Gone are those days when you had to rely on traditional methodologies and processes to uncover cyber threats in their cloud environment. 2025’s cybersecurity industry provides you with a new breed of security tools.
Threat detection tools have emerged as a vital choice for organizations that lets you identify security threats with ease and help you to build a solid cybersecurity strategy. In today’s digital age, where cyber threats are evolving rapidly and becoming more sophisticated, we understand it can be difficult to protect your cloud application and network effectively.
Getting the best threat detection in 2025 would help you fortify your cyber shield. But how would you find the best tool for your organization? Well, you won’t have to! Based on our past experience with various cybersecurity tools, we came up with the top 10 threat detection tools for cybersecurity in 2025 that you can use to protect your assets.
Let’s dive right in!
How to Choose a Threat Detection Tool?
Even when you have the list of top threat detection tools in 2025, selecting the right tool can be tricky as not all tools will cater to your requirements.
That is why we have come up with a list of features and aspects that you need to consider, which will ultimately guide you to the right tool that caters to your requirements. Here are considerations:
Activity Monitoring
Activity monitoring is an important functionality you should check in the threat detection tool you are about to choose. It should be capable of detecting all types of threats by monitoring workload access and cloud activity. The tool should analyze the user behavior to detect any kind of threat that can lead to breaches. Having a comprehensive insight of your cybersecurity posture will help your team to identify potential threats and take necessary corrective steps. The tool should offer threat intelligence, anomaly detection, and other features to provide a detailed insight into unusual activities.
Insider Threat Alert
Apart from threats from outside, the threat detection tool should be capable enough to uncover insider threats. By identifying suspicious activities and analyzing event logs, the tool should be able uncover all the insider threats.
Threat Coverage
Properly assess the threat coverage offered by the tool as not all tools have the ability to identify a wide range of threats. Make sure the tool is not only able to identify known and unknown threats but many advanced threats.
Integration
A threat detection tool that integrates easily with your existing security infrastructure would be highly suitable for your organization. Look for tools that easily integrate with your firewall, SIEM solution, and other security tools because they will streamline the whole threat management process.
Threat Prioritization
Consider looking for a threat detection tool that offers threat prioritization based on their impact. Based on various aspects, it should prioritize threats and provide your team with alerts of severe threats first.
Scalability
Always evaluate the scalability of the threat detection tool and whether it has the capability to handle a large amount of data and network traffic. Make sure that it can cope as your organization grows without compromising the threat detection performance.
Usability
Last but not the least, you should evaluate the usability of the threat detection tool and how easy it is to navigate. Having an intuitive interface will enhance the overall user experience and make it easy for every team to use them without going through a steep learning curve.
10 Best Threat Detection Tools in 2025
Now, it is time to delve into a detailed review of the top threat detection tools that you should consider to protect your infrastructure and network from threats. To make the selection much easier for you, we have created a comparison table of all the tools and what they have on offer.
Tools | Insider Threat Detection | Automation | Key Features | Price
|
CloudDefense.AI | Available | Available | 1. ML-based anomaly detection. 2. DNS threat detection. 3. Alert prioritization. 4. Real-time user behavior analysis. | The price is available after the quote request. |
SolarWinds | Limited | Available | 1. Real-time detection. 2. Automated threat response. 3. Automated event correlation. 4. End-user activity tracking. | The price is available on quote request. |
Snort | Limited | Available | 1. Cisco Talos approved ruleset. 2. Simple deployment. 3. Network traffic debugging. | Free to use. |
IBM Security QRadar | Available | Available | 1. Complete visibility. 2. X-Force threat intelligence. 3. Network behaviour analytics. 4. Magnitude Score. | The price is available on quote request. |
Cisco Secure Network Analytics | Limited | Available | 1. ML-based and behavioral modeling-based analysis. 2. Encrypted traffic analysis. 3. Quick detection. 4. Public cloud coverage. | The price is available after the demo. |
Splunk | Available | Available | 1. Internal and external threat intelligence. 2. Real-time analytics. 3. Risk-based alerting. 4. Data-driven insight. | The price is available after a free trial. |
Trend Micro | Limited | Available | 1. Real-time protection. 2. Vision One for prioritization. 3. Continuous monitoring. 4. Advanced sandbox analysis. | The price is available after a free trial. |
FireEye Threat Analytics | Available | Limited | 1. Enterprise-wide visibility. 2. Codified detection support. 3. Threat insight. 4. Rapid deployment. | The price is available on request. |
Netwitness | Limited | Available | 1. Behavioral analytics. 2. Quick threat investigation. 3. Complete visibility. | The price is available after the demo. |
Skyhawk | Available | Available | 1. Alert context. 2. Skyhawk Synthesis. 3. Malicious behavior indicator. 4. AI-based support. | The price is available after the demo. |
Let’s dive into the reviews of all the threat detection tools:
CloudDefense.AI

