What is CSPM?
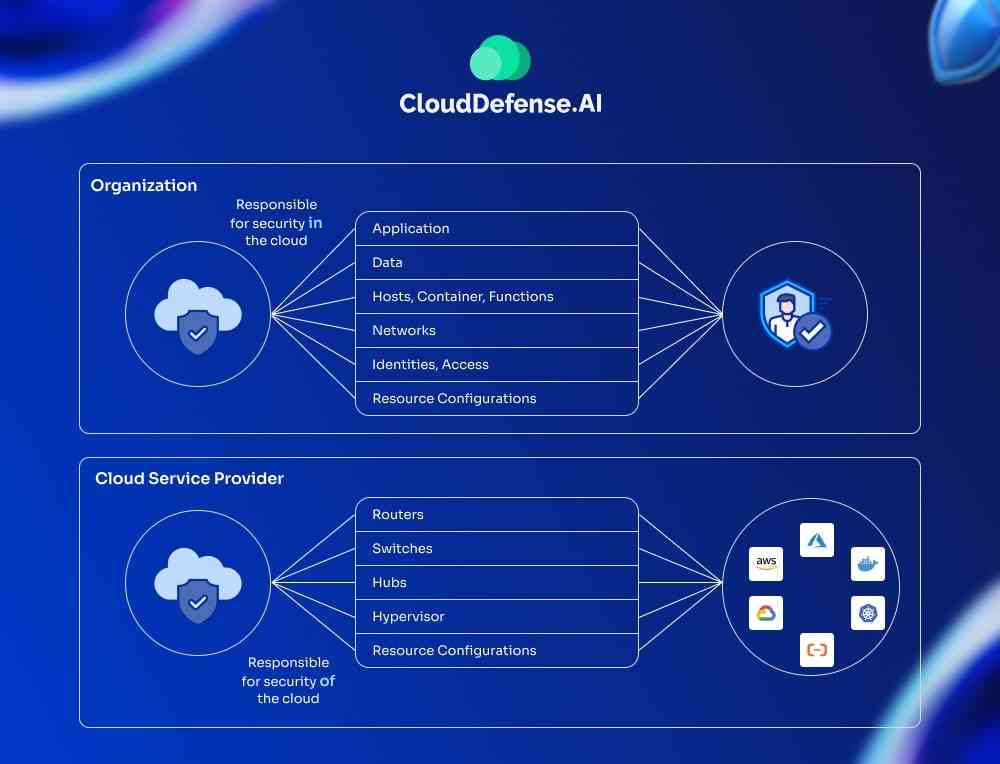
Cloud security posture management, or CSPM, is a revolutionary technology or practice that is designed for detecting and rectifying misconfiguration, compliance issues, and security threats in the cloud. It is a vital part of modern IT security tools that continuously look for vulnerabilities in the cloud infrastructure and implement security protocols whenever it detects threats.
Key functions of CSPM solutions include:
- Continuously monitoring cloud configurations for security gaps
- Automating compliance checks against industry regulatory requirements
- Identifying and alerting on potential data exposure risks
- Providing real-time visibility into cloud asset inventory
- Recommending security best practices tailored to the organization’s cloud setup
Basically, when organizations migrate their business applications to cloud providers like Amazon Web Services (AWS) or Microsoft Azure, they rely on CSPM to secure their cloud configuration and prevent any data breach. Most CSPM tools primarily examine and compare a given cloud ecosystem against a defined set of standard security practices and risks and find out the gap.
Standard tools generally highlight the risks to security management, whereas some advanced tools use artificial intelligence and machine learning to mitigate the issue automatically. As the demand for cloud computing is increasing, CSPM tools continue to evolve by harnessing the power of modern security technology and enhancing its security detection capabilities.
“According to Gartner, cloud security posture management will see explosive growth, jumping from $1.06 billion in 2022 to $3.32 billion by 2027. This 25.7% annual growth rate is due to the soaring security demand as more businesses adopt public and private clouds, containers, and serverless tech.”
Why Do Cloud Misconfigurations Occur?
