With cybercrimes on the rise, organizations of all sizes require an incident response plan that will act as a guidebook during a cyberattack. None of the organizations are fully protected against cyberattacks.
In September 2021, hackers were able to expose the personal data of 53 million T-Mobile customers, and the organization faced many consequences. So, it follows that every organization requires an incident response plan; it helps the security team minimize the impact of the attack and recover.
However, to stay ahead of the modern cyberattack, organizations need to ditch their old cybersecurity incident response plan or CSIRP and formulate a new one. This guide will help you in the process of creating a cybersecurity incident response plan and will provide other information to improve your security team’s incident response.
What is an Incident Response Plan?
An incident response plan is a set of instructions that demonstrates the steps a security team needs to follow to identify, respond, and minimize a cyberattack.
From addressing data breaches, service outages, and DDoS to severe data crimes like malware outbreaks, incident response plans are utilized by organizations to handle numerous issues.
The incident response plan is often referred to as an emergency management plan or incident management plan, as it provides guidelines for responding to different security incidents.
The primary aim of the incident response plan in cyber security is to curb the further impact of cyber incidents, enable organized response, and ensure effective restoration of business workflow.
Every organization creates this cyber incident response plan template at the earliest and it includes all the guidelines that everyone needs to follow during an incident. It is highly useful for every member of the organization because it contains numerous guidelines and not every employee deals with such incidents.
The CSIRP is usually created by a team of experts from every department, and they are approved by the organization’s senior leadership.
Why is Having an Incident Response Plan Important?
Cybersecurity incidents pose a considerable threat to the business workflow; If they are not addressed immediately, they can cause a huge impact. A cost of data breach study by the Ponemon Institute showed that an organization, on average, faces 145 security incidents per year and spends $13 million to rectify the issue.
This is why a cybersecurity incident response plan is necessary to ensure that all your employees have all the necessary guidance to minimize the impact and reduce the recovery cost.
Another study by the Ponemon Institute also showed that 77% of security incident responders don’t have formal incident response plan roles and responsibilities. When an organization makes a formal incident response plan template, it provides a guiding light to all the employees and helps them to reduce the effect of cyberattacks, limiting financial and reputational damage.
It outlines the personal responsibilities, prevention measures, escalation requirements, and essential steps every employee needs to follow during a security incident.
Additional benefits that also make incident response plans highly instrumental:
Speedy Threat Mitigation
An effective incident response plan can help mitigate a security threat early and minimize the impact. It also helps boost the forensic analysis period and shortens the recovery time.
Recovery Cost Reduction
The recovery cost of security incidents is severe: A study revealed by IBM determined an organization usually spends $4.45 million on average for recovery. However, a well-laid-out CSIRP significantly reduces the recovery cost as it can limit the damage at the earliest.
Prevent Initiation of Disaster Recovery Plan
Another huge benefit of an incident response plan is that it can prevent the need to initiate a disaster recovery plan, which is a costly affair.
Distributed Responsibility
There are many incident scenarios where the appointed incident responders may be unable to act on a security breach. During those times, first responder organizations and emergency management teams step in and help remediate the security incident.
Complying with Regulations
Many industry regulations require organizations to have an effective incident response plan as a necessary element to maintain the optimum security posture. If any organization fails to maintain a formal CSIRP, then it often results in severe fines.
Maintains Trust
With a proper data breach incident response plan, organizations can showcase their commitment to data privacy and security and gain trust among customers and stakeholders.
The 6 Phases of a Cybersecurity Incident Response Plan
Building a CSIPR can be a daunting task without the proper framework. Organizations like the SANS Institute and the National Institute of Standards and Technology (NIST) have created an incident response framework that includes six phases that can help organizations handle security incidents effectively.
The SANS Institute’s “Incident Management 101” guide outlines six phases:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lesson Learned
Besides SANS Institute’s framework, The NIST “Computer Security Incident Handling Guide” is also widely considered by the organization for its incident response plan. The NIST framework is similar to the SANS framework but with subtle variations in steps:
- Preparation
- Detection and Analysis
- Containment
- Eradication
- Recovery
- Post Incident Activity
Following either of these frameworks will help organizations create their most effective incident response guide. Let’s take a detailed look at the six phases outlined by SANS Institute.
