Protect your Cloud with the worlds top CNAPP
Seamless & Continuous Cloud Protection from Code to Runtime. Harness the power of AI and Security Graph for unparalleled visibility and control.
Protect your Cloud with the worlds top CNAPP
Continuous Emerging Threat Detection & Remediation
CloudDefense.AI’s CNAPP continuously identifies and mitigates emerging internal, external, and ransomware threats
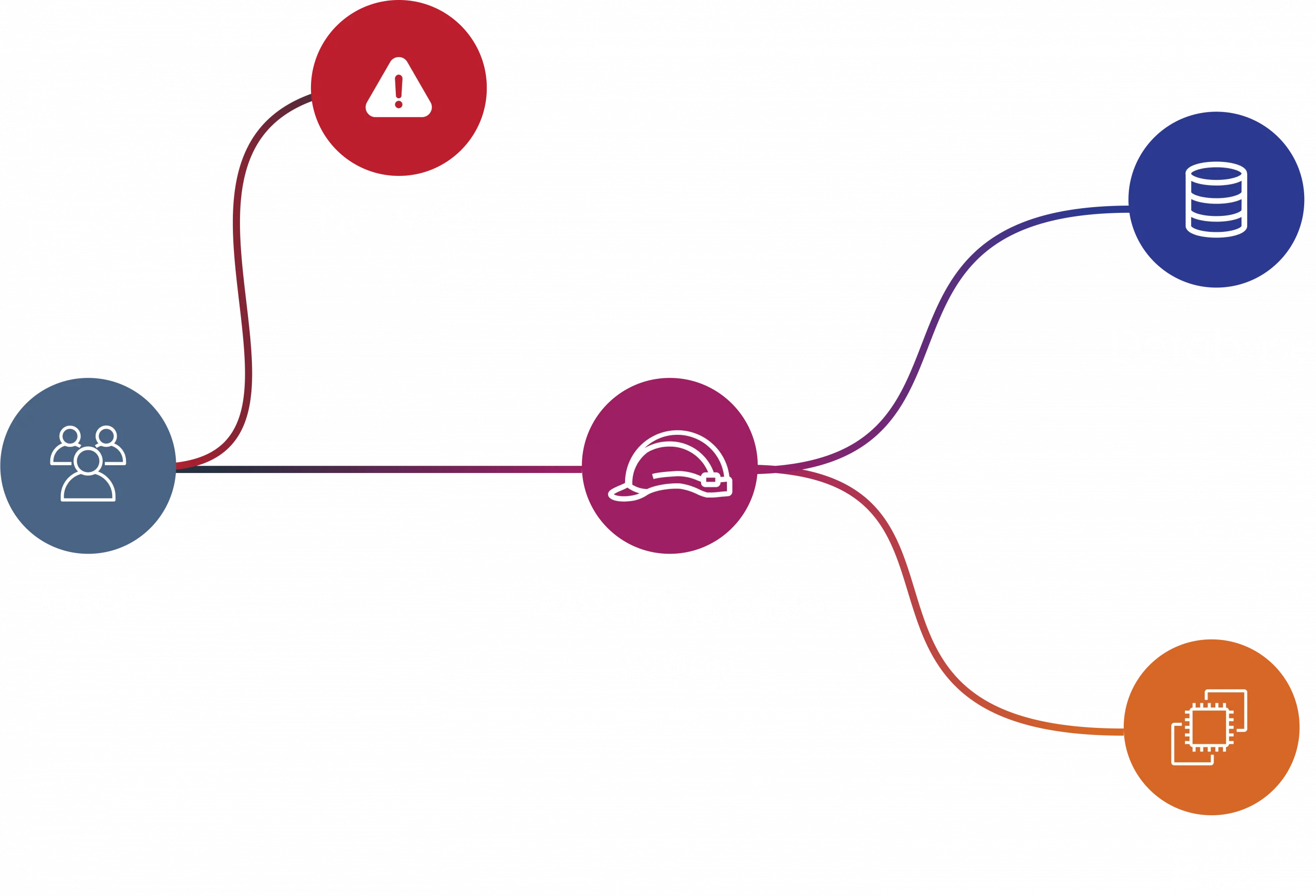
Prevent Internal Threats
Emerging Ransomware Threats
Prevent External Threats
Cloud-Native Application Protection Platform
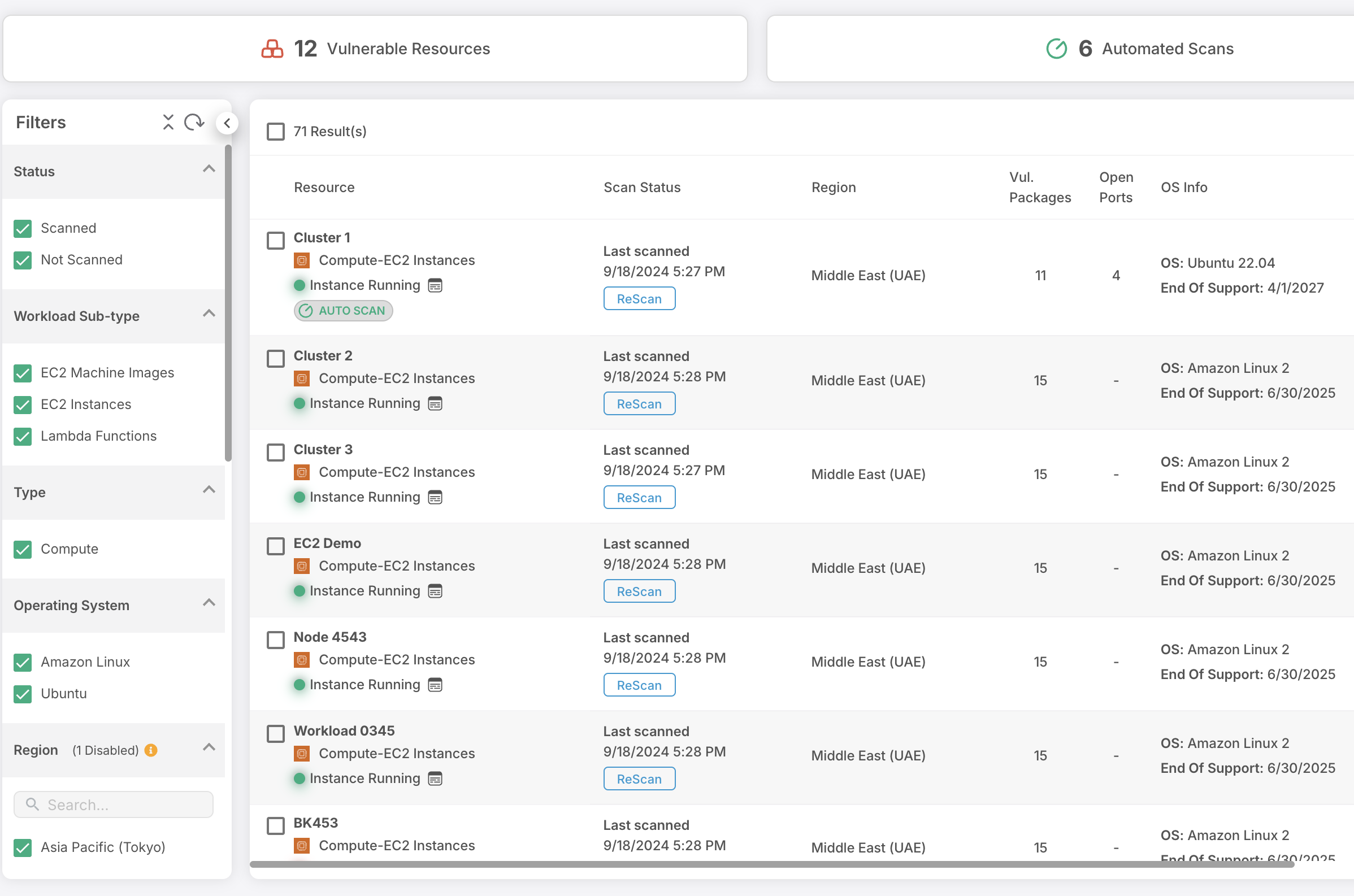
Cloud Security Posture Management (CSPM)
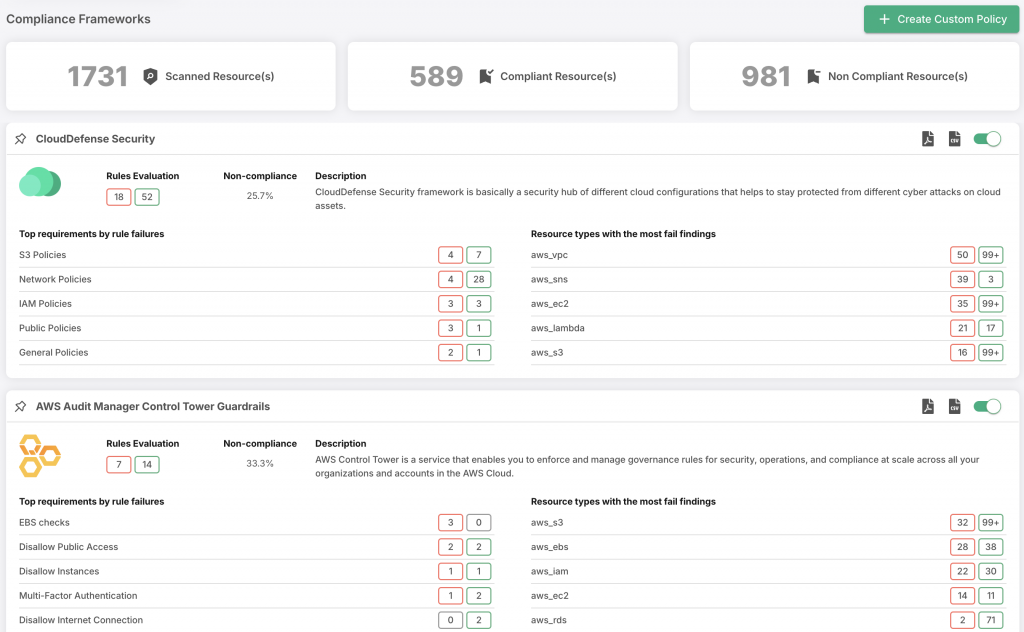
Imagine having a bird’s-eye view of your entire cloud landscape, where every deployed resource is at your fingertips, all in one place. With over 700 powerful policies at your disposal, you’re not just setting up guardrails; you’re forging an ironclad fortress of protection.ll
Cloud Infrastructure Entitlement Management (CIEM)
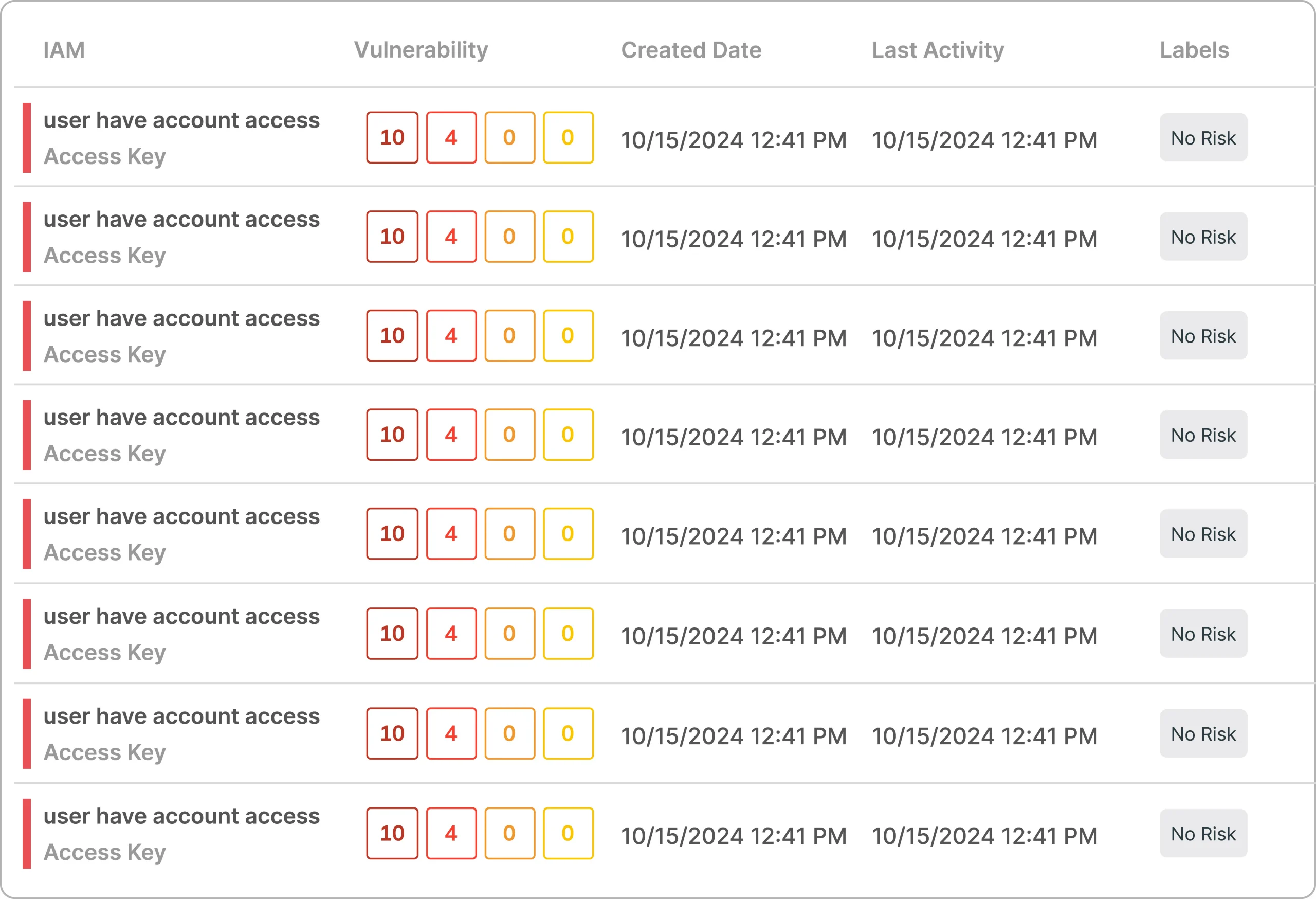
Cloud Workload Protection Platform (CWPP)
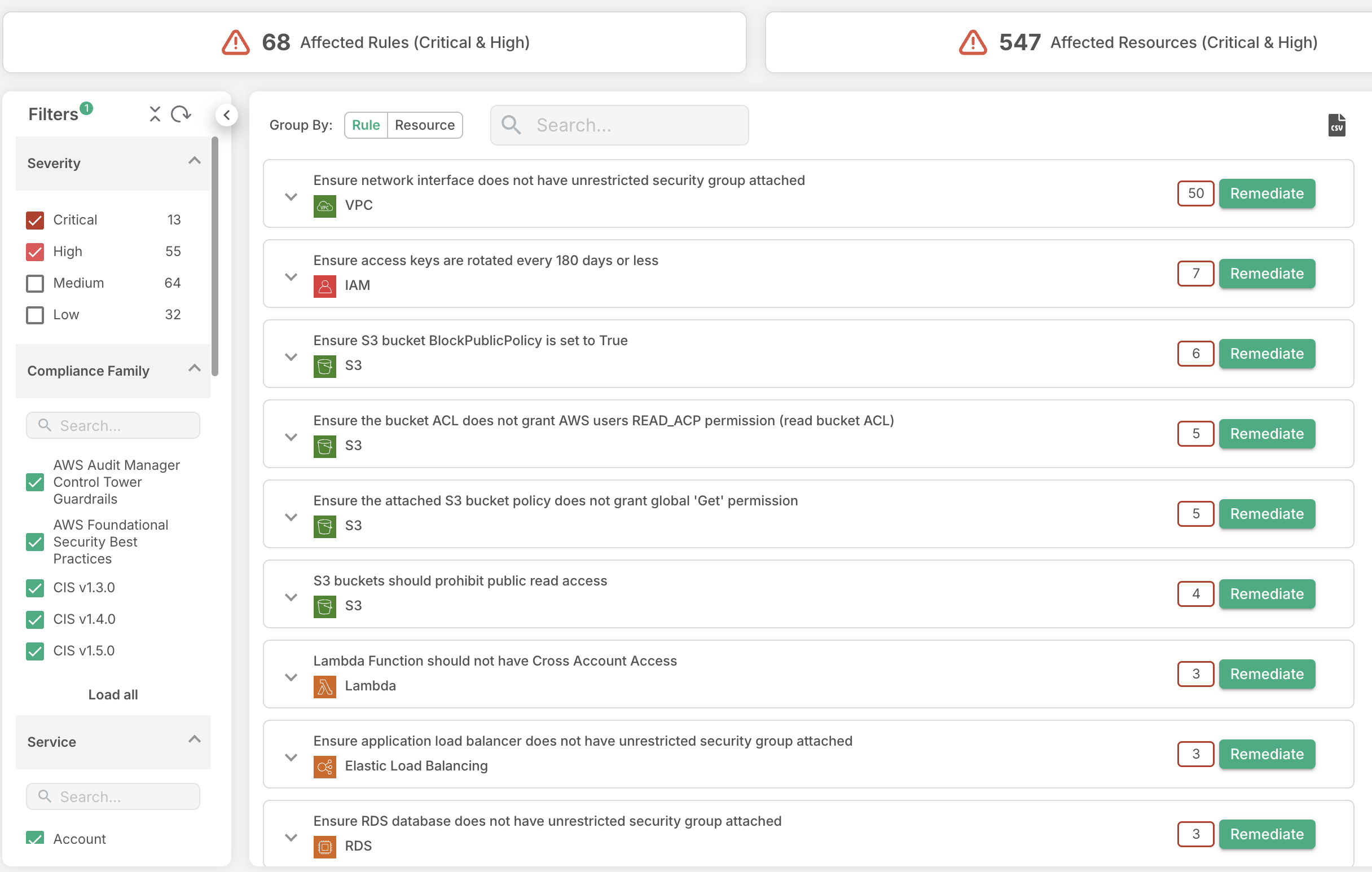