CloudDefense.AI 
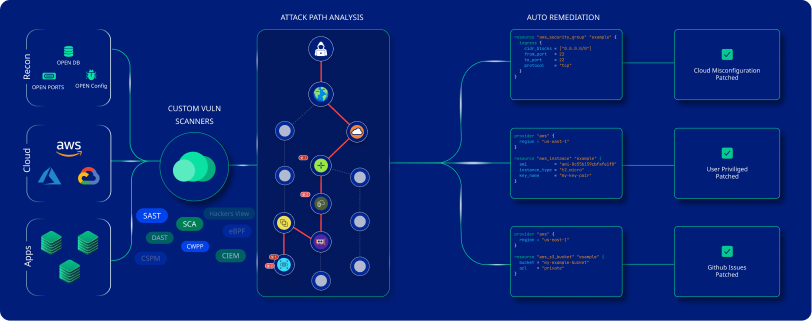
With the cutting-edge threat detection tool from CloudDefense.AI, you can effortlessly monitor and prevent potential cyber threats from affecting your cloud infrastructure. It integrates with your system to provide real-time threat detection and provide complete visibility into all the cloud activities.
To help you stay ahead of all security threats, CloudDefense.AI makes use of AI-driven anomaly detection, advanced UEBA, user-behavior analysis, Security Graph, and other modern features.
With its risk-based prioritization, this tool makes it easy for your team to target threats that can make the most impact. One of the defining capabilities of this solution is that it also safeguards your API by helping you understand the attacker’s behavior and augment them in the investigation.
Key Features
CloudDefense.AI comes with many key features that have helped it to achieve a top-tier position in the industry:
End-to-End Threat Visibility
When you implement CloudDefense.AI, you get complete threat visibility into your cloud infrastructure and all the activities. It uncovers attackers' movements by correlating them with real-time signals to deliver a quick response for mitigation.
Anomaly and Reconnaissance Detection
This tool leverages ML-based anomaly detection capability to uncover zero-day attacks, network misuse, and irregular compute provisioning. It is highly effective in protecting your assets, sensitive data, and resources. In addition, it is capable of identifying and addressing various reconnaissance techniques to protect the ports.
Activity Monitoring
With CloudDefense.AI in place, you won’t have to worry about threats as it can detect both known and unknown threats and malicious activities by constantly monitoring all the activities. It can also detect evasive activities of attackers and provide alerts to the team to take necessary security measures.
Real-Time User Behavior
This solution can closely monitor user behavior in real-time and identify various unusual activities by correlating them with historical data. Using this capability can also uncover insider threats like excessive login attempts and enhance overall security posture.
Risk Validation
Unlike most of its competitors, CloudDefense.AI can perform risk validation of threats and enable security teams to take remediation steps. It verifies exposure status in your cloud network and prioritizes risks accordingly.
Misconfigured API Detection
CloudDefense.AI serves as a powerful threat detection tool that can also identify threats associated with misconfigured API and provide reports regarding secret exposure or unauthorized access.
Pros

CloudDefense.AI enables you to spot all the potential threats by providing complete visibility into all the activities in your cloud.

It provides you with complete insight into all the threats and guides you to evaluate the safety of all the assets.

This solution can actively detect a variety of threats and malicious activities like DNS-based threat, evasive activities, insider threats and others.

It continuously monitors the whole cloud environment to uncover abnormal activities.

