When it comes to cybersecurity, vulnerability management is non-negotiable. As we progress towards becoming more digital, the scope of threats is only becoming more complex. Companies need tools that not only identify vulnerabilities but also allow for quick, efficient remediation.
However, we know figuring out which tool will be best for your organization in maintaining security and integrity can be a daunting task for you. But don’t worry. We’ve got your back! In this article, we are going to cover the best vulnerability management tools for 2025. Besides, we will also put forward the following information to help you make an informed decision:
What is Vulnerability Management?
Vulnerability management is the process of identifying, evaluating, treating, and reporting on security vulnerabilities in systems and software. It is a key part of an organization’s cybersecurity strategy, aimed at minimizing the risk posed by potential threats.
- Identifies vulnerabilities in your systems, applications, and networks.
- Assesses the severity of each vulnerability to prioritize response efforts.
- Recommends fixes and patches to address vulnerabilities.
- Monitors for new vulnerabilities and emerging threats.
- Tests implemented fixes to ensure they are effective.
- Reports on vulnerability status to keep everyone informed.
The goal is simple: reduce the risk of cyberattacks by addressing potential vulnerabilities before they can be exploited. Effective vulnerability management helps reduce exposure to cyberattacks and ensures that systems remain secure over time. By continuously identifying and addressing weaknesses, organizations can maintain a proactive security posture.
What are Vulnerability Management Tools?
Vulnerability management tools are software solutions designed to help businesses identify, track, and fix security weaknesses in their networks, systems, and applications. These tools scan your infrastructure for potential risks, providing detailed reports on what needs attention.
They also prioritize these vulnerabilities based on severity, helping security teams focus on what matters most. From automated patching to real-time monitoring, these tools are critical for maintaining security in an increasingly complex digital environment. Essentially, they’re your first line of defense against potential breaches.
Read more: Do you wish to learn more about vulnerability management? Read our exclusive article about Vulnerability Management. |
What to Look for in a Vulnerability Management Tool?
Shortlisting a vulnerability management tool is not an easy task, especially if you are using it for the first time. That is why we have created a list of factors that you need to look at while selecting a vulnerability management tool:
Continuous Monitoring
The vulnerability management tool you have selected must come with continuous monitoring to detect vulnerability whenever it appears. It needs to continuously look for issues and report them before it can make an impact.
Real-Time Alert
It is essential for the tool to offer real-time alerts whenever it detects any new vulnerability. The real-time alerts will enable the security team to assess the vulnerability and take necessary remediation steps.
Risk Scoring
Without proper classification and categorization, it can become a daunting task for security personnel to identify which security issue should be rectified first. When you are selecting a vulnerability management tool, it should come with risk scoring because it helps the team to remediate attacks based on their severity and reduce the attack surface.
Automation
Although all vulnerability management tools might not offer you, it is best to select a tool offering automated remediation. Leveraging automation allows the tool to automatically fix many common fixes and help the security team take corrective measures to prevent such issues from arising in the future.
Integration with SDLC
Integrating the tool into the development stage will largely benefit the organization. It will enable continuous vulnerability scanning and management throughout the development phase and prevent any vulnerability from getting deployed. The integration will also help your organization to maintain compliance with various regulatory standards.
Availability of Access Control
Having access control in your vulnerability management tool will help in reducing the chance of vulnerability. Access control will allow the security team to manage different users' levels of access and prevent the chance of unauthorized access or over-privileged access.
Visualization of the Attack Surface
Getting a complete overview of the attack surfaces in the cloud infrastructure is a boon to the security team. The availability of attack surface visualization streamlines the complete process of discovering the area of the attack surface. Besides, it also helps discover the assets that need to be protected when a vulnerability arises.
Customer Support
Always assess the customer support that the vulnerability management tool offers because it will help you solve any issue during implementation. Make sure they have a qualified technical team who will assist you in all types of issues.
Read more: Don’t leave your systems vulnerable! Read about the top misconfigurations that could put your organization at risk. |
10 Best Vulnerability Management Tools in 2025
Here are the ten best vulnerability management tools we have found out for you that will prevent vulnerabilities and improve your security posture with its standout features;
CloudDefense.AI

