Data Protection
The Ultimate Data Protection Platform
Secure your critical data from cyber threats, breaches, and unauthorized access with our cutting-edge security solutions.
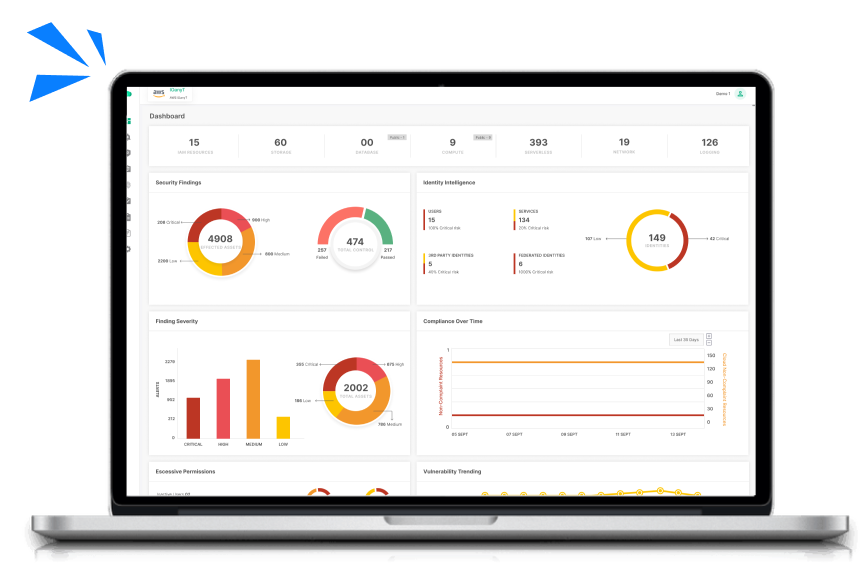
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
EMPOWER YOUR BUSINESS
One Solution, Infinite Cloud Protection: Defend Your Data Everywhere!
Do away with vulnerabilities and safeguard your data with confidence, no matter where it resides or who accesses it. Experience the peace of mind that comes from truly defending your data everywhere.

Multi-Cloud Security
Protect your data across various clouds, ensuring comprehensive protection for public, private, or hybrid cloud environments with CloudDefense.AI.

Real-Time Threat Detection
Stay ahead of threats with CloudDefense’s real-time monitoring, instantly identifying and countering potential security risks for maximum protection.

