What Is Malicious Code?
Malicious code refers to any form of code intentionally designed to cause harm or compromise the security of computer systems or networks. This includes a variety of malicious programs such as viruses, worms, Trojan horses, ransomware, logic bombs, and other types of malware.
Essentially, malicious code serves as the language through which threat actors communicate with computers, manipulating them to carry out unauthorized actions or exploit vulnerabilities. These actions may involve damaging, altering, or breaching network defenses to achieve the attacker’s objectives.
Malicious code poses a significant threat to cybersecurity as it can be reused, automated, and concealed within software systems, making it challenging to detect and mitigate using conventional antivirus software alone. This broad category includes various attack scripts, backdoors, rootkits, and other complex techniques to evade traditional security measures.
How Can Malicious Code Cause Damage?
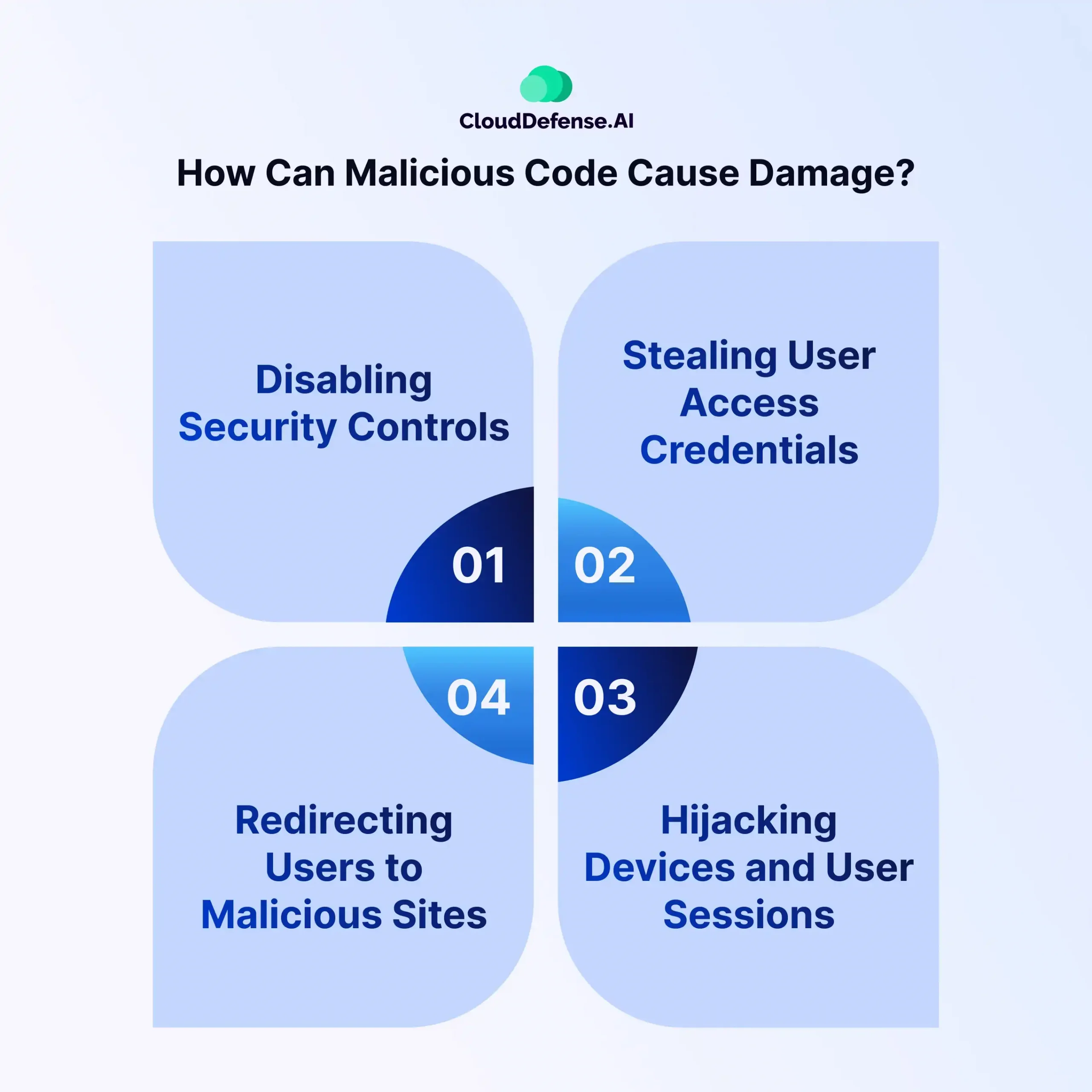
Malicious code can wreak havoc on both individuals and organizations, causing a wide range of damages and disruptions to cybersecurity. Here’s a breakdown of how malicious code can cause significant harm:
Disabling Security Controls
Malicious code can target and disable essential cybersecurity measures, such as antivirus software, firewalls, and monitoring tools. By doing so, hackers can facilitate the spread of additional malicious code and compromise the overall security posture of a device or network.
