Securing your company’s digital assets and sensitive data can become challenging when misconfigurations arise in its cloud infrastructure. But you don’t need to worry, as Cloud Security Posture Management (CSPM) tools can be a life-changing solution to reduce your cloud security woes.
The best CSPM tool can help you ensure that your cloud infrastructure adheres to industry best practices, helping you identify and resolve misconfigurations and minimize vulnerabilities and business risks. However, the market is filled with CSPM tools and finding the right one can be challenging for a starter.
To help you make an informed decision, we’ve compiled a list of the 10 best CSPM vendors, each offering tools that have unique features to strengthen your cloud security in 2025.
- CloudDefense.AI CSPM
- CloudGuard by Check Point
- Lacework Polygraph Data Platform
- CrowdStrike Falcon Cloud Security
- Cyscale
- Orca Security
- Tenable Cloud Security
- Zscaler Posture Control
- Singularity Cloud Security by Sentinel One
- Wiz CSPM by Wiz
Before we compare the tools, let’s first learn what you should look for in the best CSPM solution.
What to Look For in a CSPM Solution?
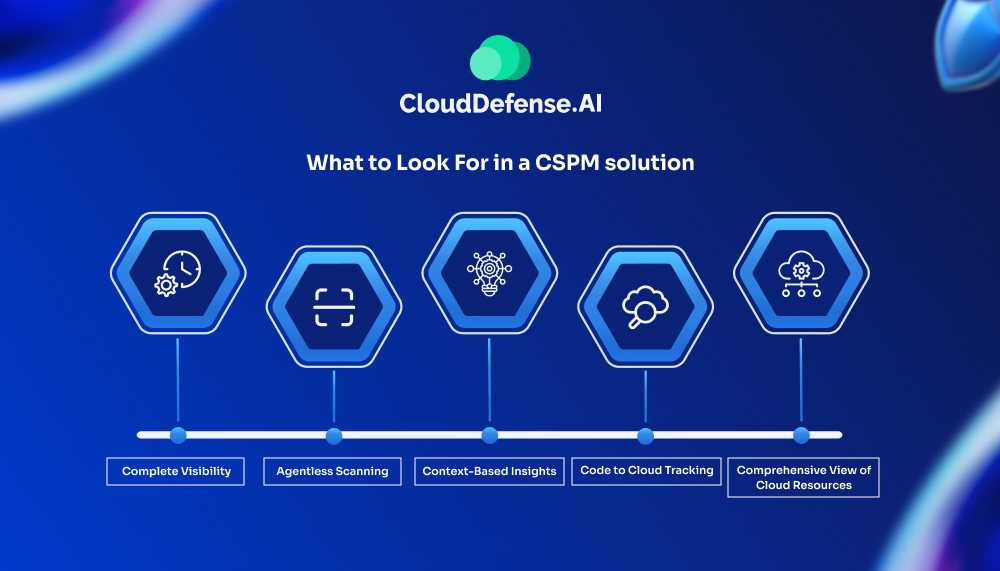
Most organizations now rely on CSPM tools, and selecting the right CSPM solution is important to ensure the optimum security for your cloud infrastructure. Here are some key capabilities you should look for in the best CSPM tools:
Complete Visibility
Complete visibility in a CSPM solution gives organizations continuous insight into their security posture. It allows for uninterrupted monitoring and mitigation of security threats in real-time. Lightweight agents help identify risks that agentless solutions may overlook, providing an extra layer of protection.
Agentless Scanning
Agentless scanning enables CSPM solutions to quickly assess workloads by taking snapshots for comprehensive risk analysis. This approach provides instant visibility into potential vulnerabilities across hybrid and multi-cloud environments, helping organizations detect and mitigate security risks without deploying agents.
Context-Based Insights
Context-Based Insights prioritize risks by evaluating their potential impact. This feature helps organizations understand which issues require immediate remediation and how they affect the cloud environment, enabling informed decision-making and more efficient threat mitigation based on severity.
Code to Cloud Tracking
Code-to-cloud tracking connects cloud workloads to their underlying code, identifying security issues at the source. This feature helps developers quickly discover the root cause of vulnerabilities and implement immediate, automated remediation, improving overall cloud security.
Comprehensive View of Cloud Resources
A CSPM solution should offer a centralized view of all cloud resources, like containers and workloads, across multiple environments. This unified inventory helps track resources, identify unauthorized assets, compliance monitoring which in turn helps in threat detection and remediation recommendation
Since now you are equipped with all the knowledge you need on the features that your ideal CSPM tool should have, let’s move on to the star section of this blog—the top 10 best CSPM tools in the market in 2025!
10 Best CSPM Tools in 2025
With so many CSPM tools flooding the market, finding the perfect fit for your business can feel like searching for a needle in a haystack. But don’t worry—we’ve done the heavy lifting for you!
We’ve curated a list of the best CSPM tools of 2025, each designed to swiftly uncover security risks and effectively mitigate them, so you can focus on what matters most—growing your business with a secured cloud infrastructure.
1. CloudDefense.AI CSPM

