Enterprise Security
Protect Your Enterprise, Secure Your Future!
From fending off complex cyber threats to maintaining smooth operations, our platform is your enterprise’s first line of defense. With cutting-edge threat detection, continuous monitoring, and swift response mechanisms, we enable you to build trust, protect your assets, and sustain your business continuity.
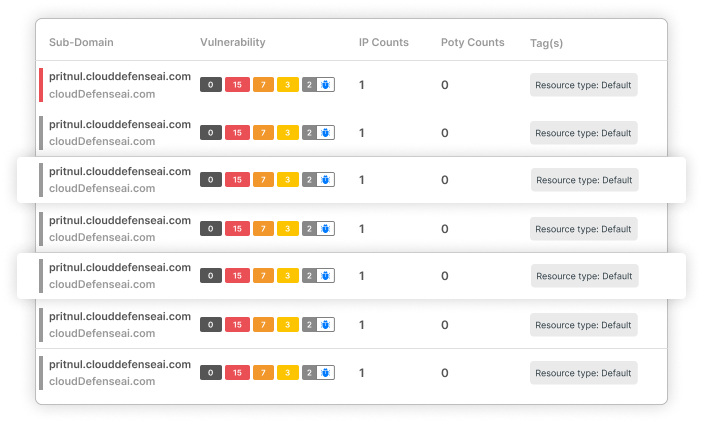
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
Elevate Your Operations
Defend Your Business, Elevate Your Operations: Total Visibility and Control of Your Enterprise Systems
Data breaches? Network vulnerabilities? Ransomware attacks? Say goodbye to the days of uncertainty. Our platform provides an all-encompassing view of your entire enterprise ecosystem, from internal databases to customer-facing applications. Detect vulnerabilities, rectify misconfigurations, and secure every aspect of your infrastructure—all within a single, powerful solution!

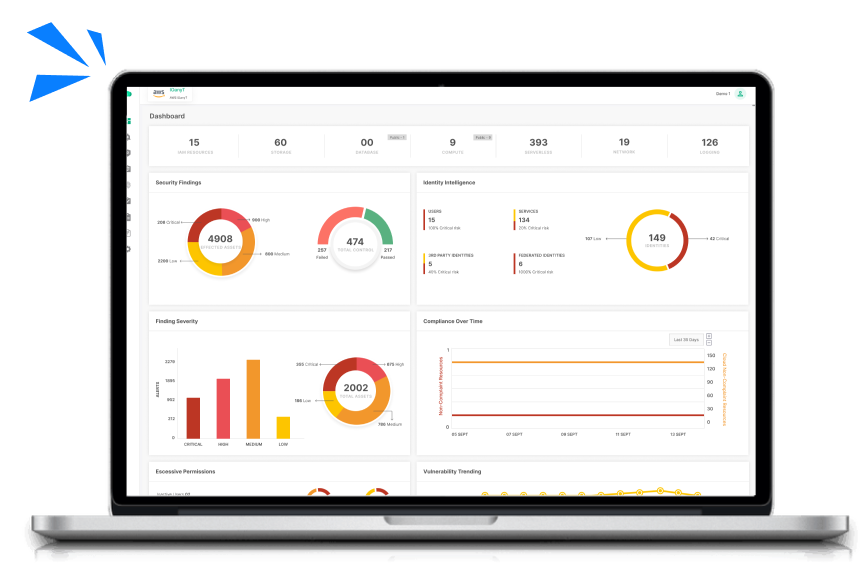
Gain Full Control Over Your Enterprise’s Cyber Landscape
Understand your entire IT environment without disruptions. Discover how each system, technology, and process integrates to drive your operations, from backend processes to client interactions. Gain actionable insights to optimize performance and enhance security.

Eliminate IT Operational Bottlenecks
Identify and remove inefficiencies that impede business growth. Address issues like slow application performance, data fragmentation, or outdated technology. Implement solutions that streamline operations and enhance customer satisfaction.

