GDPR
ISO/IEC 27001 Compliance: Elevate Your Data Security
Cyber threats lurk around every corner. ️ ISO/IEC 27001:2013 is your suit of armor, but building a secure system can be a complex beast. CloudDefense.AI is your secret weapon! We make implementing and maintaining a rock-solid Information Security Management System a breeze.
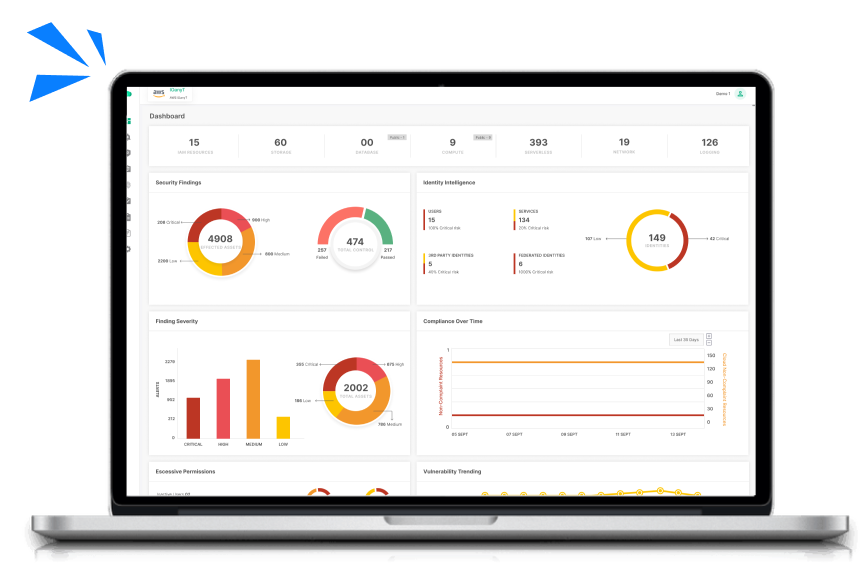
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
EMPOWER YOUR BUSINESS
Achieve Unmatched Data Security. ISO/IEC 27001 Compliance Made Simple. Book Your Live Demo Today!
Time is ticking, and every delay in security could mean missed opportunities. CloudDefense.AI’s application security solutions embed protection into every stage of your DevOps pipeline so that you can release updates quickly and confidently. Fast, secure, and effortlessly smooth—just how it should be!

The Growing Demand for Comprehensive ISMS Solutions
As organizations strive to protect sensitive data, the demand for rigorous security standards is on the rise. ISO/IEC 27001 is globally recognized, but achieving and maintaining compliance can be daunting. With CloudDefense.AI, you’re equipped with a simplified ISMS portal, making it easier to identify, assess, and mitigate risks across your enterprise.

Simplify ISO/IEC 27001 Compliance with CloudDefense.AI
Achieving ISO/IEC 27001 compliance is not just about ticking boxes—it’s about creating a resilient security posture that protects your organization from evolving threats. CloudDefense.AI provides a comprehensive platform to boost your ISMS, ensuring that you meet ISO standards efficiently and effectively.
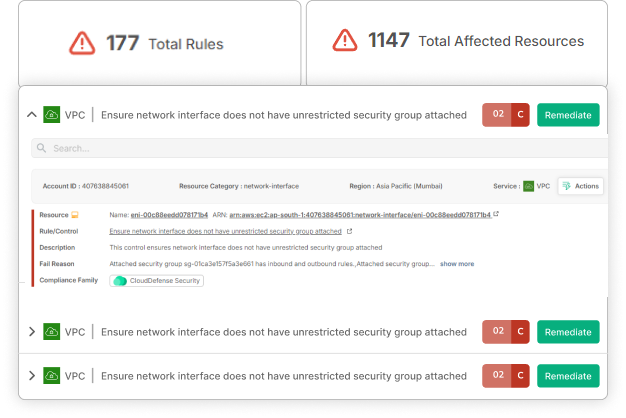
How CloudDefense.AI Keeps You ISO/IEC 27001-Ready
Unified ISMS Portal
Empower your teams with a centralized platform that simplifies ISO compliance, offering internal verifications, automated remediations, and thorough checklists to keep your security processes on track.
Prioritized Risk Management
Focus on critical updates and vulnerabilities first, ensuring that your risk management efforts are aligned with ISO/IEC 27001 standards and that potential threats are mitigated before they escalate.
Continuous Monitoring Across the SDLC
Leverage SCA, SAST, and DAST scanners to continuously monitor your software development lifecycle, identifying and addressing vulnerabilities that could compromise your compliance with ISO standards.
