With the need for speed in the application development process, developers are rapidly turning to AI-powered IDEs like Cursor. It has not only enhanced developer productivity but also enabled organizations to achieve faster release cycles. However, implementing AI-generated code into the codebase introduces new security risks and attack vectors.
Even though Cursor is backed by its internal security guardrails, organizations still require a more comprehensive approach to protect their development environment. Securing Code in Cursor is essential to maintain code integrity, prevent vulnerabilities, and ensure compliance throughout the software lifecycle.
Today, we are going to provide you with practical tips and tools that will help in writing code securely and ensure optimum Cursor AI security.
Why Cursor AI Security is Vital for Modern Organizations
Cursor AI is a powerful AI-backed code editor that utilizes LLMs to automate code generation and help with refactoring. Modern organizations are rapidly adopting Cursor to accelerate their development lifecycle. The rise of AI Code editors like Cursor may have benefited organizations in many ways.
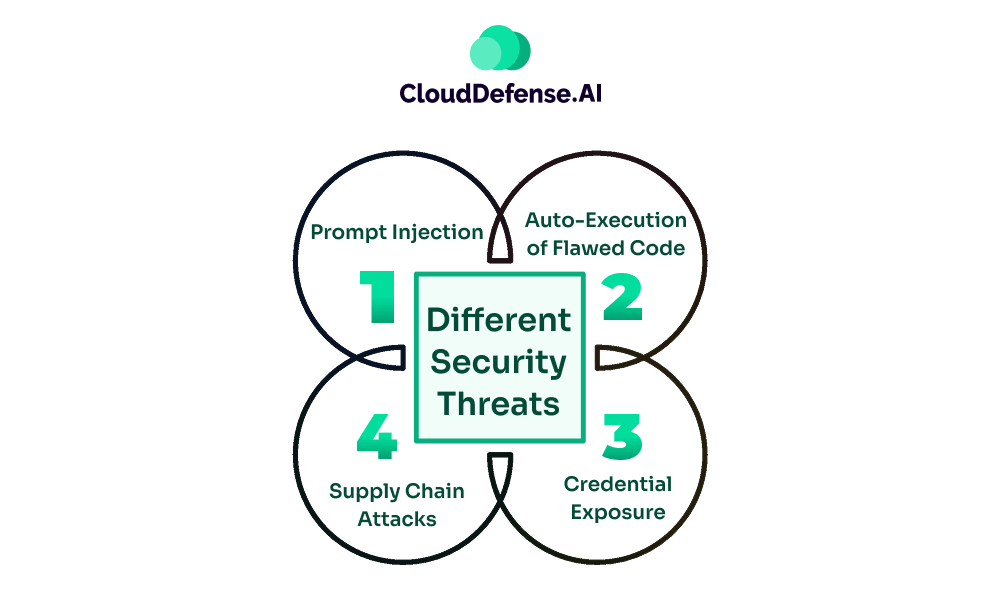
However, it also makes the application prone to different security threats, like:
- Prompt Injection: Malicious or specially crafted prompts by attackers can lead to modifying any files or running commands.
- Auto-Execution of Flawed Code: In the default settings of Cursor, threat actors hold the capability to implant autorun instructions in any repository. The malicious code gets silently executed when the project opens, causing information leakage or malicious modification.
- Credential Exposure: AI-generated codes often carry sensitive data like API keys or credentials. They carry the credentials through suggestion or session control commits.
- Supply Chain Attacks: In Supply Chain Attacks, The LLMs in Cursor may suggest the use of packages or dependencies from public registries. It can import flawed code into the project, which will allow attackers to exfiltrate.