CloudDefense.AI 
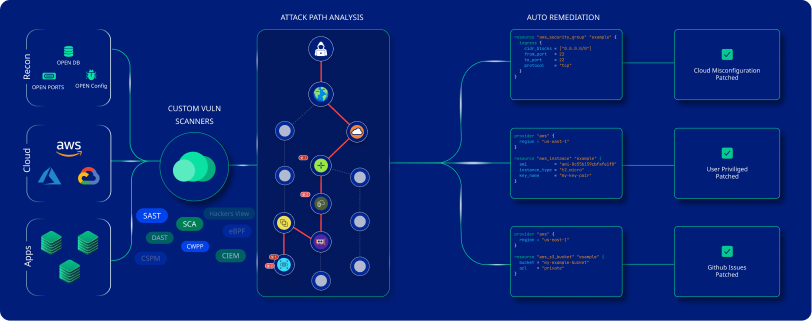
World’s Top CNAPP that Secures from Hacker Recon to Cloud to Your Code
CloudDefense.AI’s top-tier CSPM solution is the perfect choice for organizations operating in multi-cloud and semi-on-prem environments seeking complete protection. It excels in threat detection, compliance monitoring, and enforcing custom policies while using AI-powered remediation to protect against a wide range of misconfigurations and threats.
As a leading CSPM vendor, CloudDefense.AI offers complete visibility into your security posture and supports your compliance efforts. Its all-in-one approach, featuring real-time anomaly detection and automated remediation, is rapidly becoming a preferred tool for companies looking to strengthen their cloud security.
Features
Here are some key features that make CloudDefense.AI stand out among other CSPM tools:
Advanced Misconfiguration Detection
CloudDefense.AI continuously monitors your cloud environment to identify misconfigurations that could lead to security vulnerabilities. It uses AI-powered algorithms to detect a wide range of issues, from insecure storage buckets to overly permissive identity and access management (IAM) policies.
Automated Remediation
Once misconfigurations are detected, CloudDefense.AI offers automated remediation. It can automatically apply fixes as well as provide step-by-step guidance for manual resolution, reducing the time it takes to address potential threats and minimizing human error.
Detailed Alerts and Insights
With CloudDefense.AI, you receive real-time alerts on misconfigurations, allowing for immediate action. The platform provides contextual insights and detailed reports, helping you understand the severity of each issue and the best approach for remediation.
Customizable Policies
CloudDefense.AI allows you to define and enforce custom security policies customized to your organization’s specific needs. This ensures that any misconfiguration is flagged according to your unique security standards, offering a more solid and effective security posture.
Code to Cloud Security
CloudDefense.AI provides code-to-cloud security by tracking misconfigurations throughout the entire development lifecycle. It maps security gaps directly to the codebase, enabling developers to pinpoint and remediate vulnerabilities early in the process before they can impact the production environment.
Risk-Based Prioritization
CloudDefense.AI prioritizes misconfigurations based on risk, focusing on those that pose the greatest threat to your infrastructure. This ensures that your security team addresses the most critical issues first, optimizing the remediation process and enhancing cloud security through and thorugh.
Compliance-Driven Remediation
CloudDefense.AI maps misconfigurations against compliance frameworks like HIPAA, GDPR, and PCI DSS. It also offers custom-compliance-driven remediation suggestions to ensure that your cloud environment not only stays secure but also meets all regulatory requirements.
Continuous Monitoring and Validation
After remediation, CloudDefense.AI continues to monitor your cloud environment to validate the effectiveness of the applied fixes. This continuous cycle of detection, remediation, and validation ensures that your cloud environment remains secure over time.
Pros