CloudDefense.AI 
Without a doubt, vulnerability management tools from CloudDefense.AI are among the top-tier choices in the industry and are widely preferred by numerous organizations. This leading tool does more than just scan, assess, and fix vulnerabilities.
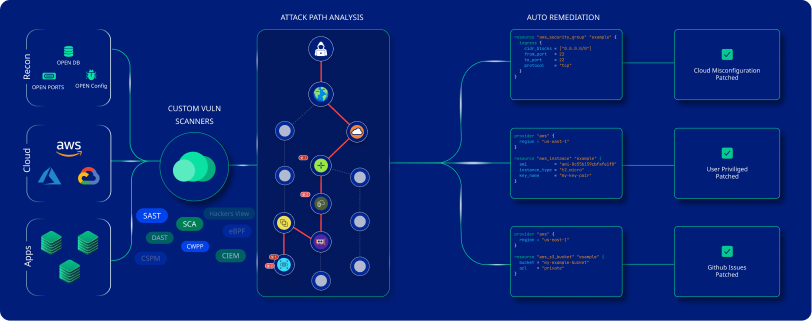
It leverages continuous agentless assessment and AI-powered remediation capability to deliver impeccable vulnerability management and help you stay ahead of the threat. It is loaded with advanced features like full inventory discovery, attack path analysis, real-time insight, and others to help you stay ahead of the threat.
Key Features:
Some top features that define CloudDefense.AI as a leading vulnerability management tool in the industry:
Detailed Inventory of Assets
CloudDefense.AI gives you a complete view of your cloud environment by making a detailed inventory of all your cloud assets, including libraries and packages. By making a full inventory, it ensures comprehensive coverage for discovering vulnerabilities across multi-cloud environments.
Context-Driven Prioritization
One of the defining features of this tool is context-driven prioritization, where it evaluates all the context of your cloud assets before prioritization. It enables your team to target vulnerabilities that will make the maximum impact.
Attack Path Analysis and Visual Graph
This tool is known for leveraging attack path analysis that helps you to identify and prioritize interconnectivity vulnerabilities and assign impact scores.
In addition, it also makes use of the visual graph, which provides the team with a visual representation of the attack path. Thus providing them an insight into cloud entities associated with it for a complete understanding of the vulnerability.
Comprehensive Asset Visibility
This vulnerability management tool from CloudDefense.AI provides complete asset visibility along with workloads and identities. This complete visibility enables the team to identify and gauge the impact of potential CVEs.
Real-Time CVE Insight
CloudDefense.AI keeps you updated regarding trending and impactful CVEs through its "From the News" widget. Plus, it also provides an analysis of the presence of those CVEs in your cloud environment and how it can impact your business.
CI/CD Integration and Automated Detection
It can seamlessly integrate into your CI/CD pipeline to identify and mitigate vulnerabilities before they reach production. It scans your VM and container images and ensures your application is completely free of security issues. CloudDefense.AI automates the scanning process to proactively detect and eliminate threats.
Compliance Management
This vulnerability management tool ensures effective compliance management by aligning with the requirement of vital security standards like ISO 27001, SOC II, GDPR, CSA, etc. It optimizes the complete compliance workflow to ensure continuous adherence.
Pros

Utilizes agentless vulnerability management approach to protect your cloud environment from vulnerabilities.

It prioritizes vulnerabilities according to the context.

It helps in understanding new CVEs and how they can impact your multi-cloud environment.

Automates the scanning process to identify and prevent vulnerability from reaching the production stage.
Cons

Employees require a deep knowledge of vulnerability management to utilize its advanced features fully.
What Sets Us Apart From Others?
CloudDefense.AI offers some exclusive features that make this vulnerability management tool stand out from the crowd. These features are:
Rapid Response To Critical Threats
CloudDefense.AI can rapidly respond to critical threats like Log4Shell by enabling the security team to identify vulnerable assets and patch them. It collects data from various vulnerability sources to accurately identify threats.
New CVE Insights
One of the defining features of CloudDefense.AI is real-time insight regarding new CVEs and providing details regarding how they can affect your environment.
Advanced Query Builder
This tool's advanced query builder is highly effective. With it, you can easily query the entire environment and gain insight into vulnerability, risk levels, and other aspects.
Rapid7 InsightVM

