How It Works
CloudDefense.AI is your single point of control providing a holistic view of threats and mitigating complexity. Our goal is to reduce the complexity of a large tool stack and allow security teams to focus on fixing vulnerabilities. We don’t replace your security tools, we make them better.
Our technology has inbuilt systems that flag keys based on pre-defined rules.
Advanced vulnerability dataset that’s richer than NVD
Fully Audited for Critical Use at Scalein Vendor Systems
From the GDPR to the HIPAA, data privacy authorities assess your Third Party Risk Management (TPRM) practices after a breach — lack of due diligence can be considered ‘wilful negligence’ of data protection. You need a strong AppSec that comes SOC II validated out-of-the-box for security: with CloudDefense.AI, critically cover your enterprise-wide applications, without adding risks to your data or compliance:
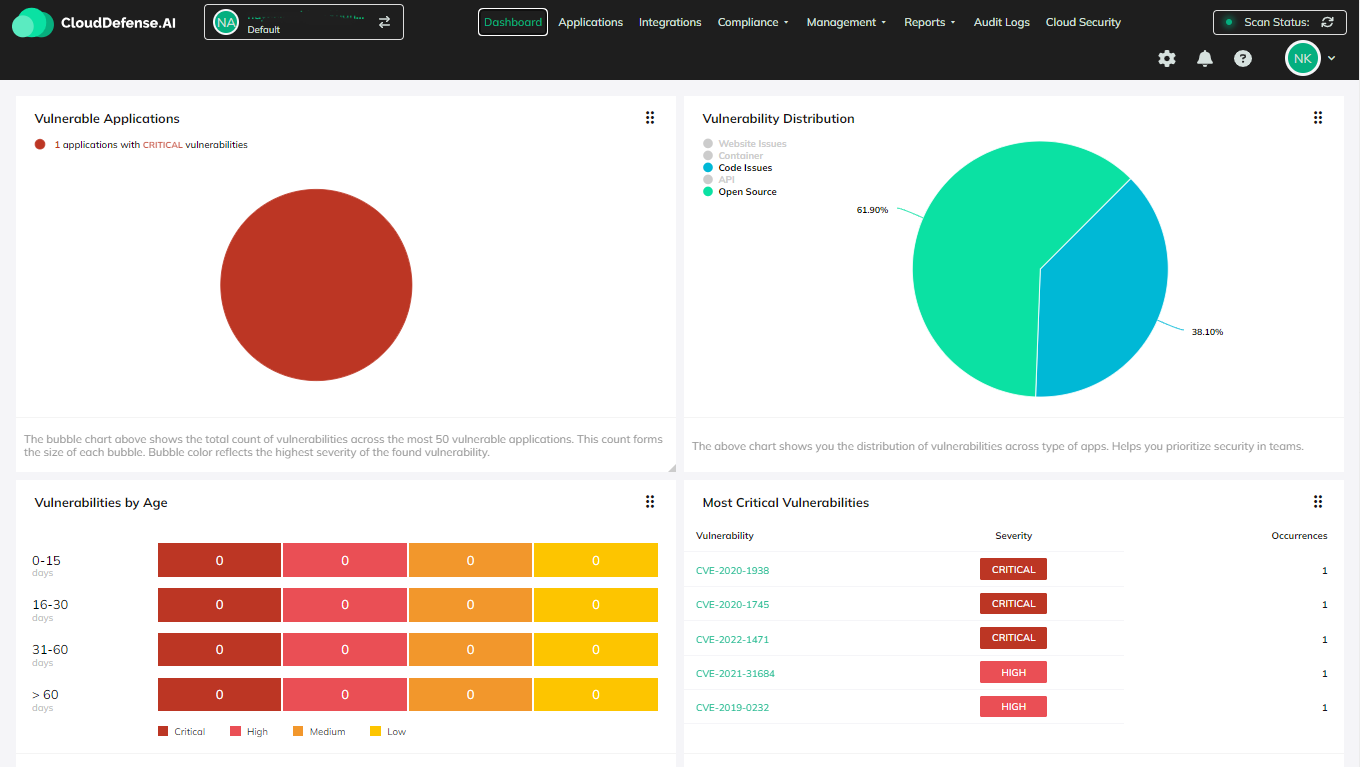
How CloudDefense.AI’s Data Security Platform
Gets and Keeps You Compliance-Ready
Comprehensive coverage
CloudDefense performs automated scans of an application’s codebase, including related artifacts to identify all open source components, their license compliance data, and any security vulnerabilities.
Code Review
Our tool helps in the early detection of code vulnerabilities and minimizes the risk of exposure along with the cost of debugging and fixing at a later stage. We do not store any code anywhere in our system.