AI-based remediation techniques address threats without human intervention.

Hassle free compliance assessments.

Accurate real-time threat detection.

It can integrate with most tools and is compatible with different cloud platforms.
Cons

Some advanced features can be difficult to utilize at first.
2. CloudGuard by Check Point

CloudGuard
2nd Easiest To Use in Cloud Security Posture Management(CSPM) Software
CloudGuard by CheckPoint is a well-known CSPM tool from the leading cybersecurity brand that automates security monitoring across your multi-cloud assets and services. It serves as an all-in-one solution that fully automates governance and compliance with comprehensive visibility and the option to customize policies.
Key Features:
CloudGuard provides a simple dashboard that helps you onboard new clouds and manage security posture across cloud platforms.
It gives you granular visibility into your assets, security groups, and networks to help you develop effective posture management.
Conforming to regulatory requirements and managing compliance posture is easy with this tool. It can run assessments for around 2400 security rulesets and 50 compliance frameworks.
CloudGuard has implemented threat intelligence through its platform and helps you gain account activity insight to identify anomalies.
Pros

CloudGuard is suitable for businesses of all sizes.

Provides a granular visibility into all the cloud assets to identify misconfiguration.

The user interface is completely user-friendly and intuitive.
Cons

It has some functionality issues in a complex environment.
3. Lacework Polygraph Data Platform

Lacework
3rd Easiest To Use in Cloud Security Posture Management(CSPM) Software
Lacework is one of the leading platforms that offer an efficient CSPM solution to strengthen your defense against all types of threats. It makes cloud security posture management a simpler task by allowing you to mitigate misconfiguration and meet compliance needs.
Key Features:
It discovers, monitors, and inventories all your cloud assets and captures all the inventory daily to keep track of changes.
This tool automatically monitors and identifies malicious activity and misconfigurations while allowing you to create custom policies to support assessment.
Get quick alerts when a security issue appears and prioritize them according to the severity.
It utilizes attack path analysis and remediation processes along with tools like Slack and Jira to fix misconfigurations and other issues quickly.
Pros

It offers a complete AI-driven security management.

Make use of attack path analysis to remediate misconfigurations.

It can correlate misconfigurations with malicious activities.

Completely customized platform.
Cons

It has poor third party integration.

Doesn’t offer auto-remediation.
4. CrowdStrike Falcon Cloud Security

CrowdStrike
4th Easiest To Use in Cloud Security Posture Management(CSPM) Software
With CrowdStrike cloud security posture management, you will not only ensure complete security enforcement but also gain visibility and compliance across your cloud environment. It serves as a unified platform through which you can gain comprehensive visibility of the security posture and manage compliance.
Key Features:
Crowdstrike, through continuous agentless monitoring, provides visibility into all the cloud assets and provides contextual insight into the overall security posture.
It comes equipped with real-time threat intelligence on hundreds of advisory groups and enables the team to respond to threats quickly.
Manage and remediate attacks and misconfigurations across your hybrid cloud.
This platform utilizes an attack path and identity analyzer to secure your IAM and AzureAD users from identity-based attacks.
It enables your team to reconfigure all the unprotected cloud resources through its one-click reconfiguration capability.
Pros

Provides targeted threat detection to reduce alert fatigue.

Automatically fix misconfigurations.

