Advanced Software Composition Analysis (SCA)
Advanced Software Composition Analysis (SCA)
Code security, Compliance Made Easy!!. Our SCA solution combines deep code analysis and real-time context to proactively assess vulnerability risks and compliance

Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
Our cutting-edge SCA Features
Next-Gen SCA: Enhancing Code Security, Compliance, and Transparency
Take control of license compliance, open source vulnerabilities, and code security like never before with CloudDefense.AI’s cutting-edge SCA scanning capabilities

Optimize Compliance with Ease
Achieve compliance efforts and reduce costs by gaining deep insights into open-source licenses and third-party components in your build pipeline.

Richer Dataset for In-Depth Analysis
We leverage vfeed’s proprietary dataset for richer insights that surpass the National Vulnerability Database (NVD)., ensuring faster, more accurate results.

Streamline SCA with a Single Command
Execute comprehensive SCA scans effortlessly with a single command, saving you valuable time and effort.

Enhanced Reporting Capabilities
Empower your team with advanced reporting features that save both time and money while keeping security at the forefront of your operations.
Our Comprehensive Approach to SCA
Streamlined Open Source Security
CloudDefense.AI empowers developers with comprehensive open source risk management. Seamlessly integrated into DevOps workflows, our solution proactively scans for vulnerabilities and ensures license compliance, providing a unified view of infrastructure and application risks.
Integrated DevOps
CloudDefense.AI seamlessly integrates with developer tools, ensuring open source risk management is a natural part of your workflow.
Full Lifecycle Security
From code to deployment and runtime, our solution offers end-to-end security for packages and container images.
Unified Risk View
Gain a single, clear view into connected infrastructure and application risks, making informed decisions effortlessly.
Granular Version Control
Enjoy precise version bump fixes for open source packages, enhancing security and compliance.
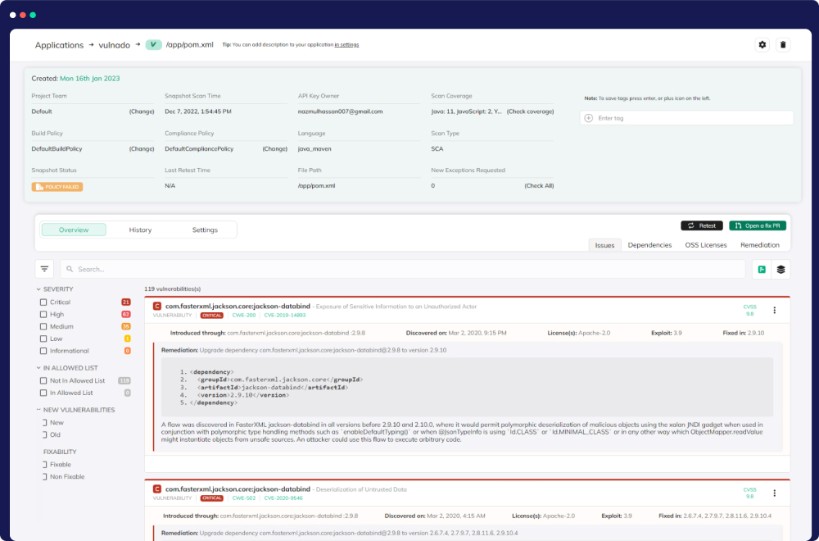
Vulnerability Remediation Made Simple
At CloudDefense.AI, we offer a robust vulnerability solution. Our database goes beyond NVD, simplifying remediation by pinpointing supported library updates. Auto-remediation streamlines security enhancement, making us your top choice.
Comprehensive Vulnerability Database
Our database goes beyond NVD, offering an extensive collection of vulnerabilities. This means you get a more complete picture of potential threats to your applications.
Simplified Remediation
