Compliance
Hassle-Free Multi-Cloud Compliance Management
CloudDefense.AI is your one-stop solution for effortless and comprehensive Multi-Cloud Compliance Management. We empower you to maintain automated compliance against industry-standard regulations and benchmarks such as GDPR, PCI, HIPAA, and more.

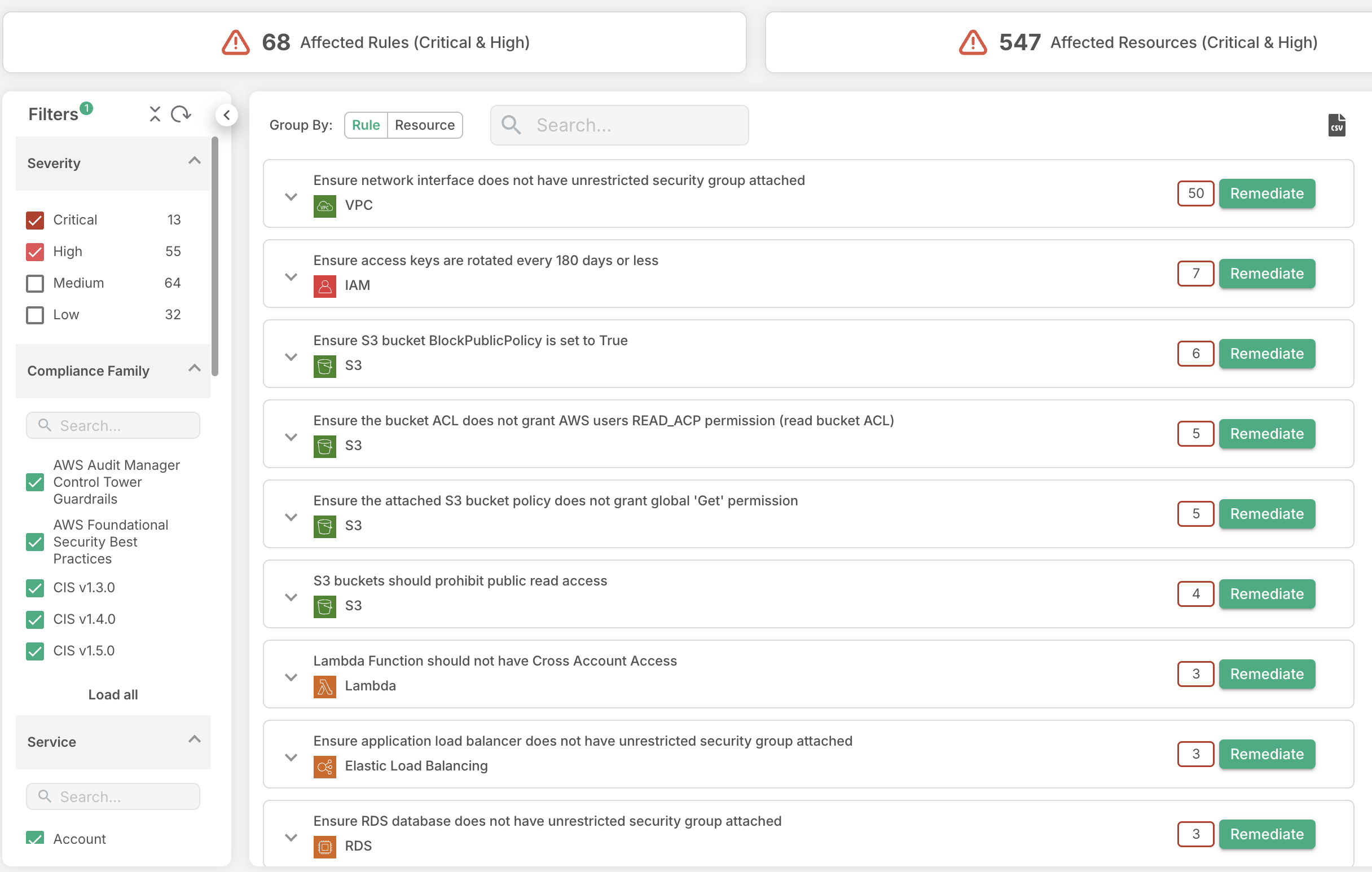
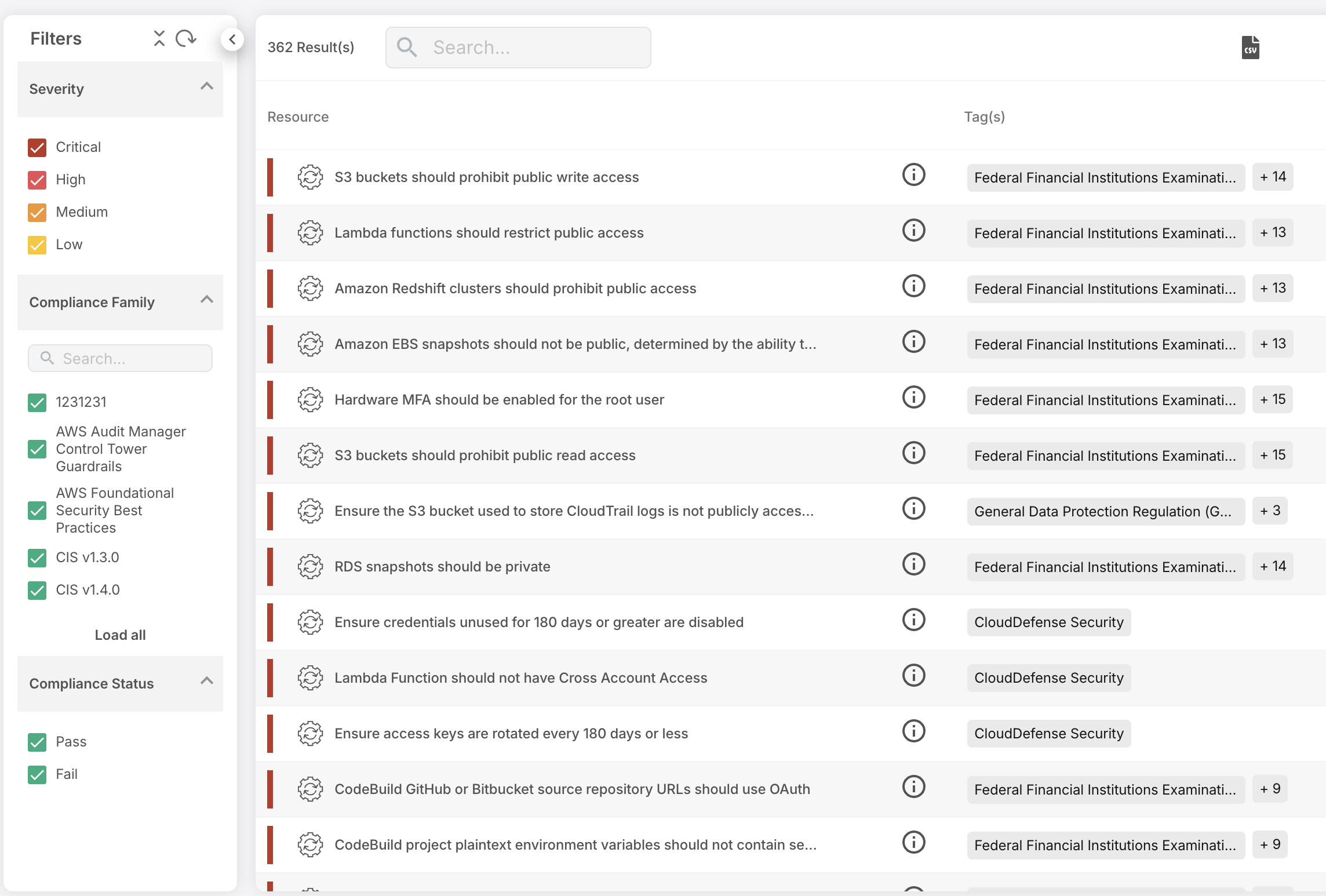
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
SIMPLiFY CoMPLIANCE
Simplify Compliance Across Clouds: Your All-in-One Solution
Effortlessly conduct compliance assessments, receive industry-standard posture scores, and generate confident, comprehensive reports—all easily accessible at your fingertips.

Expertise Right at Your Fingertips
Empower your security teams to effortlessly ensure compliance across complex multi-cloud environments.

Real-time Insights
Access real-time compliance data to empower your teams with the insights needed for audits and reporting.

