Definition — What is Role-Based Access Control (RBAC)?
Role-Based Access Control, or RBAC, is a simple but powerful system that defines who can do what within an organization. It works by assigning roles to users based on their responsibilities and linking those roles to specific permissions. With RBAC, access to sensitive resources is limited to authorized personnel, reducing risks and ensuring better control over operations.
For example, in a company, a manager might have access to employee performance data, while a customer service agent can only see customer support tickets. By restricting access based on roles, RBAC helps businesses improve security and stay efficient.
Role-Based Access Control is widely recognized as an essential practice for managing access in modern IT environments, whether on-premises or in the cloud. It’s effective, practical, and scalable for organizations of all sizes.
How does Role-Based Access Control work?
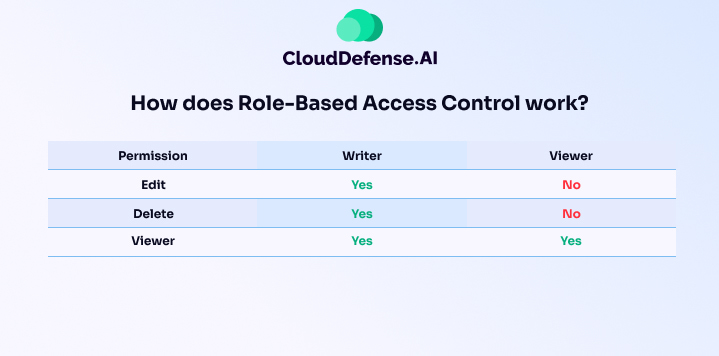
RBAC fosters the principle of allowing the least-possible access privileges to employees that are enough for them to carry out their organizational tasks. This method will enable you to create different access-control templates that can be deployed amongst employees requiring the same amount of access.
Administrators are not required to set the access privileges for each employee manually and can just rely on automated access control features. This helps in defining the set of resources that should be made available to each user class.
To make it easier for you to understand what RBAC does, consider this example of how Google Docs allow you to set access privileges for people accessing your document online. It empowers you to set what level of access a certain individual has when it comes to manipulating your document, and this is somewhat similar to how Role-Based Access Control works.
Why is Role-Based Access Control important?
RBAC, or Role-Based Access Control, is absolutely crucial. It helps organizations control who gets access to what and when. No one gets too much access, and no one gets too little. It’s all about keeping things secure, simple, and efficient. Here’s why Role-Based Access Control is a game-changer for organizations.
1. Automated Permission Management
RBAC makes managing access much easier. Instead of assigning permissions to each individual user, roles are created. People are assigned to a role, and that role comes with specific permissions. It’s fast. It’s simple. It works.
For instance, if someone starts working in a new department or gets promoted, they just get a new role, and their access rights are automatically updated. You don’t have to waste time manually changing permissions. This approach works for both full-time employees and temporary contractors—giving them the right access without risking anything.
2. Compliance Made Simple
Regulations are becoming stricter, and businesses need to be able to prove they are complying. With Role-Based Access Control, it’s easy to demonstrate who has access to what information and when. This is vital in industries like healthcare, finance, and any other field that handles sensitive data.
The clear roles and access levels provided by Role-Based Access Control help ensure your business is ready for audits and is following the rules. No guessing. No errors. Just accountability.
3. Protecting Your Sensitive Data
Data breaches are a real threat, and RBAC helps minimize the risk. With Role-Based Access Control, only the people who need access to sensitive data get it. If someone doesn’t need to see payroll data, they won’t. Simple as that.
It’s all about making sure that if someone’s credentials are compromised, the hacker can’t get access to the whole system. Role-Based Access Control helps protect your data from being exposed to the wrong people, reducing the chances of an attack.
4. Scalable and Flexible
Role-Based Access Control works for any size organization. Whether you’re a small startup or a massive enterprise, RBAC can grow with you. As your business changes or expands, RBAC helps adjust roles quickly and easily.
If new departments open up or new projects start, RBAC lets you create and assign roles on the fly, keeping everything running smoothly. It’s flexible and adaptable, making it perfect for businesses that are always on the move.
RBAC is essential for any business that wants to keep its data safe, stay compliant, and streamline its processes. It’s not just another security feature—it’s a must-have for smart and efficient operations.
Three common principles of RBAC
Role-based access control revolves around the three principles:
- Assignment: Assigning a role to a user based on their tasks and access rights.
- Authorization: Authorizing the user to leverage their role for completing a task.
- Access Rights: Providing the user with access rights if they are authorized to perform a task.
Here’s a breakdown of the three core principles:
1. Role Assignment
First, you’ve got to assign roles. Without roles, RBAC doesn’t work. A user can’t have permissions or access without being tied to a specific role. Think of roles as the key that unlocks access to specific parts of your system. Each role comes with its own set of permissions, giving users access to the resources they need to do their job. Whether it’s a manager, developer, or customer support representative, every user needs to be connected to the right role to get the right permissions.
2. Role Authorization
Once a role is assigned, the user has to be authorized for it. This is where accountability comes in. Just assigning someone a role isn’t enough. The organization needs to ensure that the person is qualified and has the necessary clearance to handle the role. This helps keep things secure and ensures that only trusted individuals are allowed to access sensitive data or make important decisions. Without this step, you run the risk of giving the wrong people access to critical systems.
3. Permission Authorization
Finally, permissions must be granted based on the role assignments. Only users who have been properly authorized through their role can access specific resources or perform certain actions. This rule ensures that there’s no overreach or unnecessary exposure to sensitive information. By restricting permissions to only those who need them, you minimize the risk of accidental or malicious breaches.
