DevSecOps
Secure Every Step of DevOps with CloudDefense.AI
In the rush to innovate and develop apps, don’t let security slip. DevOps teams need to move fast, but they can’t afford to leave vulnerabilities in their wake. With CloudDefense.AI, security becomes part of your DevOps flow. We help you ship secure code faster, so you can focus on what matters most – building great software that your customers love.
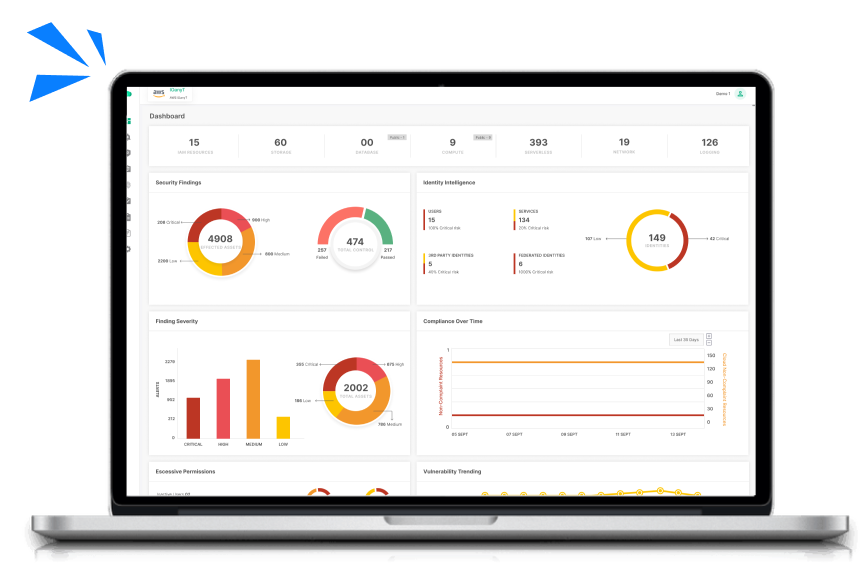
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
EMPOWER YOUR BUSINESS
Speed is Crucial, but So is Security: Accelerate Your DevOps Without Compromising on Security!
Time is ticking, and every delay in security could mean missed opportunities. CloudDefense.AI’s application security solutions embed protection into every stage of your DevOps pipeline so that you can release updates quickly and confidently. Fast, secure, and effortlessly smooth—just how it should be!

Comprehensive Scanning
We leave no stone unturned. Our platform digs deep into your container images and serverless functions, rooting out vulnerabilities, secrets, licensing issues, malware, and misconfigurations.

CI/CD Integration
Why disrupt your workflow? CloudDefense.AI play nice with your favorite CI tools – Jenkins, Azure DevOps, GitLab, you name it. Get actionable insights right within your workflow, making security a natural part of development.