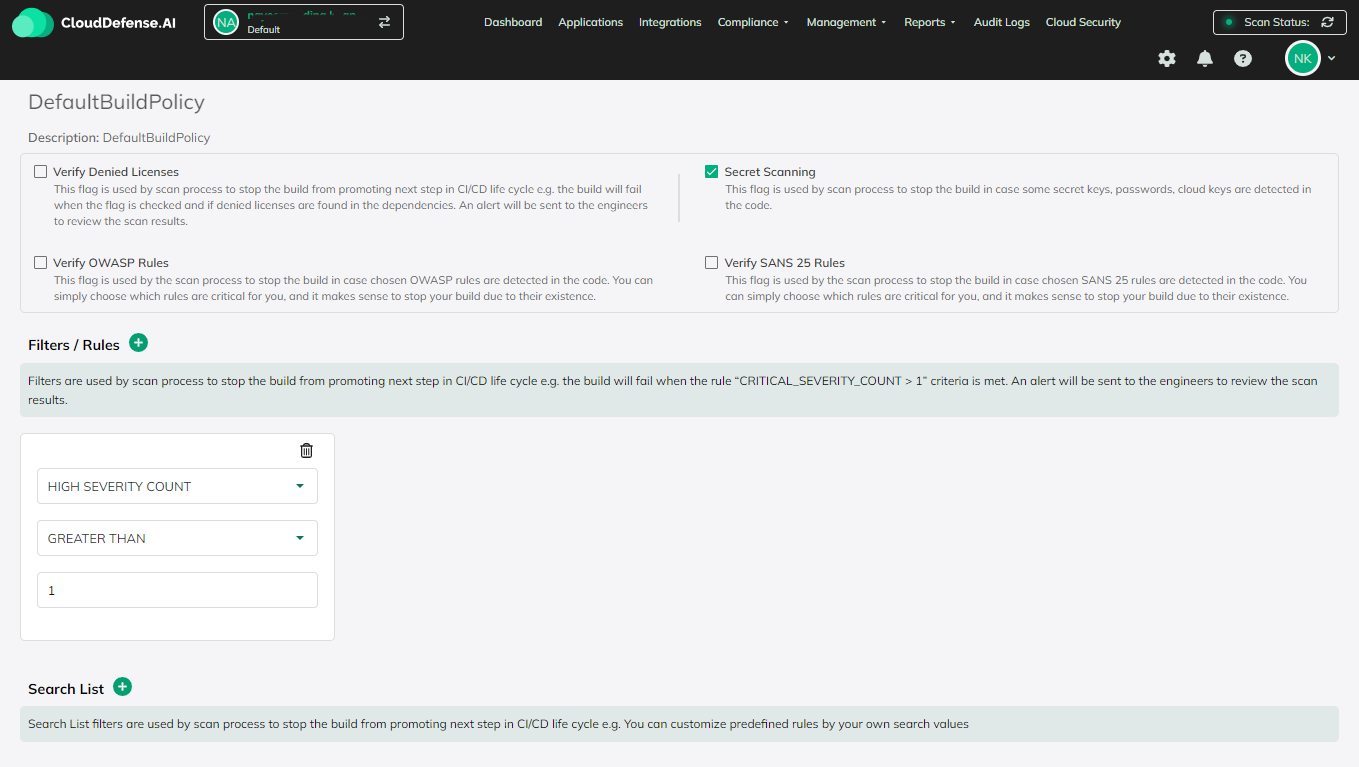
Prevent all secret keys
Customize rules based on your
policies and application needs.
In case a rule is violated, the build breaks, and a notification is generated. This can initiate a ticket creation in Jira.
Find vulnerabilities
CloudDefense helps discover a wide range of vulnerabilities such as input/output validation issues which you can find, prioritize, and assign to developers. It can be integrated with any build system of your choice.
Analyze APIs
Our simplified agent can analyze APIs on OWASP Top 10 using a simple command. It can be integrated as part of your development process so that the dev team benefits from continuous security.
Centralized Reports
To avoid preventable PII breaches suchCloudDefense provides a single pane of glass centralized reporting and visibility for Executives, Managers, and Developers for SCA, SAST, DAST, AP, Secrets and Containers vulnerabilities, and health checks.as experienced by Equifax.
Prevent new vulnerabilities from passing through the build process
20% of enterprise software companies that have adopted SAST into their DevSecOps have reduced vulnerabilities by 26%.

Easy for developers Integrated security in seconds
We’ve made it easy to integrate our platform into your existing tool chains. Whether you work with Java, Python, Rust, or JS instantly scan for vulnerabilities in your dependencies.
CI / CD

CLOUD
CONTAINER

TOOLS




