Vulnerability Remediation
Revolutionize Vulnerability Remediation
Protect your digital assets with CloudDefense.AI’s state-of-the-art vulnerability remediation solutions. Eliminate threats, smoothen processes, and strengthen your systems against cyberattacks.
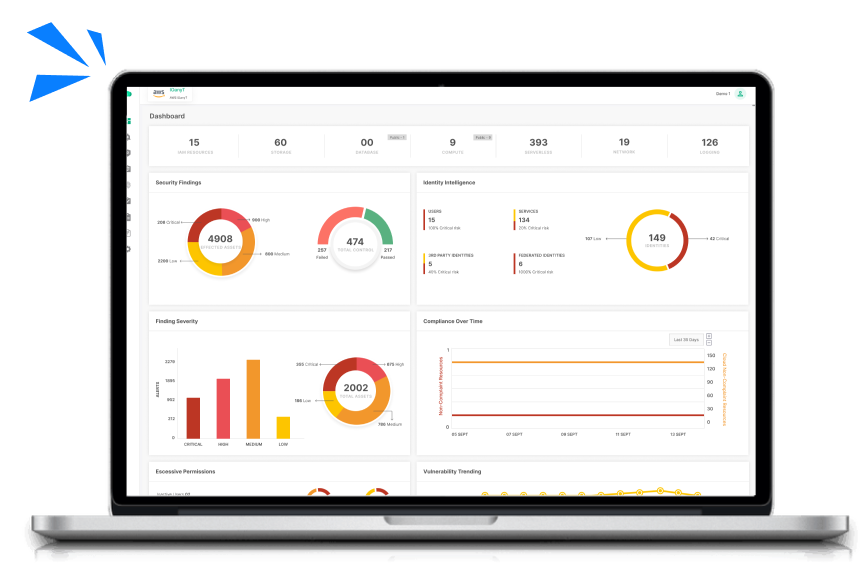
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
EMPOWER YOUR BUSINESS
One Solution, Total Vulnerability Remediation: Seal Every Gap!
Say goodbye to security loopholes and embrace a secure digital environment. With CloudDefense.AI, you can actively manage vulnerabilities and protect your organization with unmatched precision.

Centralized Control for Vulnerability Management
Take charge of your security infrastructure with CloudDefense.AI’s centralized platform, offering simplified management across diverse environments—cloud, on-premises, or hybrid.

Instantaneous Threat Response
Stay protected with CloudDefense.AI’s real-time detection and remediation capabilities, addressing vulnerabilities before they can be exploited.

