The OWASP Top 10 is one of the primary standards that enables organizations to set a baseline for their application security. It provides organizations with a foundational guide, outlines the vital and severe application security risks.
However, as attackers are getting sophisticated with their attacks and software development getting more complex, depending upon the OWASP Top 10 for AppSec is not enough. Modern applications with multiple microservices, APIs, and third-party dependencies are prone to many zero-day flaws and nuanced cyberattacks.
AI SAST is the answer to evolving application security requirements. It utilizes AI vulnerability detection, moving beyond the standard OWASP Top 10 and discovering all the contextual threats. Today, we are going to show how AI SAST helps in uncovering all nuanced and zero-day attacks.
OWASP Top 10 and Its Limitations
The Open Web Application Security Project, or OWASP, is a non-profit organization that regularly provides lists regarding the top 10 vulnerabilities related to application security. It serves as the gold standard for modern organizations as it highlights the most impactful security threats to applications.
The list provides a vital foundation for every application security strategy. It enables security professionals to assess their application security posture based on the list. In the OWASP top 10, all the cyber threats are ranked according to their severity, frequency of occurrence, and complete impact.
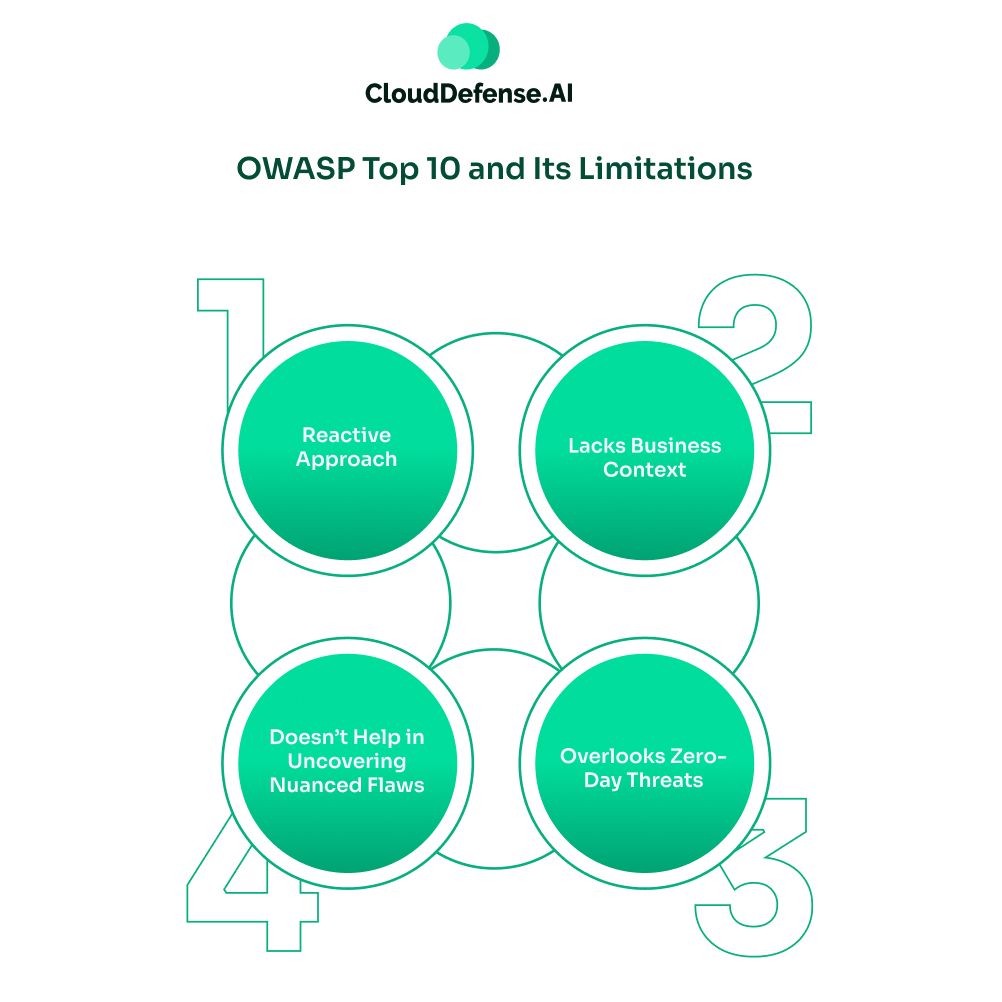
Even though it helps organizations to minimize the attack surface, it does have limitations against the evolving cyber threats:
- Reactive Approach: The OWASP Top 10 is based on known vulnerabilities that have left a major impact on application security. It enables organizations to create guardrails and remediation efforts needed to prevent these vulnerabilities. However, it doesn’t help the organization to prepare against zero-day patterns and novel threats. It only focuses on common and critical threats that have affected application security.
