Explore the best solutions to ensure robust security for your cloud workloads.
Choosing the right cloud workload protection platform can take time and effort. Security for your cloud workloads is vital, and picking the best CWPP solution is key to protecting you from the range of cyber threats out there. But with lots of choices out there, it’s easy to get lost.
To avoid wasting money on the wrong tool, it’s important to look closely at what’s available. Let me simplify things for you as I simplify all the offerings available and find the CWPP solution that suits your needs best.
Based on my experience and thorough evaluation, I’ve picked out the top 10 best CWPP vendors for securing your cloud workloads in 2025.
- CloudDefense.AI
- AWS GuardDuty
- Orca Security
- SentinelOne Singularity Cloud
- Microsoft Defender for Cloud
- Check Point CloudGuard Workload Protection
- Prisma Cloud by Palo Alto
- Trend Micro Deep Security
- VMware Carbon Black Workload
- Illumio Core
Finding the right CWPP solution requires careful thought and understanding of your company’s needs. Let me make CWPP solutions easier to understand and help you find the best fit to protect your cloud infrastructure. Keep reading!
What to look for in CWPP Tools?
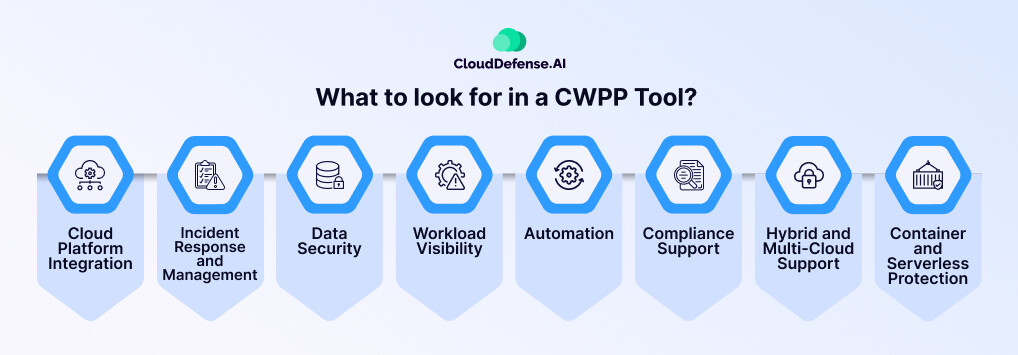
When considering a CWPP tool, there are several key factors to keep in mind to ensure you’re making the right choice for your organization’s security needs. Below I’ve laid down all the features that you need to keep in mind before zeroing down on a CWPP tool.
Cloud Platform Integration
Look for CWPP products that integrate with major cloud platforms like AWS, Azure, and Google Cloud Platform. This integration enhances visibility, administration, and security control across your cloud-deployed workloads.
Incident Response and Management
Prioritize CWPP solutions that offer incident response capabilities, including real-time alerting, threat intelligence integration, and incident management workflows. These features are crucial for swiftly detecting and mitigating security breaches.
Data Security
Make sure the CWPP tool has strong data security features like encryption, data loss prevention, and access controls. These features are essential for keeping your data safe from unauthorized access, leaks, and theft.
Workload Visibility
Having a clear view of your cloud workloads is important. The tool should show their setup, software inventory, network connections, and user permissions. This visibility helps you stay ahead by spotting any unusual activity or security risks early on.
Automation
Automating your security response can save you a lot of time. This helps prevent repetitive tasks such as vulnerability scanning and incident response. Automation accelerates security operations, reduces manual effort, and ensures consistent security across workloads.
Compliance Support
CWPP tools should help facilitate compliance with industry standards and regulatory requirements. Features like security configuration assessments, auditing, and reporting help ensure that your organization remains compliant with relevant regulations.
Hybrid and Multi-Cloud Support
As enterprise infrastructure evolves towards hybrid and multi-cloud architectures, ensure that the CWPP tool can protect various types of workloads across different cloud environments, including physical machines, VMs, containers, and serverless workloads.
Container and Serverless Protection
Confirm that the CWPP tool protects both containers and serverless workloads, with a clear roadmap for ongoing development in these areas.
10 Best CWPP Vendors in 2025
I understand the challenge of selecting the ideal security solution for your business. With numerous options available, it’s difficult to pinpoint the best one that fits your requirements.
Fortunately, I’ve simplified the process by curating a list of the top ten CWPP vendors in the market. These vendors offer the best solutions to secure your cloud workloads, with the key features I’ve mentioned previously.
If you’re short of time, we’ve also compiled a list comparing essential features, their ability to generate alerts, and whether they have machine learning capabilities. This comparison will help you make the best decision when choosing a CWPP vendor in 2025.
| Tool | Key Features | Alert Generation | Machine Learning |
|---|---|---|---|
| CloudDefense.AI |
|
Yes | Yes |
| AWS GuardDuty |
|
Yes | Yes |
| Orca Security |
|
Yes | Yes |
| SentinelOne Singularity Cloud |
|
Yes | Yes |
| Microsoft Defender for Cloud |
|
Yes | Yes |
| Check Point CloudGuard Workload Protection |
|
Yes | Yes |
| Prisma Cloud by Palo Alto |
|
Yes | Yes |
| Trend Micro Deep Security |
|
Yes | Yes |
| VMware Carbon Black Workload |
|
Yes | Yes |
| Illumio Core |
|
Yes | Yes |
CloudDefense.AI

