In 2023, the world witnessed an alarming surge in cyberattacks, impacting over 343 million victims globally. Shockingly, the period from 2021 to 2023 saw a staggering 72% increase in attacks targeting both companies and individuals. Leading research firms like Gartner predict a continuation of this trend in the current year.
In light of these growing threats, businesses must adopt strong cybersecurity measures to combat daily challenges effectively. Operational Security, or OPSEC, emerges as a specialized process uniquely equipped to address these pressing issues.
In this article, we will dive deeper into the concept of Operational Security, exploring its significance as a critical risk management methodology widely employed by companies worldwide.
Let’s dive right in!
What is Operational Security?
Operational Security, or OPSEC, is a risk management process aimed at protecting sensitive information from adversaries. It involves analyzing operations from potential attackers’ perspectives to identify vulnerabilities.
OPSEC involves behavioral monitoring, social media scrutiny, and security best practices. Information is classified according to sensitivity levels to prioritize protective measures.
Originally developed in the military, OPSEC has expanded to various sectors, emphasizing proactive measures to prevent data breaches.
By assessing risks and implementing customized countermeasures, organizations can mitigate threats effectively. OPSEC promotes a vigilant approach to security, ensuring the confidentiality and integrity of critical information.
The Five Steps of Operational Security
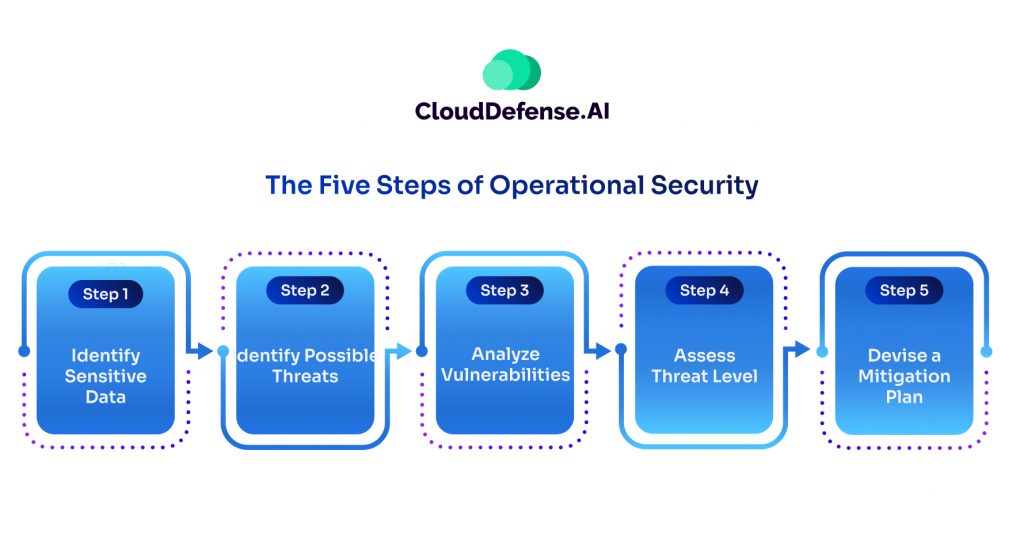
The Five Steps of OPSEC form a structured approach to protecting sensitive data and reducing security risks within organizations:
Step1: Identify Sensitive Data
Organizations begin by identifying the types of sensitive information they possess, such as customer details, financial data, and intellectual property. Understanding what data needs protection is essential for allocating resources effectively.
Step 2: Identify Possible Threats
Once sensitive data is identified, organizations assess potential threats, including external actors, competitors, and insider threats such as negligent or disgruntled employees. Recognizing potential adversaries helps in devising appropriate security measures.
Step 3: Analyze Vulnerabilities
Organizations analyze their security defenses to identify vulnerabilities that could be exploited by threats. This involves assessing processes and technologies to pinpoint weaknesses that attackers could exploit to gain access to sensitive data.
Step 4: Assess Threat Level
Each vulnerability is evaluated based on factors like the likelihood of an attack, potential damage, and mitigation effort required. This assessment helps prioritize resources, focusing on vulnerabilities with the highest risk of exploitation.
Step 5: Devise a Mitigation Plan
Armed with insights from the previous steps, organizations develop and implement a plan to mitigate identified threats. Countermeasures may include hardware updates, policy enhancements, and employee training on security best practices. Plans should be simple, adaptable, and regularly updated to address evolving security threats.
