What is Malware?
Malware, short for malicious software, refers to any software intentionally designed to damage, disrupt, or exploit computer systems, networks, or their users. Cybercriminals create malware to carry out a variety of harmful activities, such as stealing sensitive data, holding systems hostage, or disrupting critical operations.
Malware comes in various forms, including:
- Ransomware: Encrypts data and demands payment for its release.
- Trojan Horses: Disguised as legitimate software to deceive users and gain access to systems.
- Spyware: Secretly monitors and collects user information without consent.
- Adware: Delivers intrusive ads, often collecting user data in the process.
Malware plays a central role in modern cyberattacks. Every year, billions of malware attacks target individuals, businesses, and government entities, exploiting vulnerabilities across all devices and operating systems, including Windows, macOS, iOS, and Android.
How does Malware Work?
Malware, short for malicious software, operates with a single purpose: to disrupt, damage, or gain unauthorized access to a system or network. Cybercriminals use malware as a tool to steal data, harm devices, or exploit victims for financial gain. Here’s how malware typically works:
Delivery and Infection
Malware doesn’t just appear on your system—it needs to find a way in. Cybercriminals often deliver malware through phishing emails, malicious websites, software downloads, or infected USB drives. For example:
- You might receive an email with a convincing link or attachment that, when clicked, installs the malware.
- Visiting a compromised website can trigger a download without your knowledge, known as a drive-by download.
Once inside your system, the malware embeds itself in critical files or programs, often hiding its presence to avoid detection.
Activation
After infection, the malware activates when you open the infected file, launch a program, or meet specific conditions set by the attacker. For example, ransomware might stay dormant until triggered by a certain date or action.
Execution of Malicious Actions
The type of malware determines what it does next:
- Viruses attach themselves to legitimate files, replicating and spreading whenever the file is shared.
- Worms move across networks without human interaction, infecting multiple devices quickly.
- Ransomware locks your files or system and demands payment for access.
- Spyware operates in the background, quietly collecting sensitive information like passwords or credit card details.
- Trojans disguise themselves as harmless software, tricking you into installing them, only to create backdoors for attackers.
Stealth and Persistence
Modern malware is designed to stay hidden and persist over time. It may disable antivirus software, mask its activity, or create multiple copies of itself to make removal difficult.
Communication with the Attacker
Many types of malware communicate with a command-and-control server. This allows attackers to:
- Extract stolen data (like passwords, financial information, or intellectual property).
- Send new instructions to the malware, such as launching additional attacks.
Impact on the Victim
The consequences of malware can vary depending on its purpose:
- Loss of sensitive data, which can lead to identity theft or financial fraud.
- System slowdowns, crashes, or complete device failure.
- Financial extortion in the case of ransomware.
Differences Between Malware and Virus
While often thought of as the same, malware and viruses are different concepts in cybersecurity. A virus is a specific type of malware. It operates by attaching itself to legitimate programs or files, replicating its code, and spreading from one system to another. Viruses are often activated when the infected program is executed, causing harm such as corrupting files, slowing down devices, or even rendering systems inoperable.
Key Differences Between Malware and Virus
| Aspect | Malware | Virus |
| Definition | A general term for any malicious software. | A specific type of malware that replicates by infecting other programs. |
| Scope | Includes viruses, ransomware, spyware, worms, Trojans, etc. | Limited to programs that self-replicate by attaching to files or programs. |
| Propagation | Spread through various methods, including phishing, malicious links, and downloads. | Spreads by embedding itself in legitimate programs or files. |
| Purpose | Can steal data, disrupt systems, or hold devices hostage. | Typically disrupts performance, corrupts files, or spreads further. |
| Activation | May execute automatically or require user action. | Requires the host program or file to be executed. |
Are All Viruses Malware?
Yes, viruses fall under the broader category of malware. However, not all malware are viruses. Malware can act in ways that viruses cannot, such as infiltrating systems without replication or spreading via network vulnerabilities.