Leverages Security Graph feature and infrastructure context to prioritize risks.
Cons

A large number of features can be overwhelming for new employees.
Don’t just take our word for it. Book a demo and witness firsthand the power and simplicity of CloudDefense.AI.
What Sets Us Apart?
CloudDefense.AI may serve as another top-tier threat detection tool, but there are certain factors that make it different. These factors are:
Advanced UEBA
CloudDefense.AI makes use of the advanced UEBA to continuously monitor for malicious activities and respond to them swiftly.
ML/AI Based Threat Detection
Another feature that sets this solution apart is ML-based threat detection, which can accurately detect threats to secure the cloud environment.
Detailed Prioritization
By correlating threats with context and utilizing the Security Graph feature, this solution helps in understanding and prioritizing them.
SolarWinds

SolarWinds
With SolarWinds integrated into your cloud and network infrastructure, you can perform automated threat detection to protect all resources and assets. This solution identifies threats by correlating them with events and uncovers many out-of-the-box threats that can’t be easily detected. Since it performs continuous threat detection across the cloud environment and devices, none of the threats go undetected.
Pros

It enables the team to perform various automated responses after a threat has been detected.

Solarwinds performs real-time monitoring to actively pinpoint threats and alert them for quick response.

It utilizes automation to detect threats and provide a response for quick remediation.

Solarwinds has the capability to identify threats from end-user activity.
Cons

It doesn’t come equipped with some advanced features.

Lacks risk prioritization.
Snort

Snort
Considered the gold standard in the open-source threat-detection segment, Snort is a highly capable tool that can detect malicious activities and alert the user. It makes use of a series of rules to analyze all the activities in your network and uncover any potential threat in real-time. Unlike many open-source tools, this solution won’t make you go through a steep learning curve as the interface is quite simple to understand.
Pros

It serves as one of the most powerful open-source threat detection tools that can accurately pinpoint threats.

Snort utilizes a Cisco Talos-approved ruleset to define malicious activities in your network.

With its rule-based system, it can easily identify malware, spyware, and various other types of security threats.
Cons

Since it is an open-source tool, you won’t find any premium features.

Configuring this tool in your network or infrastructure requires in-depth knowledge.
IBM Security QRadar

IBM Security QRadar
IBM Security QRadar is a top-tier real-time threat detection tool that has the ability to analyze millions of events in real time and identify threats. With this tool, you can get complete visibility across your cloud environment because it analyzes all the network activities and log events. It is designed with network behavioral analytics, X-Force threat intelligence, user behavior analytics, and various pre-built cases to deliver reports of critical threats.
Pros

It accelerates threat detection by leveraging advanced features and provides high-fidelity alerts.

It provides visibility across endpoints, cloud, on-premises infrastructure, and networks.

Perform real-time analysis and contextualization to identify threats associated with IP, URLs, and malware.

Leverages ML-based User Behavioral Analytics to flag anomalies that can risk all your cloud assets.

It prioritizes threats using the proprietary Magnitude Score and helps security teams prioritize their response.
Cons

This solution might be expensive for organizations with limited budgets.
Cisco Secure Network Analytics

Cisco Secure Network Analytics
Another top threat detection tool that you can integrate is Cisco Secure Network Analytics. Formerly known as Stealthwatch, this solution leverages machine learning and advanced behavioral modeling to uncover many emerging threats along with known ones. It is a one-of-a-kind tool that helps you extend your coverage by enabling the tool to identify threats in the public cloud platform without requiring any agent.
Pros

Cisco Secure Network Analytics provides complete visibility by analyzing encrypted data for threats.

It can quickly identify insider threats and hidden malware and provide high-fidelity alerts to speed up incident response.

This tool stores all the collected data in a secured space for forensic analysis and threat contextualization.

The vendor provides complete product training through a professional team.

Impressive 24/7 customer support for all technical issues.
Cons

This tool is natively limited to network activity.
Splunk

Splunk
Splunk is a robust threat detection that is widely used by many top organizations due to its ability to identify sophisticated threats along with insider threats. By combining threat-intelligence and real-time analytics, Splunk can quickly uncover suspicious activities and malicious behaviors. It serves as a unified threat detection platform that not only helps you identify threats but also manage, investigate and remediate them.
Pros

It makes use of both internal and external threat intelligence to provide a comprehensive view of potential threats.