Rapid7 InsightVM
When it comes to getting the best vulnerability management tool, Rapid7 InsightVM is one of the best tools that is recommended by many.
It is loaded with many advanced features that let enterprises of all sizes stay ahead of vulnerabilities. Through automation and advanced vulnerability management analytics, this tool can prioritize risks and remediate them.
Key Features:
Rapid7 InsightVM provides complete visibility into your cloud environment and endpoints and prioritizes risks based on their severity.
Automated remediation and tracking of progress help the team to speed up the fixing process.
Leverages intelligent insights from Rapid7 Labs for identifying exposed assets and classifying vulnerabilities accordingly.
It offers a lightweight and universal Insight Agent that collects data from various sources to provide you with real-time updates regarding network and user risk.
Qualys

Qualys
Qualys is a top vulnerability management tool designed for organizations with complex environments. It is widely known for its continuous monitoring, compliance support, and web application firewall features. Powered by the Enterprise TruRisk platform, it provides your team with a comprehensive view of your security posture to eliminate risk efficiently.
Key Features:
Speeds up the detection of high-impact vulnerabilities and reduces the overall mean time to remediation by almost 4 hours.
It swifts up the remediation process by almost 60% by automating the patching process without any code flow.
Offers complete visibility across your cloud environment, IT, OT, and IoT assets and helps you gain insight into your organization’s security posture.
It automates the continuous process of identifying and categorizing all the assets, including unknown and internet-faced assets.
Tenable Nessus

Tenable Nessus
When it comes to getting a trusted and one of the best vulnerability management tools, Tenable Nessus is one platform that many select. It is more than just a regular management tool for your assets, as it also safeguards your web application and provides visibility into cloud infrastructure.
Key Features:
Tenable Nessus implements automated scanning into your cloud infrastructure and application to discover and fix vulnerabilities.
Integrates into SDLC to discover vulnerabilities in your software development lifecycle and eliminate them before the application reaches the deployment stage.
Provides Live Result that automatically performs a vulnerability assessment with every update and highlights the area of possible vulnerabilities based on scan history.
Comes with 450 pre-configured templates to help in discovering the area of vulnerabilities.
It allows easy auditing of compliance status by tallying it against CIS benchmarks and various best practices.
Orca Security

Orca Security
Orca Security has emerged as one of the leading vulnerability management tools that can identify and fix vulnerabilities without the involvement of any agent. From AWS and Azure to Google Platform, this tool works well with all the top cloud platforms and gathers actionable data for security teams.
Key Features:
Leverages more than 20 vulnerability data sources and a complete inventory of your cloud environment to discover vulnerabilities.
It offers SideScanning technology that helps users in overcoming traditional issues of agent-first cloud security and vulnerability scanning.
The attack path analysis allows the tool to identify interconnected vulnerabilities that can expose valuable assets and score them according to impact.
The "From the News" widget offers automatic updates of new trending and impactful CVEs, and based on that, it analyzes your environment for its presence.
Holm Security

Holm Security
The next-generation vulnerability management tool that you can take into account is Holm Security. It is a cutting-edge platform that uses threat intelligence services and attack surface management to secure your cloud environment and minimize attack surfaces. Being an advanced tool, it offers you all standard features along with API scanning and phishing training.
Key Features:
Continuously monitor your cloud environment along with assets to identify vulnerabilities and help in remediating those issues.
It offers better control with System and network scanning that covers every aspect of your infrastructure, including network devices, to manage complex vulnerabilities.
It efficiently reduces attack surfaces by discovering a large variety of vulnerabilities through web apps and API scanning.
Implements role-based access control, which gives you the option to manage the team's access to web applications and other data.
Intruder

Intruder
You can take Intruder into consideration if you are looking for a vulnerability management tool that caters to SMBs to protect their cloud estate from vulnerabilities. Trusted by many top brands, this tool utilizes an online vulnerability scanner and proactive threat response to safeguard the business from vulnerabilities.
Key Features:
Intruder continuously scans your cloud environment and network to eliminate vulnerabilities affecting the security posture.
Combines threat response, continuous network monitoring, and automated vulnerability scanning in one platform to provide a complete view of the attack surface.
It helps in creating audit-ready reports to enable auditors and stakeholders to gain insight into your security posture and compliance statutes.
Integrates with CI/CD pipeline to introduce security in the development stage and provide actionable results based on context.
Acunetix

