In today’s fast-paced software development process, developers are always trying to accelerate the development and deployment process. However, vulnerabilities have become a serious obstacle for developers in achieving a shorter time to market. The high volume of vulnerability alerts is overwhelming developers.
Not only that, but it is also forcing them to spend a lot of time on security triage. Usually, developers perform manual triage, the process of identifying, analyzing, and prioritizing security vulnerabilities for remediation. However, it is a time-consuming and complex task, leading to a slow development process, delayed remediation, and fatigue among teams.
What can be done? The answer lies with vulnerability triage automation. Automating the vulnerability triage process has become a necessity for every organization. This process streamlines the vulnerability prioritization process, and improves the development workflow. Through this guide, we will dive into various aspects of vulnerability triage automation and best practices for implementing vulnerability triage automation.
The Primary Issues with Manual Security Triage

Nowadays, modern organizations are developing applications at an unprecedented pace. However, to address vulnerabilities in the development environment, DevSec teams often rely on manual security triage using SAST, DAST, SCA, and IAST tools. These AppSec tools are effective in identifying vulnerabilities, but they produce tons of alerts. The issues that comes up are:
- Lengthy Process: Traditional AppSec tools provide a lot of security alerts. Developers, along with security teams, have to invest a lot of time in manually sorting and analyzing these alerts. It is not only lengthy but also overwhelms developers, leading to development fatigue.
- Human Error Prone: Security triage of alerts manually by developers often leads to human error. Human fatigue from repetitive tasks and biases in judgement lead to missing must-fix security vulnerabilities or inconsistent prioritisation. Result? Deployment of vulnerable code segments.
- Inconsistent Prioritisation: During manual triage, developers prioritise vulnerabilities based on their risk assessment criteria and experience. Moreover, not all organizations have specific application security policies in place for prioritizing vulnerabilities. Thus, it leads to inconsistency in the prioritization of alerts during security triage.
- Low Productivity: It has been reported that developers have to spend a lot of their development time manually performing security triage on all the findings. A lot of time is wasted in analyzing false positives. This leads to wastage of development time, leading to low productivity.
- Limited Scalability: Scalability is another major issue with manual security triage. Modern organizations leverage Agile and DevOps approaches to boost their development process. The manual triaging process is unable to cope with today’s high-speed development process, causing scalability issues.
What is Vulnerability Triage Automation?
Vulnerability triage automation in application security is a process of automatically analyzing, prioritizing, and responding to security vulnerabilities. It has become a necessity for modern organizations to implement automation for performing vulnerability triage, reducing manual security triage efforts.
This approach helps in creating a data-driven and intelligent security triage system where security alerts are categorized and prioritized based on their real-world impact. Thus, it helps developers to focus on development tasks while security professionals work on remediating high-impact vulnerabilities and other vital tasks.
Automation not only addresses traditional challenges with manual triage but also transforms the process from reactive to a proactive and efficient approach. Organizations are gradually adopting vulnerability triage automation in their application security with the primary objectives of:
- Boosting Remediation Process: To cope with the modern Agile application development process, organizations are adopting this approach to intelligently classify and assign vulnerability to the right team. It helps in quickly remediating the issue before it impacts the developed application.
- Minimizing Alert Fatigue: Developers have to spend a lot of time analyzing security alerts, which often turn out to be false positives. However, vulnerability triage automation helps in intelligently prioritizing alerts, filtering out all the false positives, and enabling teams to focus on must-fix findings.
- Getting Contextual Intelligence: It also helps the DevSec team to gain contextual intelligence and utilize it to enrich the vulnerability identification process. It is useful in prioritizing the appropriate security findings.
How Vulnerability Triage Automation Works?