User-Friendly Interface
Effortlessly manage data security with CloudDefense’s intuitive interface, making robust protection accessible to all, regardless of cybersecurity expertise.
Your Retail Empire is Under Attack
Retail is a battlefield. Every day, cybercriminals target your business, ready to steal your hard-earned revenue and damage your reputation.
The Numbers Don’t Lie!
24%
You’re a Top Target
Retailers face a staggering 24% of all cyberattacks, making you a prime target for hackers.
-$250,000
The Price of Inaction
A single data breach can cost your business anywhere from $100,000 to $250,000. That’s money straight out of your bottom line.
20%
The Growing Threat
E-commerce security incidents have skyrocketed by 20% in just one year. The threat is real, and it’s escalating.
Can you afford to be a Casualty?
Don’t let these statistics become your reality. Protect your business, your customers, and your bottom line with our strong retail and e-commerce security solutions.
Our Comprehensive Approach to Data Protection
Our holistic strategy for data protection combines cutting-edge technology, robust policies, and proactive monitoring to safeguard sensitive data throughout its lifecycle, ensuring data integrity and compliance in today’s evolving digital landscape.
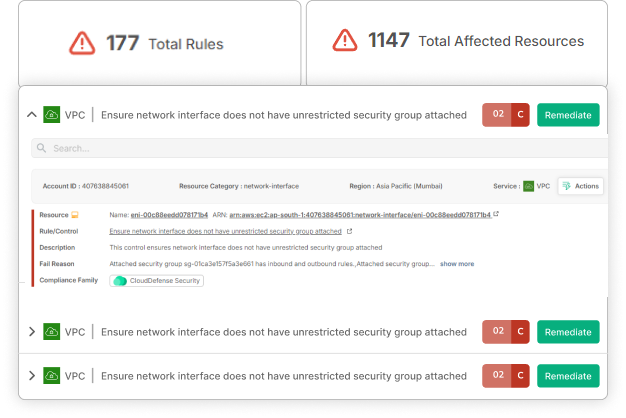
Swift Issue Detection and Recovery
At CloudDefense.AI, we empower businesses with rapid detection and recovery capabilities, transforming them into a proactive minority. Our intelligence-driven approach ensures confident, automated security policy configurations.
Swift Remediation
Instantly identify and remediate breaches, elevating your organization to the elite few capable of resolving security issues within a day.
Intelligence-Driven
Unlike manual security policy configuration, our platform leverages intelligently gathered data, ensuring you operate with unwavering confidence.
Efficiency Redefined
Streamline processes, optimize resources, and minimize downtime through our rapid detection and recovery framework.
Competitive Edge
Join the forefront of proactive security, where we don't just focus on breach occurrence but emphasize recovery and process enhancement for lasting resilience.
Zero Trust, Superior Security Scans
Enhance your data protection with meticulous scans that eliminate trust dependencies, thwart dark web data access, and reinforce intrusion points. Our cutting-edge technology ensures foolproof verification and access segregation.
Trust-Free Security
Eradicate trust-based vulnerabilities, securing your data against dark web threats.
Automated Intrusion Defense
Streamline security by auto-shrinking common intrusion points through multi-repo checks, enhancing protection against breaches.
Transparency and Verification
Demonstrate accountability with internal verifications and segregation of duties, assuring key stakeholders of your data's safety.
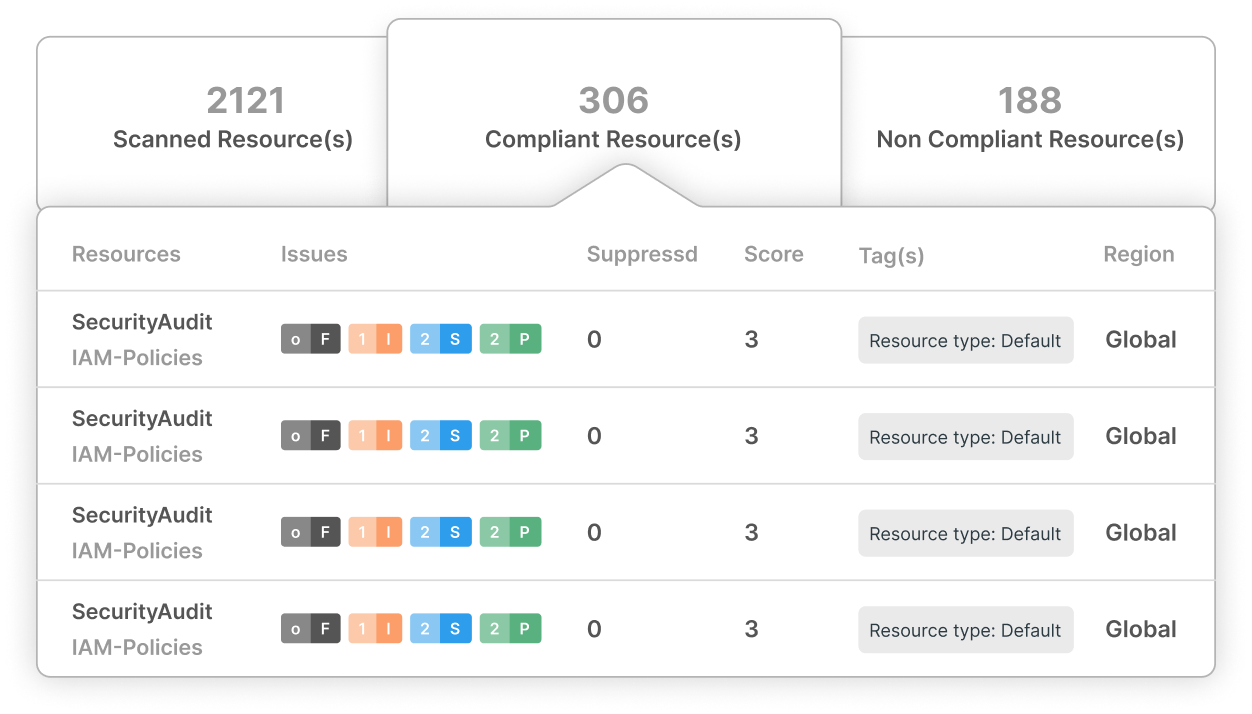
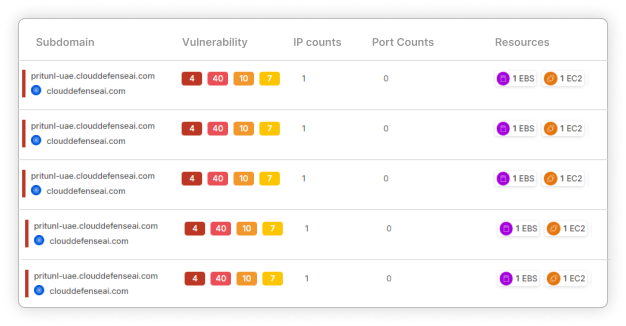
Compliance Management Made Easy
Effortlessly manage regulatory adherence with our user-friendly Airtight Checklists, identifying and rectifying organizational gaps across various key standards
Streamlined Compliance
Effortlessly navigate complex regulations with our Airtight Checklists, ensuring your organization stays in line with PCI DSS, FINRA, NYDFS, FERPA, HIPAA, GDPR, and CCPA.
Data-Driven Insights
Gain actionable insights through a comprehensive, digestible report, enabling informed data-based decisions.
Priority Flagging
Identify and address organizational gaps effectively by prioritizing compliance issues, saving time and resources.
Unmatched Ease
Simplify compliance management with our intuitive interface, making it easy for your team to stay on top of regulatory requirements.
Source-to-Target Security Fortification
At CloudDefense.AI, we safeguard your business from outside-in threats by rigorously auditing third-party applications. Our SAST technology detects and rectifies security breaches between source and target branches, ensuring your insurance sector remains resilient and secure.
Continuous Vigilance
Our SAST constantly monitors for security rule violations, ensuring your data and operations remain secure round the clock.
Source-to-Target Security
We establish a robust security barrier between source and target branches, bolstering your defense against outside-in attacks.
Proactive Security
Stay ahead of potential breaches with our proactive security measures, delivering peace of mind and uninterrupted service.
Ready to see us in action?
Spot unknowns sooner and continuously watch for signs of compromise. Join us for a trial run to experience it firsthand.