Automated Remediation
Automatically address security issues as they arise, reducing manual effort and accelerating your response time. Our tool fixes problems swiftly, so your team can focus on innovation rather than troubleshooting.
Your Retail Empire is Under Attack
Retail is a battlefield. Every day, cybercriminals target your business, ready to steal your hard-earned revenue and damage your reputation.
The Numbers Don’t Lie!
24%
You’re a Top Target
Retailers face a staggering 24% of all cyberattacks, making you a prime target for hackers.
-$250,000
The Price of Inaction
A single data breach can cost your business anywhere from $100,000 to $250,000. That’s money straight out of your bottom line.
20%
The Growing Threat
E-commerce security incidents have skyrocketed by 20% in just one year. The threat is real, and it’s escalating.
Can you afford to be a Casualty?
Don’t let these statistics become your reality. Protect your business, your customers, and your bottom line with our strong retail and e-commerce security solutions.
Speed Up Your Development While Ensuring Every Line of Code is Secure
Why choose between speed and security? With our tools, you can have both! We’ll keep your DevOps agile and your code safe, so you can zoom ahead without any security speed bumps.
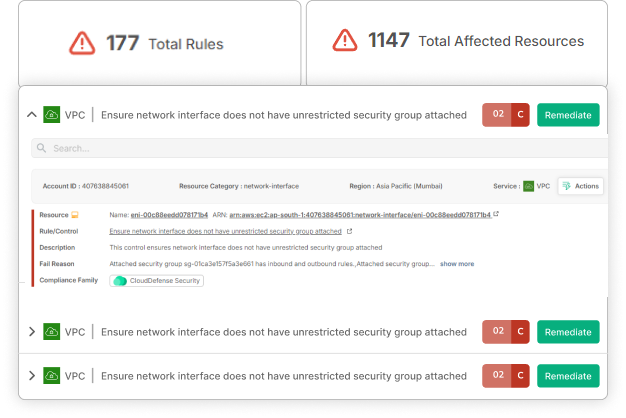
Secure Your End-to-end Development Lifecycle
Comprehensive Language Support
We cover a wide range of programming languages, ensuring your entire codebase is protected, regardless of the tech stack you use.
End-to-End Pipeline Protection
From code commit to deployment, we safeguard every stage of your pipeline, providing continuous security throughout your development lifecycle.
End-to-End Pipeline Protection
From code commit to deployment, we safeguard every stage of your pipeline, providing continuous security throughout your development lifecycle.
Incorporate Multi-Faceted Analysis at Every Stage
Static Application Security Testing (SAST)
Analyze your source code and spot vulnerabilities early before deployment. Our SAST tool provides early detection of security flaws, enabling your team to address issues during development and avoid costly fixes later.
Dynamic Application Security Testing (DAST)
Test your running applications for vulnerabilities that could be exploited in real-time. DAST identifies security weaknesses during runtime, so that your applications remain robust against issues that only manifest during execution.
Third-Party Component Scrutiny
We all use open-source libraries. But do you know what's hiding in them? Our Software Composition Analysis (SCA) keeps a watchful eye on your dependencies, alerting you to any risks lurking in third-party code.
Infrastructure as Code (IaC) Security
Your infrastructure deserves the same security attention as your application code. We scan your IaC templates to catch misconfigurations and security gaps before they make it to production. Because a small mistake can have big consequences in the cloud.
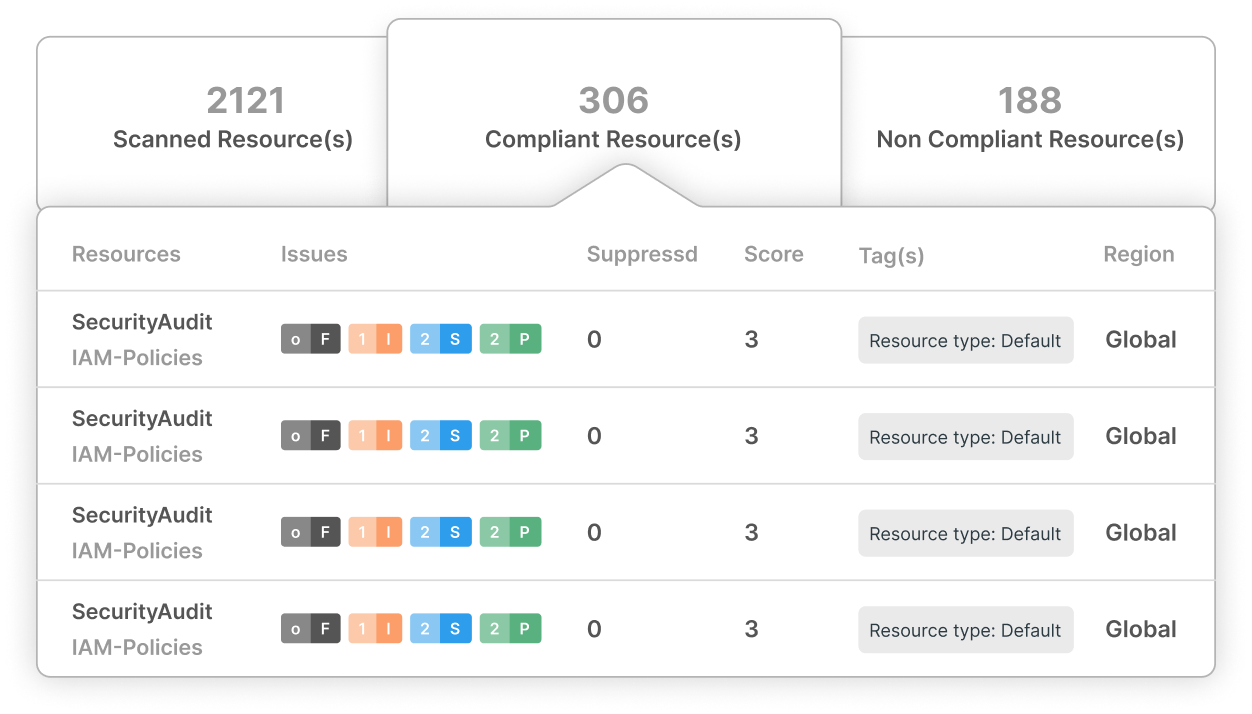
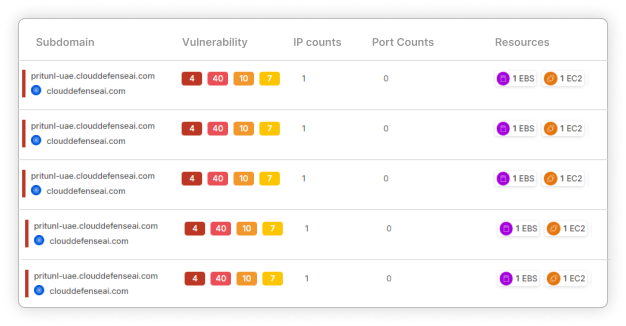
Auto Remediation
Automatic Fixes
Quickly address security vulnerabilities with automated remediation. Our solution automatically spots and fixes vulnerabilities in real time, so your team can focus on innovation without worrying about security hiccups.
Step-by-Step Fix Assistance
Not sure how to tackle a security issue? Our guided fixes walk you through the process, providing clear instructions to ensure you address vulnerabilities correctly and efficiently.
Fits Right into Your Workflow
Our auto-remediation and guidance blend seamlessly into your DevOps setup. This means you can keep your development pace while ensuring that security issues are managed swiftly and effectively.
Experience Unmatched Vulnerability Remediation
Discover how CloudDefense.AI can transform your vulnerability management strategy. Join us for a live demonstration and see the difference in action.