Stealing User Access Credentials
Cybercriminals use malicious code to covertly obtain user access credentials through various means, including spyware and phishing campaigns. By acquiring sensitive login information, hackers can gain unauthorized access to personal accounts, compromising sensitive data and potentially leading to identity theft.
Hijacking Devices and User Sessions
Malicious code enables hackers to hijack devices within a network, granting them unauthorized access and control. Additionally, cybercriminals can impersonate legitimate users by hijacking their sessions, allowing them to carry out malicious activities undetected, such as data theft or the installation of additional malware.
Redirecting Users to Malicious Sites
Hackers utilize malicious code to manipulate browsers and DNS records, redirecting users to fraudulent websites. These malicious sites may trick users into divulging sensitive information, exposing them to phishing scams, pharming attacks, or “malvertising”.
How does Malicious Code Work?
Malicious code functions through a systematic process of probing, programming, exposing, and executing, orchestrated by cyber attackers to compromise computer systems and networks for nefarious purposes. Beginning with the identification of vulnerabilities, attackers meticulously probe systems to pinpoint weaknesses that can be exploited.
They then craft code specifically tailored to exploit these vulnerabilities, often utilizing a variety of scripting languages and programming techniques. Once developed, the malicious code is deployed to target systems, either through direct interface ports or online network connections. Upon exposure, the code is executed, unleashing a range of harmful actions, from data theft and system corruption to unauthorized access and control.
The repercussions of malicious code can be severe, causing disruptions to personal and professional lives and posing significant risks to individuals and organizations alike. It underscores the critical importance of strong cybersecurity measures to detect, prevent, and mitigate the impact of these malicious attacks.
Types of Malicious Code
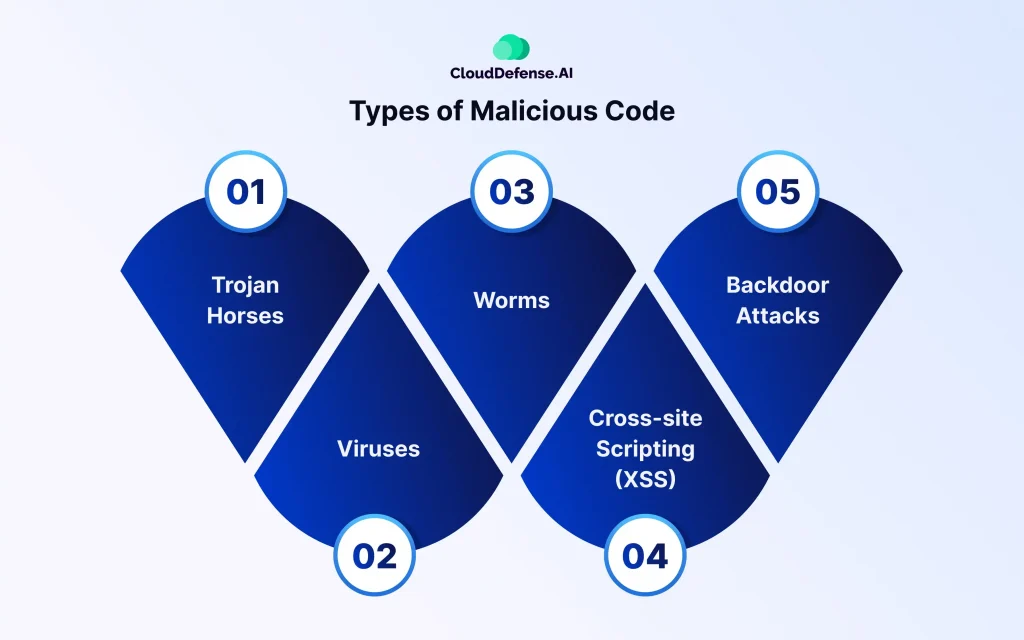
Malicious codes come in various different forms. Here are a few types for your understanding.