CloudDefense.AI 
CloudDefense.AI emerges as a standout vendor, offering a top-notch CWPP solution packed with advanced features to protect your cloud infrastructure. This vendor has a proven track record of delivering cutting-edge solutions that exceed industry standards. CloudDefense.AI’s commitment to excellence and customer satisfaction ensures that you’re not just purchasing a product, but investing in a long-term partnership dedicated to your organization’s security needs. Here are all the features that have resulted in CloudDefense.AI topping this list of best CWPP.
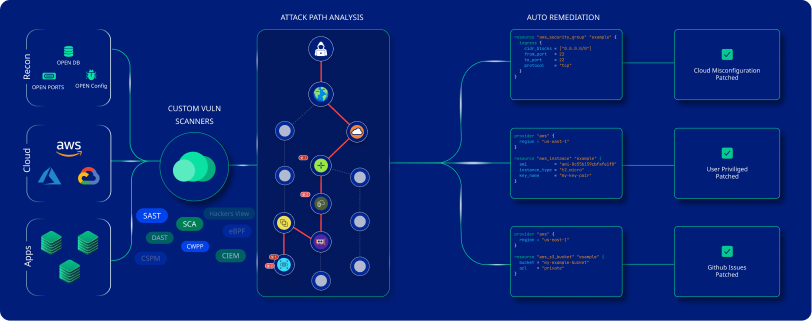
Features
All-in-one Protection Platform
CloudDefense.AI's CWPP provides complete security for hosts, containers, and serverless environments across multi-cloud and hybrid scenarios. With agentless architecture, it ensures total security without compromising the performance of your current digital infrastructure.
Rapid Risk Identification
The platform swiftly identifies critical cloud threats, including vulnerabilities, misconfigurations, malware files, and open ports, within minutes, enabling your team to mitigate all these risks.
Data Collection Beyond Limits
CloudDefense.AI goes beyond traditional data collection methods, gathering insights from your cloud setup and runtime storage to provide comprehensive risk assessment and vulnerability detection.
Compliance Management Support
Ensure regulatory and industry compliance effortlessly with CloudDefense.AI's CWPP. The platform integrates workload-specific intelligence with cloud configuration details, offering an all-inclusive security solution to make sure no ends are kept loose.
Pros

Unified protection with a single agent for Linux and Windows® hosts, containers, Kubernetes, and emerging technologies.

Automated enterprise-scale security measures reduce manual overhead and ensure strong defense across dynamic cloud-native environments.

CloudDefense.AI's CWPP secures all aspects of your cloud infrastructure, including hosts, containers, and serverless environments.

Easily scale your security measures to match your organization's growth and adapt to changing cloud environments.

Make compliance management easier by smoothly integrating workload-specific information and cloud configuration details.

Uses advanced methods like genetic signature identification and heuristic analysis to find and remove complex cyber threats.

Manage your cloud security from a single console, enhancing operational efficiency and simplifying security administration.
Cons

Advanced features may require additional training for optimal utilization.
Don’t just take our word for it. Book a demo and witness firsthand the power and simplicity of CloudDefense.AI.
AWS GuardDuty

AWS GuardDuty
AWS GuardDuty is a cloud security solution using machine learning to detect threats across AWS services. Integrating machine learning, anomaly detection, and network monitoring, it swiftly identifies threats from a range of sources like CloudTrail, VPC Flow Logs, and more, offering quick threat detection and alerting for remediation.
Pros

Integration with AWS resources for enhanced threat detection.

