Ransomware Protection
The Ultimate Ransomware Protection
Shield your business from ransomware attacks with CloudDefense.AI’s security solutions. Eliminate threats, ensure smooth operations, and secure your data with our cutting-edge technology.
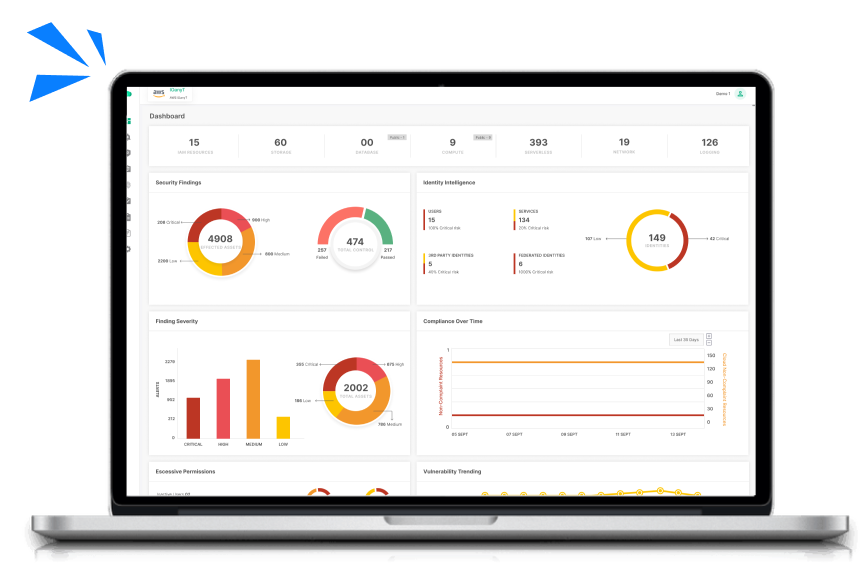
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
EMPOWER YOUR BUSINESS
One Solution, Complete Ransomware Defense: Guard Your Data Everywhere!
Say goodbye to ransomware risks and secure your business’s future. With CloudDefense.AI, you can protect your critical assets and maintain operational integrity, no matter where threats emerge.

Comprehensive Ransomware
Defense
Secure your business against ransomware across all environments—cloud, on-premises, or hybrid—through CloudDefense.AI’s unified platform.

Immediate Threat
Neutralization
Prevent ransomware attacks with CloudDefense.AI’s real-time detection and response, stopping threats before they impact your operations.

Interactive User
Interface
Effortlessly manage your security measures with CloudDefense.AI’s intuitive platform, designed for ease of use by both cybersecurity experts and beginners.
Your Retail Empire is Under Attack
Retail is a battlefield. Every day, cybercriminals target your business, ready to steal your hard-earned revenue and damage your reputation.
The Numbers Don’t Lie!
24%
You’re a Top Target
Retailers face a staggering 24% of all cyberattacks, making you a prime target for hackers.
-$250,000
The Price of Inaction
A single data breach can cost your business anywhere from $100,000 to $250,000. That’s money straight out of your bottom line.
20%
The Growing Threat
E-commerce security incidents have skyrocketed by 20% in just one year. The threat is real, and it’s escalating.
Can you afford to be a Casualty?
Don’t let these statistics become your reality. Protect your business, your customers, and your bottom line with our strong retail and e-commerce security solutions.
Our Holistic Approach to Ransomware Protection
CloudDefense.AI’s approach to ransomware protection integrates state-of-the-art technology, expert guidance, and continuous monitoring to safeguard your business from ransomware threats, ensuring resilience and compliance.