However, by establishing Cursor AI security, organizations can minimize most security threats to a large extent. Securing the Cursor not only helps in eliminating threats but also benefits the organization in many ways. These benefits are:
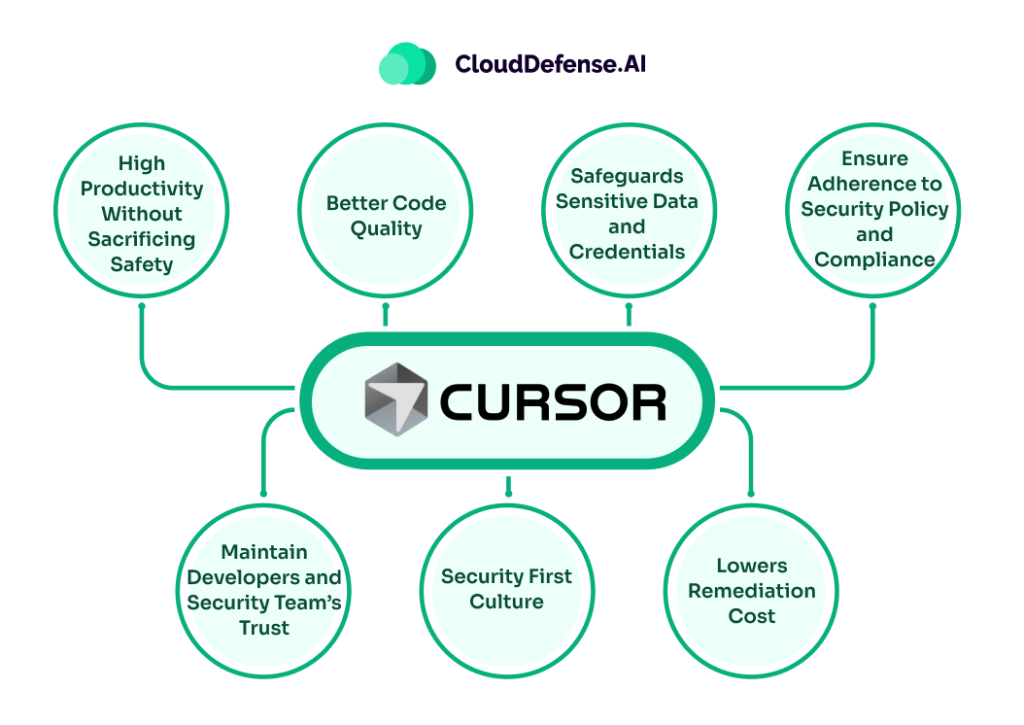
- High Productivity Without Sacrificing Safety: By integrating Cursor code scanning and other security guardrails, developers can safely use AI-generated code without worrying about security threats. Tools like QINA Clarity are utilized to automate code scanning, and they provide developers with security alerts when they are about to use the AI code.
- Better Code Quality: With Cursor editor security, organizations can enforce safe coding practices like input sanitization. It helps in creating a robust and secure application. Moreover, regular scanning and auditing dependencies also help in fixing security flaws that can affect the integrity of AI-generated code.
- Safeguards Sensitive Data and Credentials: A critical reason that every organization should implement Cursor editor security is that it helps in safeguarding sensitive data and secrets. It establishes secret management where it enforces rules and continuous scanning to prevent committing AI code carrying any secrets or sensitive data.
- Ensure Adherence to Security Policy and Compliance: With Cursor AI security, the organization can establish internal coding practices and maintain audit trails. It will not only help the organization to adhere to established security policies but also meet regulatory requirements associated with code security and access control.
- Lowers Remediation Cost: Developer and security teams always aim to fix security flaws in the development phase rather than in the product, as it is a lot cheaper. Integrating the Cursor editor security helps in catching code carrying hardcoded secrets early and prevents the organization from facing huge remediation costs.
- Security First Culture: Introducing security for the Cursor editor enables the organization to establish a security-first culture. It ensures code security is everyone’s responsibility and guides developers to follow secure coding practices.
- Maintain Developers and Security Team’s Trust: Another huge advantage of introducing security guardrails is that it assures developers and security teams that the AI-generated code workflow is secure. The DevSec teams are more likely to trust the AI code suggestion and work with the tool without any issue.
Practical Tips and Tools to Secure Cursor Editor
Securing the Cursor editor has become more important than ever for organizations, as developers nowadays largely rely on AI code generation. However, Cursor AI security is not a straightforward approach.