Types of Malware
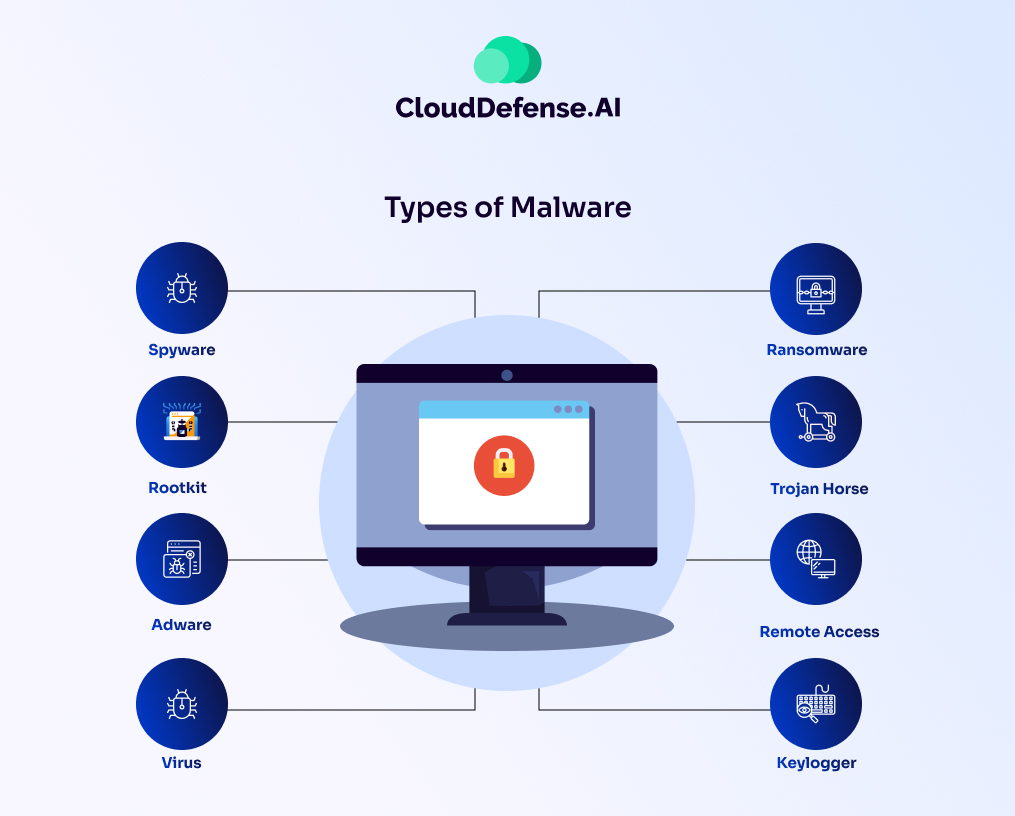
Malware isn’t a monolithic entity. It comes in a variety of forms, each with its unique way of causing trouble. Here’s a closer look at some of the most common types of malware:
- Viruses: These malicious programs replicate themselves and spread from device to device, often by attaching themselves to legitimate files. They can cause a variety of problems, from disrupting system performance to corrupting or deleting files.
- Worms: Similar to viruses, worms can self-replicate, but they exploit network vulnerabilities to spread from computer to computer. They can quickly overwhelm a network and consume resources.
- Trojan Horses (Trojans): Unlike viruses and worms, Trojans don’t replicate themselves. Instead, they disguise themselves as legitimate software, tricking users into installing them. Once installed, Trojans can steal data, install other malware, or give attackers remote access to your device.
- Ransomware: This particularly nasty type of malware encrypts your files, making them inaccessible. Ransomware attackers then demand a ransom payment in exchange for the decryption key.
- Spyware: Spyware is a stealthy malware that operates in the shadows, monitoring your activity and stealing your sensitive data, such as login credentials, browsing history, and even keystrokes.
- Scareware: This social engineering tactic preys on fear. Scareware bombards you with fake security alerts and warnings about nonexistent threats. These pop-ups often urge you to download useless or even malicious “security software” to fix the non-existent problems. Scareware thrives on panic, so staying calm and using reputable security software is the best defense.
- Adware: While not as destructive as other types of malware, adware bombards you with unwanted advertisements, pop-ups, and banners. It can slow down your system and be a nuisance.
- Rootkits: These particularly dangerous programs give attackers root-level access to your system, allowing them complete control. Rootkits can be very difficult to detect and remove.
