Choosing the best DevSecOps tool is no easy task. With cyber threats becoming more sophisticated every day, companies need stronger security measures to protect what matters most. But with so many tools out there, it’s tough to figure out which one is right for your needs.
This guide is here to make that process easier. We’ll walk you through the top 10 best DevSecOps tools in 2025, helping you make an informed choice without the hassle.
What is DevSecOps?
DevSecOps is all about weaving security into every step of software development, from the very beginning to the final product. Instead of thinking about security as an afterthought, DevSecOps makes it a priority throughout the entire process whether you’re planning, coding, testing, or deploying software. The name itself breaks down into three parts: “Dev” for Development, “Sec” for Security, and “Ops” for Operations.
At its core, DevSecOps integrates security directly into the development workflow. Automation is a huge part of this, helping teams catch issues early by adding security checks and tests into the CI/CD pipeline.
What are DevSecOps Tools?
DevSecOps tools play a crucial role in integrating security into the development workflow. They help teams identify and fix security vulnerabilities throughout the software development process, not just at the end.
DevSecOps tools also automate various security tasks at every stage of the software lifecycle from coding and building to testing and deployment. By doing this, they allow development, security, and operations teams to work together more smoothly, helping to spot and fix vulnerabilities early on.
How to Choose the Best DevSecOps Tools?
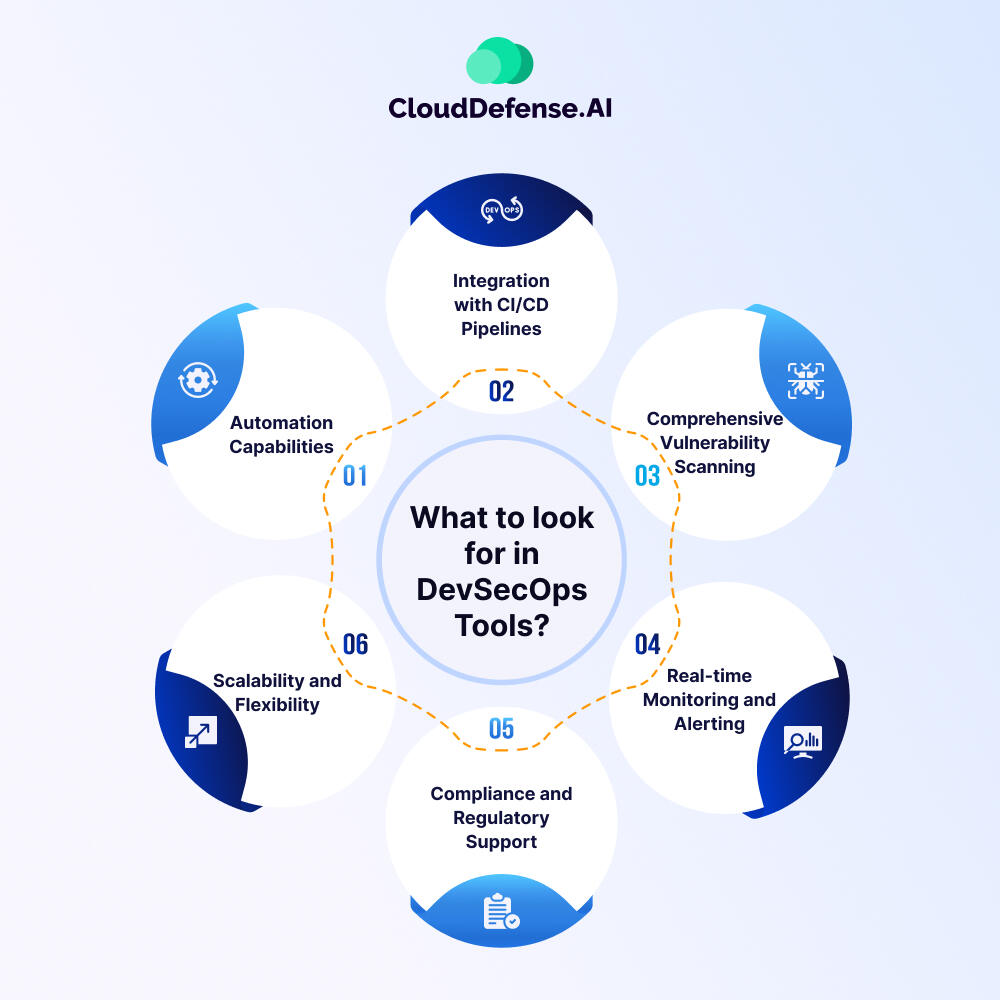
Before we head into exploring the best DevSecOps solutions, let’s explore six key factors that you need to consider when evaluating the tools. From automation capabilities to compliance support, understanding these criteria will empower you to make informed decisions and strengthen your organization’s security posture effectively.
Automation Capabilities
A great DevSecOps tool should make your life easier by automating tasks like code scanning, vulnerability assessments, and compliance checks. Automation speeds up your development process and ensures that security is applied consistently throughout. It also reduces the need for manual work, so your team can focus on more critical tasks.
Integration with CI/CD Pipelines
To really be effective, DevSecOps tools need to fit smoothly into your current workflows. Look for tools that easily integrate with your CI/CD pipelines, allowing security checks to happen at every stage, from the moment code is written to when it’s deployed. This way, security becomes a natural part of your development process.
Comprehensive Vulnerability Scanning
When it comes to application security, you want a tool that covers everything from source code to production. Look for one that offers Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Software Composition Analysis (SCA), and even container security scanning. A great option to consider is a CNAPP (Cloud-Native Application Protection Platform), which bundles all these features into one convenient platform. And if you're still unsure which tool to go with, no worries—the one at the top of our list happens to be a CNAPP!
Real-time Monitoring and Alerting
Security isn’t just about scanning—it’s also about staying alert. The best DevSecOps tools will offer real-time monitoring of your applications and infrastructure, with proactive alerts for potential threats. This way, you can respond quickly before a small issue turns into a big problem.
Compliance and Regulatory Support
If your business has to follow specific regulations like GDPR, HIPAA, or PCI-DSS, your DevSecOps tools need to have your back. Choose tools that come with built-in compliance checks and provide the documentation you need for audits, making it easier to stay in line with industry standards.
False Positive Management
False positives can be frustrating, slowing down development and creating unnecessary work. The right DevSecOps tool should have strong false-positive management features, helping your team avoid distractions and focus on actual security risks. Look for tools that allow you to fine-tune rules or exclude certain issues that aren’t real threats.
Auto Remediation
Speed is key in security, and auto-remediation features can help address vulnerabilities quickly. Some DevSecOps tools can automatically fix minor issues or suggest patches, giving your team more time to focus on complex problems. This proactive approach helps maintain security without bogging down the development process.
Scalability and Flexibility
As your organization grows, so should your tools. Make sure the tool you choose can scale with you, whether you’re a small team or a large enterprise. Flexibility is also key—tools that can adapt to your specific workflows and security needs will give you more control and save you from headaches down the road.
Top 5 Best DevSecOps Tools
Choosing the best DevSecOps vendors can feel overwhelming, especially with so many different vendors offering their services on the market.
This list simplifies your selection process, focusing on tools that align with key principles that have been mentioned above, ensuring technical compatibility without unnecessary complexity in 2025.
Here is a handy list for you to review quickly if you are short on time.
| Tools | Best For | Key Features |
| CloudDefense.AI |
|
|
| Check Point | DevSecOps |
|
| Snyk | DevSecOps |
|
| SonarQube | DevSecOps |
|
| Veracode | DevSecOps |
|
CloudDefense.AI (Best for Complete DevSecOps Solution)