Gives you a complete insight into cloud analytics and security infrastructure.
Cons

The overall analytical performance could be improved.
5. Cyscale

Cyscale
5th Easiest To Use in Cloud Security Posture Management(CSPM) Software
When you are looking for a contextual cloud security posture management tool, one name that everyone will recommend is Cyscale. With an easy-to-understand dashboard, simple interface, and support for AWS, GCP, and Azure, it has become a suitable tool for businesses from different industries.
Key Features:
Cyscale offers continuous and automated misconfiguration detection using graph technology across your multi and hybrid cloud environment.
It is loaded with hundreds of inbuilt security policies and controls to prevent known security threats.
It enables you to inventory, map, and set security scores for all your cloud assets.
Cyscale uses cloud asset inventory and integrates with different platforms to provide visibility into your cloud resources.
It offers continuous compliance monitoring for various industry standards and regulations and streamlines your audit process.
Pros

Security scores allow the team to prioritize attacks.

Implements automations for identifying and mitigating misconfiguration.

Blends with all types of cloud providers.
Cons

It doesn’t offer an on-premises version.

Not suitable small-sized businesses.
6. Orca Security

Orca Security
6th Easiest To Use in Cloud Security Posture Management(CSPM) Software
Another leading CSPM tool that you should take into consideration is Orca Security. This tool is known for continuously monitoring the security posture of your cloud environment and automatically remediating issues when detected. It consolidates all the workloads, sensitive data workload, container security, and other aspects in one platform.
Key Features:
It scans your entire workload and identities to discover threats and prioritize attack paths to help your team focus on possible threats.
Orca unifies compliance and ensures all the cloud resources comply with the specific regulatory framework and industry benchmark.
Through this platform, you can create your own powerful query to investigate any kind of security and set up a remediation process.
It offers a Security Score that allows the security team to understand and respond to risks that require immediate remediation to fortify the overall security posture.
Pros

Offers the option of performing custom queries.

It provides quick reports and alerts regarding misconfigurations.

Ensures continuous compliance support.

It can detect threats based on their attack path.
Cons

The UI is not user-friendly.
7. Tenable Cloud Security

Tenable
7th Easiest To Use in Cloud Security Posture Management(CSPM) Software
If you are looking for a CSPM tool that also offers effective privileged access management, Tenable won’t disappoint you. It delivers optimum protection by accurately detecting and remediating all the configurations and permission risks. It is a one-of-a-kind CSPM tool that combines PAM and just-in-time access management capability to minimize any risk.
Key Features:
It offers a unified view of your cloud environment and helps your team identify risks with ease.
This CSPM tool implements full-stack risk analysis to your cloud configuration and automates remediation of misconfigurations, risky privileges, and policy violations.
It automates compliance and reports and enables the team to identify compliance violations at an early stage.
By using continuous risk analysis, it offers automated threat detection to help in identifying suspicious behavior that affects cloud assets.
Pros

Provides a comprehensive view into your cloud environment.

Automates compliance to quickly identify compliance violations.

It supports all the major cloud providers.
Cons

It is not budget friendly.
8. Zscaler Posture Control

Zscaler
8th Easiest To Use in Cloud Security Posture Management(CSPM) Software
The Zscaler CSPM tool is one of the leading choices when it comes to securing your cloud assets, mitigating lateral movement risk, and governing the workload across your multi-cloud environment. Through its unified platform, you can identify and remediate issues to improve the security and compliance posture.
Key Features:
Enables you to gain complete visibility of all the assets across your multi-cloud environment and also control them.
It uses malware analysis, threat detection, and cloud-based proxy to strengthen your cloud security.
This CSPM tool integrates with Jira, Splunk, ServiceNow, etc., to prioritize alerts for security issues automatically in real-time.
It automatically compares configurations against best practices, compliance framework, and pre-built policies for compliance assurance.
Pros

It can detect lateral movement in the network.

Ensures compliance by fixing misconfigurations.

