Why Traditional Segmentation Approaches Aren’t Enough?
Too Complicated
First off, traditional segmentation is a real headache to set up. You’ve got to mess around with all these firewalls, VLANs, and subnets. IT teams spend ages configuring this stuff, and let’s be real, who’s got time for that?
Can’t Keep Up with Modern Apps
Here’s another problem: modern apps are always changing. They’re dynamic, they scale up and down, and they’re spread across different environments. The old segmentation methods just can’t keep pace. They’re too rigid and slow to adapt. By the time you’ve set up your segments, your app landscape has already changed.
Doesn’t Work Well in the Cloud
Cloud computing threw a wrench in the works for legacy segmentation. These old approaches were designed for on-premises data centers, not the fluid world of cloud environments. They just don’t translate well, leaving gaps in security that can be exploited.
Security Blind Spots
Traditional segmentation often leaves you with big blind spots in your network. You might think you’ve got everything locked down, but there are usually holes in your defense that you can’t even see.
Performance Issues
Let’s not forget about performance. Traditional segmentation can really slow things down. All that traffic going through firewalls and other security checkpoints? It creates bottlenecks and latency. In today’s world, where speed is everything, that’s a big problem.
Doesn’t Scale Well
As networks grow, legacy segmentation becomes a nightmare to manage. It doesn’t scale well at all. You end up with this complex web of rules and policies that’s impossible to keep track of. It’s a recipe for mistakes and security gaps.
So yeah, that’s why the old ways just don’t work anymore. We need something more flexible, scalable, and suited to today’s tech landscape. That’s where microsegmentation comes in, but that’s a whole other story that we discuss in coming sections.
What is Microsegmentation?
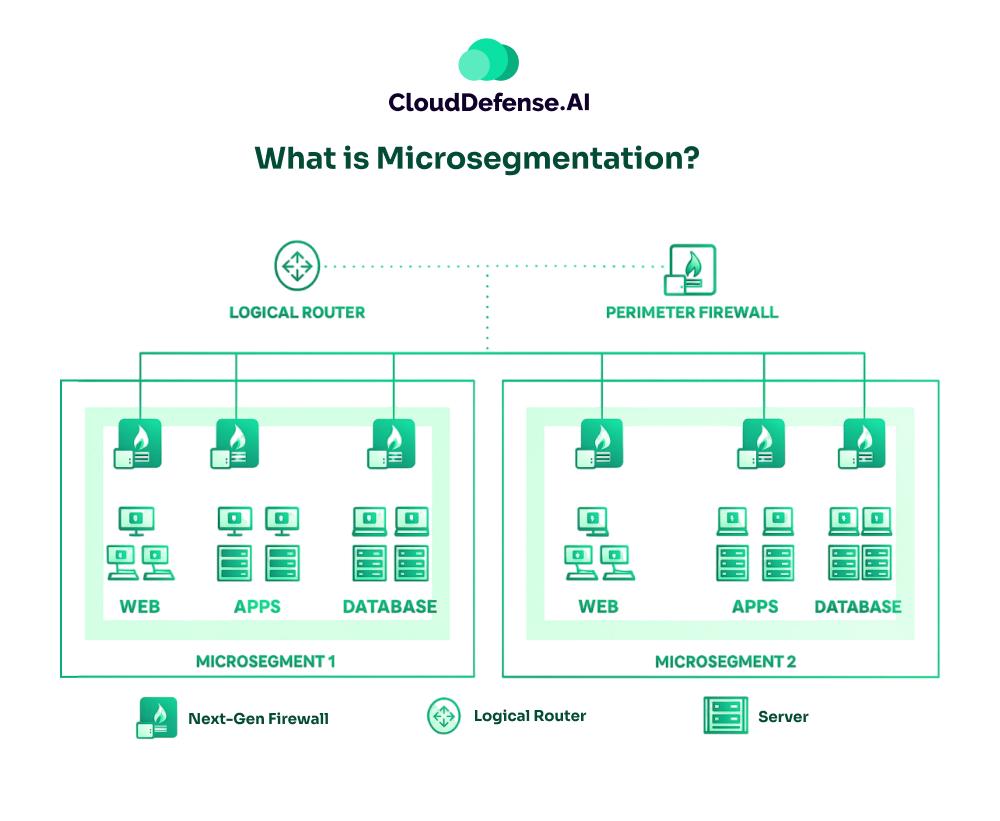
Microsegmentation is a key part of zero trust security. It’s basically the practice of breaking down your network into small, tightly controlled segments. Each segment only allows specific, authorized traffic.
