Government Cybersecurity
Protect Your Nation, Protect Your Citizens!
From preventing cyber espionage and data breaches to ensuring uninterrupted public services, our platform is your ultimate defense. With advanced threat detection, real-time monitoring, and rapid response capabilities, we empower you to build trust, ensure public safety, and uphold the integrity of your government operations.
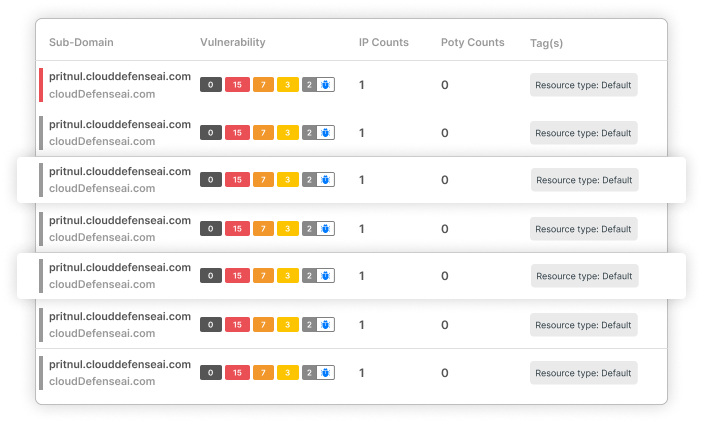
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
EMPOWER YOUR BUSINESS
Protect Your Infrastructure, Empower Your Governance: Complete Visibility and Control of Your Government Systems
Data breaches? Critical infrastructure vulnerabilities? Cyber-attacks? Gone are the days of not knowing what to do Our platform gives you a comprehensive view of your entire government ecosystem, from digital records to public service portals. Identify vulnerabilities, eliminate misconfigurations, and secure every touchpoint—all on one powerful platform!

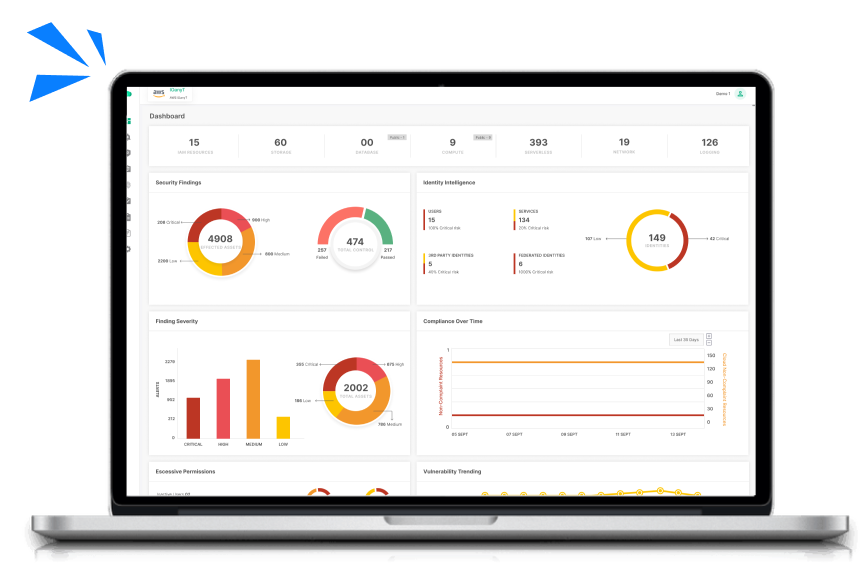
See Every Corner of Your Government’s Cyber Infrastructure
Understand your entire governmental infrastructure without disruptions. Uncover all systems, technologies, and processes involved in running your operations, from citizen services to internal communications. Gain deep insights into how every part works together to optimize efficiency.

Prevent IT Operational Bottlenecks
Identify and eliminate inefficiencies that hinder governance. Spot issues like slow service delivery, data siloing, or outdated systems. Implement solutions to streamline operations and enhance citizen satisfaction.