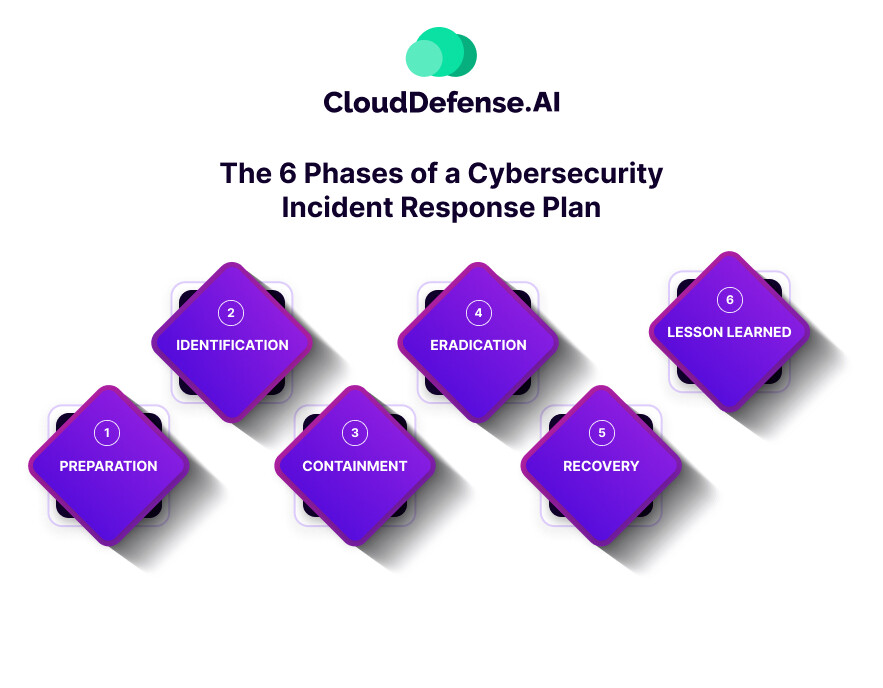
Preparation
This is the first stage, where the organization has to perform a risk assessment and identify all the critical assets and potential incidents. Then, they have to finalize the incident response team and define the roles, process, and communication plan.
Identification
Now, the cyber incident response team has to perform monitoring and accurately identify all the abnormal activities in the system. If they detect a security incident, they should then collect all the forensic data, evaluate the impact, and document the whole aspect.
Containment
After identifying the security incident, it is time for the team to contain the security incident and minimize the impact as much as possible. The team can opt for two types of containment: short-term and long-term.
In short-term containment, the team must bring down the infected part of the infrastructure or isolate a portion of the network. However, in long-term containment, the team should make temporary fixes to mitigate the incident and maintain business operations. During this time, the team should continue rebuilding the system to create a clean operation.
Eradication
While fixing the security incident, the incident response team should also make an effort to discover the leading cause behind the attack, eradicate the issue, and make arrangements to prevent such attacks in the future. All the security issues should be mitigated or patched immediately before they are further exploited.
Recovery
Recovery is a critical phase where the team resumes the production system after rebuilding and making all the necessary changes so that it doesn’t get further affected by another incident.
With verification from the top management, the team restores the production system from a certain date and time. The team also must verify that the affected part of the system is back to normal.
Lesson Learned
This is the last phase, where the team should document the complete incident from start to finish. They should also explore further to get a complete view, identify all the effective responses, and discover the areas where the team needs improvement.
This phase should be completed within two weeks so each incident responder can remember every detail clearly.
9 Steps to Create an Incident Response Plan
Every organization, whether small or large-scale, faces security incidents now and then. An incident response plan can help the team minimize the damage. However, the incident plan should be adequately designed; otherwise, it would be futile. Here are the incident response plan steps you should follow to create it:
Step 1: Assemble the CSIRP Team
Your first task is to assemble a team, preferably including experts from every department, who will effectively address any security incidents.
The members of the team should have the capability to identify the source of an attack and remediate it. It would help if you also involved members of the HR team, to help with internal communication.
Step 2: Develop a Policy
Your next task is to develop an incident response policy. This will serve as the guidebook for handling all the activities and necessary decisions. When creating the policy, it should be easy to understand and kept general so that everyone can easily follow it.
The policy should be created by the team and approved by the senior executives of the organization. A senior executive should make a team member the senior leader to handle the incident response process effectively.
Step 3: Outline the Roles
After creating the team and developing the policy, it is time to define the roles of each member and train them accordingly for different stages of incident handling.
You should conduct regular training so that everyone stays prepared for any kind of security incident. You should also conduct regular meetings to update and review the roles.
Step 4: Identify the Critical Components of the Network
The next thing you need to do is identify the critical components of your network and database. After identification, you need to create a backup and store them in a remote location. This aids during the recovery process.
Step 5: Create CSIRP Playbooks
Your next task is to create an incident response playbook that will act as a lifeline for the team. Since most security incidents follow a pattern, the playbook having a standardized response will help the team.
The playbook should outline all the steps necessary to respond to different security incidents. The steps in the playbook will act as a basic template for the team so they have an idea of how to react to certain types of security incidents. You should create different playbooks to address different incident types and help the team simplify the response process.
Step 6: Develop a Communication Plan
To effectively respond to security incidents, the CSIRP team needs to communicate correctly with other teams and stakeholders of the organization. So, the organization must establish an incident response communication plan that will outline how the teams should communicate.
The plan should also outline the type of information the incident responding team should communicate with other groups. It should also include when the team should contact law enforcement and who will have the authorization to do it.
