What is OSINT?
OSINT, or Open-Source Intelligence, is basically all the information you can legally get your hands on without breaking into anything. We’re talking about stuff that’s out there for anyone to see or find. It’s not some secret spy stuff – it’s the kind of info you could dig up if you had enough time and knew where to look.
Now, when we say “open source,” we’re not just talking about the internet, though that’s a big part of it. It’s anything that’s publicly available. That old newspaper at the library? Open-Source Intelligence. A company’s annual report? Open-Source Intelligence. Even that tweet you posted five years ago? Yeah, that’s Open-Source Intelligence too.
Here’s the thing—OSINT isn’t just about text. It’s pictures, videos, those boring webinars you never watch, speeches, and conference presentations—if it’s out there and accessible, it counts.
What makes OSINT different from other types of intelligence gathering? A few things:
- It’s all above board. We’re not talking about hacking or stealing info here. It’s all stuff that’s legally available.
- It uses a ton of different sources. Social media, news articles, public records – you name it.
- It often uses some pretty fancy tech to make sense of all this data. We’re talking machine learning and natural language processing—the kind of stuff that can crunch through mountains of information and spit out something useful.
What is OSINT actually used for in the real world?
Now, here’s where it gets interesting for cybersecurity folks. Open-Source Intelligence is like a double-edged sword. The good guys use it to find weak spots in their defenses before the bad guys do. But those same bad guys? They’re using OSINT too, looking for any little piece of info they can use to plan an attack.
For a hacker, it’s used to scope out the target. it helps them figure out where to look for weaknesses. Maybe they discover a company is still using an old, vulnerable system. Or they might find an employee who’s a bit too loose-lipped on social media. All of this helps them build a picture of where the soft spots might be.
But here’s the thing—Open-Source Intelligence isn’t just a tool for the bad guys. Smart companies and individuals use it on themselves. It’s like checking your own blind spots. You gather all the public information about yourself or your business, and then you ask, “If I were a hacker, what could I do with this?”
Maybe you realize your company’s LinkedIn page is giving away too much about your tech stack. Or you find out your employees are posting photos that show sensitive info in the background.
This self-check can reveal some eye-opening stuff. Maybe you realize your company’s LinkedIn page is giving away too much about your tech stack. Or you find out your employees are posting photos that show sensitive info in the background. This kind of self-assessment helps you plug leaks before they become real problems.
So, whether you’re on offense or defense, Open-Source Intelligence is a crucial tool. For attackers, it’s the first step in planning a strike. For defenders, it’s a wake-up call about what info you’re unknowingly putting out there. Either way, in today’s digital world, ignoring OSINT is like leaving your front door wide open and hoping no one walks in.
Open Source Intelligence (OSINT) Framework
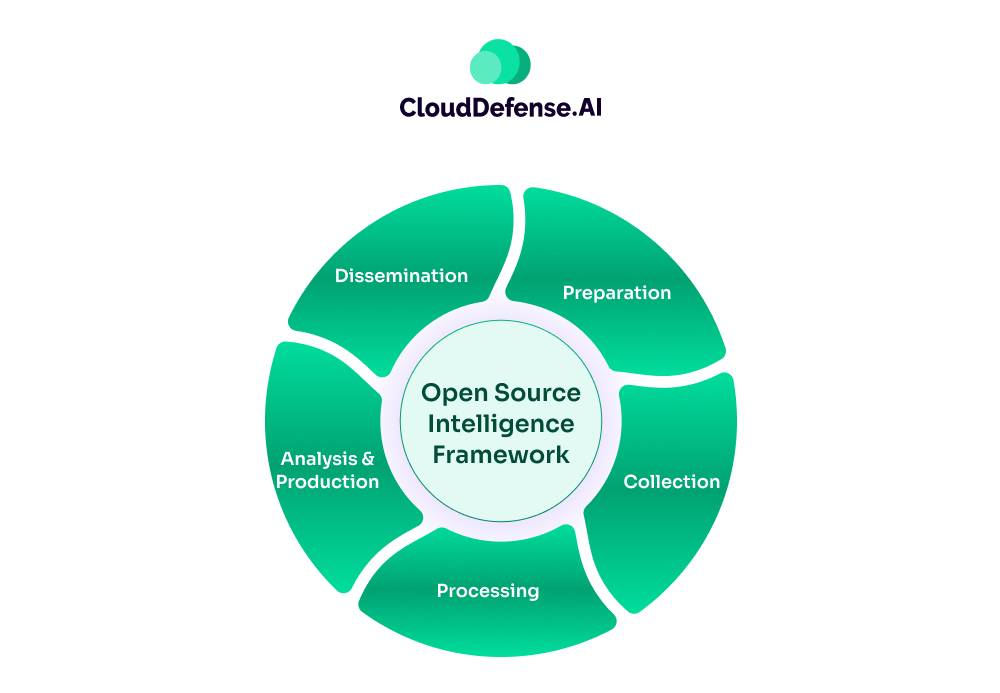
Alright, let’s break down the Intelligence Cycle and what it means for OSINT work. This cycle is a framework that helps structure the intelligence gathering process. It’s not set in stone, but most versions follow similar steps. Understanding this cycle can really help you get your head around how Open-Source Intelligence research works.