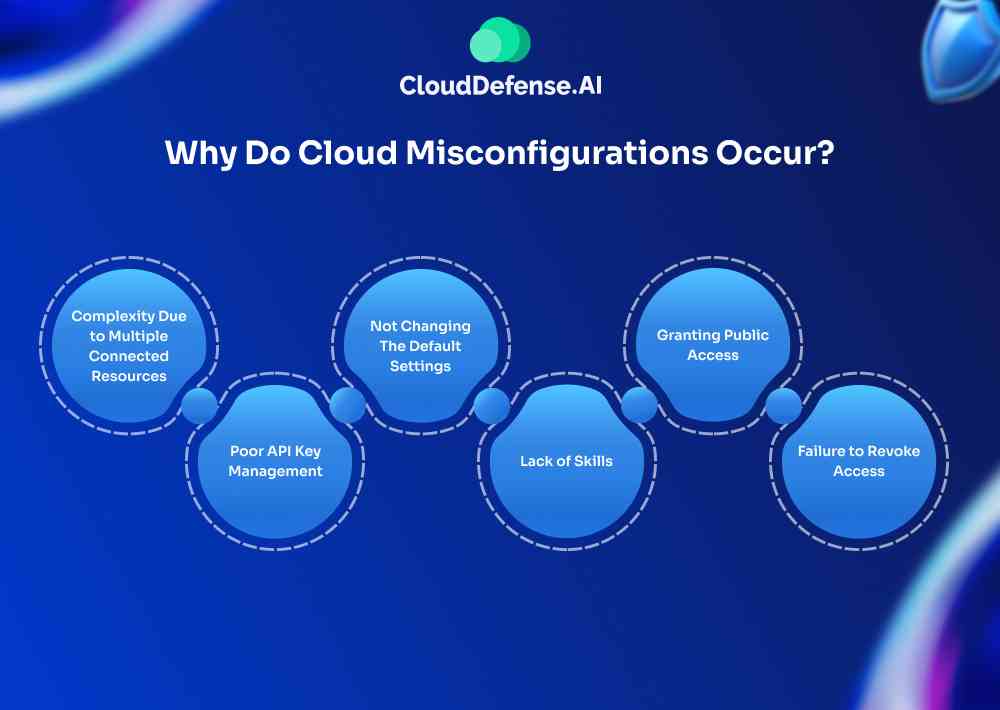
Cloud misconfiguration is a common occurrence, and it mostly happens during the deployment of business applications on the cloud. However, misconfiguration doesn’t occur due to a single cause, many causes give rise to this issue. Here are a few common reasons that lead to cause;
Complexity Due to Multiple Connected Resources
During the deployment, multiple connected resources like lambda functions, containers, and Kubernetes are involved, and when they aren’t appropriately configured, misconfiguration occurs. Cloud-based services involve a lot of factors, so it becomes difficult to monitor and manage everything, which often leads to misconfiguration.
Poor API Key Management
Cloud infrastructures are generally accessed by API keys only. Many organizations store API keys in poorly configured cloud buckets or GitHub repositories. The API keys and passwords can be easily accessed by threat actors and leave the whole system vulnerable. Since most organizations have multi-cloud deployment, a compromise in the API key of one platform will jeopardize the infrastructure and ultimately put the organization at risk.
Not Changing The Default Settings
When you start integrating your business application into a new cloud infrastructure, it comes with its default security settings. When you don’t reconfigure these default settings to secure settings according to your organization’s security, it leaves glitches and loopholes in the cloud.
Lack of Skills
Multi-cloud infrastructure is still a new concept for many businesses, even though many of them have adopted it. Securing the infrastructure is not a straightforward task, as it requires both knowledge and experience. If the security management isn’t sure how various cloud resources interact with each other, security misconfiguration occurs more often.
Granting Public Access
Organizations often mistakenly grant public access to storage containers like S3 buckets within their cloud infrastructure, and it happens when organizations aren’t adequately aware of all security settings.
When S3 buckets containing millions of sensitive company data are left open without authorization control, it leaves the whole infrastructure exposed to security breaches. S3 buckets without proper side encryption, disabling the logging of S3 buckets and public access by ACLs are some common causes of misconfiguration.
Failure to Revoke Access
Another common misconfiguration arises when organizations fail to revoke access for former employees or unauthorized individuals. If access controls are not updated promptly, it can leave critical systems open to exploitation, as people no longer affiliated with the organization may retain access to sensitive resources.
Why Is CSPM Important?
CSPM tools have a huge impact on the security of cloud environments by greatly reducing the likelihood of data breaches. Gartner reports that a substantial number of data breaches in the cloud result from misconfigurations.
Including a CSPM tool in your security arsenal allows you to mitigate cloud-based security incidents arising from misconfigurations, offering an impressive 80% reduction in cloud-based security incidents, according to Gartner’s findings.
How Cloud Security Posture Management Works?