RBAC works because these three rules work together to maintain control and ensure that access is always tightly monitored. When implemented correctly, RBAC doesn’t just protect your systems—it makes everything run more smoothly and efficiently.
Types of role-based access control
1. Core RBAC
Core RBAC is the basic model, and it works by assigning users to specific roles, which then determine what they can access.
- Assigns roles to users.
- Grants permissions based on roles.
- Makes it simple and easy to manage user access.
This system is great for organizations that don’t need anything too complicated—just clear roles and permissions.
2. Hierarchical RBAC
Hierarchical RBAC builds on Core RBAC but takes it up a notch with a clear role hierarchy, allowing higher roles to inherit permissions from lower ones.
- Creates a hierarchy (e.g., manager > employee).
- Higher roles automatically inherit lower role permissions.
- Works well for organizations with a clear structure.
This model is ideal for bigger organizations where roles are organized in layers and permissions need to be automatically passed down.
3. Constrained RBAC
Constrained RBAC adds rules and restrictions to ensure that role assignments and permissions stay within limits. It’s about tighter control.
- Applies constraints to roles (e.g., preventing conflicting actions).
- Enforces business rules around who gets what access.
- Adds extra layers of security by restricting access.
For organizations that need more control and don’t want to risk too much flexibility, this is the way to go.
4. Symmetric RBAC
Symmetric RBAC gives users more flexibility by letting them both assign roles to themselves and give roles to others.
- Lets users assign roles and permissions.
- Shares responsibilities between roles and permissions.
- Allows for more flexible access control.
This model works best when organizations need more flexibility and control over access, but still want to keep things organized.
RBAC vs. Other Access Control Frameworks
There are several access control frameworks that organizations might use as alternatives to RBAC, depending on their specific needs. Some organizations even combine RBAC with other models to fine-tune access control. Below are some common access control frameworks:
| Access Control Framework | Description | When to Use | Key Differences from RBAC |
| Role-Based Access Control (RBAC) | Assigns permissions based on roles, simplifying management by grouping users into roles with specific permissions. | Ideal for organizations with defined roles and clear responsibilities. | Simple and clear, focuses on roles and permissions. |
| Mandatory Access Control (MAC) | Strict control over who can access resources based on security labels. Users cannot change access settings. | Used in environments with high security requirements, like government or military. | More rigid than RBAC, requires predefined security levels and policies. |
| Discretionary Access Control (DAC) | Owners of resources decide who has access. Users can grant permissions to others. | Suitable for environments with flexibility and less strict security needs. | More flexible than RBAC, but potentially less secure. Permissions are user-driven. |
| Attribute-Based Access Control (ABAC) | Access is based on attributes (e.g., user department, time of access, etc.), offering more fine-grained control. | Best for complex environments with diverse conditions or dynamic access needs. | More complex than RBAC, allows for access decisions based on multiple attributes, not just roles. |
| Access Control List (ACL) | Specifies which users or systems can access specific resources, and what actions they can perform. | Works well in file systems or smaller-scale systems. | Less scalable than RBAC and more focused on individual resources. |
Each framework has its strengths and is suited to different organizational needs. While RBAC is often simpler and more structured, others like ABAC or MAC offer more flexibility or security in certain environments.
Best Practices for Implementing RBAC
Like any other tech, there is a set of Role-based access control best practices that you can consider to make your RBAC security system more effective.
Implementing IAM:
Identity and Access Management (IAM) tools are not a necessary condition for approaching RBAC. However, it is best to include it with the package to make it easier to deploy RBAC. IAM helps in identifying digital and cloud assets and having it will help your company to manage access privileges.
Creating a List of Assets:
Making a list of assets and resources that require access management is something that you should start with before Role-based access control implementation.
Categorize Roles:
Have your security team assess your employees and divide roles based on the individuals who require the same access privileges. This helps make the access management process more straightforward.
Providing Only The Least Amount Of Access:
Understand the amount of access your employees will need to complete their tasks. Assign them the least possible access privileges required by them. This will significantly reduce the attack surface from both internal and external threats.
Carry Out Audits:
Once you have everything in motion, plan audits for all the roles. This helps in determining new access privileges, if roles have changed with time, and identifying any unnecessary access privileges.
FAQ
Here are a few queries that people have regarding RBAC.
How to check RBAC in Kubernetes?
Use the command “kubectl api-versions” to verify whether RBAC is enabled in your Kubernetes. To view another user’s permissions on Kubernetes, you can enter this command, “kubectl auth can-i –list –as=username”
What is the primary goal of Role-Based Access Control (RBAC)?
RBAC primarily focuses on restricting network access to its users based on their role in the organization. Roles, in turn, help determine the amount of access privileges assigned to them.
How does RBAC differ from other access control models?
RBAC is much superior to access control methods when managing access to the network. Generic Access control methods safeguard low-level data and handle individual access management. RBAC is used for large companies and protects more data.
Conclusion
Role-Based Access Control (RBAC) is a crucial part of modern access management and data security. It’s not just about permissions; it’s a tool for keeping information safe, ensuring rules are followed, and managing who can access what.
Having RBAC helps protect organizations from unwanted access and data leaks, simplifies administrative tasks, and ensures access aligns with job roles. In a world where data protection is vital and security threats are common, RBAC is the guardian you need to build a robust cybersecurity detail.