Trojan Horses
Inspired by the legendary story of the Greeks deceiving the Trojans with a wooden horse, Trojan Horses are deceptive files that carry malicious code. Disguised as legitimate programs, Trojan Horses execute dangerous actions in the background without the user’s knowledge. They can’t reproduce or spread themselves but may contain viruses, worms, or other damaging code.
Viruses
Viruses are self-replicating malicious software that attaches itself to macro-enabled programs and spreads to other computers. They come in various forms, including Polymorphic, Compression, Macro, Boot sector, Multipart, and Stealth viruses. Viruses require a carrier, such as USB connections or downloaded files, to infiltrate devices and networks.
Worms
Unlike viruses, worms can spread themselves without attaching to a program. They utilize self-replicating code and exploit security flaws in computer networks to propagate. Worms are highly infectious and can cause bandwidth degradation or denial of service through aggressive self-propagation. Notable examples include the Stuxnet worm, used to sabotage Iran’s nuclear program.
Cross-site Scripting (XSS)
Cross-site scripting injects malicious commands into web applications, altering web content, intercepting confidential information, or infecting users’ devices. This attack interferes with users’ web browsing experience and poses a significant threat to web security.
Backdoor Attacks
Backdoor attacks involve creating hidden access points in software applications to provide remote access to cyber criminals. These backdoors can expose sensitive data, enable advanced persistent threats, and facilitate lateral movement within compromised systems. They pose a severe risk to national security and organizational cybersecurity.
How does Malicious Code Spread?

Malicious code spreads through various channels and vectors, infiltrating systems and devices to carry out its harmful activities. Here’s how it spreads:
Online Networks
Malicious code can spread through online networks, including intranets, peer-to-peer file-sharing platforms, and public internet websites. Attackers may exploit vulnerabilities in these networks to distribute malware to unsuspecting users.
Social Communications
Email, SMS, push content, and mobile messaging apps serve as common vectors for the spread of malicious code. Attackers often use phishing techniques to trick users into clicking on malicious links or downloading infected attachments, thereby infecting their devices.
Wireless Connectivity
Malicious code can spread through wireless connectivity channels such as Bluetooth. Attackers may use Bluetooth vulnerabilities to transmit malware to nearby devices without the user’s knowledge or consent.
Direct Device Interfaces
Malicious code can also spread through direct device interfaces like USB connections. Public USB charging stations and compromised software update tools have been exploited by attackers to inject malware into devices connected via USB.
Visiting Infected Websites
Infected websites can serve as gateways for malicious code to enter users’ systems. By visiting compromised websites or clicking on malicious advertisements, users may inadvertently download malware onto their devices.
Email and Text Messages
Malicious code often spreads through email and text messages containing infected attachments or links to malicious websites. These messages may appear legitimate, tricking users into interacting with them and inadvertently infecting their devices.
Software Downloads
Malicious code can be bundled with legitimate software downloads or distributed through software piracy websites. Users may unknowingly download and install malware-infected software, allowing the code to infiltrate their systems.
Scam Links on Social Media
Attackers may spread scam links on social media platforms, enticing users to click on them with promises of enticing offers or sensational content. These links often lead to websites hosting malware, leading to the infection of users’ devices.