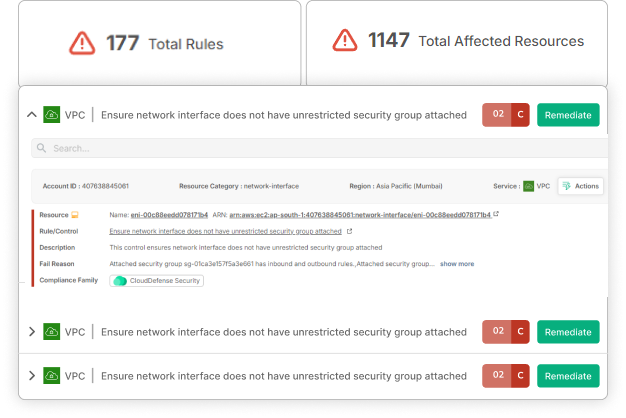
Immediate Detection and Response
At CloudDefense.AI, we equip businesses with the tools to swiftly identify and neutralize ransomware threats, transforming them into a resilient and proactive minority. Our platform’s intelligence-driven strategy ensures effective and immediate ransomware defense.
Rapid Neutralization
Detect and eliminate ransomware threats instantly, positioning your organization among the elite few capable of handling ransomware with confidence.
Data-Driven Protection
Use intelligent data to stay ahead of threats and protect your business proactively.
Optimized Operations
Simplify your processes and minimize downtime with our rapid threat detection and response framework.
Competitive Security Edge
Stay at the forefront of cybersecurity by focusing on both prevention and quick recovery for enduring resilience.
Zero Trust Security Framework
Enhance your ransomware defense with thorough, trust-free scans that identify and mitigate risks before they can do harm. CloudDefense.AI’s technology ensures foolproof protection against modern ransomware threats.
Trust-Free Ransomware Defense
Eliminate vulnerabilities linked to trust dependencies, securing your data against ransomware attacks.
Automated Threat Mitigation
Strengthen your defenses automatically by minimizing common intrusion points and enhancing your security posture.
Transparency and Accountability
Provide stakeholders with assurance through verifiable internal checks and segregation of duties.
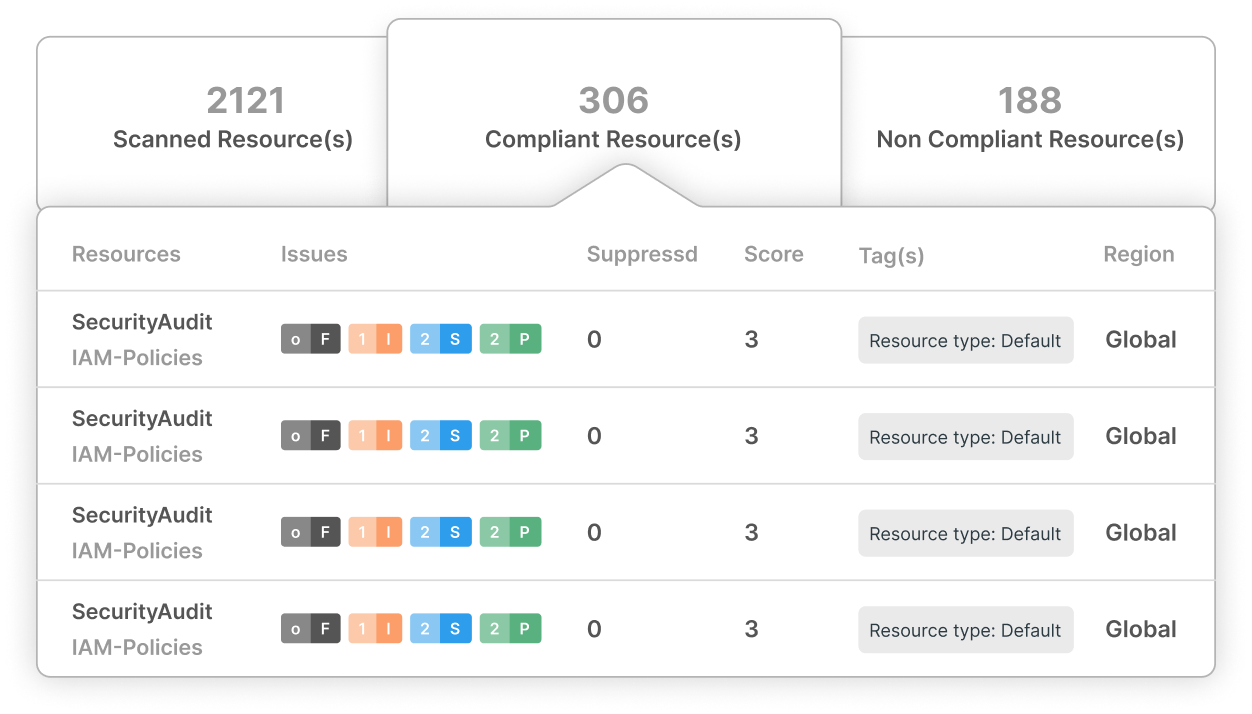
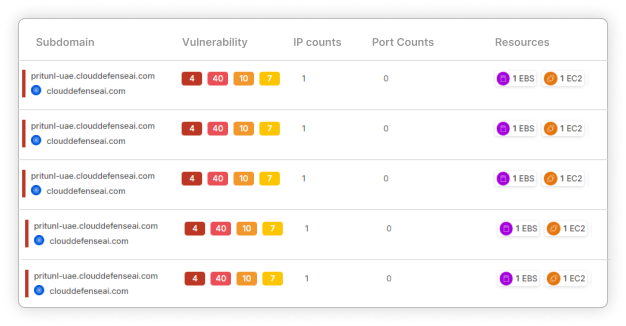
Seamless Compliance Management