Cloud security posture management, or CSPM, protects your cloud infrastructure and mitigates all future risks by providing:
Visibility
CSPM gives you a clear, comprehensive view of your cloud environment through an easy-to-use console. With this tool, you can spot misconfigurations and keep track of your security settings. It also helps you monitor changes in activity patterns so you’re always aware of what’s going on in your cloud infrastructure.
Continuous threat detection
Cloud security posture management actively looks for threats throughout the application development lifecycle. It also prioritizes vulnerabilities depending on the cloud environment and can remediate them automatically. Unauthorized access to cloud resources and malicious activity are also detected during continuous threat detection.
Remediation of misconfiguration
To discover any misconfiguration and remediate it in real-time, CSPM compares the cloud configuration against the rules set by the organization and also industry standards. It eliminates all the security and human risks that can lead to security breaches, causing theft of personal information and the organization’s sensitive data.
Compliance assurance
CSPM ensures continuous compliance with regulatory requirements by automatically tracking and updating your compliance status. It generates detailed reports to demonstrate adherence to industry standards and provides real-time alerts for any compliance issues, making it easier to maintain regulatory requirements.
Discovering new threats
Real-time monitoring of the multi-cloud environment allows CSPM to discover new threats that can lead to a severe breach. From discovering anomalies, incorrect permission, and unauthorized activity to inappropriate access to data, CSPM is highly capable of finding threats in real-time.
Integration With DevSecOps
CSPM has been instrumental in cutting down the complexity across all multi-cloud environments and provides centralized control over all the resources. It can be integrated with DevOps tools so that it can accelerate the remediation and incident response within the environment.
Benefits of Cloud Security Posture Management
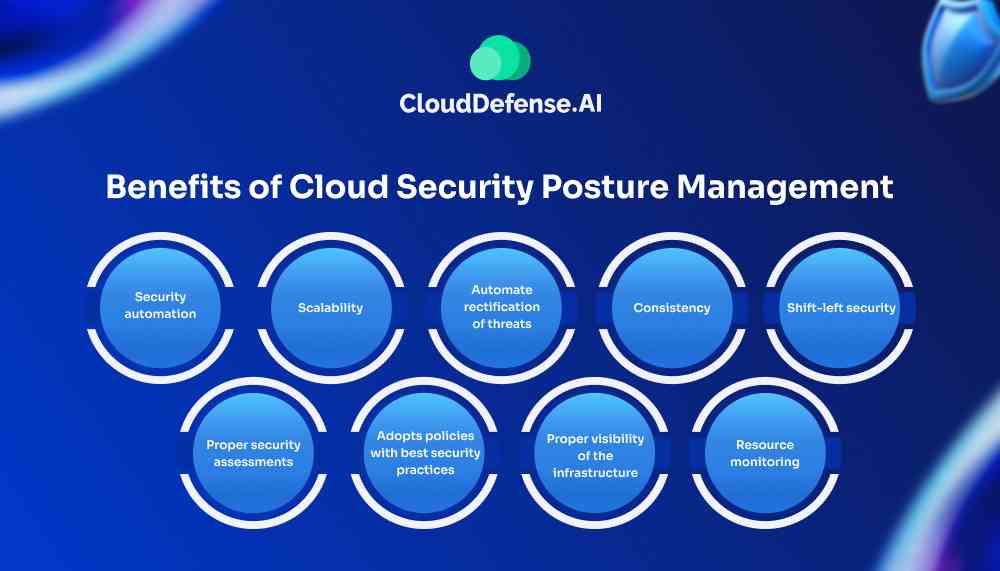
Cloud security posture management has become a pivotal tool in securing the cloud infrastructure of an organization. When CSPM is integrated into cloud infrastructure, you can benefit from it in a lot of ways;
Security automation
One of the primary benefits of CSPM is the automation of security, as it automatically enforces the security policies required to protect the infrastructure. From day one of implementation, it integrates all the security settings so that there is no occurrence of misconfiguration.
Scalability
CSPM, through automation, offers more efficiency than manual checking of security risks. This gives the organization the boost to scale its business while maintaining all the security measures to protect the growing resources in the cloud.
Automate rectification of threats
As cloud security posture management automates the security, it also automates the rectification of simple and complex threats. It uses predefined security policies to solve the issues while optimizing the security resources.
Consistency
Consistency is one of the key reasons organizations integrate CSPM as a security measure for their cloud workload. Whatever the size of the cloud workload, it consistently looks for security glitches without any limitation.