CloudDefense.AI 
As a CNAPP, CloudDefense.AI offers all-in-one security solutions. It gives you comprehensive security features, including vulnerability scanning and remediation, in a single platform. This unified approach simplifies security management for companies, ensuring overall protection across their entire application landscape.
With CloudDefense.AI’s cutting-edge DevSecOps solution, you can transform your app development journey and redefine your workflow. Offering real-time code security and production-level vulnerability defense, CloudDefense.AI is the ultimate choice for securing your applications from start to finish.
Our Application Security Solutions Include:
- Static Application Security Testing (SAST)
- Dynamic Application Security Testing (DAST)
- Software Composition Analysis (SCA)
- API Security
- Container Vulnerability Management
- IaC Scanning
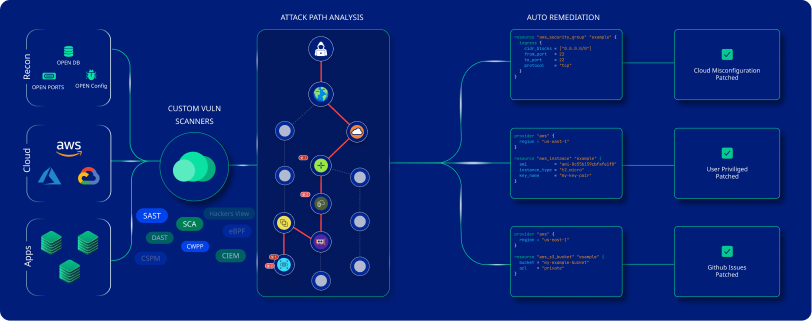
Key Features
Complete DevSecOps Coverage
CloudDefense.AI provides a complete solution for your DevSecOps posture, covering all layers of your application stack. From identifying and patching vulnerabilities in code, dependencies, containers, and infrastructure to ensuring continuous application security throughout your CI/CD pipeline, CloudDefense.AI has you covered.
Extensive Programming Language Support
Integrate CloudDefense.AI with your preferred languages, tools, and workflows for unmatched security throughout your development process.
Reporting and Analytics
CloudDefense.AI lets you stay in the loop with simple reporting and analytics features. They give you a clear picture of your security status so you can make smart choices about where to focus your efforts.
Prioritize Top Risks
We help you identify and prioritize the biggest risks facing your applications. This way, you can address the most critical issues first and improve your overall security posture.
Automated Remediation
CloudDefense.AI fully takes care of fixing vulnerabilities with automated, AI-driven remediation features. This helps lighten your team's workload, allowing them to spend more time on what they do best: creating amazing products.
Developer-Friendly Workflow
We know developers thrive in an environment that supports their creativity. CloudDefense.AI fits right into your existing workflow, making security a part of your process rather than a hurdle.
Reduced Noise
No more drowning in alerts! Our platform cuts through the clutter, so you only get the notifications that really matter. This way, you can concentrate on what’s important without unnecessary distractions.
What Sets Us Apart?
- Comprehensive DevSecOps coverage. One platform to cover all aspects of your cloud and application’s security.
- Best-in-class vulnerability database.
- Ensuring compliance throughout the development process.
- Easily integrates with your existing infrastructure.
- Generates detailed code analysis reports
- Customizable build policies
- 24/7 customer support.
- One-click and automated remediation.
- Vast language support.
- Smart remediation with AI-powered fixes
- Less false positives and unnecessary noise.
Don’t just take our word for it. Book a demo and witness firsthand the power and simplicity of CloudDefense.AI.
Check Point