Here are some tips to secure code in Cursor:
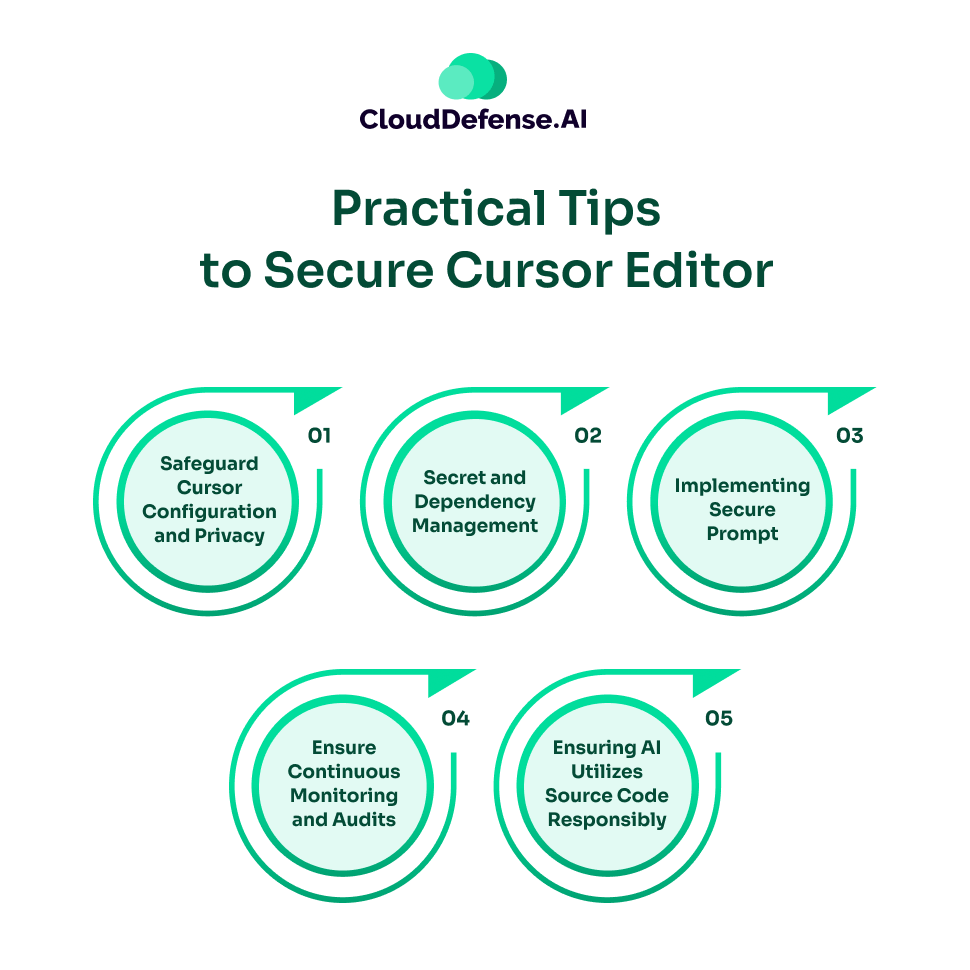
- Safeguard Cursor Configuration and Privacy: The Cursor editor comes with its own set of internal controls that let developers manage how the code interacts with external servers and AI. You should enable the Privacy Mode, which will prevent the tool from using the organization’s lines of code for model training. It is important to turn off the Auto Run Mode, which will prevent the editor from automatically executing commands without any review. Developers can also enable the MCP Tool Protection and Workspace Trust settings to prevent threats of malicious extensions and external scripts.
- Secret and Dependency Management: To properly secure Cursor AI, the organization also needs to securely manage the dependencies and secrets. A lot of security threats originate due to leaked secrets and vulnerable dependencies. Cursor comes with an integrated terminal, which can be used for running audit commands. It will make sure all packages are secure for usage. Developers should never hardcode passwords, tokens, or API keys in the source code. When these codes move to production, they can compromise the whole application.
- Implementing Secure Prompt: How developers interact with the Cursor prompt determines the security of the output. Developers need to integrate security into their prompts, which will ensure the AI doesn’t involve code with vulnerable patterns. It is vital that developers explicitly mention prompts with security when asking Cursor to create a feature involving sensitive data. A great way to ensure a secure prompt is by utilizing the Cursor rule feature and creating a rule set for the specific project. The rule set will establish security standards for developers while making prompts. Developers can even introduce Context or Reference in their commands so that it can direct the AI towards the existing security policies and enable it to follow them.
