As software development practices keep evolving, keeping track of project dependencies can feel like navigating through unexplored territory. The more complicated your projects get, the trickier it becomes to manage all those moving parts–leading to possible security issues, compliance headaches, and operational snags.
That’s where the Software Bill of Materials (SBOM) comes to the rescue! In this blog post, we will demystify the complexities surrounding SBOM and explore the why, the how, the steps of generating SBOM in GitHub Actions, and the impact of seamlessly integrating SBOM with GitHub workflow, transforming the way you approach security in your code.
What is a Software Bill of Materials (SBOM)?
A Software Bill of Materials (SBOM) is a comprehensive list detailing the components and dependencies of a software application. It serves as a structured inventory, providing information on open-source and third-party components, libraries, and frameworks used in the software’s development. The SBOM tells you exactly what’s inside the software, making it easier to understand, keep track of, and manage. It’s like a transparency label for software, helping people know what’s in it and ensuring everything is up-to-date, compliant, and secure.
To put it simply, think of the SBOM as your project’s ingredient list. It’s like knowing exactly what goes into your software recipe—the components, their versions, and how they depend on each other. As your projects get fancier, the SBOM becomes your trusty map, helping you navigate the tricky sides of dependencies.
Open Source Tools for Generating SBOMs
Several open-source tools are available for generating Software Bill of Materials (SBOMs), catering to various ecosystems and programming languages. The choice of a specific tool often depends on the development environment and the type of software being analyzed. Here are some popular SBOM tools that cater to different ecosystems:
1. Tern (Github Repository)
Description: Tern is an inspection tool to help you understand the contents of a container image. It generates SBOMs for container images by analyzing the software packages installed within the image.
2. CycloneDX: (GitHub Repository)
Description: CycloneDX is a lightweight SBOM standard designed for use in application security contexts and supply chain component analysis. It supports multiple serialization formats.
3. SWID Generator (GitHub Repository)
Description: The Software Identification (SWID) Tag Generator creates SWID tags based on the National Telecommunications and Information Administration (NTIA) guidelines. SWID tags are a component of an SBOM.
4. FOSSology (GitHub Repository)
Description: FOSSology is an open-source license compliance software system and toolkit. It can be used to scan a software package and generate SPDX (Software Package Data Exchange) files, which are a form of SBOM.
5. Ninka (GitHub Repository)
Description: Ninka is a lightweight license identification tool for source code. While it focuses on license identification, the generated information can be part of an SBOM.
6. SW360 (GitHub Repository)
Description: SW360 is an open-source application to manage the software components, licenses, and obligations that are part of your software projects.
7. Kubernetes BOM Tool (GitHub Repository)
Description: The Kubernetes BOM tool is used for promoting container images across different Kubernetes clusters. It can also generate SBOMs for container images, providing visibility into the components used in Kubernetes environments.
8. Spdx-sbom-generator (GitHub Repository)
Description: This is a tool developed by SPDX (Software Package Data Exchange) to generate Software Bill of Materials (SBOM) documents in SPDX format. It’s designed to assist in creating standardized SBOMs for open-source software.
Integration of Vulnerability Data with SBOMs
As the GitHub SBOM roadmap advances, the integration of vulnerability data emerges as a crucial element in enhancing software security. The SPDX format, instrumental in supporting diverse data formats, lays the foundation for this evolution. Going beyond mere package mapping, the next frontier involves continuous assessment of SBOMs against sophisticated intelligence sources.
The Vulnerability Exploitability eXchange (VEX) stands out as a potential game-changer. By scanning VEX documents accompanying SBOMs, users gain insights not only into the presence of vulnerabilities but also into exploitability and criticality. This integration could also address concerns about ‘false positives,’ a common deterrent for software suppliers in sharing SBOMs.
While GitHub remains tight-lipped about specific VEX support, the community’s enthusiasm around VEX suggests a promising avenue for reducing noise and enhancing the effectiveness of SBOMs in bolstering software security.
GitHub Plans CodeQL Management Update
In tandem with the expansion of SBOM capabilities, GitHub users have expressed the need for improved documentation and training. To enhance GitHub’s native security features, users have highlighted some challenges in setting up alerts for secret scanning.
While GitHub’s current secret scanning detects sensitive information, the lack of intuitive alert configurations limits its effectiveness.