Check Point
Check Point’s DevSecOps solutions are designed for enterprises looking to enhance their security posture while transitioning to the cloud. It stands out among DevSecOps tools by offering solid performance without sacrificing speed.
Key Features
Code Scanning
Automatically scans and analyzes code to identify potential issues, including bugs and security vulnerabilities.
Integration into CI/CD Pipeline
Supports automation by integrating security checks within your continuous integration and continuous delivery processes.
Intuitive Dashboard for Real-Time Insights
Provides a user-friendly interface that allows teams to monitor security metrics and gain actionable insights in real time.
Snyk

Snyk
Snyk focuses on identifying and fixing security vulnerabilities in open-source dependencies, making it a valuable tool for teams committed to maintaining secure software. Its continuous monitoring capabilities ensure that your dependencies remain protected over time.
Key Features
Broad language support
Compatible with various programming languages, allowing teams to secure their entire codebase regardless of the tech stack
Deep Integration with CI/CD Tools
Easily integrates into existing CI/CD pipelines, enabling seamless security checks throughout the development lifecycle.
Actionable Insights to Enable Developers
Provides developers with clear, actionable insights to address vulnerabilities effectively, developing a security-first mindset.
SonarQube

SonarQube
SonarQube is widely recognized for its focus on code quality, offering security-oriented plugins that assist in identifying vulnerabilities throughout the development process. Its continuous feedback mechanism is designed to help maintain high standards of code quality.
Key Features
Security-Focused Plugins
Offers a range of plugins specifically designed to identify security vulnerabilities, ensuring that security is integrated into the development lifecycle.
Continuous Feedback
Provides ongoing assessments of code quality, enabling developers to receive real-time feedback and make improvements as needed.
Code Quality
Helps teams uphold high standards of code quality, reducing technical debt and enhancing overall software reliability.
Veracode

Veracode
Veracode is a cloud-based application security platform that focuses on helping organizations identify and remediate security vulnerabilities in their applications. It is particularly beneficial for teams looking to integrate security into their software development lifecycle.
Key Features
Integrations Across the SDLC
Seamlessly connects with various applications and platforms within the SDLC, enhancing collaboration between development and security teams.
Unified Dashboard
Provides a unified dashboard for managing security policies, posture management, analytics, and compliance, simplifying oversight and reporting.
Detection of Code Bugs and Security Vulnerabilities
Identifies potential bugs and security risks early in the development process, enabling timely remediation.
Conclusion
The best DevSecOps tool is essential nowadays to ensure the security of your applications. Even minor vulnerabilities can attract cyber threats, and this is why we suggest getting a CNAPP for your company.
CloudDefense.AI, being a CNAPP, simplifies your overall security management. It offers complete security and integration with your existing infrastructure, making it the ideal choice for organizations seeking comprehensive protection. Therefore, investing in CloudDefense.AI is a smart move to enhance your cybersecurity defenses. Book a free demo now to test it out!
FAQ
1. What is DevSecOps?
DevSecOps is all about building security into the development process from the start. Instead of adding security at the end, it makes sure it’s part of every step, from planning to deployment.
2. What is DevSecOps vs DevOps?
DevOps focuses on automating and streamlining development and operations, while DevSecOps adds security into that process, embedding security checks and practices throughout the development lifecycle.
3. Is DevSecOps a tool?
No, DevSecOps is not a specific tool. It’s a methodology or approach, but there are various tools that help implement DevSecOps practices.