Offers a continuous monitoring of all the workloads.
Cons

The overall setup process takes a lot of time.
9. Singularity Cloud Security by Sentinel One

Singularity
9th Easiest To Use in Cloud Security Posture Management(CSPM) Software
PingSafe, recently acquired by Sentinel One, implements numerous measures to improve your cloud posture. It adopts offensive security practices and discovers issues throughout. What makes it stand out? The continuous compliance monitoring for leading industry frameworks and standards.
Key Features:
Offers comprehensive visibility through a single pane of glass into all your cloud estate.
It is equipped with agentless vulnerability management and real-time secret scanning capability.
PingSafe helps your team focus on critical vulnerabilities through an Offensive Security Engine and eliminate false vulnerabilities.
Automates the monitoring process to detect and rectify misconfiguration across the cloud environment.
Pros

Extremely easy to deploy.

It offers an agentless platform for vulnerability assessment.

Integrates with Jira, Slack and other necessary tools.

Impressive customer service throughout subscription.
Cons

You won’t get any upfront pricing.

Doesn’t offer much advanced features.
10. Wiz

WIZ
10th Easiest To Use in Cloud Security Posture Management(CSPM) Software
Deploy contextual CSPM across your cloud using the platform of Wiz to continuously monitor and remediate misconfigurations. This CSPM tool seamlessly integrates with your cloud environment and helps you get complete visibility.
Key Features:
Wiz implements 1400+ cloud misconfigurations, IaC scanning, and continuous CIS to protect your cloud environment from threats.
It leverages Wiz Security Graph to contextualize your misconfiguration and reduce overall alert fatigue by a large margin.
It helps you enforce custom policies and frameworks across your cloud environments and IaC codes.
It can detect misconfigurations in real-time and implement automatic rectification of the issue.
Pros

It utilized specialized technology to lower the fatigue.

Provides automated remediation facility.