- Lacks Business Context: The Top 10 list provides a generalised risk overview of the prominent security threats that might affect the application security. However, it doesn’t involve the business logic and context of a specific application. The impact of the top 10 security threats varies according to the application’s function and data streams.
- Doesn’t Help in Uncovering Nuanced Flaws: Depending solely on the OWASP Top 10 often causes the security teams to only focus on the top 10 vulnerabilities. As a result, it makes them overlook security threats that arise from the complexity in the codebase. Security teams need assistance from AI vulnerability detection tools that can detect the flawed pattern while understanding the context of the code.
- Overlooks Zero-Day Threats: The zero-day threats are those unknown cybersecurity issues that haven’t been fixed or listed on a cyber threat list. Thus, the Top 10 list doesn’t cover these threats, which can have a huge impact once they penetrate the application security. Importantly, relying solely on the OWASP top 10 creates a gap in the overall security strategy that can be compromised.
AI SAST: A Smart and Proactive Approach
Previously, traditional SAST has been the cornerstone for assessing and identifying security threats in an application. While they are still effective in finding common security threats, they can’t go beyond the OWASP top 10 and cope with evolving cybersecurity threats.
AI SAST, with its advanced AI vulnerability detection capability, can not only detect severe known security threats but also identify nuanced and zero-day attacks. It leverages artificial intelligence,machine learning, and LLM models to identify any kind of threats.
It is continuously learning from secure coding practices, business logic, and other contexts to flag actual security threats. AI SAST tools like QINA Clarity AI are widely adopted by organizations as they can detect any zero-day flaws and filter out all false positives.
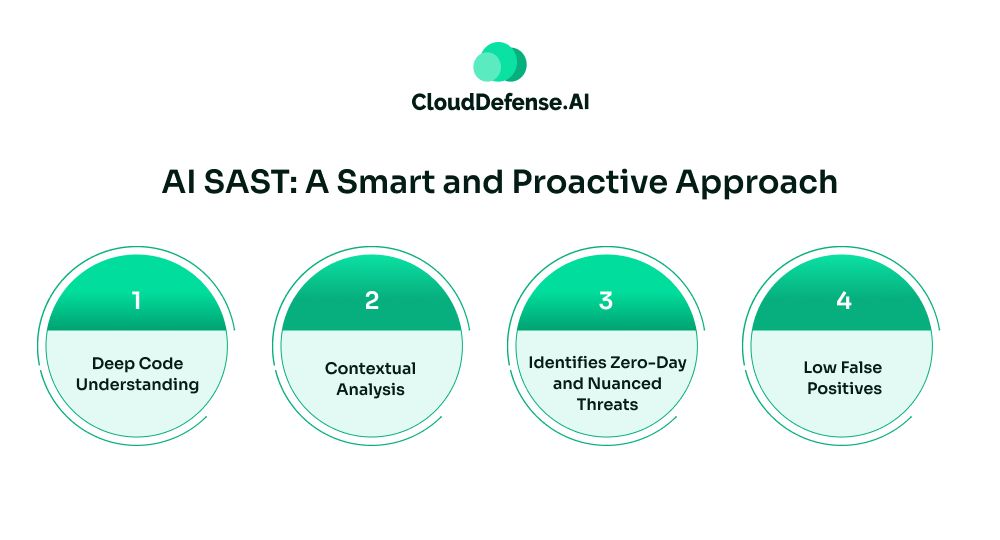
Here is how AI SAST operates and benefits the organization:
- Deep Code Understanding: AI SAST tools are continuously trained on large codebases, which include both vulnerable and secure code segments. It is also trained to understand different coding patterns, programming languages, and frameworks. This enables the tool to understand the context and purpose of a code while uncovering any nuanced threat patterns.