- Keyloggers: These malicious programs record every keystroke you type, allowing attackers to steal your passwords, credit card information, and other sensitive data.
- Fileless Malware: This newer type of malware doesn’t rely on traditional files. It leverages legitimate system tools and processes to operate, making it more difficult to detect with traditional antivirus software.
- Cryptojacking Malware: This malware hijacks your device’s processing power to mine cryptocurrency for the attacker’s benefit. This can slow down your system performance significantly.
How does Malware Spread?
Malware doesn’t magically appear on your devices. Cybercriminals employ a variety of cunning tactics to trick you into installing it or exploit weaknesses in your system. Here are some common methods used to spread malware infections:
| Method | Description | How to Protect Yourself |
| Deceptive Downloads | Malware disguises itself as legitimate software, such as useful tools, games, or updates. Users unknowingly download it via malicious links or websites. | Avoid downloading files from untrusted sources or clicking on suspicious links. |
| Malicious Email Attachments | Phishing emails often carry infected attachments, disguised as documents, invoices, or greeting cards. Opening them activates the malware. | Avoid opening unsolicited attachments and verify email senders before interacting with attachments. |
| Exploiting Software Vulnerabilities | Outdated software contains security flaws that malware can exploit to infiltrate systems. | Regularly update your operating system and applications to patch vulnerabilities. |
| Infected Removable Media | USB drives, external hard drives, or SD cards can carry malware, transferring it when connected to a device. | Scan removable media with antivirus software before use. |
| Drive-by Downloads | Visiting compromised websites may trigger automatic malware downloads via browser or plugin vulnerabilities. | Keep browsers and plugins updated and avoid visiting suspicious websites. |
| Unsecured Wi-Fi Networks | Public Wi-Fi networks can allow hackers to intercept data and inject malware into connected devices. | Use encrypted connections or VPNs when on public Wi-Fi. |
| Malicious Advertisements (Malvertising) | Legitimate-looking online ads redirect users to infected sites or install malware when clicked. | Use ad blockers and avoid clicking on ads from untrusted sources. |
| Social Engineering Tactics | Cybercriminals trick users into downloading malware through fake alerts about system issues or offers for fixes. | Be skeptical of pop-ups or alerts urging downloads; verify their authenticity before acting. |
| Peer-to-Peer (P2P) Sharing | Malware is often embedded in unverified files shared on P2P platforms or torrent networks. | Avoid downloading files from unverified sources and use reputable sharing platforms. |
By being aware of these methods, you can be more cautious about what you download, where you browse, and how you connect to the internet. This will significantly reduce your risk of falling victim to a malware infection.
How to Spot a Malware Infection?
Malware often operates in the background, making it hard to detect, but there are signs that something may be amiss with your device. Here’s what to watch for:
- Slow Performance: Is your device suddenly sluggish? Malware can consume system resources, causing slow performance, longer boot times, and frequent crashes.
- Unusual Pop-Ups and Ads: If you’re seeing a barrage of unwanted pop-ups, intrusive ads, or unexplained changes to your browser settings, adware or malware could be the culprit.
- Unknown Programs: Finding applications you don’t remember installing is a red flag. These could be malicious programs running without your permission.
- Disabled Security Software: If your antivirus or anti-malware tools are turned off or can’t update, it might be malware interfering with your security measures.
- Frequent System Crashes: Unexpected crashes or error messages, especially when running standard applications, can point to a potential malware infection.
- Missing or Corrupted Files: If your files are disappearing or showing signs of corruption, it could be malware tampering with your data.
- Network Issues: Unexpected spikes in data usage, strange outgoing connections, or difficulty accessing the internet could signal malware communicating with external servers.
- Overheating: If your device overheats without heavy usage, it might be due to malware using excessive system resources.
What to Do If You Suspect Malware?
Not all these signs definitively indicate malware, but experiencing multiple symptoms should prompt you to act. Run a full system scan using updated antivirus software, and consider using a dedicated malware removal tool to ensure your device is clean.
Being vigilant and proactive can save you from the harm malware can cause.
How to Remove a Malware Infection?
Once you’ve detected a malware infection, swift action is critical to prevent further damage. Follow these steps to remove malware from your device:
- Disconnect From the Internet: The first step is to disconnect your device from the internet. This prevents the malware from spreading to other devices or sending data to its remote server.