We make it easy for developers to address vulnerabilities by providing clear guidance on which newer library versions support the necessary fixes. No more guesswork.
Exclusive Discovery of Hidden Threats
In addition to NVD listings, CloudDefense.AI uncovers vulnerabilities not found elsewhere. This exclusive insight equips you with a more robust defense against emerging threats.
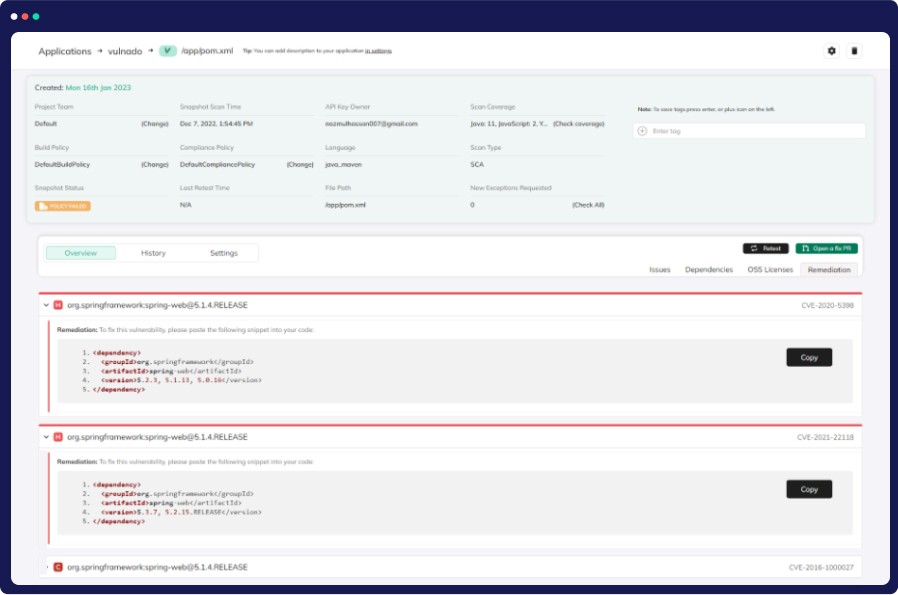
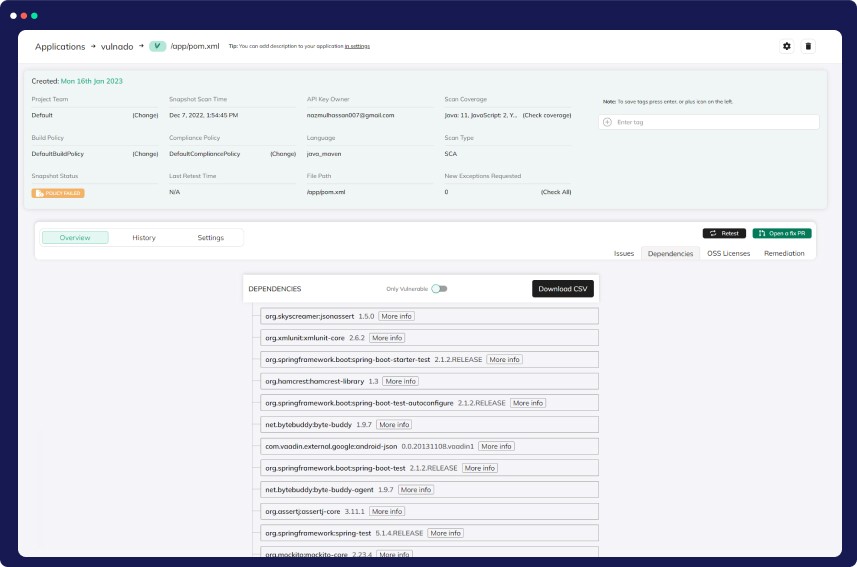
In-Depth Dependency Tree View
Discover and address vulnerabilities efficiently with CloudDefense.AI’s Dependency Tree View. Gain a holistic view of your application’s vulnerabilities, including direct and nested dependencies, for informed prioritization and enhanced security.
Comprehensive Overview
Get a holistic view of your application's vulnerabilities, encompassing all dependencies, both direct and nested, offering a complete and transparent understanding of your software's security landscape.
Prioritization Power
With our Dependency Tree View, effortlessly prioritize vulnerabilities based on their criticality. Focus your resources on mitigating high-risk threats, ensuring a more efficient and effective security strategy.
Efficient Remediation
Our platform equips you with actionable insights, allowing you to swiftly address vulnerabilities. Streamline your remediation efforts, reducing the window of exposure to potential threats and enhancing your security posture.
Unmatched Visibility
Gain unparalleled visibility into your application's security status through our intuitive Dependency Tree View. Easily identify potential risks and areas that require immediate attention, ensuring proactive threat mitigation.
Proactive Defense
Stay ahead of emerging risks and vulnerabilities with CloudDefense.AI's cutting-edge solution. By visualizing your application's dependency structure, you can proactively address security issues before they escalate.
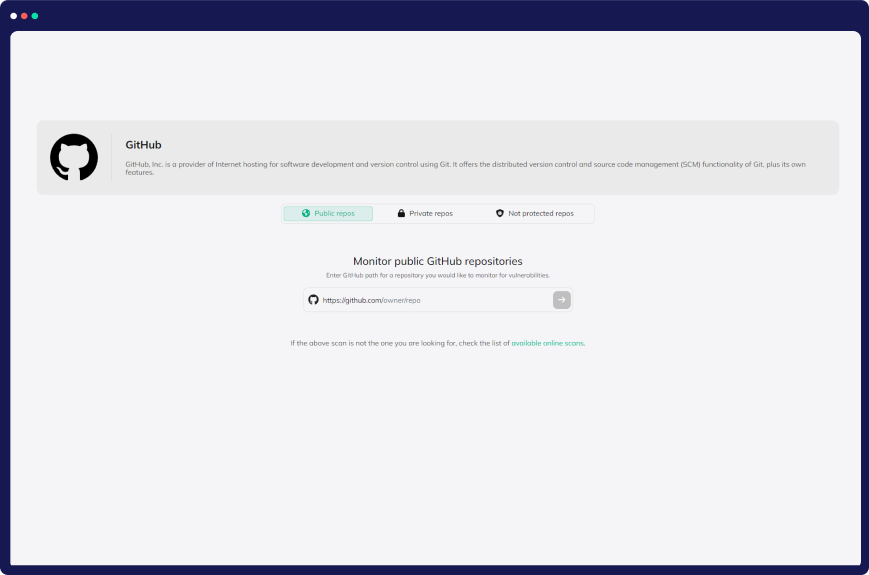
Quick and Easy Setup
At CloudDefense.AI, we prioritize simplicity and security. With our user-friendly technology, even non-experts can protect their applications in just 2 minutes, making us the trusted choice for developers and security teams.
Get Started in Minutes
CloudDefense.AI streamlines the security setup process, enabling you to launch and protect your applications within just 2 minutes. It's hassle-free and incredibly efficient.
Developer-Friendly
Our platform prioritizes developer needs, ensuring that you don't need to possess security expertise to safeguard your applications effectively. We simplify the entire security journey.
Trusted Security
Security teams across the industry place their trust in CloudDefense.AI. Our platform offers a straightforward solution to secure your applications, with just a simple command.