With the fast-paced growth of data-driven decision-making strategies, many companies are relying heavily on data to understand how customers behave and interact with products. Ensuring the security of this data has taken on an unprecedented level of importance.
In the past, the obstacle to fully leveraging the potential of data was rooted in the limitations of traditional data warehouses—expensive hardware, on-site constraints, and solutions that just weren’t flexible.
But then came Snowflake, a pioneer in the world of SaaS-based platforms. It offers scalability, simplicity, and high performance, all without breaking the bank. However, because Snowflake deals with some seriously sensitive data, it’s crucial to have a deep understanding of its robust security features.
Here we will explore why Snowflake has emerged as the preferred solution for data management and look into some of the Snowflake security best practices.
What Are the Key Features of Snowflake Security?
Snowflake is an innovative cloud-based data platform, redefining the way we approach data warehousing. It takes on the role of a Software-as-a-Service (SaaS) solution and sets itself apart with its impressive scalability, user-friendly simplicity, and top-notch performance. In essence, Snowflake empowers organizations to effortlessly store, handle, and delve into extensive datasets in the cloud, liberating them from the limitations of old-school on-premises alternatives.
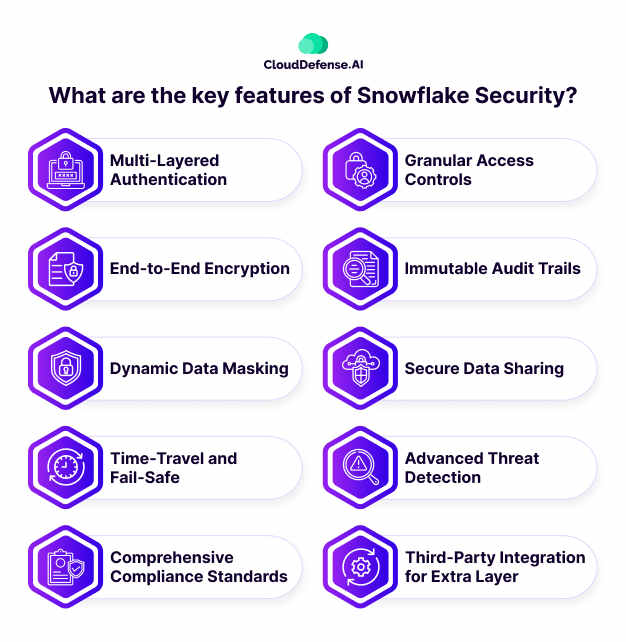
Furthermore, Snowflake offers a comprehensive set of security features designed to protect data at every level of the platform. Here are key features that contribute to Snowflake’s robust security framework:
Multi-Layered Authentication
Snowflake ensures data integrity through multi-layered authentication mechanisms. It makes sure only authorized individuals achieve access by subjecting users to a thorough authentication process, including multifactor authentication. Doing so guarantees that only authorized access happens on the platform.
Granular Access Controls
Here’s where Snowflake truly shines, giving organizations the power to be precise. It offers granular access controls, allowing admins to fine-tune permissions at the schema, table, or even column level. This means you have nuanced control over who can access what within your data infrastructure.
End-to-End Encryption
Security is the top priority from start to finish with Snowflake’s end-to-end encryption. Whether in transit or at rest, data remains encrypted, thwarting potential threats and ensuring confidentiality across all stages of data processing.
Immutable Audit Trails
The immutable audit trails of Snowflake’s security compliance serve as an indelible record of user activity. Such a comprehensive logging system not only aids in compliance but also provides a crucial tool for post-event analysis and forensic investigations.
Dynamic Data Masking
To enhance data privacy, Snowflake employs dynamic data masking. This feature dynamically conceals sensitive information, ensuring that users only see the data they are authorized to access, thus preventing inadvertent exposure of critical details.
Secure Data Sharing
Facilitating collaboration without compromising security, Snowflake enables secure data sharing. Organizations can selectively share data with external parties, confident in the knowledge that access is tightly controlled and monitored.
Time-Travel and Fail-Safe
Snowflake’s time-travel functionality acts as a safety net. Organizations can roll back to previous states of the data, providing a fail-safe mechanism to rectify errors or recover from unforeseen issues, bolstering overall data resilience.
Advanced Threat Detection
Proactively safeguarding against potential threats, Snowflake employs advanced threat detection mechanisms. Snowflake employs advanced threat detection mechanisms, keeping a close eye on things through continuous monitoring and anomaly detection. Real-time identification and mitigation of security risks—that’s how it secures your data environment.