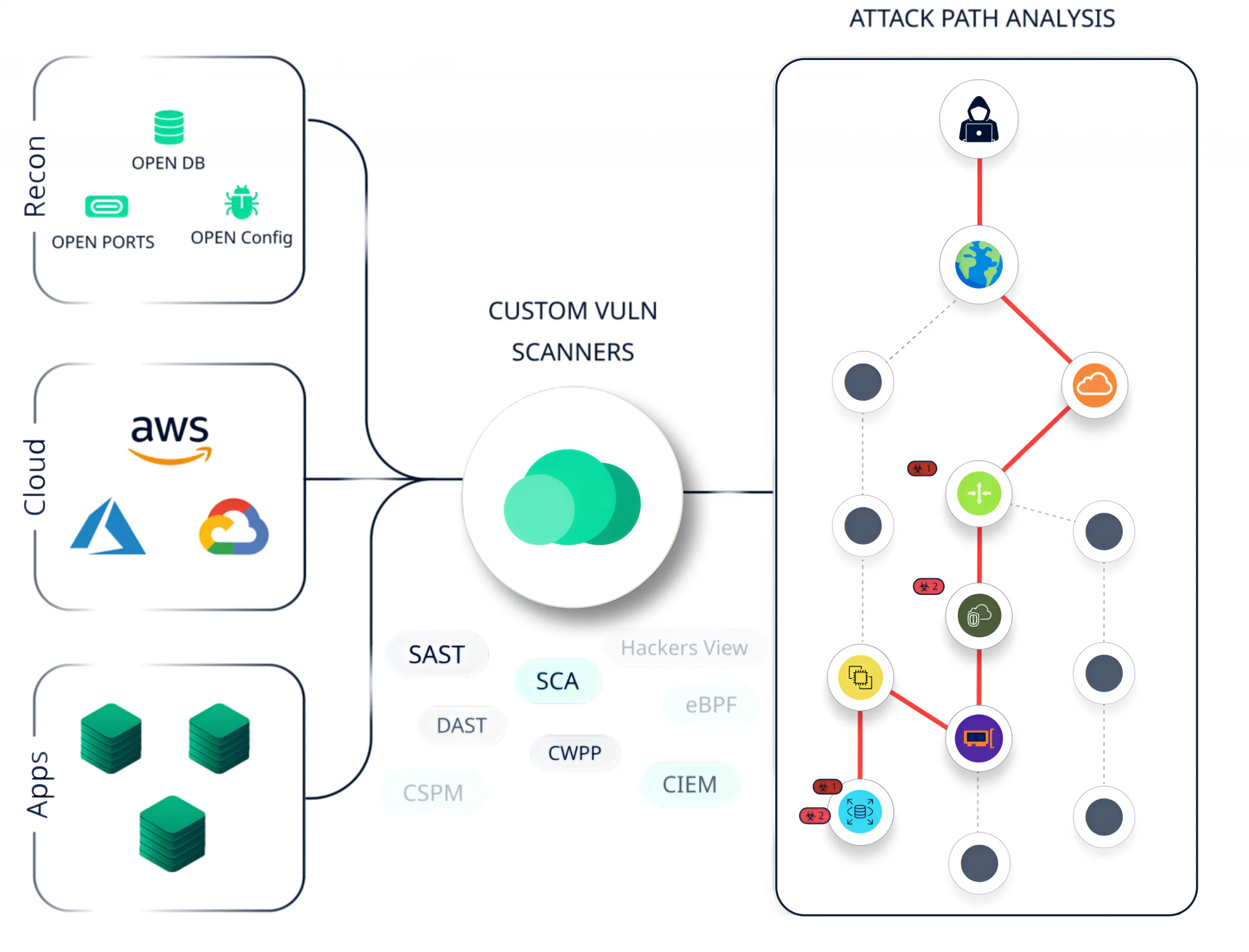
Cloud Vulnerability Management
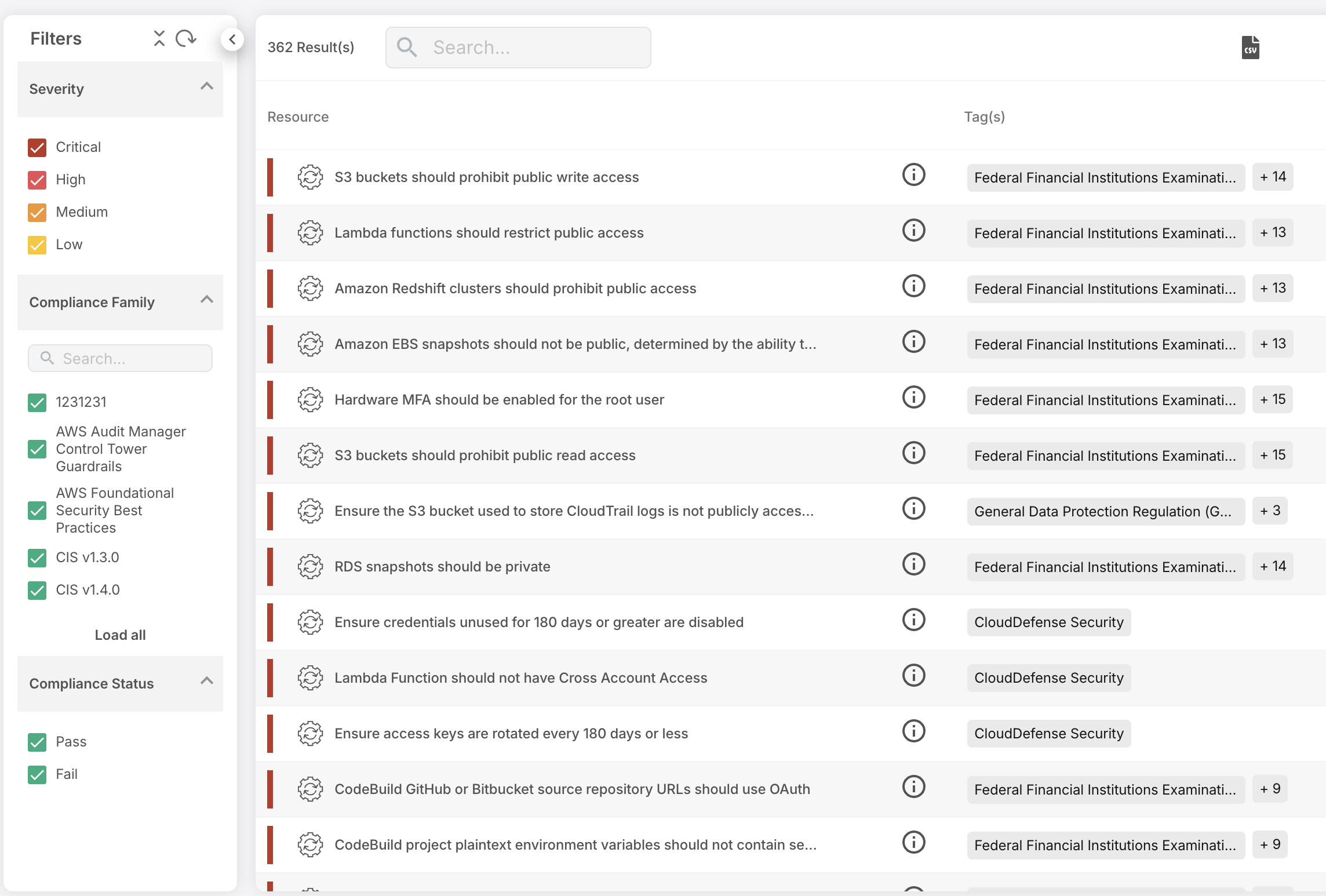
Holistic Multi-Cloud Compliance
Hacker’s ViewTM (EASM)
Why we are the Best CNAPP
Your Safety, Our Priority! From advanced threat detection to real-time monitoring and rapid incident response, our platform delivers complete protection, providing you with the confidence to navigate today’s complex security challenges.
Powerful Agentless CNAPP
Seamlessly connecting with your Cloud and Kubernetes landscape, our revolutionary CNAPP ensures lightning-fast infrastructure scans and delivers comprehensive vulnerability reports in mere minutes. No extra resources, no maintenance hassle.
A Unified Solution for Your Cloud and Applications
Imagine having all your cloud protection needs in a single, easy-to-use platform. From tackling vulnerabilities to ensuring multi-cloud compliance, safeguarding workloads, and securing containers – we’ve got it all covered.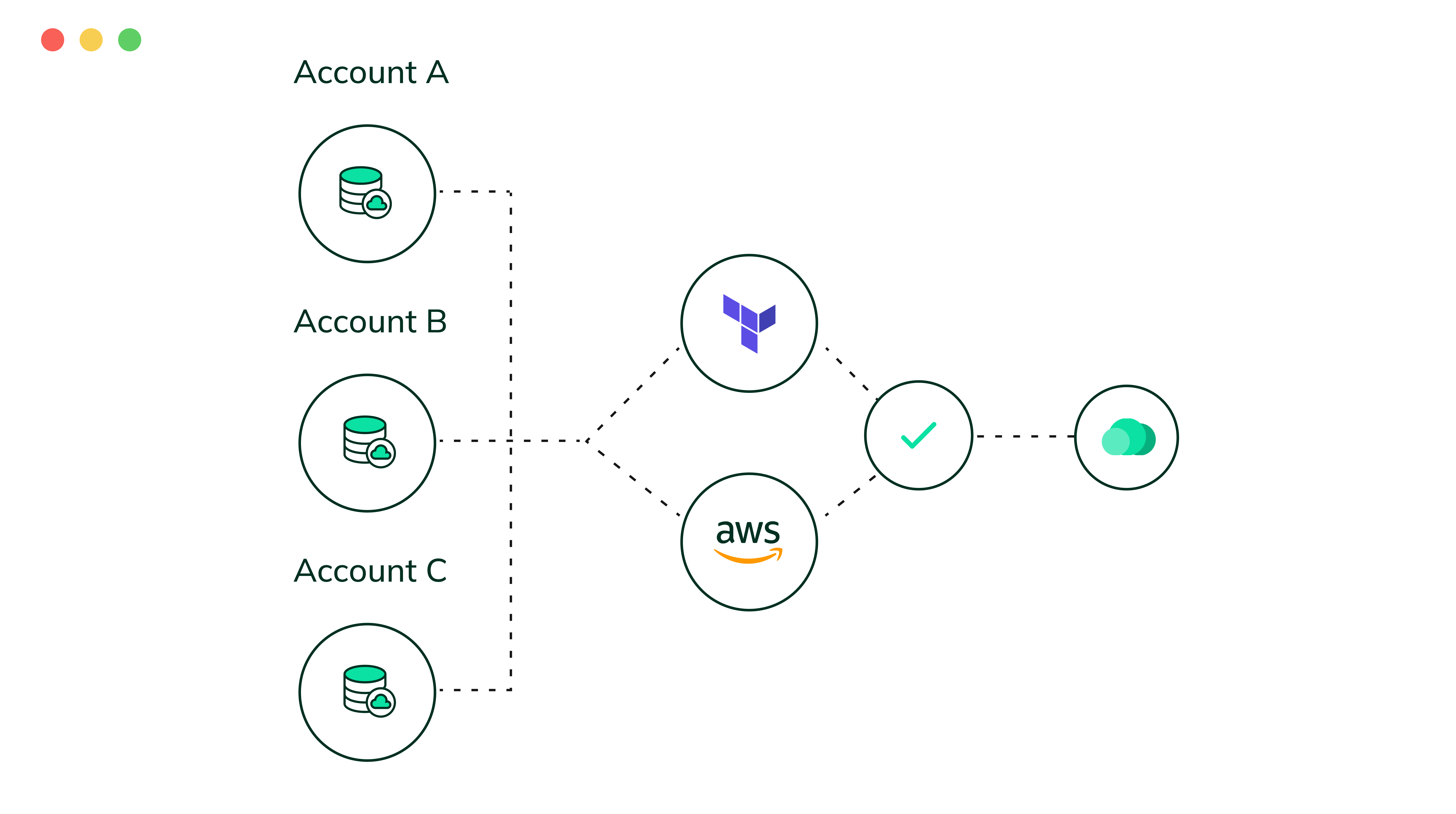
Effortlessly Remediate in Minutes