In a zero trust setup, we don’t automatically trust anything inside or outside the network. Microsegmentation takes this idea and applies it at a granular level. It creates secure zones in data centers and cloud environments, letting you isolate workloads and protect them individually.
Basically, it assumes that threats can come from anywhere – inside or outside your network. So instead of just building a strong perimeter, you create a ton of internal barriers. This way:
- If an attacker gets in, they can’t move around freely
- You can spot and contain threats faster
- You have more control over who can access what
It’s a big shift from the old “castle-and-moat” approach, where we just focused on securing the network perimeter. With microsegmentation, security is baked into the fabric of the network itself.
Microsegmentation can be applied to various objects within a network:
- Workloads: These are specific instances of programs or applications running, each with its own resource requirements.
- Applications: The actual software programs running on computers, in the cloud, or on virtual machines.
- Virtual Machines (VMs): These are software-based computers that run within the framework of a physical computer, containing all necessary components to function as independent systems.
- Operating Systems (OSes): The fundamental software that manages a computer’s resources and allows other software to run.
Benefits of Microsegmentation
Improved Security
Microsegmentation makes it way harder for attackers to move around in your network. Even if they get in, they’re stuck in a tiny area. It’s like they’ve broken into a house but can only access one room. Good luck doing much damage that way.
Better Visibility
With microsegmentation, you can see exactly what’s going on in your network. You know who’s communicating with whom and what apps are doing what. It’s like having x-ray vision for your IT infrastructure. It makes spotting weird behavior a lot easier.
Easier Compliance
If you’re in an industry with strict regulations, microsegmentation is a saviour. It helps you control and track data flow, which is huge for things like GDPR or HIPAA. You can prove to auditors that you’re keeping sensitive data locked down tight.
Flexible Security
Your network’s always changing, right? New apps, new users, and cloud stuff. Microsegmentation can keep up. You can adjust security policies on the fly without having to rewire your whole network. It’s security that moves as fast as your business.
Reduced Attack Surface
By limiting what can talk to what, you’re basically shrinking the target for attackers. There are fewer ways in, fewer ways to move around. It’s like closing a bunch of doors and windows that bad guys could use.
Better Performance
Yeah, security often slows things down. But microsegmentation can actually help here. By controlling traffic more precisely, you can reduce network congestion. Your legit traffic flows more smoothly.
Cloud-Ready Security
Moving to the cloud? Microsegmentation has your back. It works just as well in the cloud as on-premises, so you can keep your security consistent no matter where your stuff is running.
Faster Breach Detection
Because you can see everything that’s happening, you spot weird stuff faster. If something’s not behaving the way it should, it sticks out as odd. This means you can catch and stop attacks quicker, before they do serious damage.
Cost Savings
In the long run, microsegmentation can save you money. You’re preventing breaches, which are crazy expensive. Plus, you’re using your network resources more efficiently. It’s an investment that pays off.
How does Microsegmentation Work?
As discussed earlier, Microsegmentation creates highly granular security zones within your network. Imagine it like creating custom security bubbles around specific applications or workloads. These bubbles are enforced using firewalls or security policies that dictate exactly what traffic can flow in and out.
Here’s the key: by default, all traffic is denied. This aligns with the zero-trust approach, which states that nothing is trusted until explicitly allowed. Security policies are then created to permit only the essential communication needed between applications within their designated zones.
For example, the marketing database might only be allowed to talk to the website server and wouldn’t have access to the financial transactions database. This strict control significantly reduces the attack surface for any potential threats. When a hacker breaches one zone, they’re stuck within its boundaries, unable to roam freely, and wreak havoc across your entire network.
