Protecting Series A/B Companies
Take Your Security to the Next Level and Protect Your Growth!
As your startup scales, strong cybersecurity is essential to secure investor confidence and protect your expanding operations. Our platform delivers advanced threat detection, continuous monitoring, and swift incident response, ensuring you’re prepared to tackle security challenges.
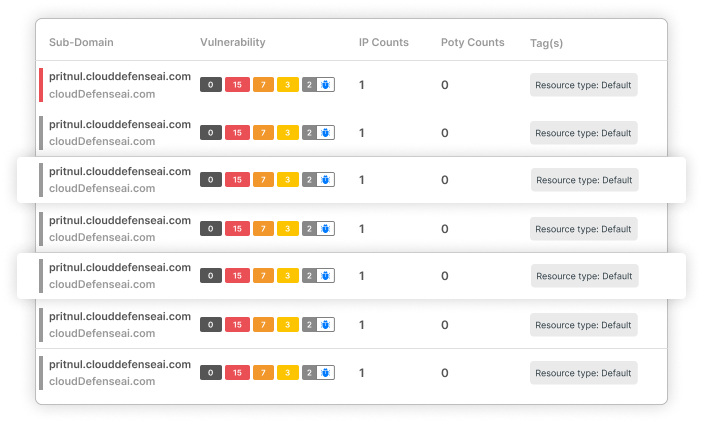
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
Strengthen Your Deals
Enhance Your Growth: Complete Cybersecurity Solutions for Series A/B Companies
Scaling fast but worried about security gaps? Struggling to keep pace with compliance needs? As a Series A/B company, your focus is on growth but that growth shouldn’t come at the cost of security. Our platform empowers you to strengthen your infrastructure, providing real-time insights, active risk management, and protection across every touchpoint. Protect your business as it expands, ensuring every step forward is a secure one—all through a powerful, unified solution designed with your scaling needs in mind!

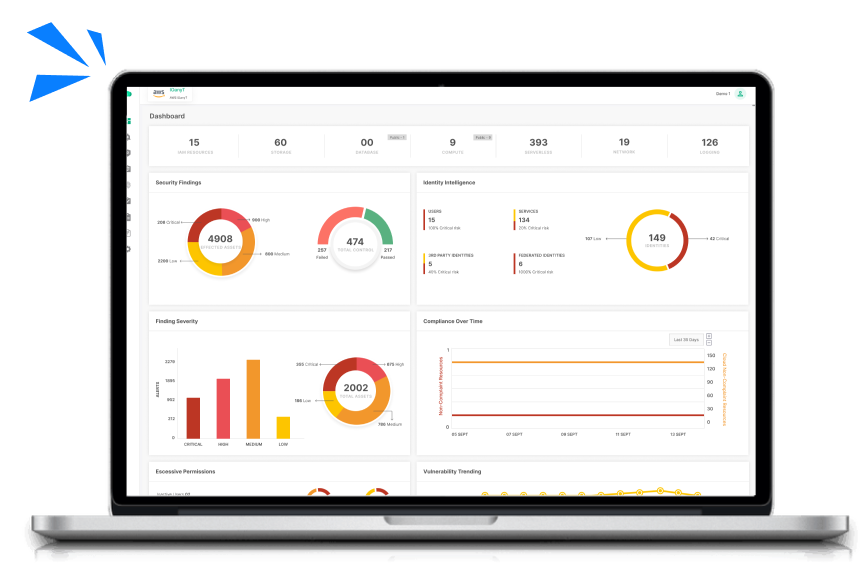
Achieve Complete Visibility
Gain a deep understanding of your entire IT landscape. Our platform meticulously examines your systems, applications, and networks to uncover potential security risks that could compromise your growth. Gain clarity on how each component contributes to overall security and operational resilience.

Reduce Operational Risks Early On
Avoid growth roadblocks by addressing cybersecurity risks before they escalate. From outdated software to misconfigured networks, we help you identify and rectify issues that could hinder operations or devalue your company in the eyes of investors.