- Enter Safe Mode: Reboot your computer into ‘Safe Mode’. This limits the number of programs that can run, preventing the malware from operating while you troubleshoot.
- Run a Malware Scan: Use reliable antivirus or anti-malware software to perform a full system scan. Ensure your security software is up to date, as newer threats may evade older versions.
- Review and Quarantine Suspicious Files: After the scan, review the flagged files. Most antivirus tools will allow you to quarantine or delete them. Be cautious about deleting essential system files if flagged incorrectly.
- Uninstall Unknown Programs: Check your list of installed programs and remove any suspicious or unknown applications. Use your operating system’s built-in uninstallation tools to do this safely.
- Clear Your Browser: Malware can modify browser settings. Reset your browser to its default settings, clear cookies, and delete cached data to remove lingering traces.
- Update Software and Operating System: After removing the malware, update all your software and operating system. This patches vulnerabilities that the malware may have exploited.
- Enable Real-Time Protection: Activate real-time protection features in your antivirus software to monitor and block potential threats in the future.
- Scan External Devices: If you’ve used USB drives or external hard drives, scan them for infections. Malware can spread through these devices, reinfecting your system.
- Seek Professional Help if Needed: If the infection persists or you’re unsure about the next steps, consult a professional IT specialist. They can ensure your system is thoroughly cleaned and secure.
Removing malware is only the first step—preventing future infections is equally important. Regularly update your software, avoid suspicious downloads, and practice good cybersecurity hygiene to keep your system safe.
How to Proactively Prevent Malware Infections?
Having just battled a malware infection can be frustrating, but the good news is that you can reduce your risk of future infections by following essential preventative measures. Here’s how to fortify your defenses:
- Keep Your Software Updated: Outdated software is a common entry point for malware. Regularly update your operating system, applications, and security software to patch vulnerabilities.
- Use a Reputable Antivirus Program: Install trusted antivirus or anti-malware software and ensure it includes real-time protection. Schedule regular scans to detect and remove potential threats.
- Be Cautious With Email Attachments and Links: Avoid opening unsolicited email attachments or clicking on links from unknown senders. Phishing scams are a common malware delivery method.
- Download Only From Trusted Sources: Stick to official app stores and trusted websites for software downloads. Avoid third-party sources, as they often harbor malware-laden programs.
- Enable a Firewall: A firewall acts as a barrier between your device and malicious traffic. Ensure your device’s built-in firewall or a third-party firewall is enabled and properly configured.
- Practice Safe Browsing Habits: Avoid visiting suspicious websites or clicking on pop-up ads. Use a browser with built-in security features and consider ad-blocking extensions to reduce risks.
- Regularly Back Up Your Data: In the event of a malware infection, having an up-to-date backup ensures you don’t lose important files. Use cloud-based solutions or external storage for backups.
- Use Strong, Unique Passwords: Weak passwords make you vulnerable to attacks. Use strong, unique passwords for each account and enable multi-factor authentication (MFA) whenever possible.
- Be Wary of Public Wi-Fi: Avoid connecting to unsecured public Wi-Fi networks, which can expose you to malware and other threats. If you must use public Wi-Fi, always use a VPN to encrypt your connection.
- Educate Yourself and Others: Stay informed about common malware threats and share this knowledge with family, friends, or coworkers. Awareness is one of the best defenses against cyberattacks.
Proactively preventing malware infections requires vigilance and consistent cybersecurity practices. By combining these measures with a robust security mindset, you can keep your devices safe and enjoy peace of mind while navigating the digital world.
Final Words: Stay Vigilant, Stay Secure
The fight against malware is an ongoing battle, but by following the steps outlined above, you can significantly reduce your risk of infection. Remember, cybercriminals are constantly developing new methods, so it’s crucial to stay vigilant and informed about the latest threats.
Here at CloudDefense.AI, we are committed to providing cutting-edge security solutions that keep your devices and data safe. Our advanced technology utilizes artificial intelligence to proactively identify and neutralize malware threats before they can cause harm.
Ready to learn more and see CloudDefense.AI in action? Request your free demo today and experience the power of our comprehensive security solutions.