Here are the main stages:
1. Preparation
This is where you figure out what you’re actually trying to do. You’re asking questions like: What’s the objective here? What do we need to know? Where are we likely to find this information? It’s about setting the stage for your research.
2. Collection
This is the meat and potatoes of OSINT work. You’re gathering data from all the relevant sources you can find. This could be anything from social media posts to public records. The key here is to cast a wide net.
3. Processing
Once you’ve got all this data, you need to organize it. This stage is about sorting through what you’ve collected and putting it into a format that’s easier to work with. You might be creating databases, timelines, or just organizing your notes.
4. Analysis and Production
This is where you start making sense of all that information you’ve gathered. You’re looking for patterns, connections, and insights. The goal is to take all that raw data and turn it into actionable intelligence. You’re also producing a report that answers the original intelligence question, draws conclusions, and suggests what to do next.
5. Dissemination
Finally, you need to present your findings. This could be in the form of written reports, presentations, or briefings. The key here is to communicate your insights clearly to the stakeholders who need this information.
This cycle isn’t a one-and-done thing. Often, you’ll go through these steps multiple times as you refine your research and uncover new leads. It’s a process that helps ensure you’re being thorough and systematic in your OSINT work.
Remember, Open-Source Intelligence isn’t just about finding information – it’s about finding the right information and understanding what it means. This cycle helps you do just that.
The Importance of OSINT in Application Security
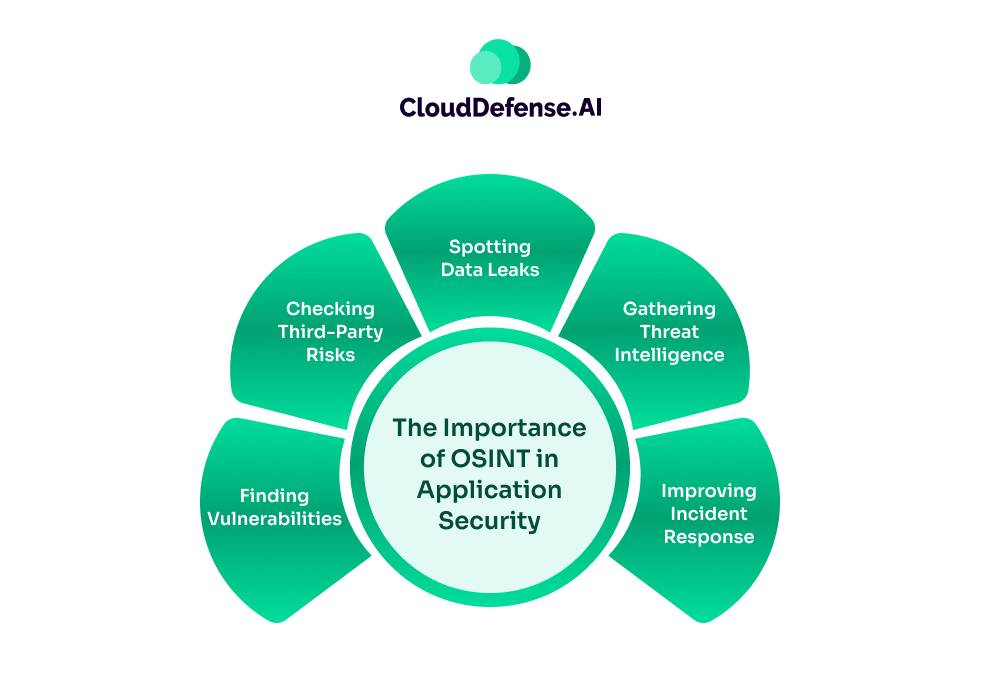
Open-Source Intelligence plays a crucial role in application security, and here’s why:
1. Finding Vulnerabilities
Instead of waiting for an attack to happen, security teams can use Open-Source Intelligence to check public databases and forums where people share info about software weaknesses. This way, they can patch up holes before hackers even get a chance to exploit them.