Supreme User Experience
Manage complex security operations effortlessly with our insightful platform, designed for both cybersecurity professionals and novices alike.
Your Retail Empire is Under Attack
Retail is a battlefield. Every day, cybercriminals target your business, ready to steal your hard-earned revenue and damage your reputation.
The Numbers Don’t Lie!
24%
You’re a Top Target
Retailers face a staggering 24% of all cyberattacks, making you a prime target for hackers.
-$250,000
The Price of Inaction
A single data breach can cost your business anywhere from $100,000 to $250,000. That’s money straight out of your bottom line.
20%
The Growing Threat
E-commerce security incidents have skyrocketed by 20% in just one year. The threat is real, and it’s escalating.
Can you afford to be a Casualty?
Don’t let these statistics become your reality. Protect your business, your customers, and your bottom line with our strong retail and e-commerce security solutions.
Our Comprehensive Approach to Vulnerability Remediation
CloudDefense.AI’s approach to vulnerability remediation combines advanced technology, expert-led policies, and continuous monitoring to protect your assets from threats, ensuring resilience and compliance.
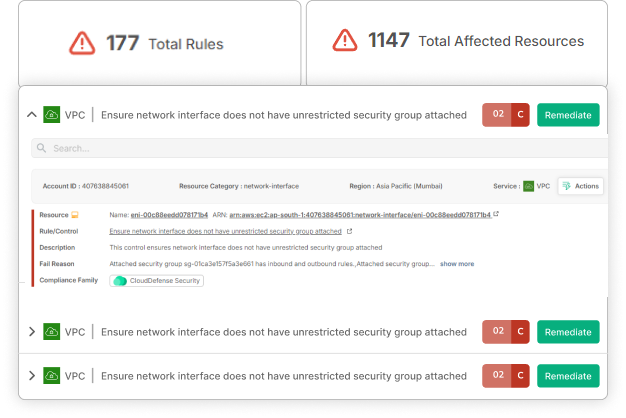
Centralized Detection and Response
Swift Vulnerability Identification and Resolution At CloudDefense.AI, we empower businesses with rapid detection and resolution, transforming them into a proactive, resilient minority. Our platform’s intelligence-driven approach guarantees quick and effective vulnerability management.
Rapid Resolution
Quickly detect and remediate vulnerabilities, positioning your organization among the elite few capable of resolving security issues promptly.
Data-Driven Intelligence
Our platform uses intelligent data collection, ensuring your security operations are confident and proactive.
Optimized Efficiency
Buttery smooth processes that help to minimize downtime through our swift detection and resolution framework.
Competitive Advantage
Stay ahead in the cybersecurity game by focusing on both breach prevention and swift recovery for sustained resilience.
Zero Trust Security Framework
Superior Security with Zero Trust Scans Enhance your vulnerability management with thorough, trust-free scans that eliminate risks and reinforce your defenses. CloudDefense.AI’s technology ensures complete protection against modern threats.
Trust-Free Protection
Remove vulnerabilities tied to trust dependencies, securing your data against advanced threats.
Automated Defense Mechanism
Automatically strengthen your defenses by minimizing common intrusion points, and enhancing your security posture.
Accountability and Verification
Assure stakeholders of your security measures with internal verifications and duty segregation.
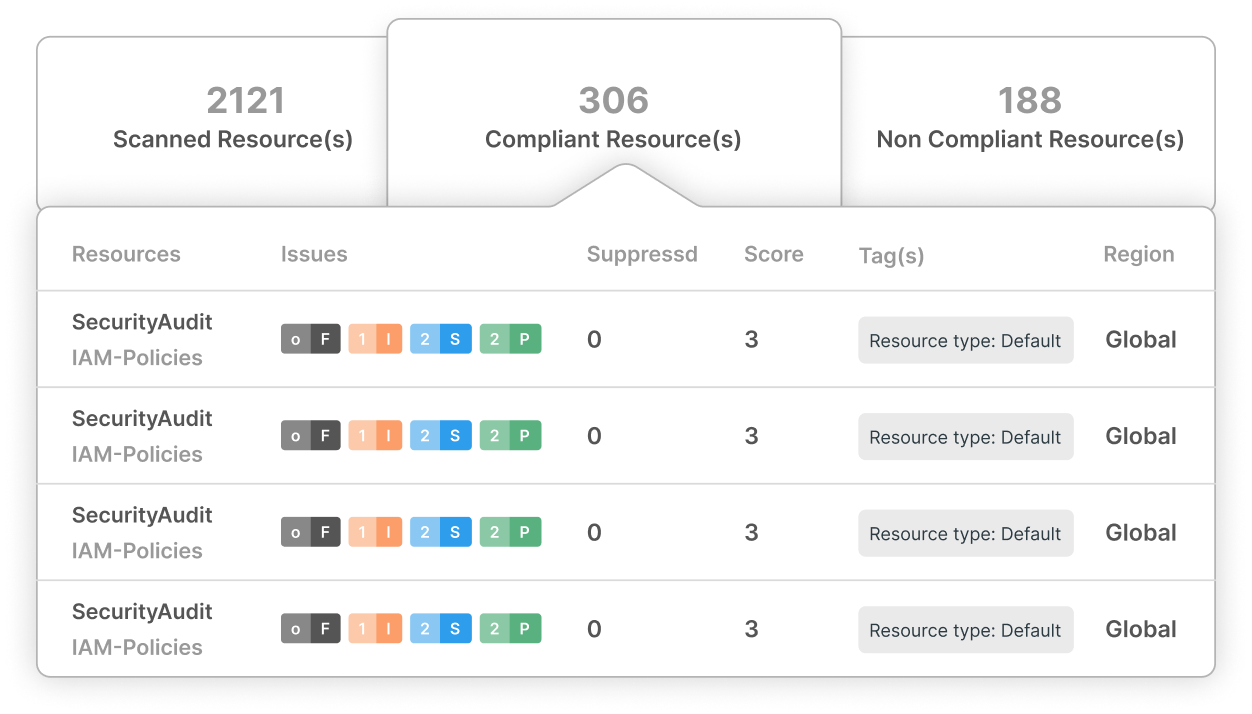
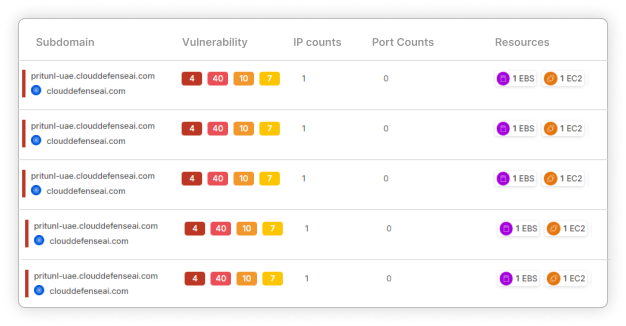
Effortless Compliance Management
Simplify Regulatory Compliance with CloudDefense.AI’s Vulnerability Remediation Navigate complex regulations with ease using CloudDefense.AI’s compliance management tools. Our platform simplifies the process, ensuring your organization remains compliant across all key standards.
Streamlined Compliance
Easily manage compliance with regulatory requirements using our comprehensive Airtight Checklists, covering PCI DSS, FINRA, NYDFS, FERPA, HIPAA, GDPR, and CCPA.
Insightful Reporting
Gain actionable insights from detailed reports, empowering informed decision-making.
Priority-Driven Focus
Identify and address compliance gaps efficiently, saving time and resources.
User-Friendly Interface
Simplify your compliance management with our intuitive platform, making it accessible to all users.
End-to-End Security Fortification
Strengthen Your Systems from Source to Target CloudDefense.AI provides strong protection against external threats by rigorously scanning third-party applications. Our SAST technology ensures your systems remain secure, resilient, and free from vulnerabilities.
Continuous Monitoring
Our SAST technology constantly scans for security rule violations, maintaining the integrity of your systems.
Source-to-Target Protection
Establish a strong security barrier, protecting your operations from external attacks.
Proactive Threat Management
Stay ahead of potential breaches with CloudDefense.AI’s proactive approach to security.
Experience Unmatched Vulnerability Remediation
Discover how CloudDefense.AI can transform your vulnerability management strategy. Join us for a live demonstration and see the difference in action.




