The arrival of AI code editors revolutionized how developers write and debug their code. Even though the use of AI started as just a feature, it soon became an integral part and evolved into a complete AI based code editor.
Among all of these, Cursor and Windsurf are widely used AI code editors. It enhances accuracy and productivity in the development process by a large margin. However, these code editors also raise the question “Is the code secure to use?”.
The answer lies with the approach of how the DevSecOps team manages the security of the code during the software development process. Here is a complete step-by-step guide on how DevSecOps can automatically secure code from Cursor and Windsurf and maintain optimum security posture.
Cursor and Its Security Posture
Cursor is an AI code editor running on VS Code to offer real-time code suggestions and testing features. This editor features a privacy mode that allows developers to use the code specifically for the ongoing projector and no other projects in the future.
It also enables developers to prevent specific files in a project from getting indexed by the AI system. This tool has also come up with specific rules. During integration into the IDE, developers can set security guidelines and coding standards. Despite all these security measures, the auto-generated codes aren’t completely secure.
This Cursor AppSec integration is of high importance for the organization. The security feature of Cursors requires regular monitoring and secure storage to safeguard them from any kind of malicious tweaking.
Windsurf and Its Security Posture
Windsurf serves as an agentic AI code editor that has similar features to Cursor AI. But it holds the capabilities to assess the complete projects and use the context to automate various tasks. It allows developers to control the training of the agentic editor on sensitive data, preventing unintentional exposure.
Since Windsurf can generate context from the whole project, it helps with code suggestions that are better secured. This agentic AI editor often uses the MCP server to gain more accurate context. However, there lies the risk that if the context is not secure or an external source is not properly sanitised, it leads to vulnerabilities.
Importantly, the Cascade agents also utilize the Memories and Rules feature to use context for code generation. Even though it follows all the best practices of REST API, it doesn’t inherently secure the code. A Windsurf DevSecOps integration serves as a solution, as it can help in integrating security checks at every step.
Issues from Automatically Securing Codes from Cursor and Windsurf
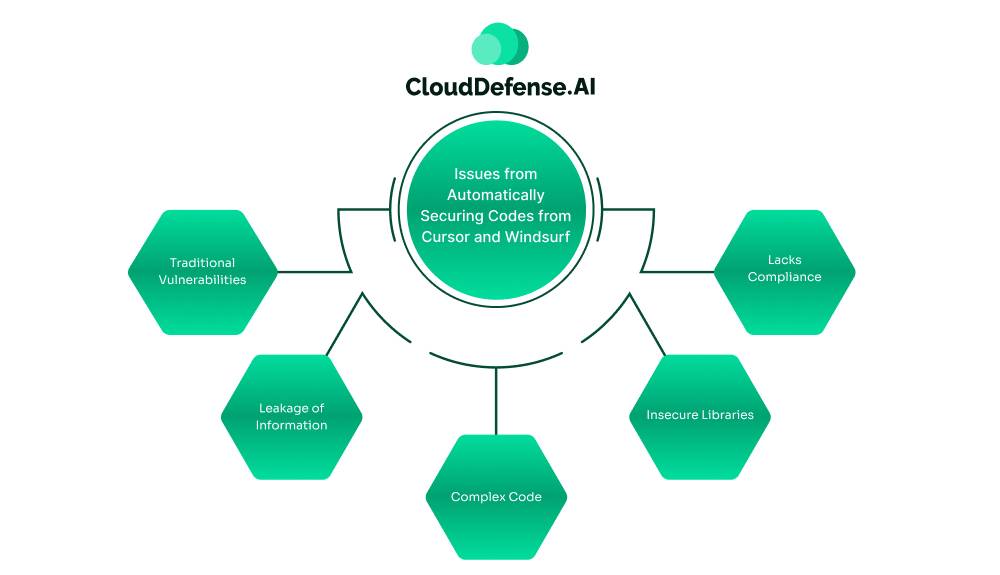
Integrating AI backed code editor or Agent AI in IDE for automated code generation can lead to many potential security issues:
- Traditional Vulnerabilities: In many instances, auto-generated codes can introduce certain vulnerabilities in the workflow. Vulnerabilities in SQL Injection, weak encryption, and XSS are serious issues that can make the whole codebase vulnerable.
- Leakage of Information: A Data leak is another major issue that can occur, as Cursor and Windsurf often have access to sensitive data. If the code is not properly validated, then it can expose information API keys or user information.
- Complex Code: Based on the context of the developer’s prompt, an AI powered editor can generate complex code. These difficult codes often give rise to security flaws in the development lifecycle.