You will get 24/7 customer support.
Cons

It can be difficult to use for first timers.
Top 10 Best CSPM Solutions Comparison
Each CSPM solution comes with its respective capabilities, which makes them different from each other. To help you understand between all the top CSPM solutions, we have created the following comparison:
CSPM Tools | Attack Path Analysis | Risk Scoring | AI Remediation | Key Features |
Yes | Yes | Yes |
| |
CloudGuard by Checkpoint | No | Yes | Yes |
|
Lacework Polygraph Data Platform | Yes | No | Yes |
|
CrowdStrike Falcon Cloud Security | No | No | Yes |
|
Cyscale | No | No | Yes |
|
Orca Security | No | No | Yes |
|
Tenable Cloud Security | Yes | No | Yes |
|
Zscaler Posture Control | No | No | Yes |
|
Singularity Cloud Security by Sentinel One | No | Yes | Yes |
|
Wiz CSPM by Wiz | Yes | No | Yes |
|
How to Choose the Best CSPM Tool?
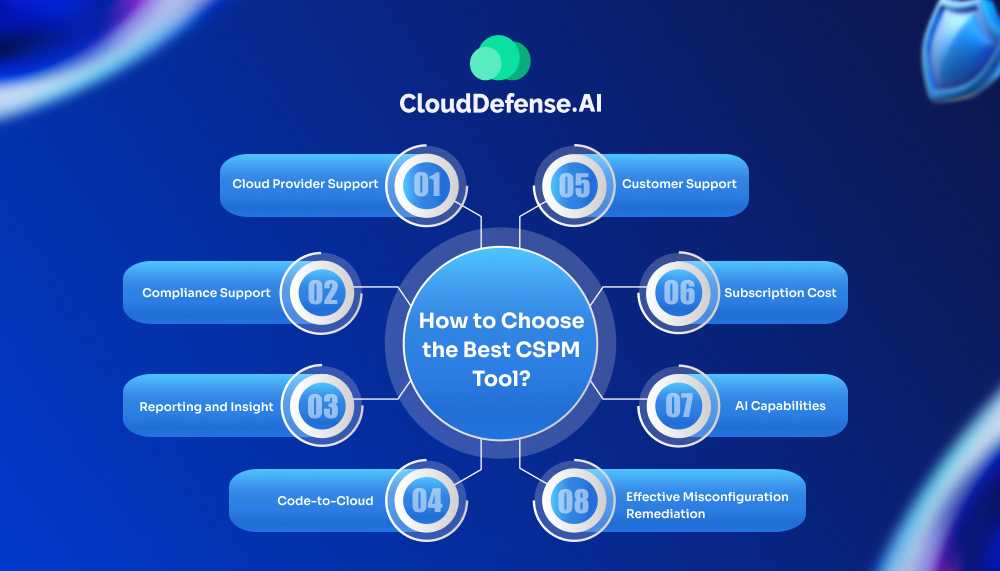
Choosing the best CSPM tool is crucial for your business as it will ensure the optimum security posture of your cloud environment. However, not everyone knows how to select them. That is why we have come up with some criteria that will help you to choose:
Cloud Provider Support
Whenever you are selecting a CSPM, you need to consider which cloud provider you are using and whether it integrates with the selected CSPM tool. If you are using GCP, not every CSPM tool will support it.
Compliance Support
The CSPM tool should support all the leading security standards like HIPAA, PCI DSS, NIST, GDPR, and others. Moreover, it should offer compliance monitoring to prevent violations.
Reporting and Insight
Having automated reporting and providing contextual insight through threat intelligence is an important aspect of CSPM tools. The tool should provide a quick report whenever an issue is detected to help the team immediately solve it.
Code-to-Cloud
A top-tier CSPM tool should offer code-to-cloud tracking capabilities, linking security across the entire development lifecycle. This feature identifies vulnerabilities from the codebase to the cloud infrastructure, providing a holistic view and enabling effective risk prevention at every stage.
Customer Support
Always consider the level of customer support the CSPM vendor offers, especially if you are implementing CSPM for the first time. Ensure that the support is there to assist you every time you need it.
Subscription Cost
Every CSPM tool comes with a unique range of subscription costs, and you will have to shortlist the one that caters to your budget.
AI Capabilities
Look for a CSPM tool that leverages AI for threat detection and automated remediation. AI-driven capabilities enhance the tool's ability to identify and address potential risks swiftly, offering a more proactive approach to cloud security.
Effective Misconfiguration Remediation
Choose a CSPM solution that provides efficient misconfiguration remediation. The tool should either automate the remediation process or offer clear, actionable steps for your team to rectify issues quickly, minimizing security risks and reducing the likelihood of breaches.
Conclusion
CSPM has become a must-have security solution for any business operating in the cloud. With its capabilities, it shields your organization from a wide range of threats, ensuring a stronger security posture. In this guide, we’ve highlighted the 10 best CSPM tools for 2025 to help you make an informed decision.
In the battle of best CSPM tools, CloudDefense.AI stands out as an all-in-one platform that not only enforces critical security measures and policies but also offers advanced features to detect misconfigurations and maintain compliance. Choosing CloudDefense.AI will significantly enhance your cloud security posture and keep your environment safe and secure.
Don’t believe us? Witness it yourself, book a free demo now!
Frequently Asked Questions (FAQs)
What is CSPM? Cloud Security Posture Management Explained
Cloud Security Posture Management (CSPM) detects and remediates cloud misconfigurations and security issues, automating real-time monitoring to ensure compliance with best practices. While some CSPM tools provide automated remediation, others alert security teams for manual action. CSPM supports SaaS, enhancing security and reducing compliance risks across cloud platforms, including containers and hybrid setups.
Why do you need a CSPM Tool?
A CSPM tool is essential for maintaining the security and compliance of your cloud environment. As cloud infrastructures grow in complexity, manual monitoring becomes nearly impossible. CSPM tools automate the process, identifying misconfigurations and vulnerabilities before they turn into security breaches. They ensure your cloud infrastructure aligns with best practices, helping you avoid costly compliance violations and providing peace of mind that your data is always protected.
What are CSPM Tools?
CSPM tools are software solutions designed to improve the security posture of cloud environments by continuously monitoring and assessing them for misconfigurations, compliance issues, and security risks. These tools offer features like automated remediation, compliance management, real-time threat detection, and policy enforcement. They support various cloud models, including SaaS and multi-cloud infrastructures, providing a centralized way to secure cloud resources and maintain compliance with industry standards.