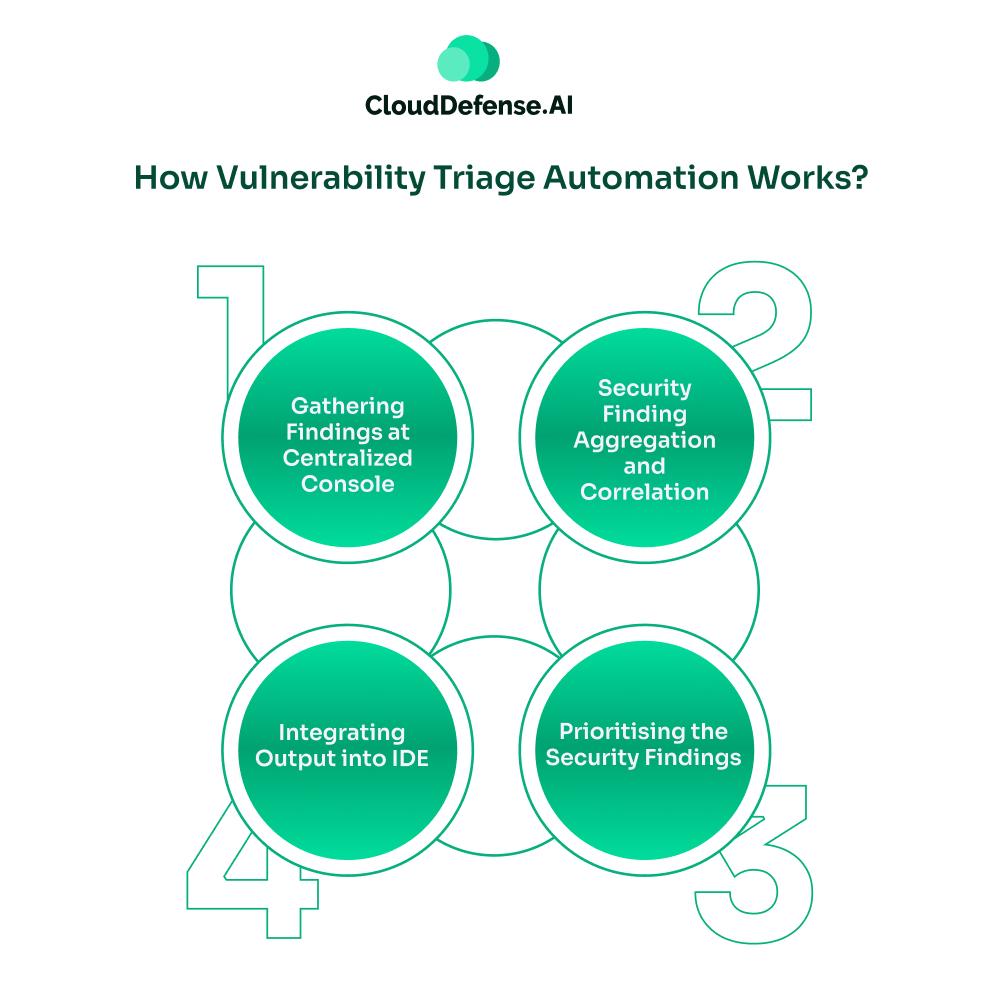
Vulnerability triage automation serves as an intelligent solution for modern organizations. It is benefiting them in many ways, especially with false positive removal. But curious to know, how does it work? Well, it works by involving various components and steps. Here, let’s take a look at how it works:
- Step 1-Gathering Findings at Centralized Console: The centralized vulnerability console serves as the main platform where security findings from all sources are consolidated. Application Security Orchestration and Correlations (ASOC tools are often utilized. It helps in consolidating and streamlining all the security alerts from tools like SAST, DAST, and SCA.
- Step 2-Security Finding Aggregation and Correlation: After consolidating all the security findings in a centralized console, ASOC also performs normalization and deduplication to provide a clean output. This process also involves Application Vulnerability Correlation for correlating all the security findings. AVC utilizes an intelligent correlation process to provide detailed insight into the security findings. This is useful in removing all the noise from the manual security triage process.
- Step 3-Prioritising the Security Findings: This serves as an important step where the process intelligently prioritises vulnerabilities using an automated prioritisation engine. Usually, CVSS is utilized for prioritisation, but automated prioritisation does more than that. It considers various factors like business context, vulnerability impact, severity score, exploitability, and various other factors while prioritising vulnerabilities. Using these factors, the prioritization engineer creates a severity score for each finding. This enables the security and development team to focus on security findings that require immediate remediation.
- Step 4-Integrating Output into IDE: The final task is to integrate all the prioritised alerts from automated security triage into the developer’s workflow. It will not only help developers to easily fix vulnerabilities in the beginning, but also prevent them from committing vulnerable code. The integration can be achieved through policy-based automation, a ticketing system, or instant feedback. It is effective in accelerating and streamlining the remediation process.