- Insecure Libraries: AI code editors like Windsurf and Cursor often leverage open source code or insecure libraries for code generation. As a result, vulnerabilities are often generated through those libraries.
- Lacks Compliance: As auto generated codes help in a quicker software development process, it also leads to compliance issues. Reviewing code and ensuring its adherence to industry regulation standards becomes problematic.
Complete Guide on How DevSecOps Team Can Introduce Security in the AI Based Development Lifecycle
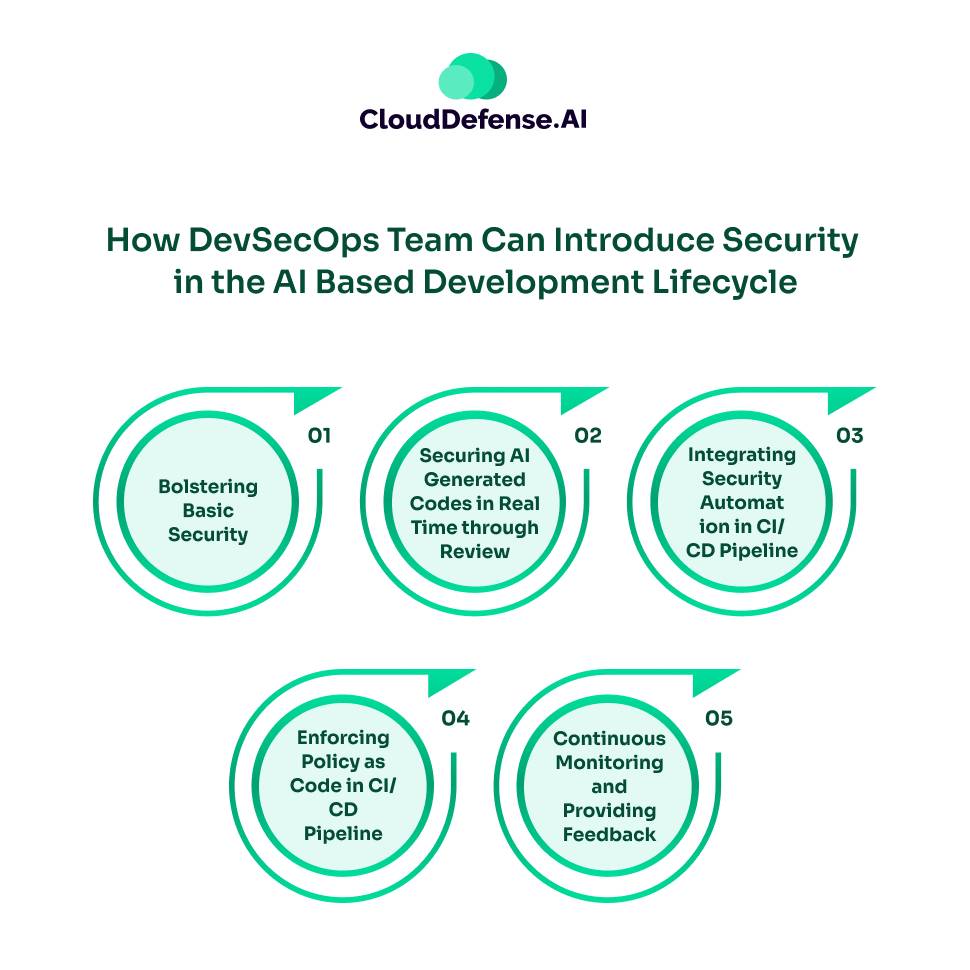
Here is a complete guide on how the DevSecOps team can introduce various security measures and practices into the development lifecycle. It highlights the security check that the team integrates to auto secure AI generated codes used by developers:
First Step: Bolstering Basic Security
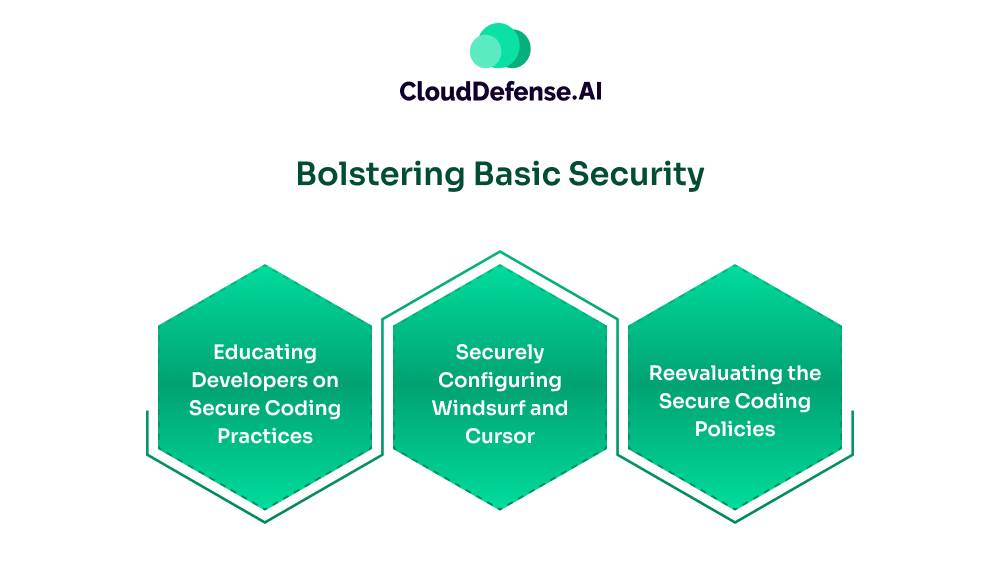
Before beginning with the process to secure code from Cursor and Windsurf, it is important to bolster the foundation security. Various approaches must be taken:
- Educating Developers on Secure Coding Practices: The Organization should emphasize training developers on different secure coding practices. Importantly, developers should be taught how to use prompts to generate secure code. Workshops must be conducted to highlight various risks associated with AI generated codes.
- Securely Configuring Windsurf and Cursor: It is vital for the DevSecOps team to configure the security settings of Windsurf and Cursor AI. The team should focus on implementing admin control on AI powered code editors to ensure they follow all the on-premises security policies.
