CCPA
CCPA Compliance: Empowering Privacy and Trust
Privacy must be protected and to maintain that you require CCPA to empower you. CloudDefense.AI is your trusted ally as we don’t just meet CCPA standards; we exceed them. Easily maintain compliance while strengthening your security.
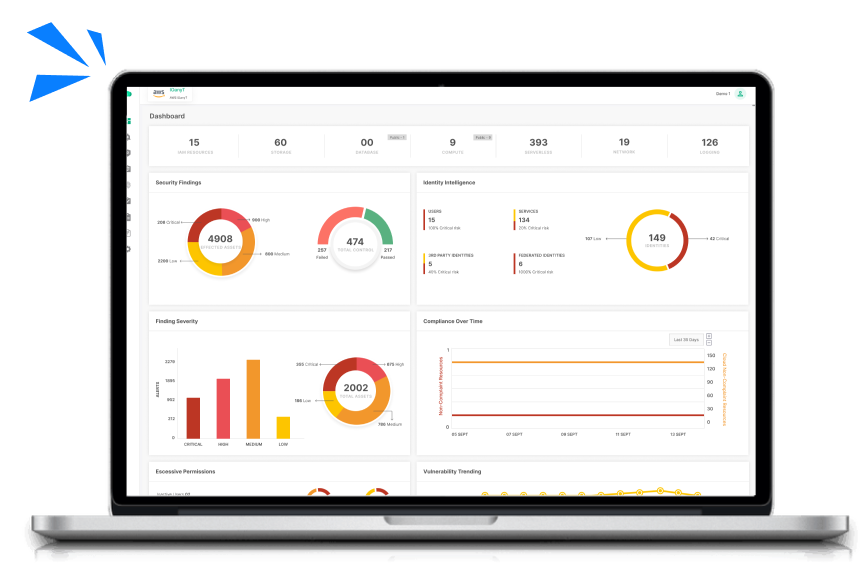
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
EMPOWER YOUR BUSINESS
Protect Consumer Privacy. Achieve CCPA Compliance. Book Your Live Demo Today!
Time is ticking, and every delay in security could mean missed opportunities. CloudDefense.AI’s application security solutions embed protection into every stage of your DevOps pipeline so that you can release updates quickly and confidently. Fast, secure, and effortlessly smooth—just how it should be!

The Open Source Challenge: Ensuring Privacy in Innovation
Open-source technology fuels innovation, but it can also introduce vulnerabilities that compromise consumer data. Ensuring CCPA compliance in an open-source environment requires a solution that understands these unique challenges. CloudDefense.AI helps you leverage the power of open source while protecting consumer privacy and meeting CCPA standards.

Strengthen Your Data Protection with CCPA Compliance
CCPA compliance is more than a regulatory requirement—it’s a commitment to respecting consumer rights and protecting their personal information. But how do you ensure your systems are always ready to meet these rigorous standards? CloudDefense.AI provides a comprehensive platform to manage risks, ensure transparency, and maintain the trust of your customers.
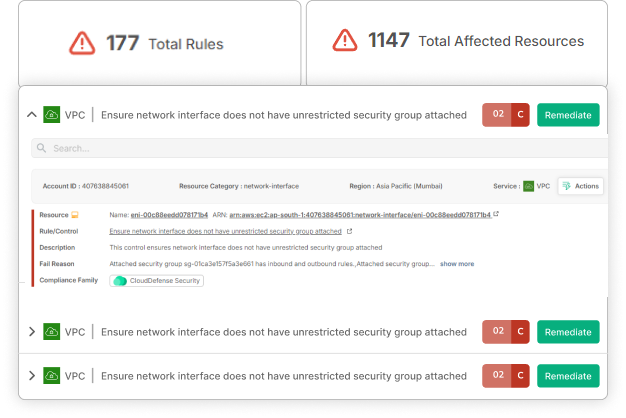
How CloudDefense.AI Keeps You CCPA-Ready
Unified Developer and Admin Platform
Smoothen your compliance efforts with a centralized hub that offers automated remediations, internal audits, and checklist-driven compliance management—all designed to protect consumer data.
Prioritize Critical Updates
Address vulnerabilities that could compromise consumer privacy with a focused approach, ensuring that critical updates are handled promptly and effectively.
Continuous Monitoring for Compliance
Utilize SCA, SAST, and DAST tools to continuously monitor your Software Development Lifecycle for potential CCPA-related issues, ensuring comprehensive data protection.
