SOC II
SOC II Compliance: Take Your Security Standards to a New High
Achieving SOC II compliance isn’t just about meeting regulatory requirements—it’s about proving to your clients that their data is in the safest hands. With CloudDefense.AI, you get a cutting-edge security platform designed to exceed SOC II standards, ensuring your organization is always a step ahead in the security game.
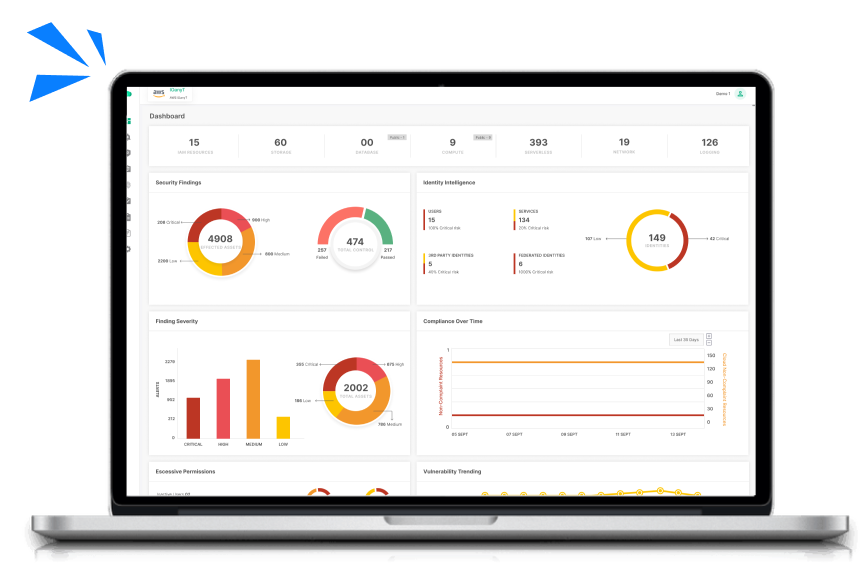
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
EMPOWER YOUR BUSINESS
Build Trust. Strengthen Security. Achieve SOC II Compliance. Book Your Live Demo Today!
Time is ticking, and every delay in security could mean missed opportunities. CloudDefense.AI’s application security solutions embed protection into every stage of your DevOps pipeline so that you can release updates quickly and confidently. Fast, secure, and effortlessly smooth—just how it should be!

The Open Source Conundrum: Balancing Agility with Assurance
Open source tools drive innovation, but they can also introduce risks that jeopardize SOC II compliance. Navigating this landscape requires a partner who understands both the power and the pitfalls of open source. CloudDefense.AI empowers you to harness the benefits of open source while ensuring your systems remain secure and fully compliant with SOC II standards.

Strengthen Your Security Posture with SOC II Compliance
SOC II compliance is more than a checkbox—it’s a commitment to upholding the highest standards of data security and privacy. But with cyber threats evolving daily, how can you ensure your defenses are always up to par? CloudDefense.AI provides you with the tools and insights you need to stay compliant, minimize risks, and reinforce the trust your clients place in you.
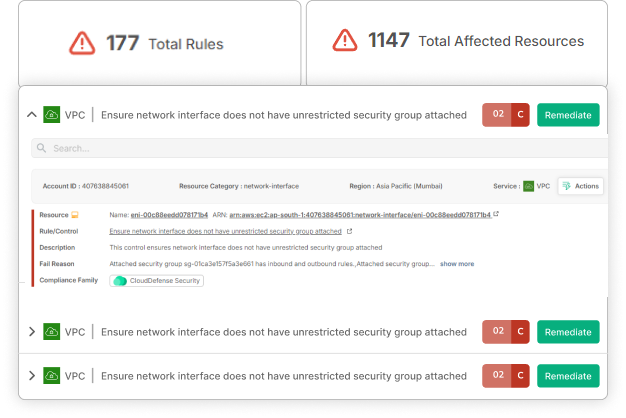
How CloudDefense.AI Keeps You SOC II-Ready
Developer and Admin Empowerment
Equip your teams with a centralized platform that simplifies internal audits, automates remediations, and ensures compliance with every checklist, all from a single detailed interface.
Critical Updates First
Prioritize the most crucial updates with laser precision, addressing vulnerabilities before they escalate into compliance issues or security breaches.
Continuous Security Monitoring
Use SCA, SAST, and DAST tools that tirelessly scan for threats across your entire Software Development Lifecycle, ensuring every line of code meets SOC II requirements.