Best Practices to Follow During Vulnerability Triage Automation
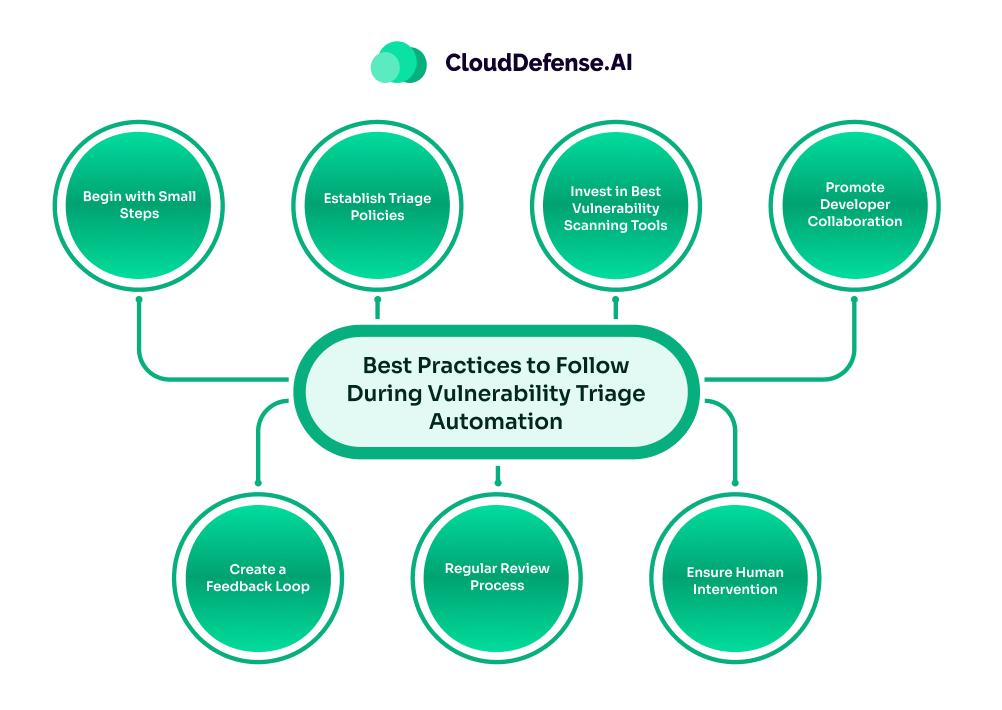
For an effective implementation of vulnerability triage automation, it is vital that the organization follows certain best practices:
- Begin with Small Steps: Rather than automating the vulnerability triage process, it is vital that organizations start with specific application or vulnerability types. A step-by-step will be ideal as it will help in refining the process and expanding accordingly.
- Establish Triage Policies: While automating security triage, organizations must establish a clear policy for prioritizing and assigning vulnerabilities. The policies should be based on the business’s goals and risk tolerance.
- Invest in Best Vulnerability Scanning Tools: Security findings that are provided by scanning tools play a vital role in determining the effectiveness of automation. So, the organization must invest in top-quality scanning tools that offer accurate and false-positive removal.
- Promote Developer Collaboration: A successful automated vulnerability triage is only possible through the development team’s involvement. The security team must work with the developers to get insight into the workflow and develop a streamlined process.
- Create a Feedback Loop: Organizations should implement a policy for continuously monitoring the effectiveness of the automated triage process and create a feedback loop. It will help security and development tools to refine the configuration and make improvements.
- Regular Review Process: Since the cybersecurity world is constantly evolving, regularly reviewing the policies has become vital. All the security trial policies and rules should be reviewed to ensure they stay effective.
- Ensure Human Intervention: Automated vulnerability triage can seamlessly perform most of the tasks, but in some cases, human expertise is required. A security team must always be available when the tool requires assistance in triaging complex vulnerabilities.