Smooth Integration for Ongoing Compliance
Maintain real-time compliance by syncing patch management with live repositories, keeping your systems aligned with CCPA regulations and avoiding costly penalties.
Cross-Industry Certification
Achieve compliance across multiple frameworks, including CCPA, HIPAA, GDPR, PCI-DSS, ISO, and SOC 2, with a single, strong solution designed to meet diverse industry needs.
Exceed Consumer and Regulatory Expectations
Protect consumer data from breaches and demonstrate your commitment to privacy, exceeding both consumer and regulatory expectations with CloudDefense.AI’s comprehensive security solutions.
Why CCPA Compliance is Crucial for Your Business
In a world where consumers are increasingly concerned about their privacy, CCPA compliance is your ticket to building trust and maintaining a positive reputation. CloudDefense.AI ensures that your data protection strategies are not just compliant but leading-edge, keeping you ahead of potential threats and ensuring consumer confidence.
Mapping CCPA Requirements to CloudDefense.AI Solutions
Data Privacy and Protection
Our SCA tool integrates CCPA compliance across your entire SDLC, providing superior data protection and ensuring that consumer privacy is maintained at every stage.
Transparency and Consumer Rights
Implement transparent security practices and a strict internal verification processes to uphold consumer rights, avoid fines and maintain trust in your brand.
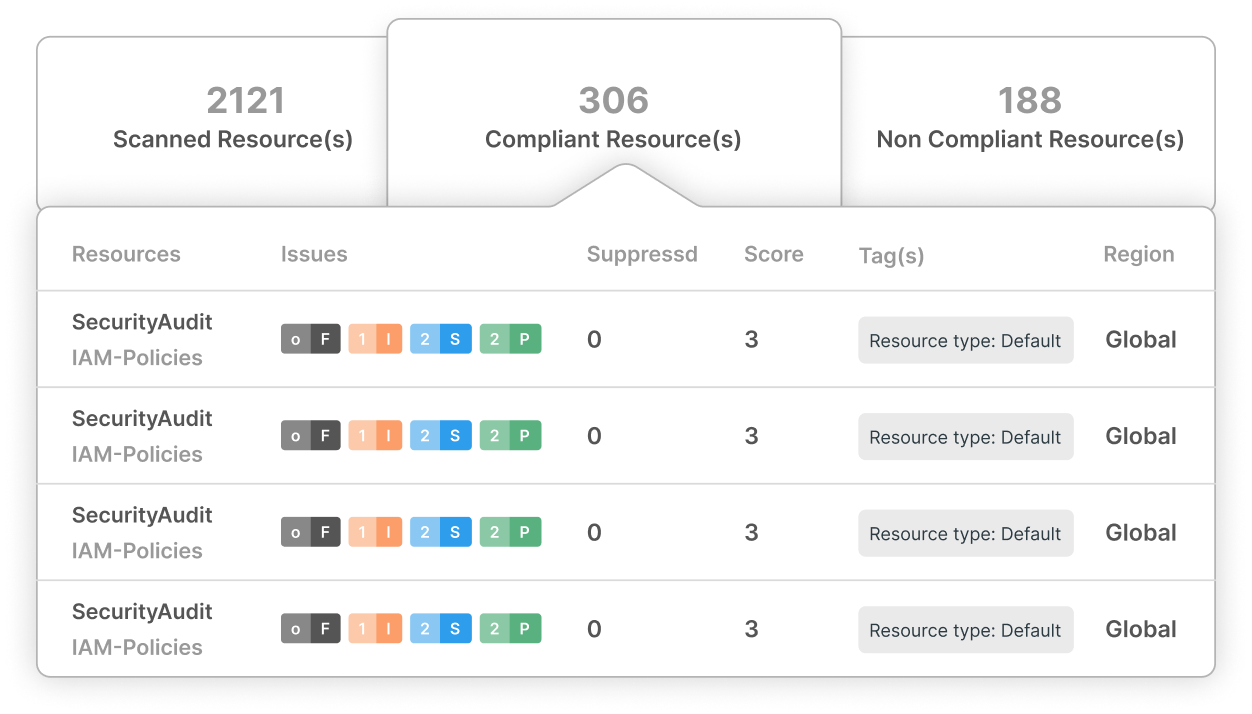
Ready to Protect Consumer Privacy?
Go beyond compliance lead with trust. Schedule a demo with our team today and discover how CloudDefense.AI can help you achieve and maintain CCPA compliance while building stronger relationships with your customers.