Smooth Compliance Integration
Maintain digital compliance effortlessly by syncing patch management with real-time repository updates, keeping your systems aligned with SOC II standards at all times.
Certified for Diverse Industries
Achieve compliance across multiple frameworks, including SOC II, HIPAA, GDPR, PCI-DSS, ISO, and more, with a single solution designed for cross-industry application.
Exceeding Client and Industry Expectations
Build and maintain the trust of your clients by protecting their data from breaches and ensuring your organization meets and exceeds the stringent standards of SOC II compliance.
Why SOC II Compliance is a Game-Changer
In a world where data breaches can make or break a company, SOC II compliance is your assurance that your security protocols are not just top-notch but exemplary. With CloudDefense.AI, you’re not just ticking boxes—you’re setting new benchmarks for security. As threats continue to evolve, having a proactive and comprehensive security strategy is essential to protect your business and the data entrusted to you.
Mapping SOC II Criteria to CloudDefense.AI Solutions
Security and Availability
Our SCA tool embeds SOC II compliance throughout your SDLC, offering superior protection and ensuring your systems are always secure and available.
Processing Integrity and Confidentiality
Transparent security practices, combined with rigorous internal verification, help you maintain the highest levels of data integrity and confidentiality, essential for SOC II compliance.
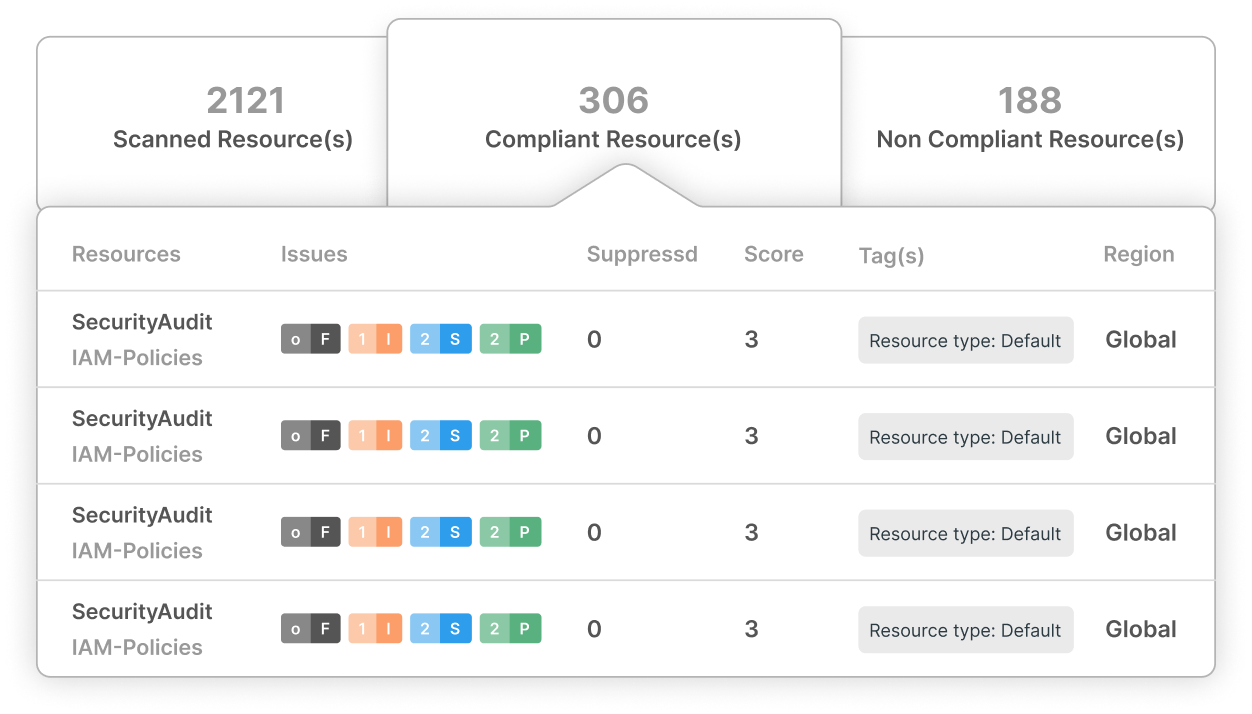
Ready to Elevate Your Security?
Don’t just meet SOC II standards exceed them. Schedule a demo with our team today and discover how CloudDefense.AI can enhance your security posture and build unshakable trust with your clients.