Say goodbye to time-consuming fixes! Address security concerns effortlessly with our prebuilt auto-remediations, guided steps, and instructive videos. Gain comprehensive insights through in-depth root cause analysis and dynamic guardrails, empowering your team to achieve unparalleled remediation speed.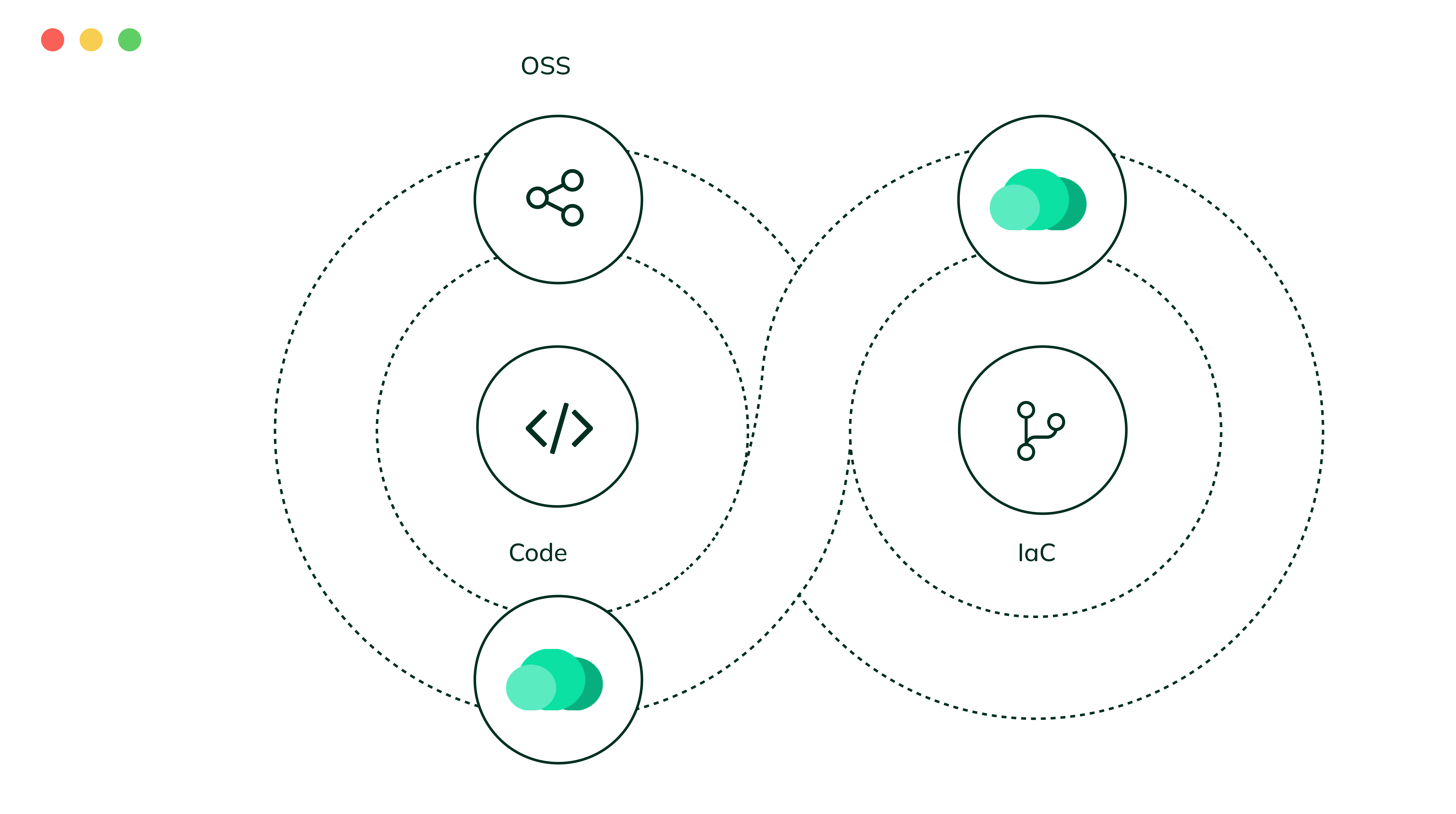
Robust Shift Left Security
With over 140 MM+ code commits processed, we offer unparalleled Shift Left Security for IaC templates and container images – all within a unified platform. Detect vulnerabilities and rectify misconfigurations at the earliest stages, ensuring a development journey that’s not only efficient but also highly secure.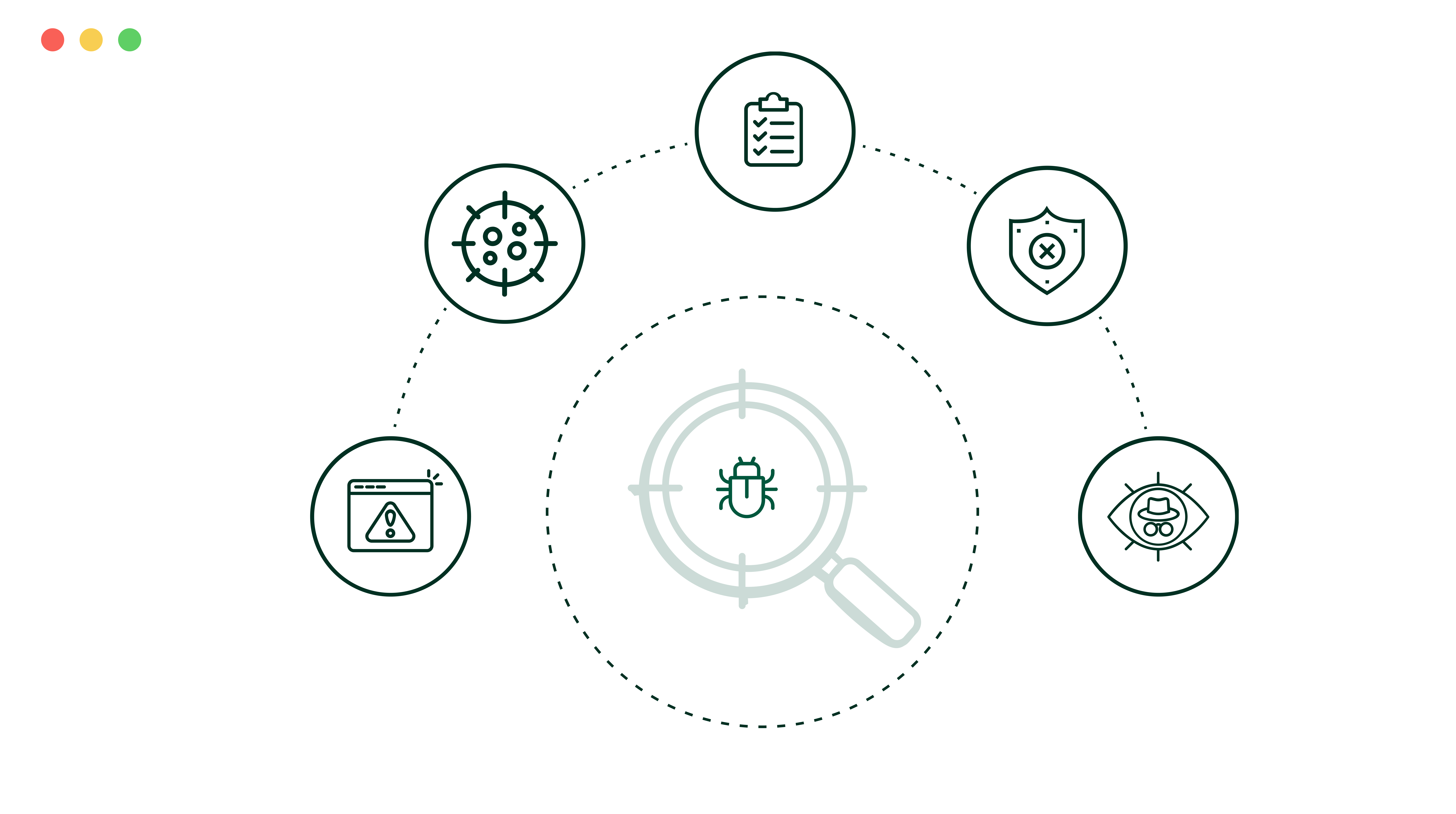
Proactively Detect and Analyze Real-Time Threats
Leverage the power of advanced AI to swiftly pinpoint IoBs (Indicators of Behavior) with unparalleled speed and precision. Transition from post-incident IoCs (Indicators of compromise) to proactively identified IoBs, reshaping the landscape of threat discovery and investigation.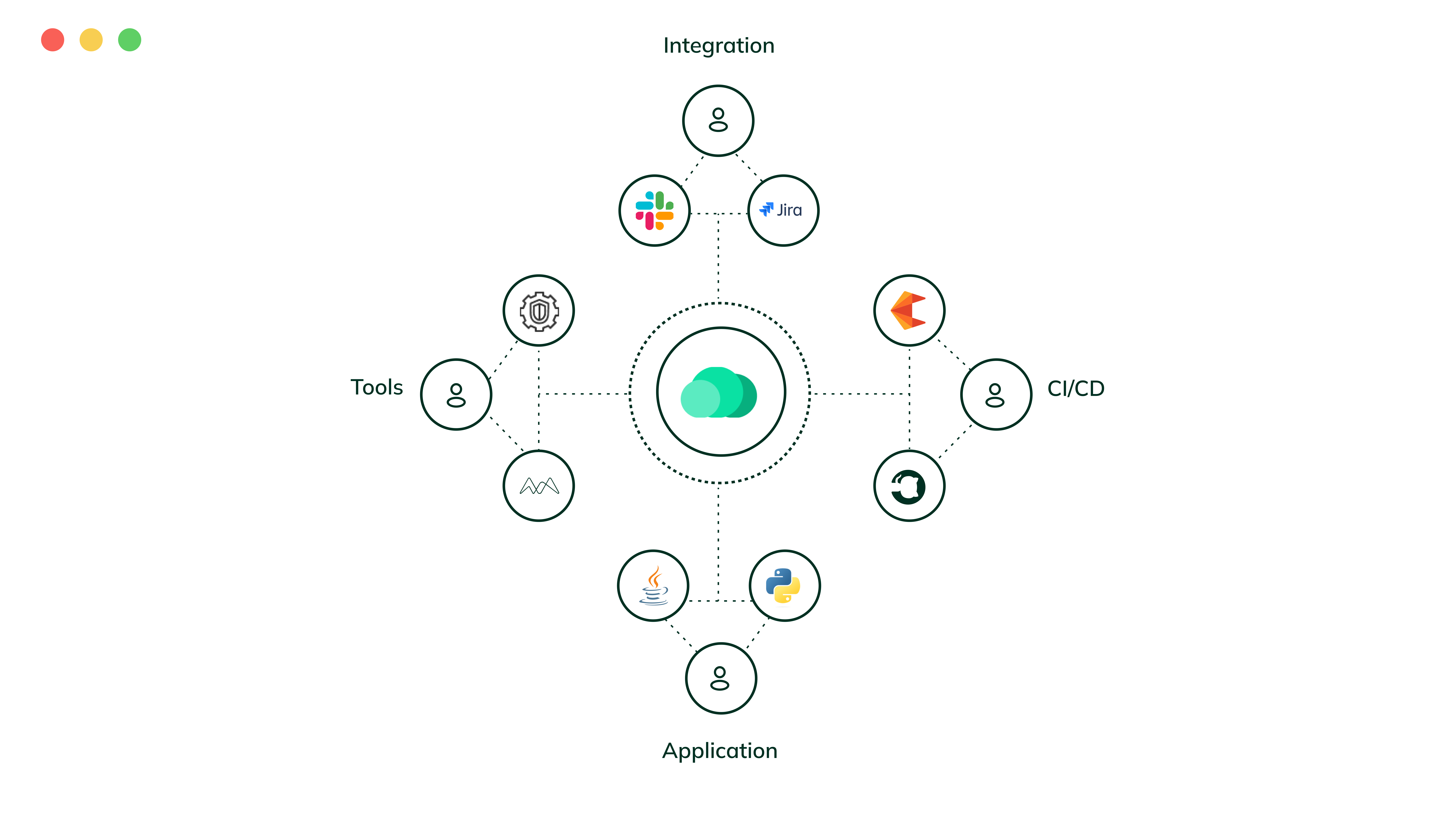
Boosted Collaboration Across Teams