Navigate complex regulatory laws with ease using CloudDefense.AI’s compliance management tools. Our platform ensures your organization remains compliant while safeguarding against ransomware.
Easy to Maintain Compliance
Manage compliance with regulatory standards using our comprehensive Airtight Checklists, covering PCI DSS, FINRA, NYDFS, FERPA, HIPAA, GDPR, and CCPA.
Insightful Reporting
Access detailed, actionable reports that empower informed decision-making.
Priority-Focused Compliance
Identify and address compliance gaps effectively, optimizing time and resources.
User-Friendly Experience
Simplify compliance management with our intuitive platform, accessible to all levels of expertise.
End-to-End Ransomware Defense
CloudDefense.AI provides strong protection against ransomware by rigorously monitoring and auditing all aspects of your digital infrastructure. Our SAST technology ensures continuous vigilance and resilience against ransomware attacks.
Continuous Monitoring
Our SAST technology constantly scans for vulnerabilities, ensuring your systems remain secure against ransomware.
Comprehensive Defense
Establish a strong security perimeter from initial intrusion attempts to full remediation.
Proactive Ransomware Management
Stay ahead of ransomware threats with CloudDefense.AI’s proactive security measures, ensuring uninterrupted business continuity.
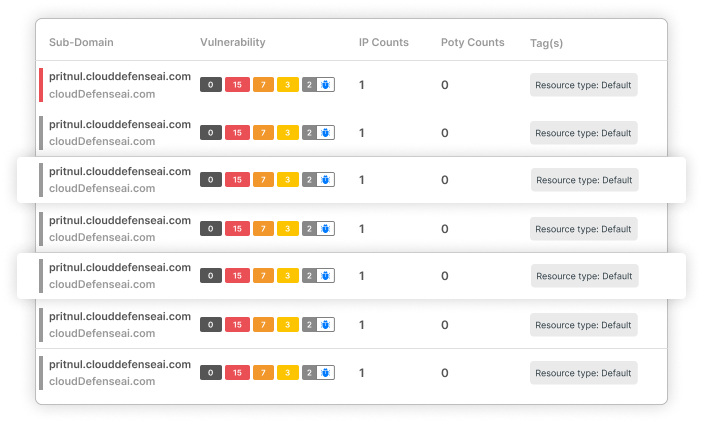
Experience Unrivaled Ransomware Protection
Discover how CloudDefense.AI can strengthen your business against ransomware. Join us for a live demonstration and witness our protection in action.