Comprehensive Compliance Standards
Committed to meeting the highest compliance standards, Snowflake provides a platform that adheres to regulatory requirements. Whether it’s GDPR, HIPAA, or others, Snowflake ensures that organizations can confidently manage data in compliance with industry regulations.
Third-Party Integration for Extra Layer
Recognizing the diversity of Snowflake data security needs allows for seamless integration with third-party security solutions. This flexibility empowers organizations to augment native controls with additional layers of security tailored to their specific requirements.
The Most Common Challenges in Snowflake
Data Exposure Risks: One common puzzle for Snowflake users revolves around the potential exposure of data, where sensitive information might be inadvertently accessed or viewed by unauthorized individuals.
Access Complexity: Managing access control within Snowflake can become intricate, especially as user roles evolve and data permissions require constant adjustments. Striking a balance between accessibility and security is like walking a tightrope—it’s a continuous challenge.
Compliance Concerns: Meeting industry-specific compliance standards can be a hurdle, as organizations using Snowflake must navigate a complex landscape of regulations and ensure that their data practices align with the requisite standards.
Security Configuration Overheads: Configuring and optimizing security in Snowflake settings is no walk in the park. It’s like fine-tuning the settings on your favorite gadget—time-consuming and requiring a deep understanding to ensure top-notch protection without making things overly complicated.
Integration Challenges: Integrating Snowflake seamlessly into an existing IT ecosystem poses challenges as organizations must align security measures across various platforms and technologies.
To tackle these challenges, you need a strategic security approach. In the next section, we’ll dive into these security best practices, offering insights on how to effectively deal with these challenges.
Top Snowflake Security Best Practices
1. Data Masking Approach
Data masking plays a crucial role in Snowflake’s security toolkit by discreetly hiding column values during the data loading process. Although the actual data remains intact in the system, the visibility of these values is cleverly concealed based on the user’s role.
This becomes incredibly valuable in situations where storing data is a must for compliance or downstream modeling, but limiting who can see it is of utmost importance.
Creating the Admin Role
To initiate the data masking process, the first step is to establish a dedicated role, perhaps named ‘data_mask_admin.’ This role is then granted the essential privileges to create, apply, and manage masking policies within the relevant schema. Subsequently, the role is assigned to authorized personnel, typically analytics or data engineering professionals responsible for policy application.
| create role data_mask_admin; grant create masking policy on schema [your_db_name.your_schema_name] to role data_mask_admin; grant apply masking policy on account to role data_mask_admin; grant role data_mask_admin to user your_username; |
Implement a Masking Policy for masking Specific Data
Once the role is established, devising a masking strategy means creating conditions that dictate which values in certain columns stay visible. Let’s consider a hypothetical scenario involving employee data, where the salary column needs protection. The masking policy, named ‘hide_salary,’ reveals the salary information only to users with the role ‘HR_MANAGER’.
| create or replace masking policy hide_salary as (val string) returns string -> case when current_role() in (‘HR_MANAGER’) then val else ‘*********’ end; |
Apply a Masking Policy to a Column
Application of this policy to a designated column ensures that only individuals with the ‘HR_MANAGER’ role can view the actual salary values.
| alter table if exists employee_data modify column salary set masking policy hide_salary; |
Crafting a personalized strategy for data masking isn’t just in alignment with Snowflake’s dedication to security—it also highlights its flexibility in meeting various data protection demands. When organizations put these masking policies into action, they can boldly steer through compliance necessities and safeguard sensitive information with precision.
2. Role-Based Access Controls
When you’re tapping into the potential of a cloud data platform like Snowflake, building a strong security foundation boils down to smart access control. The key is tailoring access according to user roles, creating a safe space where users have just enough access for their specific tasks. This forward-thinking approach goes a long way in reducing the risk of data compromise.
Let’s dive into some essential tips for beefing up access control within Snowflake.
Keep it Minimal with Least Privilege: Grant users the bare minimum access needed for their job. For instance, analysts using existing models might only need READ permissions instead of full access to raw data.
Fine-Tune Control with Role-Based Granularity: Make the most of Snowflake’s role-based access control by crafting specific roles with distinct permissions. Match these roles to job responsibilities for tight control over data access.
Lock Down Raw Data Access: Reserve access to raw data for specific individuals, like analytics engineers or those handling data ingestion and transformation. This ensures that sensitive raw data stays protected from any unauthorized meddling.
