visual data insights regarding secret access.
Don’t just take our word for it. Book a demo and witness firsthand the power and simplicity of CloudDefense.AI.
AWS Secret Manager

AWS Secret Manager
AWS secret manager is a widely popular secret management tool that you can incorporate into your workflow and centrally manage all the secrets. Whether you want to retrieve, rotate, or manage your secrets, this tool helps you with everything throughout the secret lifecycle. This tool is quite simple to operate and works well when your development environment and application are part of AWS.
Pros

AWS secret manager centrally stores and manages all the secrets including API keys, credentials, and encryption keys.

Lets you utilize AWS IAM permission policies to effectively govern who can have access to your secrets.

Using AWS Lambda lets you rotate secrets based on a schedule.

You can monitor and audit the usage of your application’s secrets.
Cons

It works at full potential for AWS native applications.

The interface is not well-laid out.
1Password

1Password
Without a doubt, 1Password serves as an obvious choice for a secret management tool as it lets you safeguard the secrets of your global workforce. It is an all-in-one platform through which you can govern secret usage, mitigate any potential secret breaches, and shadow IT activity. This tool has been designed with optimum security measures and integrates seamlessly with your workflow and tools to provide log activity.
Pros

It created a highly secured secret vault to let you securely share passwords among teams.

You get complete visibility and detailed reports on password security posture.

Integrates effortlessly with your IAM infrastructure to secure every sign-in.

Helps mitigate data breaches and curb support tickets. It has a straightforward interface that requires no prior experience.
Cons

This tool is mostly designed to serve small scale businesses.
HashiCorp Vault

HashiCorp Vault
Considered as one of the pioneers of secret management tools in the market, HashiCorp Vault is a top-tier solution that you can utilize to safeguard all the secrets. It is an API-driven solution that effortlessly integrates with existing identities to automate users’ access to secrets. Like every top solution, it maintains granular access control and detailed audit logs to ensure tight control over access.
Pros

It offers fine-grained user access control that allows users and applications to automatically access specific secrets.

HashiCorp Vault can dynamically provide secrets on-demand for various processes.

Automatically rotates secrets to maintain overall secret security posture.

You can easily navigate through its web interface.

The access to secrets is provided on authentication against trusted sources.
Cons

The web UP doesn’t offer all the features.

It is mostly designed to serve large organizations.
Doppler

Doppler
Another widely preferred secret management tool in this list is Doppler. It is a developer-first solution that allows developers to manage, set permission, monitor access and other tasks at scale. It utilizes missing secret detection capability where it automatically identifies and alerts the team member whenever there is a secret missing. However it is the efficient access management that will help you deploy flexible access controls.
Pros

It is quite straightforward to set up and works by introducing secrets as variables.

Doppler offers secret referencing, which eliminates old duplicated secrets and updates them.

Using Slack alerts keeps track of every version of the secret.

Extensibility through the BApp Store allows for additional features via third-party add-ons.
Cons

You can only use it as a managed service.

It might not be feasible for small-sized teams.

Doesn’t come with any SDK for integration.
Bitwarden

Bitwarden
When you want to easily and securely manage your secret, Bitwarden is one secret management solution that should be considered. It is an end-to-end encrypted solution that offers you a TOTP authenticator, event logs, and SSO integration to have complete control over how secrets are accessed. Importantly it is the open-source platform through which you can centrally store all the associated secrets and automate them in the workflow.
Pros

The simple interface and documentation support enable users to deploy quickly.

It allows you to control which device and user can access which secrets.

Eliminates the need for hard coding by sharing and deploying secrets.

Offers a centralized location for storing secrets of different applications.
Cons

To use additional features, you will have to pay extra.
Akeyless

Akeyless
Akeyless is a renowned secret management tool that not only enables you to protect all your digital secrets but also automates the access across your DevOps and cloud platform. This solution can work in both multi-cloud and hybrid environments, enabling seamless secret rotation and managing secret sprawls. A great thing about this solution is that it allows you to share secrets securely and automate certificates.
Pros

It provides a centralized location to securely store all the certificates, API keys, and digital credentials.

You can even securely manage and encrypt your Kubernetes secrets through this platform.

It helps inject a variety of secrets into your application, workload, and servers.

It enables quick onboarding and doesn't require any long process for installation.

It is based on a distributed architecture.
Cons

You will have to spend extra money on additional features and integrations.

Some of the advanced features might not be needed for small-scale organizations.
Azure Key Vault

Azure Key Vault
Organizations running their application on the Azure platform would definitely find Azure Key Vault simpler and more effective while managing and integrating secrets. It provides you with granular control over all the secrets by centrally managing permissions. Since this tool natively integrates with the Azure ecosystems, the developers can easily safeguard all the secrets associated with the application by inventorying them in a single repository.
Pros

Offers seamless and easy integration when the application is associated with Azure services.

This tool acts as a bridge between secrets and applications and ensures that the application has no direct access.

It helps in reducing latency and cope with the global scale by storing the secret in a central storage.

Offers one of the fastest ways to create and import encryption keys.
Cons

The pricing structure is slightly complex due to the different customization options.

Not every developer finds it simple to use.

It lacks some advanced features like secret referencing.
Infisical

Infisical
Designed mostly to cater to SMBs in the industry, Infisical is an open secret management tool that enables you to manage secrets across your team. This platform features secret versioning, point-in-time recovery, secret overrides, secret referencing, and other useful features to safeguard your secrets from being exposed. However, it is the Infisical Radar that makes it more effective as it continuously performs secret scanning and prevents leaking of secrets.
Pros

It offers granular access control and compliance policies to enhance the overall secret security posture.

Offers secret referencing and automates secret integration to prevent secret sprawls.

It helps in generating dynamic secrets, which are really useful for creating access.

Provides high granular access control and allows you to control which user can access which account.
Cons

It doesn’t integrate seamlessly with on-premises installations.

The interface could have been better.
Keeper

Keeper
Keeper is a comprehensive and cloud-based secret management tool that is designed to safeguard infrastructure secrets like database passwords, API key, certificate and access keys. It provides the capability to manage rights and permissions to secrets and also securely share them whenever needed by the team. Using this platform, you can easily automate secret rotation and perform post-rotation processes.
Pros

Provides a centralized location to store all the secrets associated with the application and infrastructure.

It lets you conduct automated secret rotation for different services, RES-based API accounts, and admin accounts.

This solution can scale according to the increase in the number of secrets.

Support a wide range of platforms with complete integration.
Cons

To use additional features, you will have to pay extra.
Conclusion
Secret management has become a need of the hour for most organizations in the world as manual key management is getting complicated with time. Moreover, it is increasingly becoming a key requirement for a secure software development environment.
After thorough research, we have created this list of 10 best secret management tools in 2025, and we are confident this article will help you find the appropriate tool for securely managing all your secrets. Based on our evaluation, CloudDefense.AI serves as the best option for its all-in-one features and functionality. However, you should also evaluate others based on your requirements.