Protect Your Government from Threats
Secure your valuable government data and public information. Identify potential vulnerabilities in your systems, processes, and personnel. Implement strict security measures to prevent cyber espionage, data theft, and system breaches.
Your Government Is Under Attack
Governance is a battlefield. Every day, cybercriminals target your systems, aiming to disrupt public services and undermine national security.
The Numbers Don’t Lie!
1661 Attacks
Cyberattacks on the rise
Government organizations experienced an average of 1661 cyberattacks per week in 2022, a 46% increase from the previous year.
60%
Ransomware, a major threat
Ransomware attacks on government organizations increased by 60% between 2022 and 2023.
4%
Underfunded security
On average, government agencies allocate only 4% of their IT budgets to cybersecurity, falling short of industry standards.
Can you afford to be a Casualty?
Don’t let these statistics become your reality. Protect your government, your citizens, and your national security with our state-of-the-art cybersecurity solutions.
With CloudDefense.AI…
Stop Security Headaches and Start Governing Confidently!
Tired of chasing down security threats while critical public services are at risk?
Most government agencies spend countless hours manually configuring security, leaving them exposed and overwhelmed. CloudDefense.AI changes the game, empowering you to join the elite countries in the world that can fix vulnerabilities and breaches within a DAY!
Here's how we turn security into a competitive advantage:
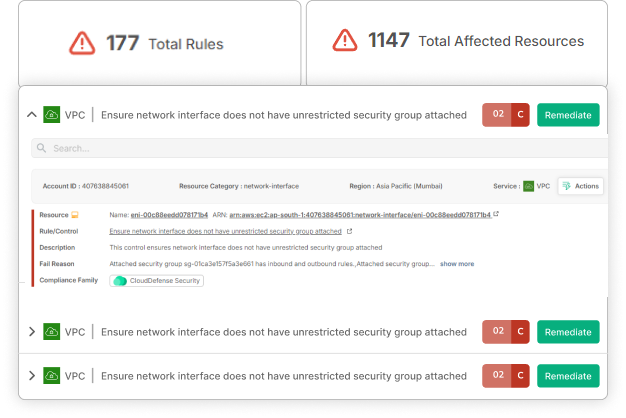
From Chaos to Control
Effortless Setup
Ditch the complex configurations! We automate everything, making security painless.
Double-Edged Protection
Our battle-tested scanner tackles both threats and code compliance, keeping you ahead of the curve.
Fix It Fast
No security expertise is needed! Smart suggestion trees pinpoint and resolve issues automatically
Get Smarter, Not Buried in Data:
Goodbye Report Overload
Forget endless reports. Get one, easy-to-understand report with actionable insights.
Compliance Made Simple
Airtight compliance checklists expose vulnerabilities and prioritize tasks across your entire team.
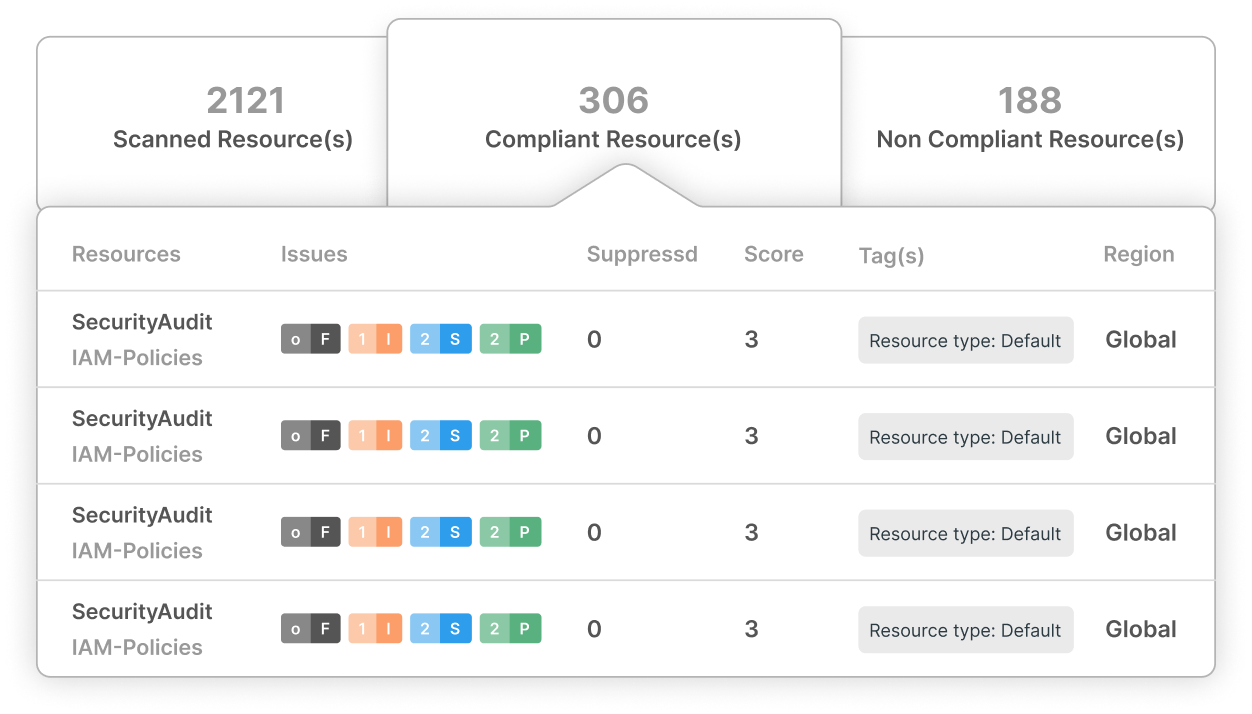
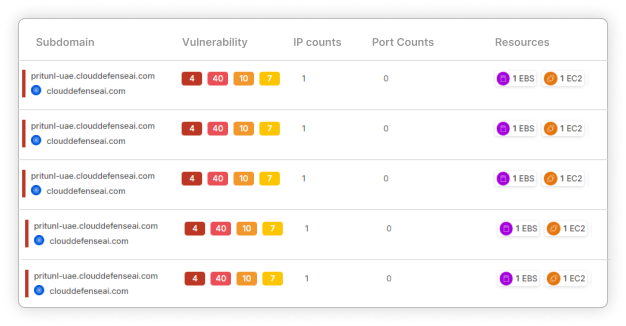
Security Built for Today’s Modern Governments
Agile and Adaptable
We understand the complexities of modern government environments. CloudDefense.AI SAST continuously protects your digital infrastructure.
Third-Party Protection
External threats are real. We constantly monitor all third-party connections, ensuring total security.
More Than Just Security, It's Governance Success
Risk Management Made Easy
We help you manage risks and maintain compliance with ease.
Expert Guidance
Our team of specialists provides best practices and ongoing support to ensure your security journey is a smooth ride.