Empower your security, Devs, and DevOps teams to seamlessly unite for rapid and secure cloud-native app development. With CloudDefenseAI, amplify teamwork via Slack, Jira, Webhooks, Email, and beyond. Elevate your workflow with tailored integrations, fostering collaboration and accelerating application deployment while ensuring top-notch security at every step.What our Customers say About our Products

We are a now Cloud Detense customer, our experience has been nothing but positive so far. Cloud Defense has been vary helpful during the POV and they continue to be supportive since we bought the product.They are quick to answer and very knowledgeable. They supportive since we bought the product….

What do you like best about Cloud Defense AI?
1) Proactive Vulnerability Management – Offers 3 sided view of our cloud env – code scanning, resource monitoring, and “hacker view” for early vulnerability detection and automated fix generation
2) Comprehensive Coverage – Provides integrated protection for cloud infrastructure, workloads, data, APIs, containers, and access mgmt/identities. It also automaticcally generates the scripts needed to fix the vulnerabilities or misconfigurations discovered. the agentless and SaaS offering was easy to implement/adopt.
3) Built-in Compliance Support: Streamlines adherence to regulations like GDPR, HIPAA . . .

I found them to:
-Enthusiastically listen to our complaints and work on them.
-Respond to our queries promptly and patiently provide detailed answers to our questions
-Regularly seek ideas/suggestions and implement them when possible collaborate in product customization
-Work with us in enterprise integration efforts etc.
Cloud Defense’s innovative data security solutions are a game changer. In an era where data is the
new currency, Cloud Defense emerges as a formidable guardian, ensuring businesses stay aheadin the digital landscape.

The CNAPP solution by CloudDefense.I has changed the way we think about cloud security posture. its unique design incorporates 3 distinct views (app code level scanning, cloud resource monitoring, and outside view of our env – AKA “Hacker View”), for creating a holistic view of our cloud environment and a comprehensive understanding of the issues we face (vulnerabilities, misconfigurations, improper access, etc.) What truly set CloudDefense apart of the unified protection across all aspects of our cloud env – infra, workloads, app + data, APis, containers, even identities and access policies, etc. Here is what CloudDefense changed for us: 1) We can replace multiple scanners & monitoring solutions with 1 unified tooling – the agent-less approach and the SaaS offering simplifies the work we need to do and help us to save money. 2)Now we have automated scanning but also automatically generated scripts for fixing the . . .

CloudDefense.AI offers a single platform for monitoring our entire cloud environment, simplifying our security operations. It digs into the details to uncover misconfigurations, vulnerabilities, and excessive permissions, enabling us to prioritize and fix issues efficiently. The team actively listens to user feedback, frequently releasing new features and improvements.
CloudDefense.AI have all the important tools like CSPM, CIEM, Threat Detection, CWPP, SAST, DAST, SCA, Container Security, API Security and more in one platform. I can see everything in one dashboard and I can see my priorities easily.

All in one Application Security Testing Tool
Fantastic all in one platform for application security testing. This is one of a kind application security tool that combines many tools into one and provides the development teams the confidence to meet their objectives.
Industry Solutions
CloudDefense.AI is an industry-leading multi-layered CNAPP that safeguards your cloud infrastructure and cloud-native apps with unrivaled expertise, precision, and confidence.
Financial Services
CloudDefense.AI fortifies the financial services sector by ensuring the security of critical data and compliance with industry regulations. Our solutions offer deep visibility into cloud environments, identifying vulnerabilities and providing actionable insights to mitigate risks and strengthen overall security posture.
Healthcare
CloudDefense.AI safeguards healthcare organizations by securing sensitive patient data and ensuring compliance with HIPAA and other regulations. Our platform provides visibility into vulnerabilities, automated remediation recommendations, and continuous monitoring to protect against breaches and enhance data security.
E-Commerce
CloudDefense.AI boosts e-commerce security by safeguarding customer information and ensuring compliance with data privacy regulations. Our platform provides visibility into cloud vulnerabilities, automated alerts for risks, and actionable recommendations for effective cloud security.
Information Technology
CloudDefense.AI supports IT companies by safeguarding intellectual property and enhancing development workflows. Our platform offers container security, DevSecOps integration, and automated compliance checks to address the unique challenges of managing cloud environments.
Government
CloudDefense.AI enhances national security by providing comprehensive cloud solutions that ensure data sovereignty and compliance with regulations. Our platform features identity and access management, secure data sharing, and incident response planning tailored for government operations.
Education
CloudDefense.AI secures educational institutions by protecting sensitive student and faculty information while enabling secure online learning. Our solutions focus on data encryption, secure collaboration tools, and compliance, fostering a safe educational environment.
Ready to see us in action? Schedule a time
to speak with our team!
Curious to see us in action? Set up a time to talk with our team!