- Reevaluating the Secure Coding Policies: The secure coding policies and standards must be reevaluated to ensure they cover AI generated codes. The team should opt for guidelines that ensure the review of codes and maintain a security library.
Second Step: Securing AI Generated Codes in Real Time through Review
The DevSecOps team needs to work towards using real-time security assessments for all the AI generated code. The processes Cursor and Windsurf DevSecOps team can leverage to review all the code with security flaws:
- Integrating Linters Plugins: The team can integrate linters and SAST plugins within the IDEs. It will provide feedback regarding any issue with the AI generated code in real-time. Usually, tools like Cursor and Windsurf enable teams to include plugins that provide real-time security feedback.
- Peer Assessment: The DevSecOps team must thoroughly perform peer review on all the code generated from Cursor and Windsurf. Pull or merge request review functionality can be utilized by developers for reviewing any code. The organization has the option to create a dedicated team to review common vulnerabilities and security flaws within the codebase in the IDE.
Third Step: Integrating Security Automation in CI/CD Pipeline
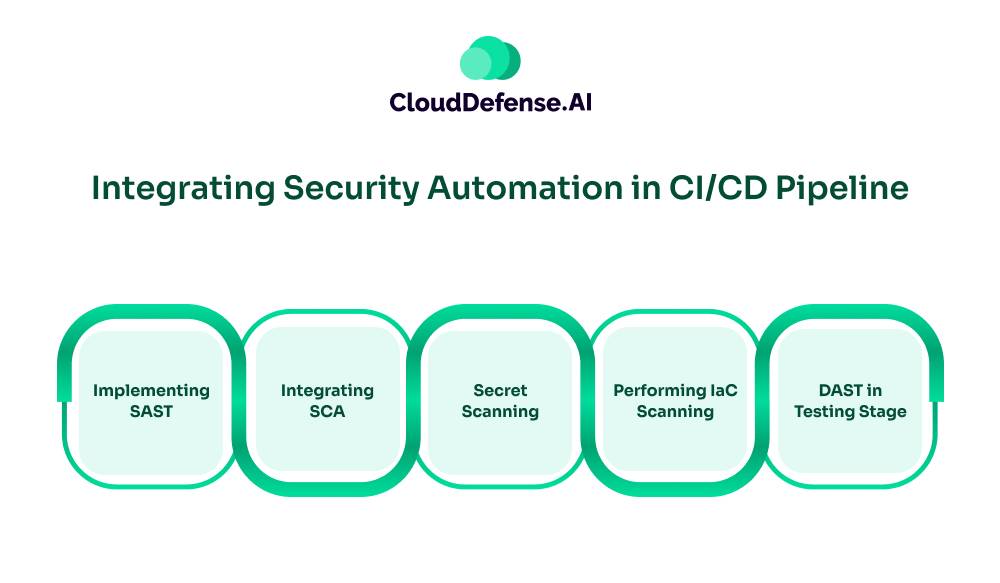
Integrating security automation serves as an important aspect in the Windsurf and Cursor AppSec integration. The team needs to focus on leveraging various security tools that will auto secure all the AI generated codes.