Step 7: Testing the Plans
Now, it is time to test all the processes defined in the incident response plan and determine whether they work or not. You should perform incident response plan testing in a simulated environment and verify that teams have updated plan information and understand their responsibilities.
From DDoS attacks, misconfiguration, and firewall breaches to ransomware, you should test all the plans with various simulated scenarios. While testing the plans, teams should discuss properly while applying the procedures and potential issues that might occur.
Step 8: Explore the Lessons Learned After an Incident
After every security incident, you should conduct a formal lessons-learned meeting in which every team member involved in the security response should participate. These meetings will help identify all the vulnerabilities and gaps that gave rise to the security incident.
During these meetings, team members should also discuss the areas where the incident response plans need adjustment to ensure a better mitigation strategy. Extrapolating the lessons from each current security incident will help prevent future security incidents and also handle them in a better manner.
Step 9: Making Regular Updates
The incident plan should be updated at regular intervals as security threats are evolving rapidly. The plans should also be validated and evaluated after every security incident and change in the organization’s infrastructure.
Incident Response Plan Examples and Templates
Here, we present to you some incident response plan examples and templates:
- Minnesota Department of Agriculture: This incident response plan is designed for agriculture chemicals. This incident response plan showcases a well-documented process; it introduces STARR response and how local responders are alerted first during an emergency. It also shows how everyone can recover from the incident and utilize emergency equipment and supplies.
- University of Oklahoma Health Science Center: The OUHSC follows a PCI DSS (Payment Card Industry Data Security Standart) incident response plan that outlines plans for the cardholder data environment and incident response phases. The plan comes into play whenever the cardholder data is lost, stolen, or accessed by unauthorized individuals.
- California Government Department of Technology: This is a brief yet detailed incident response plan that highlights a seventeen-step plan with references. It is designed to aid organizations in responding to different security incidents like malware, data breaches, and system failure.
- Carnegie Mellon: Carnegie Mellon showcases a computer security incident response plan that highlights the employee’s needs to perform for recovery. It outlines all the steps everyone needs to follow in case of a computer security breach.
- University of Buffalo: The University of Buffalo’s incident response template is designed to address security incidents in the IT environment. Here, the vice president and chief information officer are the responsible executives. The plan helps the team to recover from cyber attacks in the IT environment.
Key Elements of a Cyber Incident Response Plan
While creating a cyber incident response plan, every organization must be familiar with all the key elements that should be included. However, all these elements may not apply to your organization. Here are the elements that you should keep in mind:
Identifying the Source of the Cyberattack
When a security incident occurs, the first thing you should do is to identify the source of the cyberattack. Your team should thoroughly check how and from where the cyberattack originated in the system.
Containing the Attack
The incident response team should make all efforts to contain the infected part of the system or network and isolate it from affecting others. The team should try to minimize the damage as soon as possible.
Contacting the Legal Team
When a security incident occurs, it would also be a wise idea to take advice from your legal team regarding regulatory compliance. Consult with them regarding the legal issues that may arise from the incident.
Informing the Insurer Regarding Attack
When you have a cyber liability policy, it would be best to inform the insurer regarding the security breach in your system. You should provide all the documents regarding the cyberattack so they may take care of any losses that happened due to the attack.
Notifying Everyone Regarding the Attack
If the cyber attacks have affected any customers, stakeholders, and third-party individuals, then it is wise to inform them regarding the cyber attack. You can release a public statement regarding the attack so that everyone is aware.
Accurately Assess the Extent of the Damage
Once the attack has been isolated, your team should properly assess the extent of the damage to the system. The assessment will give you an idea of the areas that have been affected and what you should do next.
FAQs
Is a cybersecurity incident response plan mandatory?
A cybersecurity incident response plan plays a vital role in developing your cybersecurity strategy as it provides guidelines needed following a security incident. Importantly, most industry regulations require organizations to have a formal incident response plan in place as a regulatory requirement.
What is the purpose of a response plan?
The primary purpose of a response plan is to create a guidebook that will help the responders identify, respond to, and recover from a security incident. It enables the team to minimize the impact of a security incident.
What is the first step in an incident response plan?
The first step in an incident response plan is preparation, during which the organization gathers all the resources required to create the plan. In this phase, the organization also identifies the security gaps, principal components, and possible security incidents.
What should be included in an incident response plan?
An incident response plan includes several components that allow the organization to identify and recover from a security incident. These components include preparation, detection and analysis, containment, eradication and recovery, and post-incident improvement.
Does HIPAA require an incident response plan?
To stay compliant with HIPAA, an organization is required to have an effective incident response plan in place to detect, contain, and recover from breaches in the healthcare environment. So, yes, HIPAA does require an IRP.
Conclusion
We are hopeful that we have been able to guide you in creating an effective incident response plan that will help your organization prepare for and easily recover from security incidents.
We have presented every step in detail so it becomes easier for you to create your incident response plan properly. Creating an incident response plan for ransomware, security breaches, and insider threats is vital for every organization. Our guide will help you with all the essential information.







