M&A Cybersecurity Due Diligence
Secure Every Deal, Protect Your Investment!
In the high-stakes M&A environment, ensuring the cybersecurity integrity of acquisition targets is non-negotiable. Our platform offers advanced threat assessment, continuous monitoring, and swift remediation, giving you the confidence to make informed, risk-averse decisions.
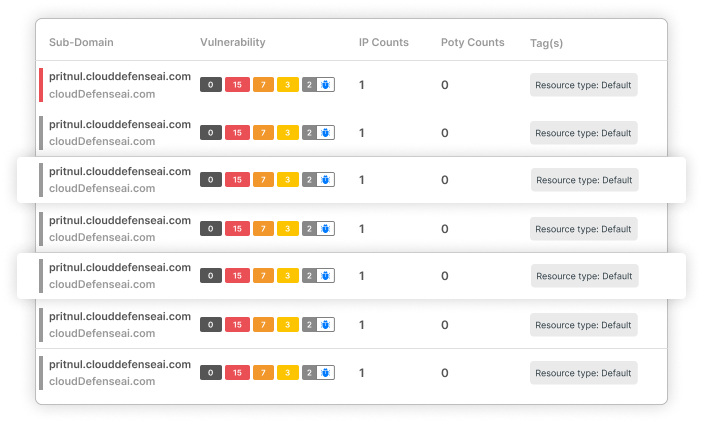
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
Strengthen Your Deals
Strengthen Your Deals: Detailed Cybersecurity Audits for M&A
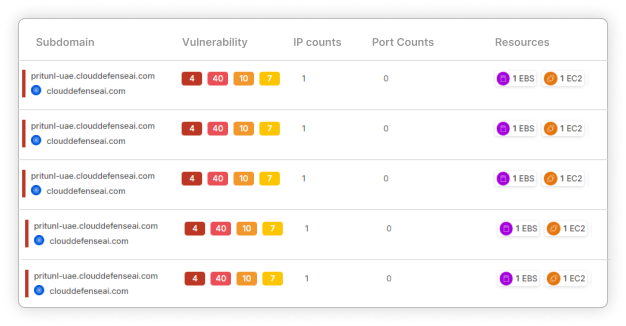
Due diligence doesn’t have to feel like running through a minefield. With our platform, you gain complete visibility into the cybersecurity skeleton of potential acquisitions. Uncover hidden risks, flag vulnerabilities, and ensure that every asset—from digital footprints to on-premise infrastructure—is secure before the deal closes. Make informed decisions with confidence, backed by a platform that leaves no stone unturned!

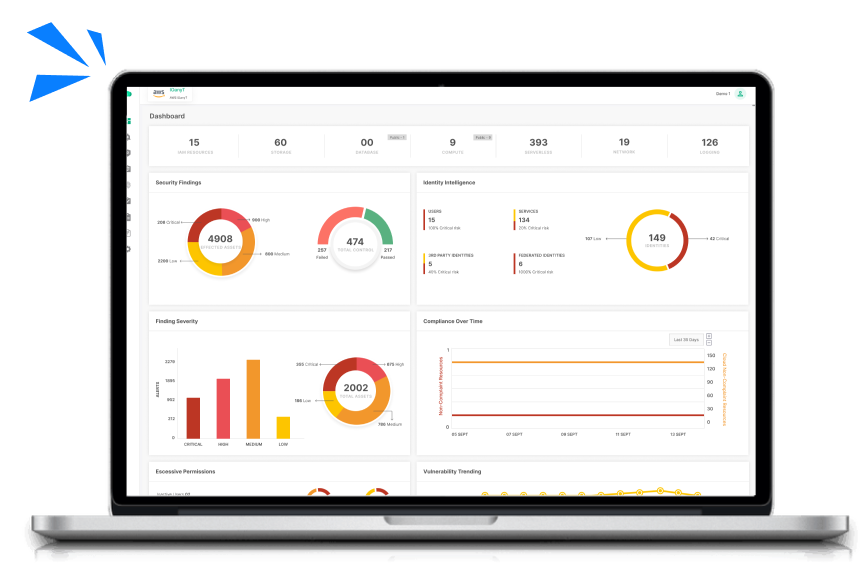
Gain Total Insight
Understand every facet of your target’s IT infrastructure. Our platform dives deep into systems, applications, and networks to uncover potential risks that could jeopardize your investment. Gain clarity on how each component impacts overall security and operational integrity.

Minimize Operational Risks Early
Avoid post-acquisition surprises by addressing cybersecurity risks during the due diligence phase. From outdated applications to poorly configured networks, we identify and rectify issues that could disrupt operations or erode value.