- Ensure Continuous Monitoring and Audits: To establish a robust Cursor AI security, organizations need to implement continuous monitoring and auditing of the generated code. The developers should consider all the AI-generated code as untrusted and should properly analyze it before committing it. All the command logs should be regularly audited, as they will allow the DevSec team to identify anomalies or flawed actions. Developers should be aware of the new dependencies suggested by Cursor, and they should properly security analyze them before leveraging them.
- Ensuring AI Utilizes Source Code Responsibly: Cursor comes with Code with Source features, which allows the tool to index the complete source code. It helps the AI to make contextual code suggestions. However, organizations need to be careful how they allow Cursor AI to access sources, especially if it is sensitive data or proprietary code. Developers should carefully direct the AI towards repositories carrying sensitive data. To regulate the access of AI to sensitive code segments, developers can implement role-based access control at appropriate stages.
Implementing these tips won’t be sufficient for Cursor AI security; organizations also need to integrate security tools in their Cursor workflow.
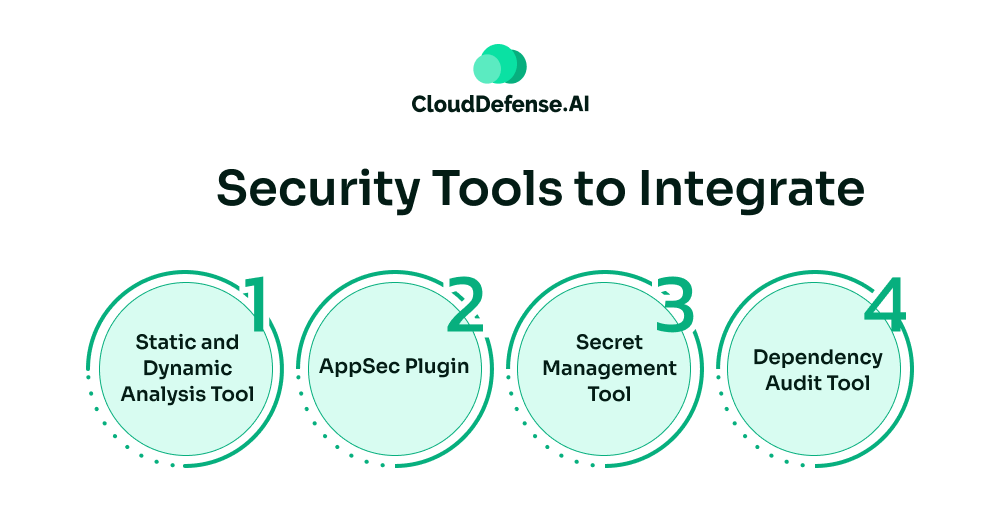
- Static and Dynamic Analysis Tool: Integrating SAST and DAST tools into the IDE is one of the best ways to analyze AI-generated code and provide feedback before they are committed. AI SAST tools like QINA Clarity can effectively take up this role. In addition, DAST tools also need to be integrated that help in testing the running application. As an alternative, organizations can leverage the capability of QINA Pulse and find any vulnerability associated with Cursor through a simple command.
- AppSec Plugin: Many AppSec tools like QINA can be integrated with Cursor, and it will automate the vulnerability detection and remediation process. It will ensure that Cursor provides AI code that is free from any security flaws.
- Secret Management Tool: To prevent exposure of credentials like API keys or passwords through hardcoded secrets, it is vital to utilize a secret management tool. An organization can utilize SCA tools to automate the detection of secrets in the AI code before they are committed. Otherwise, QINA Pulse can be directed through simple commands to automate the detection of secrets in the AI-generated code from Cursor.
- Dependency Audit Tool: The Organization can also introduce dependency audit tools that will specifically perform package verification checks through pre-commit hooks or plugins. It will make sure that Cursor can only introduce new packages when it is properly vetted.
Bottom Line
AI-powered code editor, Cursor, has revolutionised how developers build software by helping them to create code with ease. However, it has also introduced new attack vectors. For establishing Cursor AI security, organizations can’t just rely on default security guardrails. It is important that they apply appropriate security efforts and tools that will ensure optimum Cursor editor security.
This guide not only offers effective tips but also vital tools like QINA Clarity that will help with Cursor code scanning and provide real-time feedback. By following these tips and integrating the tools, the organization can completely utilize Cursor without adding vulnerable code or exposing sensitive data.