Smooth Integration with Existing Processes
Maintain real-time ISO/IEC 27001 compliance by syncing your security protocols with live repositories, ensuring that your ISMS evolves alongside your organization’s needs.
Certified for Cross-Industry Standards
Meet not only ISO/IEC 27001 but also other critical standards such as GDPR, HIPAA, PCI DSS, and SOC 2, with a platform designed for comprehensive, cross-industry compliance.
Exceed Customer Expectations
Protect your organization’s reputation by demonstrating a commitment to data security that exceeds regulatory requirements, and building trust with customers and stakeholders alike.
Why ISO/IEC 27001 Compliance Matters
ISO/IEC 27001 compliance is more than a regulatory requirement—it’s a strategic advantage. By implementing a strong ISMS, you protect your organization’s most valuable assets and enhance your ability to respond to emerging threats. With CloudDefense.AI, you’ll be well-positioned to meet these challenges head-on.
Mapping ISO/IEC 27001 Rules to CloudDefense.AI Solutions
Information Security Roles & Responsibilities
CloudDefense.AI offers enterprise-wide reporting and flexible data management, ensuring that your organization’s governance and security intelligence align with ISO requirements.
Teleworking Controls
Our platform’s auto-remediations and WAF firewall provide comprehensive protection for both premise and cloud infrastructure, even as users access sensitive data remotely.
Segregation of Duties (Access Controls)
Implement a ‘least-privilege’ access model to minimize risk and eliminate single points of failure, ensuring that access to sensitive information is appropriately controlled.
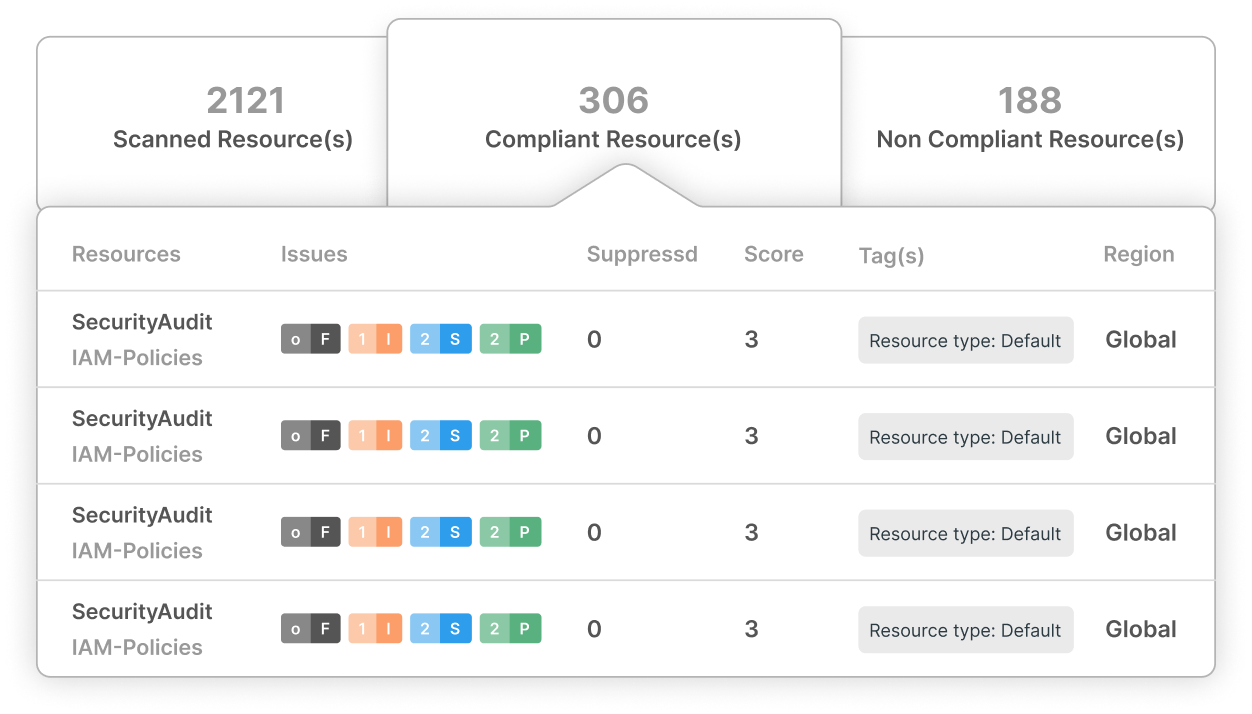
Ready to Elevate Your Security Posture?
ISO/IEC 27001 compliance is within reach with CloudDefense.AI. Schedule a demo with our team today and discover how our platform can help you achieve and maintain the highest standards of data security.