Addressing this concern, GitHub plans to introduce quality-of-life updates, including enhanced alert functionalities for secret scanning. Additionally, users anticipate organizational-level management for CodeQL, GitHub’s code-scanning tool. Presently, enabling CodeQL across multiple repositories demands manual activation in each one, posing a significant hurdle for organizations with extensive codebases.
GitHub aims to streamline this process by introducing a bulk code scanning feature in the coming months. These advancements align with GitHub’s commitment to fortifying security measures and simplifying code analysis across diverse projects and repositories.
Generate an SBOM in GitHub Actions
Generating an SBOM in GitHub Actions involves using a combination of tools and scripts to analyze your project’s dependencies and produce the necessary SBOM file.
Here is a basic example using CycloneDX as the SBOM format and GitHub Actions for automation. This example assumes a Node.js project, but you can adapt it for other languages or build systems.
Creating a GitHub Actions Workflow
Create a file named .github/workflows/sbom.yml in your repository with the following content:
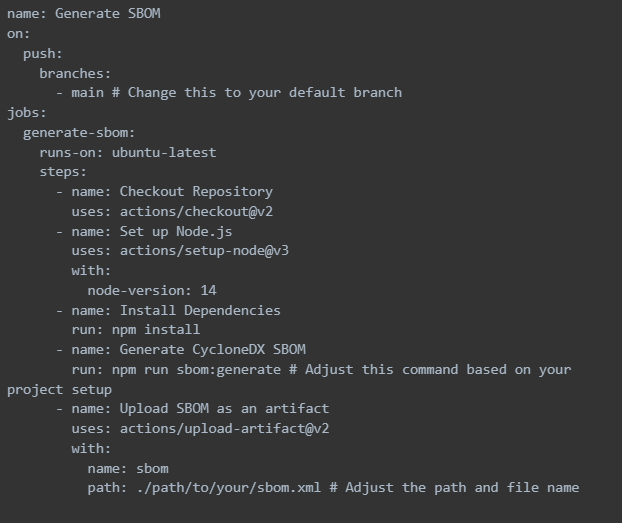
Add SBOM Generation Script
In your project, add a script to generate the CycloneDX SBOM. This could be part of your existing build scripts or a dedicated script. For example, in a Node.js project, you might add a script in your package.json file:
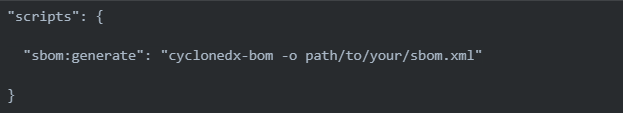
Make sure to adjust the command based on the tools you use for generating the SBOM.
Commit and Push Changes
Commit the changes to your repository, including the new GitHub Actions workflow and any necessary scripts.
Run the Workflow
Push your changes to GitHub, and the GitHub Actions workflow will automatically run. The SBOM will be generated and uploaded as an artifact.
Access SBOM Artifact
Once the workflow completes, you can access the generated SBOM artifact. On your GitHub repository, go to the “Actions” tab, find the workflow run, and click on it. In the run details, you should see the “Artifacts” section where you can download the generated SBOM file.
FAQ
What is the primary purpose of an SBOM?
An SBOM (Software Bill of Materials) provides a comprehensive and structured list of components and dependencies used in a piece of software, enhancing transparency and aiding in supply chain management, security, and compliance.
How do I create an SBOM file?
Creating a Software Bill of Materials (SBOM) involves identifying and documenting all software components, including third-party libraries and dependencies. Key steps include listing components, documenting version information, capturing licensing details, and using SBOM generation tools like CycloneDX or FOSSology.
Integration into build processes ensures consistent and automated SBOM creation. The process enhances supply chain transparency, aids in vulnerability management, facilitates compliance, and contributes to effective incident response by providing a comprehensive inventory of software elements and their details.
How does SBOM contribute to cybersecurity?
SBOM enhances cybersecurity by improving visibility into software supply chains. It helps organizations identify and address vulnerabilities, track open-source components, and respond quickly to security threats, ultimately improving the overall security posture of software applications.
Conclusion
Syncing your SBOM in GitHub Actions is akin to making your code extra safe. It’s not just about ticking compliance boxes; it’s about boosting your software’s transparency and security.
Why does it matter? You can manage your software supplies better, stay on the right side of regulations, and most importantly, keep your code castle well-guarded. So, if you have the whole “building robust and secure software” goal, relying on the SBOM-GitHub Actions bandwagon is the way to go. It’s not just a trend; it’s a smart move in the game of code-fortification.