- Implementing SAST: Static Application Security Testing serves as a vital aspect of the DevSecOps model. The team should integrate the SAST tool in the CI pipeline so that it can automate the scanning process of source code. It will help in identifying vulnerabilities before they are compiled into the codebase.
- Integrating SCA: Along with SAST, Software Composition Analysis(SCA) can be utilized to hunt for vulnerabilities. It can be implemented in the CI pipeline to find vulnerabilities within public libraries or open-source components that AI powered code editors use.
- Secret Scanning: Organisations also need to utilize Secret Scanning to prevent accidental exposure of a secret that can jeopardize the whole application or web app. This tool must be implemented in the CI pipeline so that it can scan every commit for secrets like passwords or tokens in the code. This tool discovers secrets by matching them with known secret formats. Once discovered, it sends an alert to the team.
- Performing IaC Scanning: The DevSecOps team must perform IaC scanning if AI generated codes are leveraged for Infrastructure as Code. IaC Scanners should be integrated into the CI pipeline involving all the infrastructure codes. It will scan all the configurations by comparing them with all the best practices and regulatory requirements, and provide reports of misconfigurations.
- DAST in Testing Stage: DevSecOps team needs to implement Dynamic Application Security Testing in the CD pipeline. It is ideal to integrate DAST in the test environment after the application has been deployed. As a result, DAST will assess the AI code-based application for vulnerabilities and report to the DevSecOps team.
Fourth Step: Enforcing Policy as Code in CI/CD Pipeline
DevSecOps must utilize Policy as Code or PaC to enforce various security policies and rules as code to ensure automation and version control. PaC needs to be integrated into the CI/CD pipeline as it will help the team to write a custom policy and ensure it is consistently enforced. Importantly, this approach will validate all the dependencies, structure, and configuration associated with AI generated code to an optimum security posture.
Fifth Step: Continuous Monitoring and Providing Feedback
Once an application based on AI generated code is deployed in the market, DevSecOps must continue with the monitoring process. The team can utilize:
- RASP and WAF: RASP or Runtime Application Self Protection is a vital tool that attaches to the application runtime to detect vulnerabilities and prevent attacks. Web Application Firewall, on the other hand, will be useful in filtering out all the malicious traffic.
- Vulnerability Check and Penetration Testing: The Organization can develop teams to perform vulnerability assessment and penetration testing at regular intervals. The team should mainly focus on the features and segments that are based on the code from Cursor and Windsurf.
- Utilizing Feedback Loop: On many occasions, specific vulnerability types might appear from the AI based codes from Cursor or Windsurf. The vulnerability often appears due to various issues, which include unsanitized inputs. When specific vulnerabilities appear a number of times, the developers need to update them on the feedback loop and prompt guidelines. This will allow others to provide input prompts while mentioning that the AI code editor must avoid those specific vulnerabilities.
Human Intervention: Manually Monitoring Codes from Cursor and Windsurf
Automating the process to secure code from Cursor and Windsurf can significantly reduce the chance of security breaches. However, human intervention and assessment of AI generated code are still important. Here are some approach the DevSecOps team can take to ensure only secure code are committed:
- Reviewing the Code: When Surfer or Windsurf generates a code, developers must review it and understand the logic. They shouldn’t consider the code as a secure and reliable input.
- Keeping Team Up to Date: AI code editor tools like Surfer and Windsurfer are constantly evolving with new training models. The team must stay up to date with new vulnerabilities that the new models might arise.
- Maintaining Responsibility: The team or developer who commits a particular AI generated code must be accountable for it. This approach will compel every developer to only commit secure code from Cursor and Windsurf.
Final Words
While AI generated codes from Cursor and Windsurf are streamlining the software development, it isn’t still devoid of security flaws. However, by putting safety checks in every step in the software development lifecycle, the DevSecOps team can enable secure usage of Cursor and Windsurf.
We have highlighted the steps that the DevSecOps team can implement to ensure a secure and efficient AI powered software development process. As we move forward, the use of AI based codes from Cursor and Winsurf will become a norm. The organization needs to adapt and make the most of the available tools to ensure security.