2. Checking Third-Party Risks
Now, most apps these days don’t work alone. They rely on all sorts of third-party components and services. Open-Source Intelligence helps keep tabs on these external parts. It’s like doing a background check on all the pieces that make up your app, making sure they’re not bringing any unwanted risks to the table.
3. Spotting Data Leaks:
Data leaks are a nightmare for any company. Open-Source Intelligence tools are like digital bloodhounds, sniffing out any sensitive info that might’ve slipped through the cracks and ended up where it shouldn’t be on the internet.
4. Gathering Threat Intelligence
Open-Source Intelligence helps security teams stay up-to-date on new threats. By collecting info from various sources, they can see what kinds of attacks are trending and prepare accordingly.
5. Improving Incident Response
Lastly, if the worst happens and there’s a security breach, OSINT becomes super valuable. It can help figure out who the attackers might be, how they operate, and why they did it. This info is gold when it comes to dealing with the aftermath and preventing future attacks.
Practical Attack Vectors OSINT Presents in Application Security
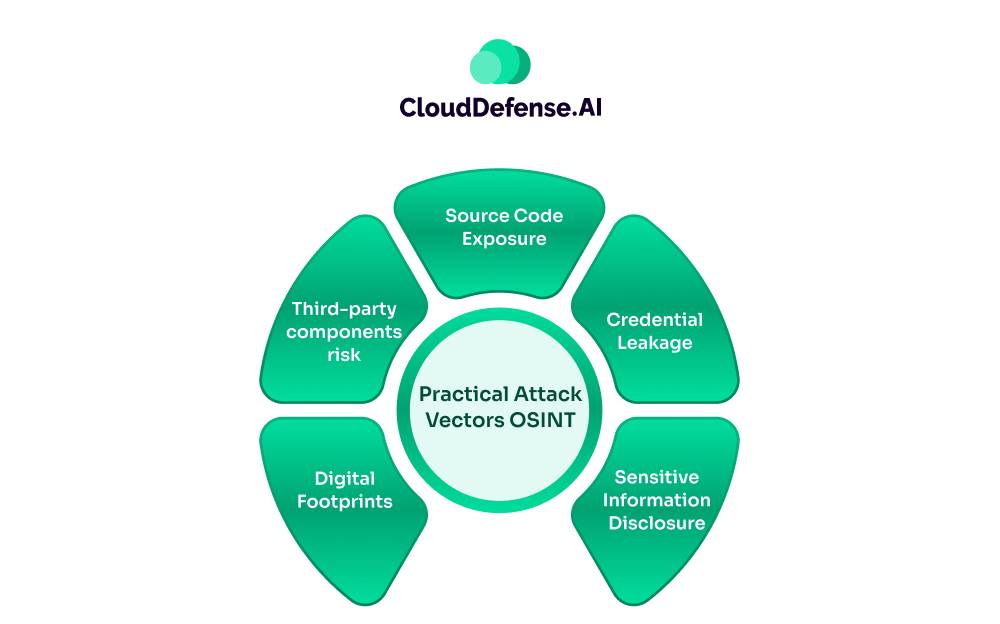
Let’s get real about how Open-Source Intelligence can actually be used against us in app security. It’s not all doom and gloom, but knowing these risks helps us stay on our toes.
Source Code Exposure
Ever thought about what might happen if parts of your code end up online? It happens more often than you’d think. Developers might accidentally push sensitive code to public repositories on GitHub or Bitbucket. Or maybe your app uses open-source components that have their code out in the open. Attackers can comb through this exposed code, looking for weaknesses to exploit.
Credential Leakage
Passwords and login info can end up in some pretty dark corners of the internet. Hackers hang out on dark web forums and marketplaces, trading this kind of info. Sometimes it’s stolen data, but other times it’s just careless employees oversharing. Either way, it’s a goldmine for attackers looking to break into your systems.
Sensitive Information Disclosure
Developers are problem solvers, and when they hit a roadblock, they often turn to sites like Stack Overflow for help. The trouble is, in their rush to get answers, they might accidentally share more than they should. Same goes for paste sites like Pastebin. What looks like a harmless code snippet might actually contain sensitive info that shouldn’t be public.