- Contextual Analysis: Unlike traditional SAST tools that rely on OWASP Top 10 and other databases, AI SAST analyzes the data flow for contextual analysis. It understands how different parts of the code interact, enabling them to under nuanced threat patterns and complex vulnerabilities arising from a series of insecure coding practices.
- Identifies Zero-Day and Nuanced Threats: These tools leverage an AI vulnerability detection mechanism that holds the ability to identify subtle and zero-day patterns. As a result, it can provide alerts regarding different types of nuanced vulnerabilities that go beyond the standard OWASP Top 10 or SANS list. Nuanced flaws like business logic flaws, supply chain risk, access control issues, etc, are uncovered by the tool.
- Low False Positives: The AI SAST tool holds the ability to perform semantic code analysis and understand the context of the code along with its intent. It enables the tool to distinguish between code segments that are genuine threats and false alerts. Advanced AI SAST tools like QINA Clarity AI make use of a 4-stage analysis, where it takes the code through four different stages to filter out security findings that are false positives. It is highly useful for DevSec teams because it cuts down the noise and helps them focus on real threats.
How AI SAST Uncovers Nuanced and Zero-Day Threats
AI SAST is a next-generation tool that uncovers nuanced and zero-day threats that are yet to be patched or have been publicly listed. It allows the organization to create an AppSec strategy that goes beyond OWASP Top 10, SANS, and other vulnerability databases. It ensures all types of novel threats are detected before they reach the production environment.
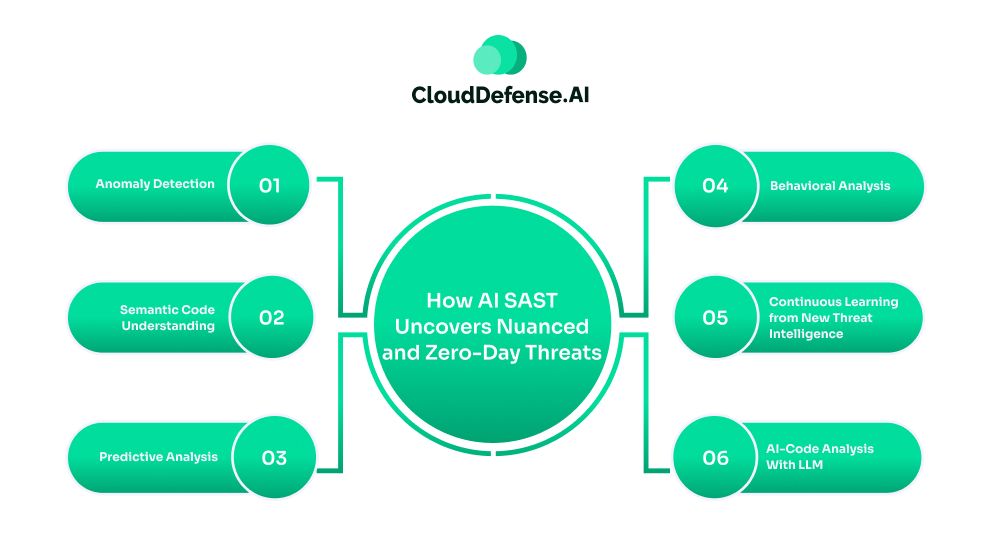
But how does AI SAST uncover nuanced and zero-day flaws? Here is how it identifies all the severe security threats:
- Anomaly Detection: AI SAST tools like QINA Clarity AI are trained on millions of codebases, especially on secure coding patterns. This allows the tool to create a baseline for secure and standard coding practice. When a new code deviates in data flow or API usage from the normal baseline, the tool identifies it as an anomaly. It is constantly learning from codebases and secure coding patterns, which enables it to identify novel threats.