Instant Audit-Ready Report
Generate comprehensive, audit-ready reports in an instant. Don’t just identify issues, provide you with the precise guidance to fix them.

Diversified and Flexible Reporting
Tailor compliance assessments to your needs. Evaluate compliance posture per framework for various business units or applications.
Our Comprehensive Approach to Compliance Management
Multi-Cloud Visibility and Compliance Enforcement
CloudDefense.AI redefines the landscape of multi-cloud resource management and compliance enforcement. Supporting the top five clouds, it maintains 20+ compliance frameworks, enabling one-click audit-ready reporting and policy enforcement with 300+ pre-built security policies.
Multi-Cloud Insights
Gain real-time insight into all your multi-cloud resources, ensuring comprehensive visibility to monitor and secure your infrastructure effectively.
Wide Cloud Support
CloudDefense.ai covers the world's top clouds like AWS, Azure and GCP, providing versatile security and compliance solutions across various cloud environments.
Compliance Simplified
Effortlessly maintain compliance with 20+ frameworks and customize your own, all while generating one-click audit-ready reports to streamline your security efforts.
Holistic Cloud Asset Management
Gain immediate visibility into your resource utilization, streamline inventory management for ultimate control, and take security to new heights. Our expertise extends across the domains of AWS, Azure, and Google Cloud giving you the tools to not just manage but transform your cloud experience.
Unified Dashboard
Access a single dashboard to seamlessly monitor all your cloud assets, providing a holistic view of their security posture and simplifying management.
Multi-Cloud Support
Extend cloud protection across AWS, Azure and Google Cloud enabling transformational cloud management.
Resource Classification
Leverage API metadata for automatic resource classification, enabling a deeper understanding of your environment and enhancing security posture assessment.
Real-time Risk Insights
Track asset risk in real time, backed by fine-grained audit trail analysis for historical context, simplifying cloud incident analysis and auditing.
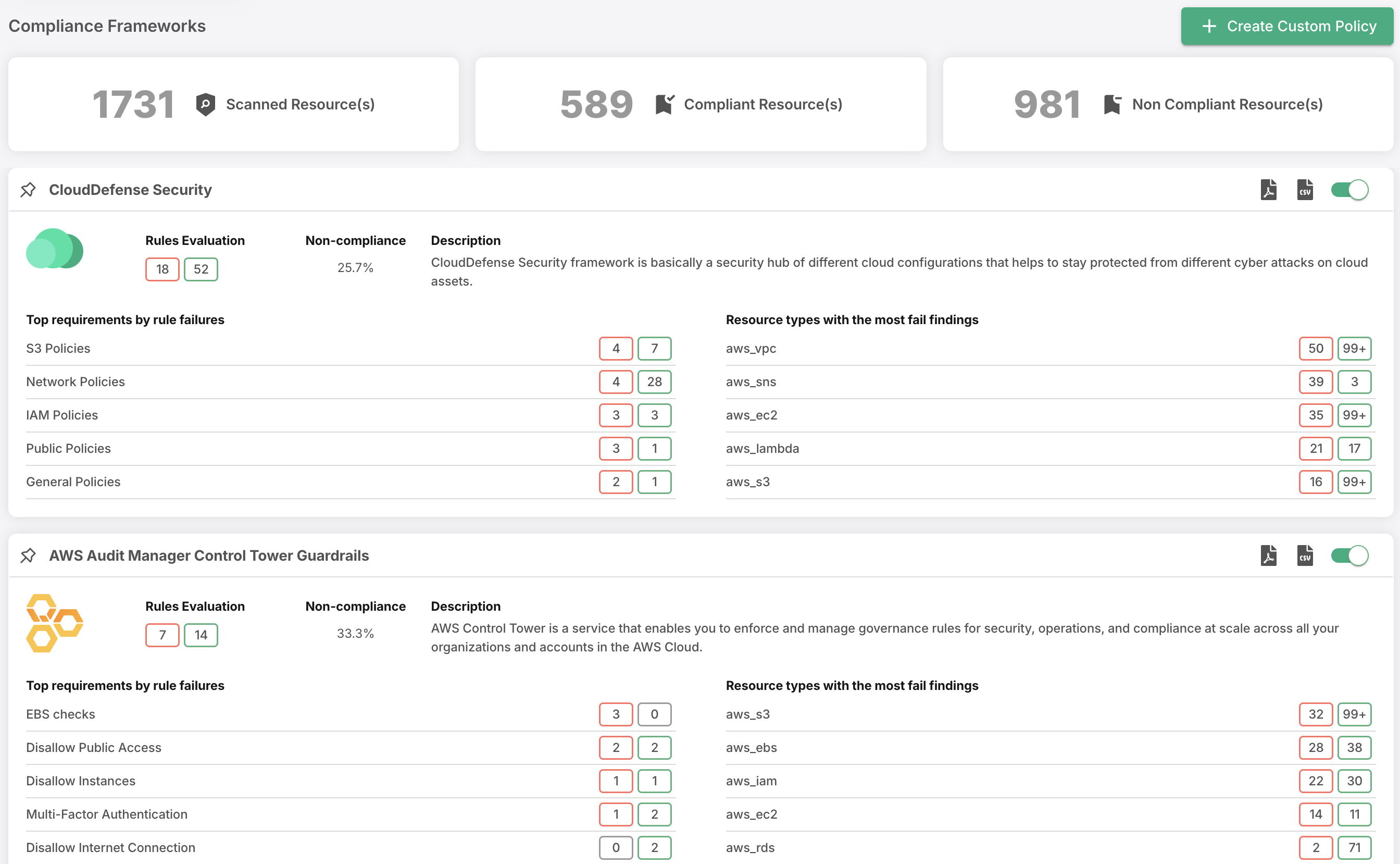
Seamless Compliance Customization
Elevate your compliance management with CloudDefense.AI’s user-friendly framework customization. Tailor compliance frameworks to your unique requirements, leverage templates, and fine-tune controls effortlessly.
Fully Customizable Frameworks
Craft compliance frameworks that suit your exact needs. Choose from templates or start from scratch, adjusting rules, controls, and settings as you see fit.
Fine-Tune Existing Frameworks
Effortlessly make minor adjustments to existing frameworks, combining rules from multiple sources to suit your specific compliance needs.