Benefits of Vulnerability Triage Automation
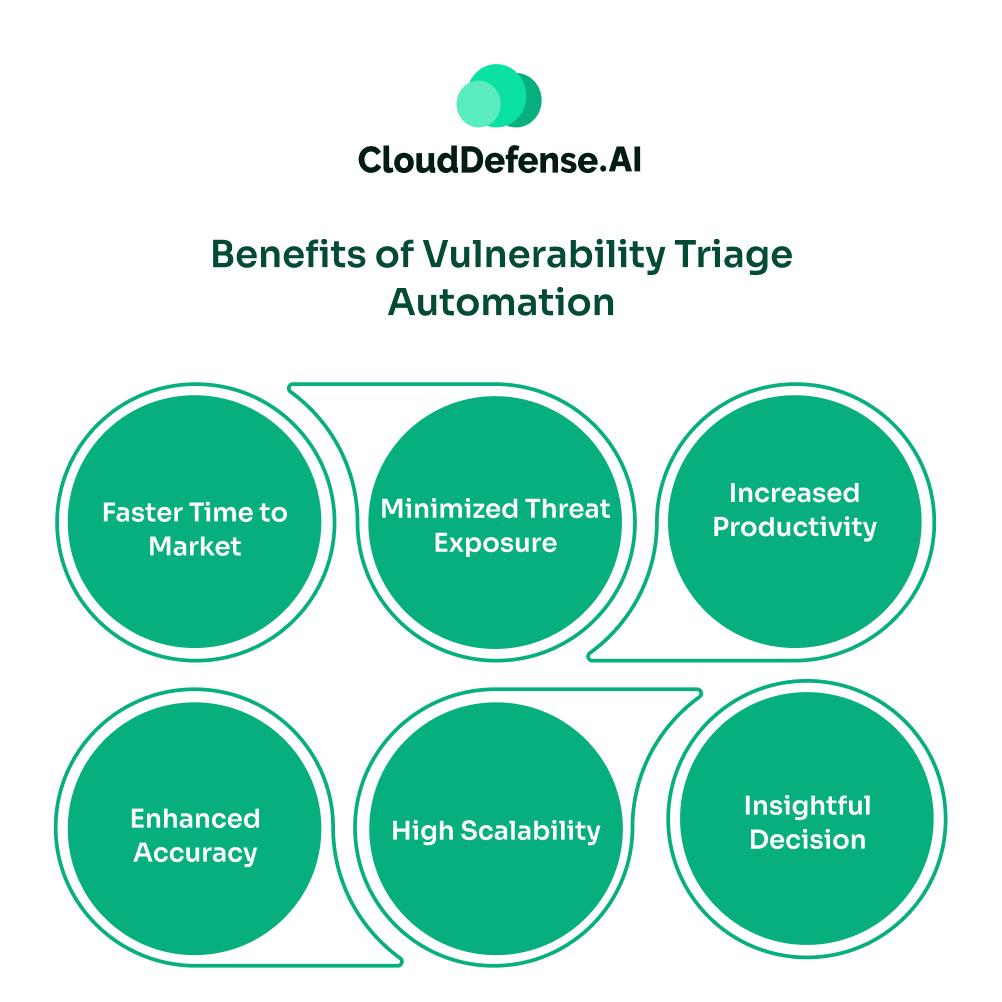
Integrating vulnerability triage automation benefits an organization in many ways:
- Faster Time to Market: Through intelligent prioritisation, teams can quickly identify critical vulnerabilities and remediate them. This enables the development team to build and deploy applications quickly in the market.
- Minimized Threat Exposure: With automated triage processes helping teams to address security threats in the beginning, the threat exposure is minimized by a large margin. All the issues are remediated quickly, lowering any risk.
- Increased Productivity: Due to smart classification of vulnerabilities, development teams can focus on actual threats. Whereas security teams can get rid of repetitive tasks and focus on application security strategies.
- Enhanced Accuracy: Automation in the vulnerability triage eliminates any bias and human error, ensuring high accuracy in vulnerability prioritisation. It also ensures the consistent implementation of AppSec policies on all the findings.
- High Scalability: Organizations can easily cope with an increasing number of security alerts from different IDEs and ensure that it doesn’t affect productivity. This process can easily handle a huge number of alerts from security tools.
- Insightful Decision: Intelligent correlation and analysis provide deep insights into different vulnerabilities and the overall security posture of the organization. It enables security professionals to make data-driven decisions for AppSec strategies.
Bottom Line
Vulnerability triage automation is a fundamental requirement for modern organizations to cope with the ever-evolving cybersecurity world. Organizations must work toward it to be included in the AppSec program and ensure an optimal security posture.
SAST tools like QINA Clarity from CloudDefense.AI can help in streamlining the security triage process. It is an intelligent AI-SAST tool that quickly scans for vulnerability and uses a 4-stage analysis process to provide prioritised results. It can be utilized in conjunction with automated vulnerability triage programs as it quickly prioritizes vulnerabilities and helps in quick remediation through guided steps. To see QINA Clarity in action, Book a free demo today.