Examples of Malicious Code Attacks
Examples of malicious code attacks illustrate the diverse tactics used by cybercriminals:
- Stuxnet Worm: Emerging in 2010, Stuxnet targeted industrial control systems, notably Iran’s nuclear facilities. It exploited zero-day vulnerabilities to infiltrate systems via USB flash drives, causing physical damage to critical infrastructure. While Stuxnet’s activity has waned, its legacy persists as a benchmark for targeted cyber attacks on vital systems.
- Emotet Trojan: Since 2014, Emotet has evolved into a sophisticated threat spread through email spam and phishing campaigns. It tricks users into downloading malware, enabling various malicious activities like delivering additional malware payloads and stealing sensitive information.
Detection and Removal of Malicious Code
Detection and removal of malicious code are crucial steps in maintaining cybersecurity. Here’s how to tackle these tasks effectively:
Indicators of Malicious Code
Before using detection tools, there are a few ways you can find out that there is a probability of your system containing malicious code.
- Performance Issues: Frequent crashes, slowdowns, or malfunctioning of essential functions could indicate malware presence.
- Strange Behavior: Unexplained changes to files or activities initiated without user input may suggest malware activity.
- Suspicious Activities: Sudden increases in internet traffic or the appearance of mysterious files on the hard disk could be signs of malware.
Detection
Here are some detection methods that you can use to find malicious code in your IT systems.
- Utilize Malware Detection Tools: Services like Web Application Firewalls can block malware injection attacks by employing signature, behavioral, and reputational analysis at the edge of your network.
- Monitor for Backdoors: Implement services like Backdoor Protect to intercept communication attempts with backdoor shells on web servers. This helps identify highly obfuscated malware even if it was installed before implementing security measures.
- Implement Two-Factor Authentication (2FA): Deploy solutions like Login Protect, which offer flexible 2FA to prevent unauthorized access using stolen credentials, thereby thwarting malware installation attempts.
Removal
Once malicious codes have been detected, this is how you can remove them from your system.
- Security Scans: Perform thorough scans on your devices using reliable security software to detect and remove malware.
- Update Software: Uninstall vulnerable software and download the latest versions with enhanced security features and patches.
- File Inspection: Delete suspicious files and clear browser caches to eliminate any potential malware remnants.
Prevention
Removal of the malicious code shouldn’t be the last step. Follow these preventive measures below to stop the future spread of malware in your computers.
- Use Antivirus Software: Install antivirus and anti-malware software with automatic updates and real-time protection features.
- Regular Updates: Ensure routine maintenance, including updating systems, plug-ins, and critical software, to patch vulnerabilities.
- Practice Secure Browsing: Exercise caution with unfamiliar URLs and email attachments to avoid inadvertently downloading malware.
- Secure Networks: Be wary of public Wi-Fi networks that lack authentication, as attackers may exploit them to deliver malicious code.
- Backup Data: Implement data backup strategies to protect critical applications and information, enabling quick recovery in the event of a malware attack.
Malicious Code Protection with CloudDefense.AI
CloudDefense.AI offers protection against malicious code by using advanced AI-driven capabilities. Through real-time threat detection and complete visibility into cloud activities, it identifies both known and unknown threats, including zero-day attacks and insider threats. The platform’s risk-based prioritization ensures that critical vulnerabilities are addressed promptly, maximizing resource efficiency.
Additionally, CloudDefense.AI’s graph-driven investigation tools provide detailed insights into incidents, enabling swift remediation. By detecting misconfigured APIs, it helps prevent unauthorized access and data exposure. With CloudDefense.AI, companies can proactively protect their cloud infrastructures and mitigate the risks posed by malicious code.
Conclusion
Malicious code poses a significant threat to individuals and organizations. With its ability to infiltrate systems through deceptive means, malware can cause grave harm to data and infrastructure.
However, by employing strong malware detection techniques, adopting multi-layered security measures, and leveraging advanced technologies like CloudDefense.AI, organizations can effectively defend against these cyber threats and ensure a secure operating environment.
Book a free demo now to experience the power of next-gen cloud-based security.