- Semantic Code Understanding: Another great aspect of AI SAST is that it understands the context and purpose of the code segment. Based on code context, it builds an Abstract Syntax Tree and Call Graph of the application, which helps in tracking the data flow from user input to execution. As a result, the tool is able to extract information regarding any complex and chained vulnerabilities that are often omitted by other tools.
- Predictive Analysis: AI SAST tools utilize advanced predictive analysis mechanisms where they assess the code segments against previously identified vulnerabilities. By assessing the code for known weaknesses and structural flaws, it can predict the chance of threats originating from the code. It is constantly learning from new databases, which enhance its prediction accuracy.
- Behavioral Analysis: To detect any kind of zero-day or unknown vulnerability, AI SAST also utilizes behavioral analysis techniques. It simulates the probable behavior of the code and predicts how it may react when an unexpected or flawed input occurs. It is highly useful in identifying vulnerabilities that might occur under unforeseen situations.
- Continuous Learning from New Threat Intelligence: AI-based SAST continuously gathers all the threat intelligence to learn about new threat patterns and techniques. The continuous threat data stream keeps it updated regarding all the threat intelligence, allowing it to adapt to the modern threat environment.
- AI-Code Analysis With LLM: As more and more developers are shifting towards using AI coding assistants to accelerate development speed, the chance of zero-day threats is increasing. AI SASTs are leveraging LLM to specifically analyze AI-generated code along with its dependencies to uncover patterns that are missed by traditional methods.
Future of AI SAST: A Collaborative Approach
The use of AI SAST in SDLC doesn’t erode the importance of the OWASP Top 10 in vulnerability management. Rather, the use of AI SAST indicates a collaborative approach where the tool utilises the foundation of OWASP Top 10 along with deep and continual analysis.
The OWASP Top 10 will remain the crucial foundation for application security, but it will no longer serve as the ultimate answer.AI SAST enables organizations to take a leap to an intelligent and comprehensive AppSec strategy that can not only identify known threats but also zero-day and nuanced vulnerabilities.
AI SAST tools like QINA Clarity AI are revolutionizing application security as they leverage AI vulnerability detection to intelligently predict and identify threats. Developers can identify and remediate threats before a code segment is committed. It also provides them with prioritised security with zero false positives. With the adoption of AI SAST, organizations can:
- Smartly Shift Left: By integrating AI SAST into the SDLC, especially the CI/CD pipeline, organizations can smartly implement the shift left approach. Integrating security analysis early will help developers get actionable and intelligent feedback in the development environment.
- Accurate and Smart Prioritization: AI SAST likes QINA Clarity AI offers smart prioritization of security findings. It utilizes an intelligent 4-stage analysis that assesses all the security findings and provides prioritised alerts while negating all false positives.
- Automate Tasks: The adoption of AI-based SAST also enables teams to automate vulnerability detection tasks, going beyond the reference of OWASP Top 10. The remediation tasks are also automated to prevent any delay in the response. It frees up the time of security professionals and allows them to focus on more important cybersecurity tasks.
- Staying Proactive: AI SAST helps organizations to shift from a reactive to a proactive approach. It helps the team to proactively identify and remediate all the emerging threats and zero-day flaws.
The cyber threats are evolving rapidly, and attackers are getting sophisticated with their techniques. AI SAST provides the necessary arsenal to organizations to look beyond standard threat databases and uncover all the nuanced and zero-day flaws. It ultimately helps the organization to build a future-proof and robust application security.