Traditionally, firewalls might separate broad categories like “web servers” or “internal networks.” Microsegmentation takes it a step further. Imagine you can define specific policies for each individual application or workload.
Here’s the technical overview:
- Segmentation: Microsegmentation tools leverage technologies like network virtualization or security policies on physical firewalls to carve up your network into these tiny zones.
- Policy Enforcement: Once the zones are defined, you can set granular access controls. This means specifying exactly what traffic is allowed in and out of each zone. For example, the marketing database might only be allowed to communicate with the marketing application server, not the finance department’s systems.
- Zero Trust: Microsegmentation aligns perfectly with a zero-trust security model. By default, all traffic is denied unless explicitly allowed by the policy. This minimizes the blast radius of an attack. Even if a hacker breaches one zone, they’ll struggle to pivot to other parts of the network because communication is so restricted.
Microsegmentation significantly reduces the attack surface and hinders a hacker’s ability to move laterally within your network by creating these micro-perimeters and enforcing strict traffic controls. Even if a breach occurs, the damage is contained within a specific segment, minimizing the overall impact.
Microsegmentation vs. Network Segmentation
| Feature | Network Segmentation | Microsegmentation |
| Granularity | Less granular – segments broad network zones (e.g., DMZ, internal network) | Very granular – segments individual applications or workloads |
| Focus | Protects against unauthorized access from outside the network | Protects against lateral movement within the network |
| Implementation | Physical separation (VLANs, subnets) or firewalls | Software-defined policies, network devices, cloud platform functionalities |
| Security Approach | Perimeter-based defense | Zero-trust approach, least privilege access |
| Complexity | Relatively simple to set up | More complex due to granular control |
| Scalability | Scales well for static network environments | More dynamic and adaptable for changing workloads |
| Attack Surface | Larger attack surface due to fewer zones | Smaller attack surface due to isolation of workloads |
| Lateral Movement | Easier for attackers to move laterally within a zone | Limits attacker movement and lateral spread of breaches |
| Example | Separating public-facing servers from internal servers | Isolating a development environment from production servers |
Types of Microsegmentation
Application Segmentation
This is all about locking down your apps. It’s pretty straightforward – you set up rules for how different apps can talk to each other. Say you’ve got a web server and a database. You make sure they can chat, but nothing else can butt in. It’s super specific, which is great for security.
The cool thing about application segmentation is that it doesn’t care where your app is running. It could be on-premises or in the cloud; it doesn’t matter. The rules stick. This is huge for people using hybrid setups.
It’s also pretty good at stopping lateral movement. If some bad actor gets into one app, they can’t just hop around to others. Each app is in its own little bubble.
User Segmentation
Now we’re talking about controlling what users can access. It’s not just about whether you can log in or not. It gets way more detailed than that.
With user segmentation, you can set up rules based on all sorts of stuff. Job roles, locations, time of day, whatever. So maybe your marketing team can access certain apps, but only during work hours and only from the office network.
This is great for things like BYOD policies or remote work setups. You can make sure people only get to the stuff they need, when they need it, from where they’re supposed to access it.
Container Segmentation
This one’s for people working with containers. Container segmentation is about setting up security rules for these containers. The tricky part is that containers come and go real quick. They spin up, do their job, and disappear. Traditional security can’t keep up.
With container segmentation, you can set up rules that automatically apply to containers as they pop up. It’s dynamic, just like the containers themselves. You can control how containers talk to each other, to the outside world, whatever you need.
This is crucial for microservices architectures, where a bunch of little services work together instead of one big monolithic app. Container segmentation helps keep all those moving parts secure.
Final Words
Alright, let’s wrap this up. Microsegmentation is currently a big deal in network security, and for good reason. It’s not just some fancy tech jargon – it’s a practical way to lock down your network without making it a nightmare to use. Sure, it takes some work to set up, but the payoff is huge. You get better security, more control, and a clearer picture of what’s happening in your network.
Whether you’re worried about compliance, moving to the cloud, or just want to sleep better at night knowing your data is safe, microsegmentation is worth a look. It’s not perfect, but it’s much better than the old ways of doing things. So if you’re serious about security, it’s time to get on board.