Shift-left security
Another primary reason many organizations integrate CSPM is that it helps security shift left by identifying risks at the beginning of the development. This early detection alerts the security management about the risks and helps it rectify them before they are exposed.
Proper security assessments
CSPM performs security assessments against external security standards and frameworks to ensure there are no policy violations for security breaches. It follows standards set by CIS benchmarks, ISO, and NIST frameworks, which are highly useful.
Adopts policies with best security practices
CSPM tools help in adopting the best security policies when integrated into a multi-cloud environment to mitigate all the risks. It chooses the best security practices from a ton of security libraries and makes sure there is no theft of personal information, card details, organization workflow, etc.
Proper visibility of the infrastructure
When it comes to gaining insight into the cloud configuration, security parameters of the cloud workload, and resource utilization, CSPM is really useful. This technology provides assessments and recommendations based on the best industry practices, which help address risks.
Resource monitoring
Helping organizations review and manage critical cloud resources (crown jewels) is one of the vital reasons organizations consider CSPM as the primary security tool. CSPM tools can automatically find and inventory all the cloud resources and assist security management.
Traditional Vs. Modern CSPM Tools: What’s Changed?
Legacy CSPM tools were great in their time. They helped businesses spot cloud misconfigurations, keep track of resources, monitor them in real time, and check if they were compliant. But let’s be real—they come with their own set of issues:
- Context-Free Alerts: Traditional CSPMs throw out alerts without giving you the full picture. They miss key details like how a misconfiguration affects your network or exposes sensitive data, so you’re left guessing how serious the problem is.
- Alert Overload: You’re bombarded with alerts, but they don’t tell you which ones are the most critical. So, your security team ends up sifting through a pile of notifications without a clear priority.
- Operational Mess: Managing these tools can be a hassle, often requiring additional tools and processes that aren’t always in sync with your main operations.
Modern CSPMs, on the other hand, have stepped up their game. They’ve built on the basics of legacy systems but added some serious upgrades:
- Contextual Awareness: They provide the full picture, giving you detailed insights about misconfigurations, including how they affect your network, data, and identities.
- Prioritized Alerts: Modern CSPMs sort alerts by criticality, so you can focus on the biggest risks first and cut down on the noise.
- Streamlined Operations: These tools fit better with your existing processes and systems, making your security operations smoother and more integrated.
These modern tools not only patch up the gaps left by their predecessors but also bolster cloud security with context-driven defenses. They help prevent threats from moving laterally, support DevOps and CI/CD workflows, minimize attack surfaces, and manage data and Kubernetes security more effectively.
CSPM vs. Other Cloud Security Solutions
There are a number of other cloud-specific security solutions that you can use to protect different components of the cloud. While CSPM primarily focuses on analyzing the security posture of live cloud environments—ensuring configurations and compliance are aligned to prevent misconfigurations—each solution serves its own purpose.
We have compared each one of them with CSPM to help you decide which ones you are going to need for a strong security infrastructure.
| Security Solution | Focus | Key Features | Comparison with CSPM |
| CNAPP Vs CSPM | Cloud-native application protection | Secures containerized, serverless, and microservices-based applications | CNAPP focuses on protecting cloud-native applications, addressing dynamic cloud-native architectures, whereas CSPM concentrates on overall cloud configurations and compliance. |
| CWPP Vs CSPM | Individual workloads and applications | Runtime protection, vulnerability management, threat detection specific to workloads | CWPP specializes in securing individual workloads and applications, while CSPM focuses on broader cloud configuration and compliance issues. |
| CASB Vs CSPM | Data movement between on-premises and cloud | Secures data moving between on-premises and cloud, enforces data access policies, visibility into data usage | CASB provides visibility and control over data access and movement between environments, whereas CSPM deals with cloud configuration and compliance. |
| CIEM Vs CSPM | Entitlements, permissions, and access controls | Manages entitlements, permissions, and access controls, reduces unauthorized access risks | CIEM focuses on managing and controlling user permissions and access levels, while CSPM addresses overall security posture and compliance. |
| IaC Security vs CSPM | Infrastructure deployment scripts | Validates security of deployment scripts and IaC templates to prevent insecure configurations | IaC Security ensures secure infrastructure deployment through code validation, whereas CSPM deals with ongoing configuration and compliance monitoring. |
Does Your Company Need a CSPM Tool?
If you’re a startup in the early stages, especially around Series A or B, you might think you don’t need a CSPM tool right away. However, even at this stage, as your cloud infrastructure grows, potential security gaps can appear. While Infrastructure as Code templates and native cloud tools might suffice in the beginning—especially if your dev team prioritizes security—introducing a CSPM tool early on can help you catch issues before they escalate.