READ-Only Power: If users just need to peek at the data without making changes, toss them the READ permission. It’s a sweet spot between access and safeguarding the data.
Craft Roles for Different Permissions: Create a fresh role for each unique set of permissions your organization needs. This modular approach makes for a more scalable and easily manageable access control system.
Tool-Specific User Segmentation: Give each tool connected to Snowflake its dedicated user. This nifty practice streamlines the handling of tool-specific access, making it crystal clear which tools are playing with which datasets.
In a nutshell, when it comes to securing your data on Snowflake, it’s all about giving the right people the right access – not too much, not too little. That way, you’re not just locking things down; you’re doing it intelligently.
3. Tagging and Classifying
When it comes to robust data management, Snowflake security best practices, such as tagging and classifying, emerge as instrumental tools that enhance the features of data governance. Tags, which are flexible identifiers at the schema level, go beyond just ensuring security—they play a role in complying with regulations, promoting easy data exploration, and offering valuable insights into how resources are utilized.
Initiating the tagging process involves the creation of a specialized role, such as ‘label_admin,’ tasked with managing tags. This role is bestowed with the necessary permissions to create and apply tags at the schema level, ensuring a streamlined approach to data organization.
Creating the Admin Role
| create role label_admin; grant create tag on schema [your_schema_name] to role label_admin; grant apply tag on account to role label_admin; grant role label_admin to user your_username; |
Creating a Tag
With the label_admin role established, the creation of tags involves specifying permissible values and their intended purpose. Consider a scenario where schemas are to be tagged based on data sensitivity—creating the tag ‘data_sensitivity’ with allowed values ‘HIGH’ and ‘LOW’.
| create tag data_sensitivity allowed_values ‘HIGH’, ‘LOW’; |
Once tags are in place, they can be assigned to Snowflake objects, either existing or newly created. To illustrate, imagine adding the ‘data_sensitivity’ tag to the ‘user_email’ column in an existing table.
| alter table your_table_name modify column user_email set tag data_sensitivity = ‘HIGH’; |
To manage and retrieve tag information effectively, Snowflake offers insightful queries. For a comprehensive view of all created tags in the account:
| select * from snowflake.account_usage.tags; |
Furthermore, querying tag references at different levels—table or view and column—facilitates understanding the tags associated with specific objects.
| # to view tags assigned to objects within a table or view select * from table(information_schema.tag_references_all_columns(‘your_table’, ‘table’)); # to view tags assigned to a specific column select * from table(raw.information_schema.tag_references(‘your_schema.your_table.your_column’, ‘COLUMN’)); |
Snowflake’s classification mechanism, utilizing tags, aids in grouping and identifying objects. This classification proves instrumental when implementing security measures such as data masking. For instance, identifying columns with sensitive data through classification allows for the targeted application of masking policies.
| # to identify columns with a specific tag for potential masking select * from snowflake.account_usage.tag_references where tag_name = ‘DATA_SENSITIVITY’ and tag_value = ‘HIGH’; |
FAQ
Is Snowflake secure?
Yes, Snowflake is considered secure. It takes extra precautions by employing encryption, access controls, and multi-factor authentication to ensure that your data, whether stored or in the process, remains well-protected within the platform.
Why is Snowflake so popular?
Snowflake’s popularity stems from its cloud-based data warehousing architecture, which enables scalable and efficient data storage and processing. It not only offers scalable and efficient data storage and processing but also scores big on user-friendliness, flexibility, and the ability to handle various data workloads. It’s no wonder it’s gaining popularity so quickly.
Where is the Snowflake database hosted?
Snowflake is hosted on major cloud platforms such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). Users get to pick their preferred cloud provider and region, tailoring it to their exact needs for data storage and processing.
Conclusion
To wrap up, it’s absolutely crucial to boost security measures when diving into Snowflake for your data storage and analytics needs. This blog has covered some top-notch Snowflake security best practices that act as your go-to manual for keeping sensitive info safe and your data infrastructure rock-solid.
Follow these practices, and your organization can build a defense against potential threats, ensuring that your data remains confidential, integral, and always available. It’s all about staying on top of access controls, encrypting data at rest or on the move, and keeping an eye on what users are up to—the essential ingredients for a proactive security game plan in the Snowflake environment.
At the end of the day, a well-thought-out security strategy isn’t just about thwarting potential breaches. It’s about giving stakeholders, clients, and partners the confidence that your data warehouse is impenetrable.