Helps in reducing alert fatigue by providing alerts on threats based on their severity.

Splunk can help your team address insider threats, credential access issues, and lateral movement in the cloud environment.

Provides data-driven insight to effectively detect threats and mitigate them with ease.
Cons

It doesn’t offer you upfront pricing.

The interface might seem difficult for new users in the beginning.
Trend Micro

Trend Micro
When it comes to finding a top threat detection tool for your organization, Trend Micro should go unnoticed. It is an enterprise level tool that provides your organization with real-time protection and helps in preventing advanced threats like ransomware.
Importantly, Trend Micro is equipped with advanced features like sandbox analysis, Deep Discovery, and intelligence sharing and analytics, the main aim of which is to quickly analyze and detect threats.
Pros

Enables your team to identify, analyze, and address advanced threats in real-time with ease.

You can perform custom sandbox analysis to discover hidden threats lingering in the infrastructure.

Trend Micro also helps you evaluate the threat and prioritize your response accordingly.
Cons

This tool is highly resource-intensive.

Some of the features can be difficult to understand in the beginning.
FireEye Threat Analytics

FireEye Threat Analytics
FireEye Threat Analytics is a cloud-based threat detection solution that helps you protect your organization against modern threats that bypass traditional security barricades.
This next-generation tool implements behavioral analytics and threat intelligence to optimize the threat detection and alerting capability. Like most popular threat detection tools, this tool can easily scale with the expansion of your cloud infrastructure without hampering the performance.
Pros

It offers enhanced threat detection by using codified detection expertise.

This tool helps the security team to uncover covert malicious behavior by offering a sub-second search.

Provides you with complete visibility through its behavior analytics and cloud-based Threat Analytics Platform.

It offers Guided Investigation to improve the efficiency and prioritization of threat investigations.
Cons

The features are not properly segregated in the interface.
Netwitness

Netwitness
Designed to protect an organization’s network from advanced threats, Netwitness has emerged as an obvious choice when it comes to threat detection tools. This tool has revolutionized threat detection and response capability by offering automation, behavioral analytics, attack correlation, and other advanced features. It is one of those tools that allows you to prioritize, respond to, and investigate threats to generate appropriate responses.
Pros

Netwitness offers unrivaled visibility across your cloud infrastructure and helps in identifying hidden threats.

Super fast threat detection capability helps an organization mitigate threats before they can make any impact.

ML-based behavioral analytics identifies anomalies that can lead to threats as early as possible.

Provides enriched threat intelligence by analyzing all the available data.

Generates real-time alerts to enable teams to respond quickly.
Cons

It doesn’t offer up-to-date threat feeds.

This solution is prone to false positives.
Skyhawk

Skyhawk
With Skyhawk, it gets easier for you to monitor behaviors and unusual activities and identify threats that can lead to serious breaches. It is a cloud-based tool that leverages automated Continuous Proactive Protection to continuously monitor your cloud environment and find security threats. Most importantly, it is able to eliminate alert fatigue by utilizing Skyhawk Synthesis and provides alerts of the most severe attacks.
Pros

Skyhawk creates a custom model within your cloud environment to enhance threat detection accuracy.

Provides runtime monitoring that is able to detect threats when it unfolds.

This tool utilizes ML and AI-based malicious behavior indicators to accelerate threat detection.

It updates the threat detection model according to changes in security requirements.
Cons

It is designed mainly to cater to cloud environments.
Conclusion
Threat detection tools are gradually becoming an integral part of modern security and many organization are combining it with other security tools to enhance their security posture. The increasing popularity of this tool has brought a large number of vendors, creating a confusion for organization whom to choose.
Through this article, we have tried to eliminate the confusion by providing you with a list of the top 10 threat detection tools in 2025. The tools in this list offer a variety of advanced features, but all with the primary aim of identifying all the threats. In our view, CloudDefense.AI delivers the best performance among all and caters to every security requirement.