For smaller security teams, CSPM tools provide that extra layer of confidence by streamlining alerts and giving you clear priorities, so you can stay focused on product development without letting security slip. And if you’re a larger company moving towards hybrid or multi-cloud systems, a CSPM tool isn’t just helpful—it’s critical for securing your growing cloud environment.
As your cloud infrastructure expands, CSPM ensures consistency across platforms, making it essential for any organization looking to scale securely. Whether you’re a startup or a large enterprise, adopting a CSPM tool early can be a smart move that pays off as you grow.
CloudDefense.AI’s Approach to CSPM
Keep your cloud environment safe and sound with CloudDefense.AI’s CSPM tool. Our solution takes the hassle out of securing your cloud by offering real-time visibility and smart, automated fixes to keep things running smoothly. Here’s a quick overview of our CSPM solution:
Hassle-Free Configuration Management
- Spot and Fix Issues: Quickly identify and resolve misconfigurations to prevent security vulnerabilities and ensure smooth operations.
- Prioritize Risks: Focus on the most critical risks first, based on their potential impact, so you address the biggest threats right away.
- Clear Actionable Insights: Receive detailed insights on each misconfiguration, including suggested corrective actions to streamline your response.
Unified Console for Holistic CSPM
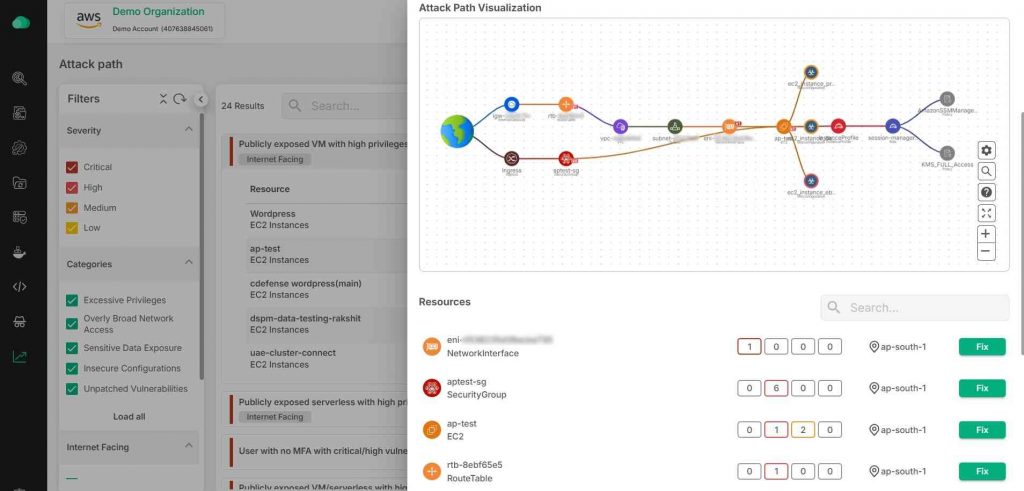
- Insightful Alert Visualization: Get a clear view of your alerts with detailed visual representations of attack paths, helping you quickly grasp the context of each incident.
- Prioritized Incident Details: See which alerts matter most by automatically sorting them based on their significance, so you can focus on what’s critical.
- Comprehensive Incident Breakdown: Understand the full scope of each alert with rich, contextual information that provides a complete picture, making it easier to act swiftly and accurately.
Agentless Architecture
- Rapid Deployment: Deploy quickly and easily without the need for agents.
- Performance Uninterrupted: Get comprehensive protection without impacting your system’s performance.
- Adapt Quickly: Adjust to changing cloud environments without the overhead of managing agents.
Multi-Cloud Security Management
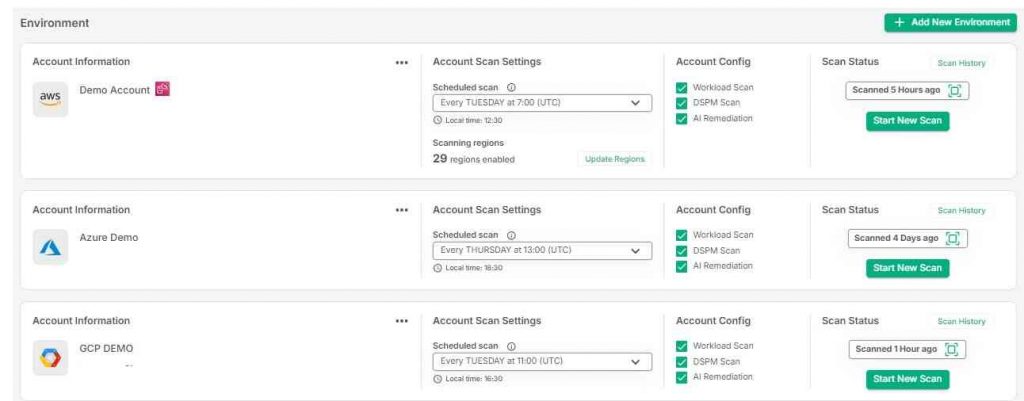
- Continuous Monitoring: Regularly check for misconfigurations across all your clouds.