Best Practices for Operational Security
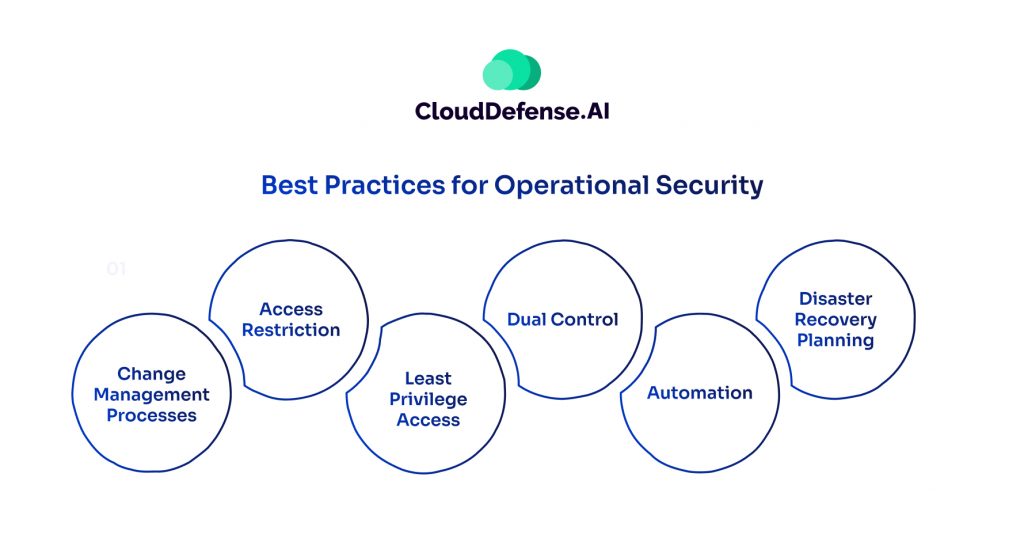
Best Practices for OPSEC include a range of strategies aimed at identifying and mitigating potential threats and vulnerabilities within organizations’ operations and systems:
Change Management Processes
Implement precise change management procedures to control and log network modifications. This ensures changes are monitored and audited effectively, reducing the risk of unauthorized alterations.
Access Restriction
Limit network access to only essential devices and personnel through stringent authentication measures. Adopting a “need-to-know” basis for information sharing minimizes exposure to potential threats.
Least Privilege Access
Assign employees the minimum access required to perform their duties, following the principle of least privilege. This reduces the likelihood of insider threats, limits the attack surface, and enhances audit and compliance readiness.
Dual Control
Separate network maintenance roles from security policy-setting roles to prevent conflicts of interest. This ensures accountability and reduces the risk of insider collusion compromising security measures.
Automation
Automate tasks to reduce human error, a common vulnerability in security processes. Automation streamlines operations minimizes oversight, and enhances overall security posture.
Disaster Recovery Planning
Develop robust incident response and disaster recovery plans to address potential cyberattacks and mitigate damages effectively. Planning for contingencies ensures swift and coordinated responses to security breaches.
What are the Elements of Operational Security?
The Elements of OPSEC consist of five foundational components essential for protecting sensitive data and mitigating security risks within organizations:
- Identifying Sensitive Data: Organizations must identify and categorize their sensitive data resources, including customer information, intellectual property, financial statements, and research findings. These data assets require heightened security measures to prevent unauthorized access and disclosure.
- Identifying Potential Threats: Comprehensive OPSEC involves identifying and documenting potential threats to sensitive data, both from external attackers and insider threats. Understanding the various ways data breaches can occur enables organizations to implement targeted security measures.
- Analyzing Security Vulnerabilities: Conducting an objective evaluation of current security measures is crucial for identifying vulnerabilities that could be exploited to access sensitive data. This assessment encompasses internal and external security protection measures, highlighting areas for improvement.
- Determining Risk Levels: Each identified vulnerability must be assessed based on factors such as the potential impact of an attack, the likelihood of occurrence, and the organization’s ability to recover. Ranking risks helps prioritize mitigation efforts and resource allocation effectively.
- Implementing Threat Mitigation Plans: Based on the analysis of security vulnerabilities and risk levels, organizations develop and implement threat mitigation plans tailored to their unique environment. These plans may include employee training, hardware upgrades, and data governance policies aimed at protecting sensitive information.
Why is OPSEC Important?
OPSEC is crucial for businesses because it offers several advantages. It acts as a proactive shield against financial losses, damage to reputation, and legal troubles caused by data breaches. By spotting and addressing possible threats and weaknesses, OPSEC helps reduce the expenses linked with fixing breaches, avoiding big financial strains.
It protects the trust and credibility of stakeholders by preventing the exposure of sensitive information and preserving the organization’s reputation. Adherence to OPSEC principles ensures alignment with regulatory requirements, mitigating the risk of fines and legal actions.
Furthermore, OPSEC builds business continuity by mitigating the potential disruptions caused by security incidents.
OPSEC helps you keep important data safe from getting into the wrong hands, protecting a company’s plans and strategies. This helps maintain its competitive advantage. OPSEC also strengthens cybersecurity and ensures businesses can thrive in the industry without facing major risks.
Final Words
Operational security stands as a cornerstone of modern cybersecurity, offering a full-on approach to protecting sensitive data from unauthorized access and cyber threats. By diligently following the OPSEC process, organizations can identify, assess, and mitigate potential risks, thereby strengthening their security posture and protecting their critical assets.
Through measures such as identity and access management, business continuity planning, and AI-driven automation, companies can effectively counter threats and ensure resilience in the face of adversity.
Accepting OPSEC as a fundamental element of their cybersecurity strategy gives organizations the power to continue doing business with confidence and resilience.