Rule Customization
Take control by defining your own rules and controls, ensuring a personalized compliance framework that meets your organization's standards.
Seamless User Experience
Experience a user-friendly interface designed for intuitive framework configuration, simplifying the complex process of compliance management.
Automated Remediation Workflows
At CloudDefense.AI, we empower organizations to streamline compliance workflows effortlessly. Our platform seamlessly integrates compliance alerts into existing processes, automating assignments and enabling rapid, contextualized issue remediation to maintain security and compliance.
Seamless Integration
Effortlessly integrate compliance alerts into existing workflows for automatic assignment and processing by relevant teams.
Multi-Channel Alerts
Automatically integrate alerts with ticketing systems like Jira and ServiceNow.
Rapid Risk Remediation
Address potential risks swiftly with rapid reporting and guided, automated remediation to prevent compliance violations and security threats.
Contextual Insights
Benefit from rich contextual information provided with alerts, allowing remediation teams to operate independently and efficiently.

Comprehensive Compliance Reporting Suite
Effortlessly track, customize, and share compliance status and trends, ensuring seamless communication with stakeholders and auditors.
Comprehensive Reporting
Gain insights into compliance posture with detailed reports covering Compliance Status, Checklist, Non-compliant Resources, and Issues.
Customization Capabilities
Tailor reports to your needs, reflecting your unique compliance requirements and goals.
Executive Summaries
Share concise evidence of compliance progress and trends, facilitating clear communication with executives and teams.
PDF Export
Generate polished reports in PDF format for easy distribution and documentation.
Streamlined Compliance Monitoring and Reporting
Generate instant audit reports and access real-time and historical compliance data. Empower resource-constrained teams with effortless continuous monitoring. Stay audit-ready and secure in multi-cloud environments with confidence.
Comprehensive Compliance Support
Simplify compliance adherence with support for 20+ standards, including PCI, HIPAA, GDPR, SOC2, and more.
Instant Audit Reports
Achieve audit readiness at the click of a button. Detailed reports pinpoint violations and offer guidance for swift issue resolution.
Real-Time Insights
Gain valuable real-time and historical compliance data to streamline audits and reporting for robust security.
Ready to see us in action? Schedule a time
to speak with our team!
Spot unknowns sooner and continuously watch for signs of compromise. Take us on a test drive to see for yourself.