Detects a broad spectrum of threats, including malware, data breaches, and cloud misconfigurations.

A User-friendly interface allows easy policy management and remediation actions.

Cost-effective pricing model based on resource usage.
Cons

Reliance on other security detection systems for overall threat coverage.

Potential for false positives, requiring manual verification and remediation.

Limited to AWS-native environment, lacking support for multi-cloud or hybrid setups.
Orca Security

Orca Security
Orca Security stands out for its advanced cloud configuration capabilities, offering superior security, vulnerability management, and complete visibility across multiple cloud platforms. Its agentless approach and continuous monitoring ensure protection for cloud workloads, despite a learning curve and limited network layer visibility. With thorough vulnerability scans, advanced malware detection, and real-time data breach prevention, Orca Security provides actionable insights for efficient cloud security management.
Pros

Deep insight into cloud workloads, assets, configurations, and vulnerabilities for effective security management.

Agentless operation reduces deployment complexities and resource overhead, ensuring seamless integration with cloud environments.

Real-time threat identification and response minimize potential harm and downtime through continuous monitoring.
Cons

Limited network layer insights compared to network-based security technologies due to its agentless approach.

Requires advanced resources and training for optimal utilization, especially in configuring complex security policies.
SentinelOne Singularity Cloud

SentinelOne Singularity Cloud
SentinelOne Singularity Cloud is a leading CWPP tool known for its advanced automation capabilities, offering simplified runtime detection and response for cloud VMs, containers, and Kubernetes clusters. With AI-driven threat detection, adaptive security controls, and visibility, Singularity Cloud ensures maximum security and agility for cloud workloads.
Pros

AI-driven threat detection and behavioral analytics provide real-time protection against advanced threats.

Adaptive security controls dynamically adjust to security policies without compromising regulatory requirements.

Scalable performance ensures efficient and dependable protection as infrastructure expands across different cloud environments.
Cons

Requires advanced resources and training for optimal utilization, especially in configuring complex security policies.

Integration with existing cloud infrastructure may require careful planning and coordination, particularly for organizations with complex architectures.

Limited network layer insights compared to network-based security technologies due to their focus on runtime detection and response.
Microsoft Defender for Cloud

Microsoft Defender for Cloud
Microsoft Defender for Cloud stands out as the top choice for Azure integrations, offering advanced threat detection, vulnerability assessment, and dynamic security controls tailored for Azure workloads. With native Azure integration, real-time threat intelligence, and compliance monitoring, it provides powerful protection within the Azure ecosystem.
Pros

Dynamic security policies based on workload behavior reduce false positives and enable accurate threat response.

Compliance monitoring and reporting capabilities ensure adherence to industry regulations and standards.

Advanced machine learning and behavioral analytics block malicious activities, while continuous vulnerability scans highlight security weaknesses.
Cons

Limited coverage for non-Azure platforms may require additional security solutions for organizations with multi-cloud environments.

Implementation and configuration may require careful planning, particularly for complex cloud architectures.

Concentration on Azure may limit flexibility for organizations with diverse cloud infrastructures.
Check Point CloudGuard Workload Protection

Check Point CloudGuard Workload Protection
CloudGuard Workload Protection by Check Point offers fully automated and completely cloud-native security for unified visibility, compliance, and threat prevention across various cloud environments. With features like vulnerability monitoring, network security, and advanced threat intelligence, it provides protection for cloud workloads. It is fair to note that implementation may require training and expertise, and pricing could become costly over time.
Pros

Supports multiple cloud platforms, including AWS, Azure, Google Cloud Platform, and VMware.

Utilizes advanced threat intelligence and machine learning for quick detection and mitigation of threats.

Provides deep visibility into network traffic and integrates seamlessly with other Check Point security solutions for comprehensive security posture.
Cons

Implementation may require training and specialized resources to make use of its capabilities effectively.

Pricing increases annually and could potentially become expensive for enterprises.

Some users have reported experiencing a slow interface, which could impact user experience and efficiency.
Prisma Cloud by Palo Alto

Prisma Cloud by Palo Alto
Prisma Cloud by Palo Alto Networks is best known for its DevOps integration and container security features. While it excels in larger, complex environments, smaller organizations may find deployment more challenging. Nonetheless, its real-time compliance reporting, network and container security, and continuous vulnerability management make it a strong choice for enterprises seeking complete cloud workload protection.
Pros

Integrates seamlessly with DevOps pipelines for secure and compliant application development.