Acunetix
Another top vulnerability management tool in this list is Acunetix, and it automatically scans your website, application, and infrastructure for vulnerabilities. With proof of exploit, it eliminates false positives and helps the security team to achieve high accuracy. It is a one-of-a-kind vulnerability management tool that comes with 3000 checks for scanning.
Key Features:
Option to automate and schedule vulnerability scans to minimize the attack surface.
Integrates with your CI/CD, WAF and issues to make it easier for developers to identify and fix vulnerabilities and also assist in writing secure codes.
Acunetix stays up to date with the latest and trending vulnerabilities and has the capability to detect over 7000 vulnerabilities with high accuracy.
Thoroughly scans multiple cloud environments at the same time. The scanning coverage can be improved by integrating DAST and IAST scanning.
Digital Defense

Digital Defense
Undoubtedly, Digital Defense is an easy-to-use vulnerability management tool that enables small to medium-sized businesses to identify and manage vulnerabilities.
By using proprietary scanning technology, it helps in comprehensive vulnerability assessment and risk prioritization. This frontline VM tool is more than just a scanner and takes a proactive approach to maintaining a security posture.
Key Features:
Discovers all the assets and automatically labels them for easy filtration during a vulnerability assessment.
Provides the option to create patch management and asset-specific vulnerability reports.
Scans the entire cloud environment, including networks, to identify internal and external vulnerabilities.
Helps in staying compliant to industry standards and regulations.
Tripwire

Tripwire
Last but not least, we would also like you to consider Tripwire, which has emerged as a powerful vulnerability management tool. It is one of those tools that covers every aspect of your cloud environment, including assets, devices, and applications. Whether on-premises or cloud infrastructure, Tripwire can encompass every platform wherever it is implemented.
Key Features:
Provides a holistic view of your vulnerability profile spanning from cloud environment, on-prem, and network to IT and OT.
Leverages leading prioritized scoring technology to help security teams focus on vulnerabilities that have mattered the most.
Performs continuous monitoring and detection for vulnerability with both agentless and agent-based monitoring capabilities.
Offers the support of trained experts and hands-on tool management to steer through compliance issues.
Best Vulnerability Management Solution Comparison
Now, we want you to take a look at the brief comparison table of all the vulnerability management tools we have added:
| Continuous Scanning | Comprehensive Asset Visibility | Risk Scoring | Automation | Pricing |
CloudDefense.AI | Available | Available | Available | Available | The pricing is available on quote request. |
Rapid7 InsightVM | Available | Available | Available | Available | Minimum $2.19 per asset per month. |
Qualys | Available | Available | Available | Available | The pricing is available on quote request. |
Tenable Nessus | Limited | Available | Available | Available | The basic plan starts from $3590 per year. |
Orca Security | Available | Available | Available | Available | The pricing is offered after you apply for a demo. |
Holm Security | Available | Available | Limited. | Available | The pricing is available on the quote request |
Intruder | Available | Limited | Available | Available | The pricing is available after consultation. |
Acunetix | Available | Available | Limited | Available | The pricing is available on quote request. |
Digital Defense | Available | Available | Available | Limited | The pricing is available on the quote request |
Tripwire | Available | Available | Available | Limited | The pricing is available after you book a demo. |
How to Choose the Best Vulnerability Management Tool?
When considering the best vulnerability management tool that will safeguard your cloud environment from vulnerabilities, you will have to be careful with your choice. To guide you in this process, we have highlighted some factors that you need to consider:
User Interface
The vulnerability management tool you are about to choose must have an intuitive and simple interface. It must be easy to navigate so that every user can confidently utilize the features.
Core Features
It is important for a vulnerability management tool to include continuous monitoring, automation, risk scoring, asset visibility, and reporting capabilities. Having these core features will enable the tool to efficiently reduce the attack surface. It would be best if it could provide RBAC and risk exceptions.
Integration
Make sure the tool you are about to choose integrates with your CI/CD pipeline, SDLC, and other security tools without jeopardizing productivity.
Customer Support
The customer support offered by the vendor is an important aspect, and they must provide a dedicated technical team to provide you with complete assistance. Dedicated support will maximize the potential and productivity.
Pricing
The best vulnerability management tool must be effective and value for money, and you should evaluate this factor while choosing.
Conclusion
Every year, thousands of new vulnerabilities are discovered, and this is expected to increase with the evolution of cloud technology. Having the best vulnerability management tool for your organization will help in safeguarding your cloud environment and prevent severe financial loss.
Through this article, we have covered the top 10 vulnerability management tools that can assist your organization to reduce attack surface and attain optimum security posture.