- Centralized Management: Oversee and control security settings across AWS, Azure, and Google Cloud Platform (GCP) from a single, unified dashboard.
- Unified Cloud Oversight: Easily manage and oversee security across AWS, Azure, and GCP from a single, integrated dashboard, giving you a clear and consistent view of your entire cloud infrastructure.
Top-notch Compliance Management
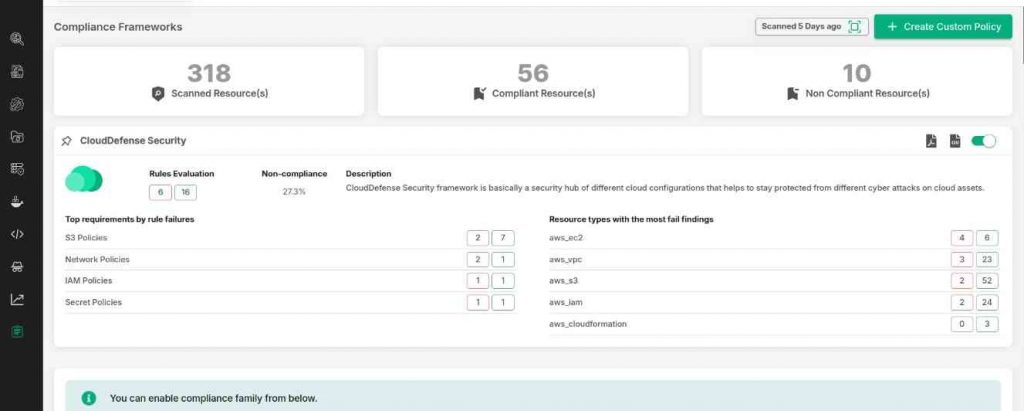
Effortless Compliance Tracking: Stay on top of regulatory requirements with a system that continuously monitors and updates your compliance status.
- Automated Compliance Reports: Quickly generate detailed reports to demonstrate your adherence to industry standards, saving you time and reducing manual effort.
- Customizable Policies: Adapt policies to fit your organization’s unique security requirements.
Want to take your cloud security to the next level? Book a demo today and see how CloudDefense.AI’s CSPM can make a difference for your organization.
FAQs
What is the use case for CSPM?
CSPM (Cloud Security Posture Management) is really about keeping your cloud setup secure. A typical use case? Spotting misconfigurations before they turn into security disasters—like making sure a database isn’t accidentally exposed to the public. It’s also useful for staying compliant with regulations like GDPR or HIPAA. In short, if your business relies on the cloud, CSPM helps you avoid costly mistakes by continuously monitoring and improving your security posture.
What is CWPP and CSPM?
CWPP protects workloads (like apps and containers), while CSPM monitors your cloud’s overall security posture. CWPP focuses on runtime protection, whereas CSPM looks for gaps and misconfigurations in your cloud setup.
What is the difference between CSPM and SIEM?
CSPM focuses on cloud security, finding issues like misconfigurations. SIEM tracks activity across your entire IT system, alerting you to threats in real-time. CSPM is proactive for cloud security; SIEM is more reactive across all systems.
Who needs CSPM?
Anyone using the cloud should have CSPM. It’s especially important for industries with sensitive data, like finance and healthcare, to avoid breaches and stay compliant.
Conclusion
Misconfigurations in the cloud are a huge problem and have caused countless data breaches for companies. That’s why Cloud Security Posture Management (CSPM) is such a big deal—it’s a must-have for businesses running things in the cloud. Protecting sensitive data, customer info, and everything valuable is a priority, and CSPM makes sure you’re covered. CSPM is quickly becoming a go-to for companies serious about their cloud security. Try CloudDefense.AI to protect your cloud environment and keep your data secure.