Provides complete cloud workload protection, including network security, container security, and data loss prevention.

Delivers real-time compliance evaluations and actionable insights for maintaining regulatory compliance.
Cons

Deployment and operation may be more complex for smaller organizations with simpler infrastructures.

Pricing starts at $9,000 annually per 100 Business Edition credits, potentially making it costly for smaller enterprises.

Extensive features may require additional resources and training for effective implementation and utilization.
Trend Micro Deep Security

Trend Micro Deep Security
Trend Micro Deep Security is ideal for hybrid cloud environments, offering security features and automated compliance processes. While implementation may be challenging for smaller setups, its deep protection, real-time threat intelligence, and centralized administration make it a compelling choice for enhanced cloud security.
Pros

Comprehensive security features provide complete protection against various threats.

Speedy upgrades and proactive defense against emerging threats use Trend Micro's extensive threat intelligence network.

Automated compliance management saves time and ensures adherence to regulatory requirements.
Cons

Integrating with existing cloud infrastructure may be resource-intensive, particularly for organizations with intricate cloud environments.

Some users may find the interface and deployment process challenging, particularly in smaller environments.
VMware Carbon Black Workload

VMware Carbon Black Workload
VMware Carbon Black Workload stands out as the top choice for virtualized environments, offering protection and integration with VMware ecosystems. Its resource-efficient design and real-time threat prevention make it ideal for dynamic workload demands, while its comprehensive security features ensure strong application control and protection for virtual machines.
Pros

Designed to be resource-efficient, minimizing impact on virtualized environment performance.

Integrates with VMware ecosystems, optimizing security operations and providing scalable protection.

Utilizes advanced analytics and behavioral analysis for real-time threat detection and proactive response.
Cons

May require initial familiarization and training to fully utilize advanced features.

The user interface differs from other CWPP vendors, potentially requiring additional training for users familiar with other platforms.

Implementation complexity may vary depending on the organization's virtualized environment and existing infrastructure.
Illumio Core

Illumio Core
Illumio Core excels in providing advanced micro-segmentation capabilities for enhanced cloud workload protection, offering granular security management and real-time threat detection. With seamless scalability and workload visibility, it’s ideal for dynamic environments. However, its sophisticated features may require advanced resources and training for optimal utilization, and integration with existing infrastructure could require additional configuration and coordination.
Pros

Detailed perspective of cloud workloads for easier visibility and effective security management.

Automatic adjustment of security policies as workloads change, ensuring continuous protection.

Fine-grained control over network traffic with micro-segmentation capabilities.
Cons

Sophisticated features may require advanced resources and training for optimal utilization.

Integration with existing infrastructure may require additional configuration and coordination.
What is Cloud Workload Protection?
Cloud Workload Protection, or CWP, involves constantly monitoring and eliminating threats from cloud workloads and containers. CWP is essential today as it protects against breaches in workloads, containers, and Kubernetes, empowering organizations to confidently and quickly build, run, and secure cloud apps.
Most importantly, CWP provides clear insight into workload and container events for quick detection and response, with automated security measures to stop suspicious activities. On top of that, it integrates with CI/CD workflows, ensuring secure workload management in line with DevOps speed, without sacrificing performance.
What is CWPP?
CWPP are companies providing solutions for Cloud Workload Protection Platforms. These platforms are advanced security tools crafted to protect cloud workloads across different environments. They offer features like workload monitoring, anomaly detection, vulnerability scanning, and incident response to counter security threats in cloud-based applications and infrastructure.
Conclusion
At this moment, keeping cloud workloads secure is of high priority for any organization in development. Using a CWPP tool is key to boosting your cloud security measures. With my experience in security tools, I know how crucial it is to pick the right CWPP for your organization. That’s why I’ve gathered the best CWPP vendors for you. But in the end, the choice is up to you to decide the best tool that suits your needs completely.
While doing so do ensure that you keep in mind all the key features that I have mentioned above to choose the best tool for yourself. By prioritizing cloud workload protection and selecting the best CWPP, you can ensure a secure cloud infrastructure for your company and mitigate potential risks effectively.