Implement Strong Security Measures
Secure your company with cybersecurity strategies customized to your growth stage. Protect sensitive data, maintain regulatory compliance, and prevent unauthorized access as you scale.
Your Growing Startup Faces New Threats
Series A/B Companies Are Prime Targets for Cyberattacks!
As your company attracts attention from investors, it also becomes a target for cybercriminals. Don’t let security vulnerabilities hinder your progress!
The Numbers Don’t Lie!
$2.5 M
Data breaches cost small businesses an average of $2.5 million.
50%
Only 50% of small businesses have a formal cybersecurity plan.
300%
Ransomware attacks increased by 300% in the last year, with small businesses being prime targets.
The Stakes Are Higher Than Ever—Can You Afford the Risk?
Don’t allow security gaps to stall your growth. Protect your assets, your reputation, and your future with our specialized cybersecurity services for Series A/B companies.
With CloudDefense.AI, Your Growth is Protected
Don’t Let Cyber Threats Derail Your Startup’s Success!
Navigating the complexities of scaling while managing cybersecurity risks can be challenging. CloudDefense.AI simplifies this process, enabling you to identify, address, and minimize risks efficiently, so you can focus on growth.
Here’s How We Turn Cybersecurity Into a Growth Enabler for Your Startup:
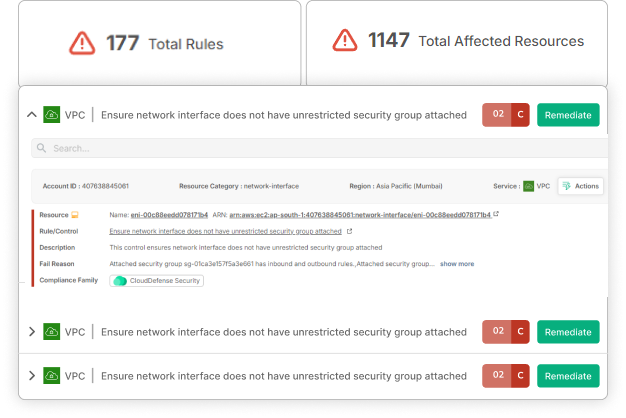
From Complexity to Clarity:
Smooth Integration
Automate your security processes, making them an effortless part of your scaling strategy.
Dual-Layer Defense
Our platform addresses both threat detection and compliance, keeping you secure as you grow.
Rapid Remediation
Our advanced diagnostics quickly identify and fix vulnerabilities, protecting your operations from disruption.
Actionable Insights, Not Overwhelming Data
Concise Reporting
Receive clear, actionable insights that empower you to make informed, data-driven decisions.
Prioritized Compliance
Our tools simplify compliance management, ensuring your growth isn’t hindered by security gaps.
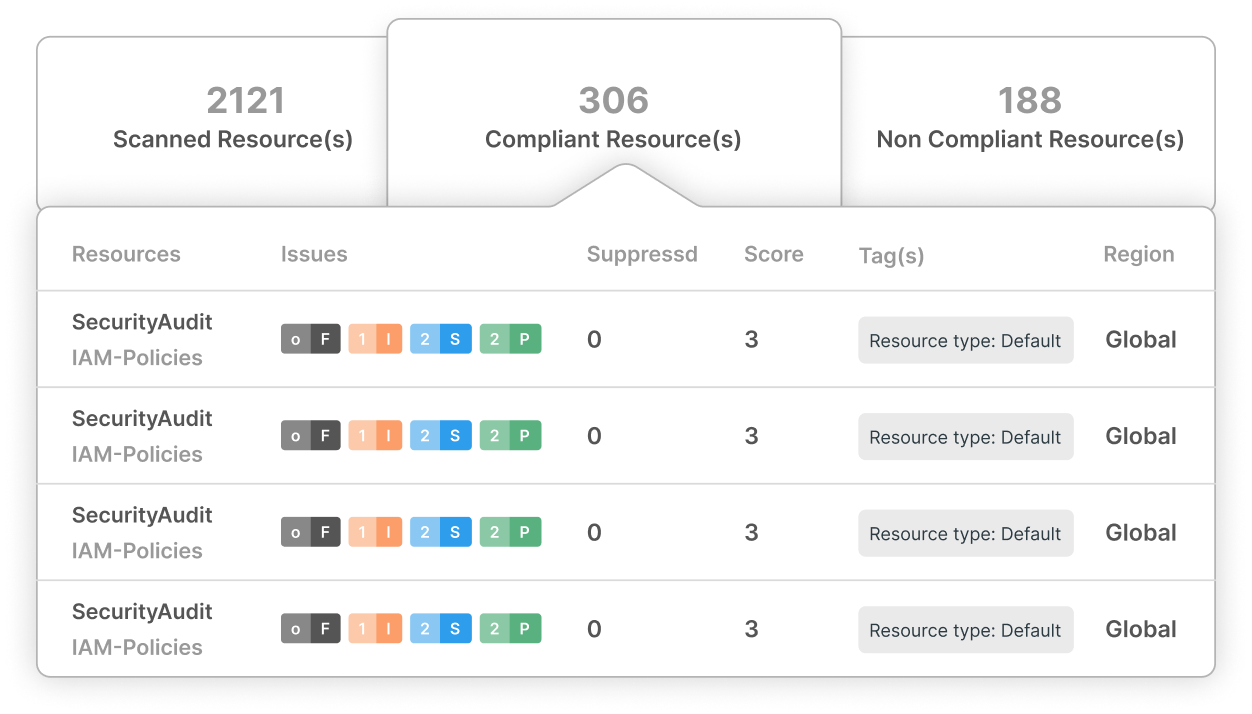
Customized Security for Scaling Startups
Flexible and Scalable
CloudDefense.AI adapts to your growth, offering continuous protection across all digital assets.
Third-Party Risk Management
Monitor and secure all third-party interactions to maintain a comprehensive security posture.
Beyond Security—It’s Strategic Growth
Proactive Risk Management
Simplify risk management and compliance to keep your startup on track for success.
Expert Support
Our team provides ongoing guidance, helping you survive in this competitive start-up industry and optimize your growth strategy.