Ensure Complete Protection
Protect your investment by implementing robust cybersecurity measures tailored to the specific needs of the acquired entity. Protect sensitive data, ensure compliance, and prevent unauthorized access from day one.
Your Acquisition Targets Are Under Attack!
M&A targets are prime for cyberattacks, with hackers aiming to exploit vulnerabilities during transitions. Don’t let your deal become the next headline!
The Numbers Don’t Lie!
$4.45 M
The average cost of a data breach in 2023 was $4.45 million
80%
80% M&A deals resulted in cyber incidents after acquisitions
90%
About 90% dealmakers consider Cybersecurity as a critical factor in the decision-making process.
The Stakes Are High—Can You Afford to Take the Risk?
Don’t let cybersecurity blind spots derail your acquisition. Protect your assets, your reputation, and your future with our specialized M&A Due Diligence services.
With CloudDefense.AI…
Stop Cyber Threats From Undermining Your Deals!
Surfing through the complexities of M&A while managing cybersecurity risks can be overwhelming. CloudDefense.AI simplifies the process, allowing you to identify, address, and minimize risks with unparalleled efficiency.
Here’s How We Turn Cybersecurity Into an Asset for Your M&A Strategy:
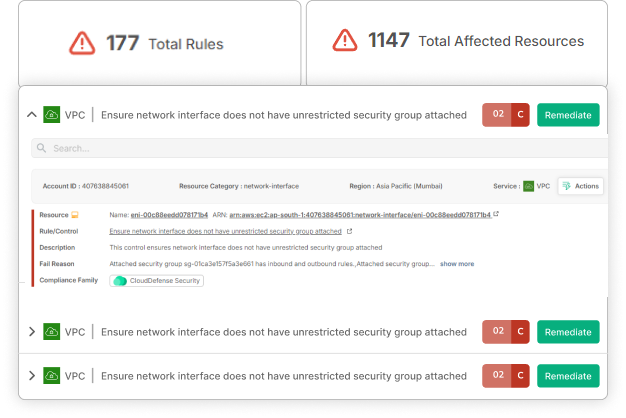
From Complexity to Simplicity
Effortless Integration
Automate your cybersecurity checks, making the due diligence process seamless and efficient.
Dual-Layer Defense
Our platform covers both threat detection and compliance, keeping you ahead of potential risks during the M&A process.
Swift Remediation
Our intelligent diagnostics pinpoint and resolve vulnerabilities, protecting your investment without delay.
Actionable Insights, Not Overwhelming Data
Clear Reporting
Receive precise, actionable reports that empower you to make informed, data-driven decisions.
Streamlined Compliance
Our compliance tools prioritize risks, ensuring that your M&A process remains on track and secure.
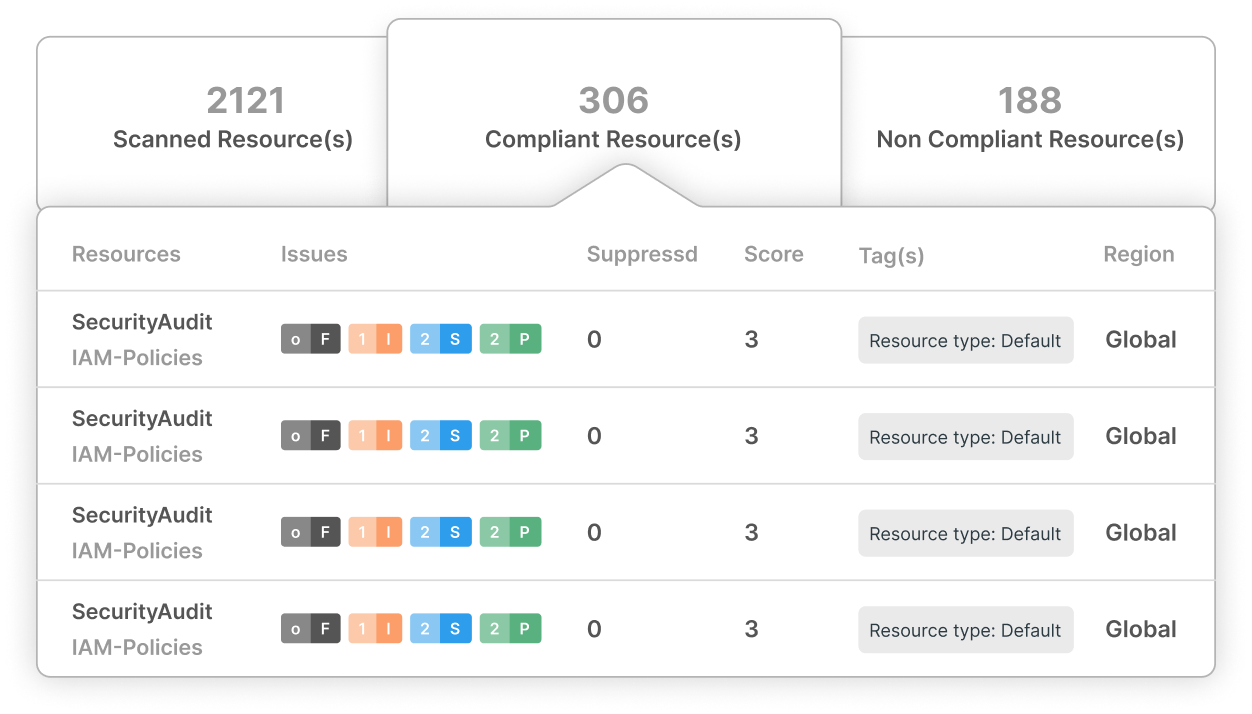
Customized Security for Every M&A Deal
Adaptive and Scalable
CloudDefense.AI adapts to the needs of each acquisition, offering continuous protection across all digital assets.
Third-Party Risk Management
Protect against external risks by monitoring all third-party interactions, ensuring comprehensive security.
More Than Just Security—It’s Strategic Success
Proactive Risk Management
Simplify risk management and compliance, ensuring your deals are not only secure but also poised for success.
Expert Guidance
Our team offers ongoing support, helping you to rise and shine in the cybersecurity landscape and optimize your M&A strategy.