Third-party components risk
We use a lot of open-source stuff in our apps these days, which is great, but it also means we inherit all their security problems. If a vulnerability pops up in one of these components, suddenly, our app is at risk, too.
Digital Footprints
Lastly, don’t forget about search engines and web archives. These are supposed to be helpful, but sometimes they end up caching and storing stuff we’d rather keep private. And those web archive sites? They can be a goldmine of old, forgotten info about our apps and systems.
OSINT Best Practices
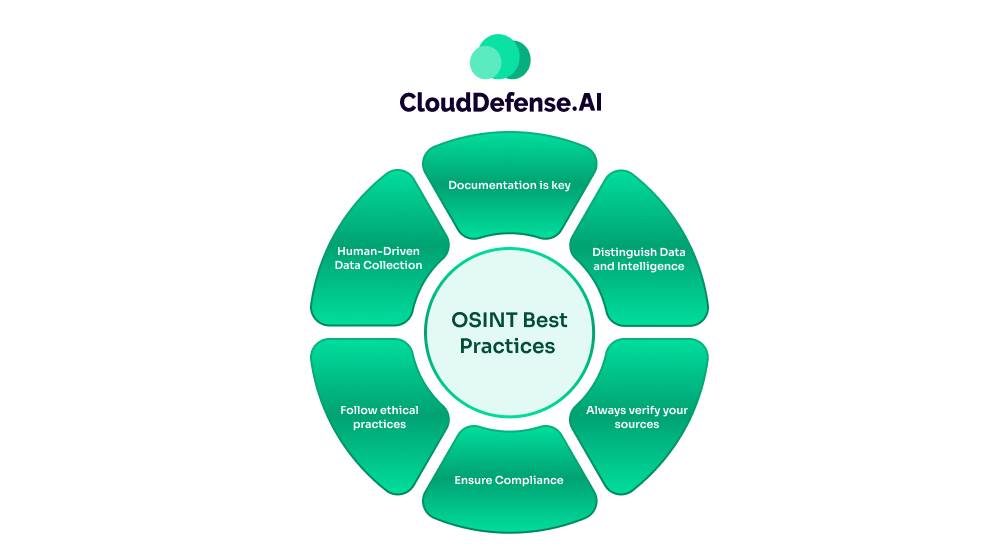
When it comes to using Open-Source Intelligence for cyber defense, there are some key best practices you need to keep in mind. Let’s break them down:
Documentation is key
Keep detailed records of everything you do. Where did you find that piece of information? When? How? This isn’t just about being organized – it’s about being able to verify your findings later. If you can’t trace your steps, your work loses credibility.
Distinguish Data and Intelligence
Open source data is just raw info you can find publicly. It’s like having a bunch of puzzle pieces. Open-source intelligence is when you’ve put those pieces together to form a useful picture. The trick is not to get bogged down in collecting every piece of data you can find. Instead, focus on what you actually need for your specific investigation. It’s about quality, not quantity.
Always verify your sources
Just because something’s out there doesn’t mean it’s true. Cross-check information across multiple sources. Be especially wary of social media – it’s a goldmine of info, but also a minefield of misinformation.
Ensure Compliance
If you’re dealing with personal data—and with Open-Source Intelligence, you often are—you need to be careful. Regulations like GDPR are no joke. You could be creating a big risk for your organization if you’re not handling this data properly. And if you stumble across evidence of a crime during your investigation, there might be specific legal requirements about how you handle that info.
Follow ethical practices
Just because the information is public doesn’t mean you can use it however you want. You need to think about the impact on people, both inside and outside your organization. Collect only what you need to meet your goals, and make sure you’re not violating anyone’s rights in the process.
Human-Driven Data Collection
Don’t let technology do all the work. It’s easy to set up systems to collect data automatically, but this can lead to gathering stuff you shouldn’t. You need humans in the loop, making decisions about what to collect and how to use it. Everyone involved in your OSINT project should understand the ethical and legal limits.
Final Words
OSINT has now become an indispensable part of cybersecurity. However, it can also be a double-edged sword, strengthening defenses or exposing vulnerabilities, depending on how it’s used. Remember, OSINT is a powerful tool, but with great power comes great responsibility. Use it wisely, use it ethically, and always stay on the right side of the law.