Protect Your Business from Cyber Threats
Safeguard your critical business data and intellectual property. Identify potential risks in your systems, processes, and personnel. Implement robust security measures to prevent data breaches, unauthorized access, and cyberattacks.
Your Enterprise Is Under Siege!
Your business faces relentless cyber threats aiming to disrupt operations and compromise sensitive information. The stakes have never been higher!
The Numbers Don’t Lie!
$4.45 million.
The average cost of a data breach in 2023 was $4.45 million
600%
Supply chain attacks surged by 600% in 2022
130 Security Breaches
Enterprises faced an average of 130 security breaches annually.
Can You Afford to Be the Next Victim?
Don’t let these risks become your reality. Protect your enterprise, your customers, and your reputation with our advanced cybersecurity solutions.
With CloudDefense.AI…
End Security Worries and Focus on What Matters!
Tired of battling security threats while trying to run your business?
Most enterprises struggle with complex security configurations, leaving them vulnerable and overwhelmed. CloudDefense.AI simplifies your cybersecurity, empowering you to resolve vulnerabilities and prevent breaches with unmatched efficiency!
Here's how we turn security into a competitive advantage:
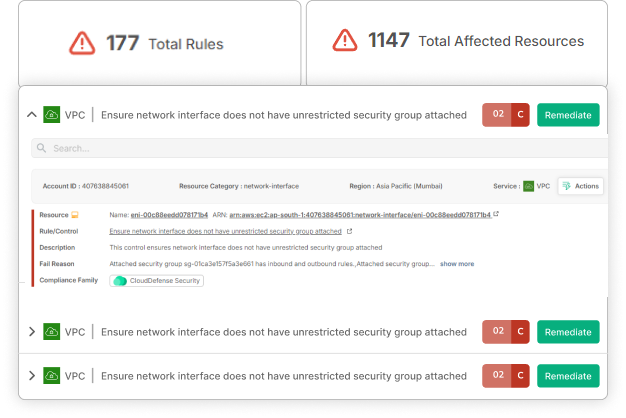
From Complexity to Clarity:
Effortless Integration
Say goodbye to cumbersome setups! We automate your security processes, making protection seamless.
Dual-Layer Defense
Our sophisticated scanner handles both cyber threats and regulatory compliance, ensuring you stay ahead of potential risks.
Rapid Resolution
No cybersecurity expertise is required! Smart diagnostics automatically identify and fix vulnerabilities.
Get Strategic, Not Overwhelmed by Data
Simplified Reporting
Forget the data overload. Receive concise, actionable reports that help you make informed decisions.
Streamlined Compliance
Our comprehensive compliance tools expose risks and prioritize tasks across your teams.
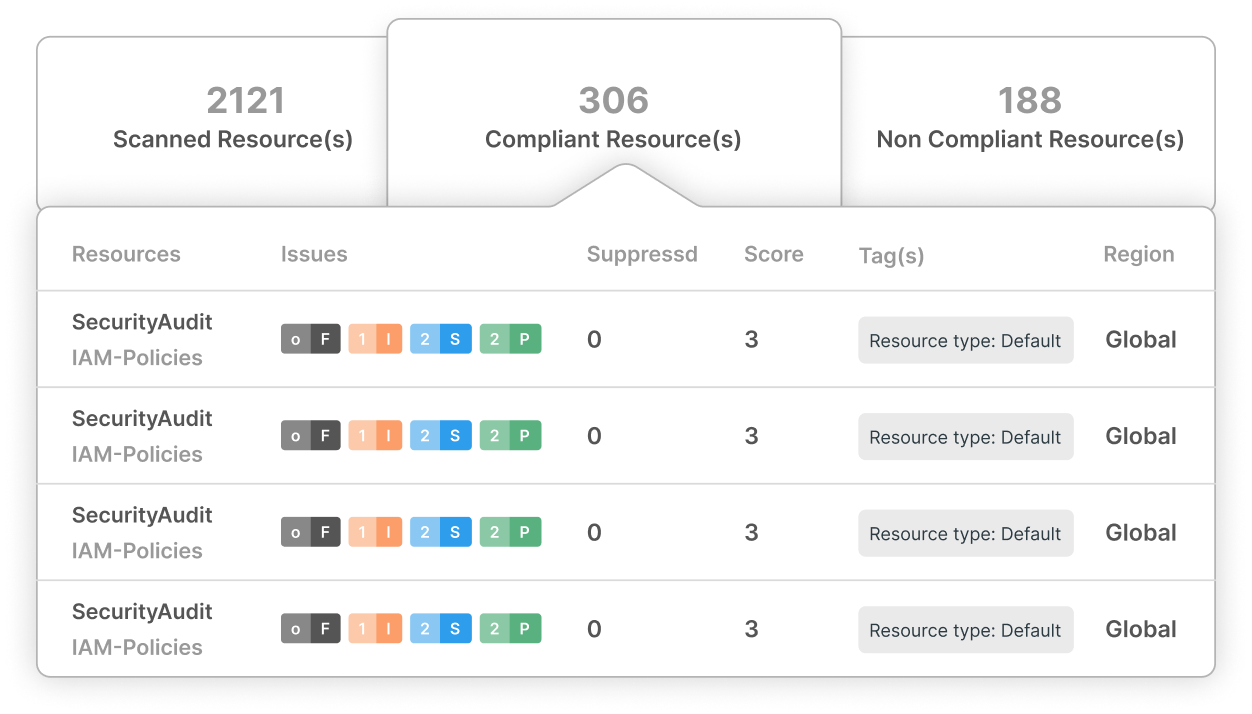
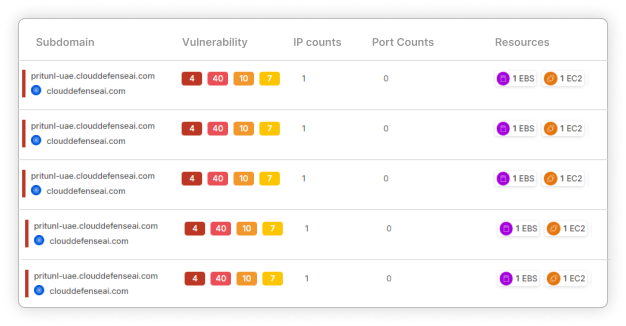
Security Customized for Today’s Enterprises:
Agile and Scalable
We understand the demands of modern businesses. CloudDefense.AI SAST continuously protects your digital infrastructure.
Vendor Security
External risks are real. We monitor all third-party interactions, ensuring comprehensive protection.
Beyond Security, It’s Business Excellence:
Proactive Risk Management
We simplify risk management and compliance to keep your business running smoothly.
Expert Support
Our team provides best practices and ongoing guidance to ensure your security strategy is effective and evolving.