Organizations are increasingly adopting cloud technologies to enhance efficiency and scalability. However, this shift also introduces complex security challenges, particularly in protecting cloud infrastructures and the sensitive data they handle. Two critical strategies, CSPM and DSPM, can address these concerns.
CSPM focuses on identifying and rectifying security risks within cloud environments, ensuring that configurations adhere to best practices and compliance standards. Conversely, DSPM is dedicated to discovering, monitoring, and protecting sensitive data across various platforms.
Understanding the different roles and benefits of CSPM vs DSPM is essential for organizations aiming to implement a fail-proof security framework. Additionally, we explore how a CNAPP integrates both, providing a unified approach to securing cloud configurations and sensitive data while enhancing overall security posture.
What is CSPM?
Cloud Security Posture Management (CSPM) involves the continuous identification and resolution of risks within cloud environments and services (for example, S3 buckets with public read access).
CSPM tools automatically evaluate cloud configurations based on industry best practices, regulatory standards, and security policies, thus ensuring the security and effective management of cloud environments.
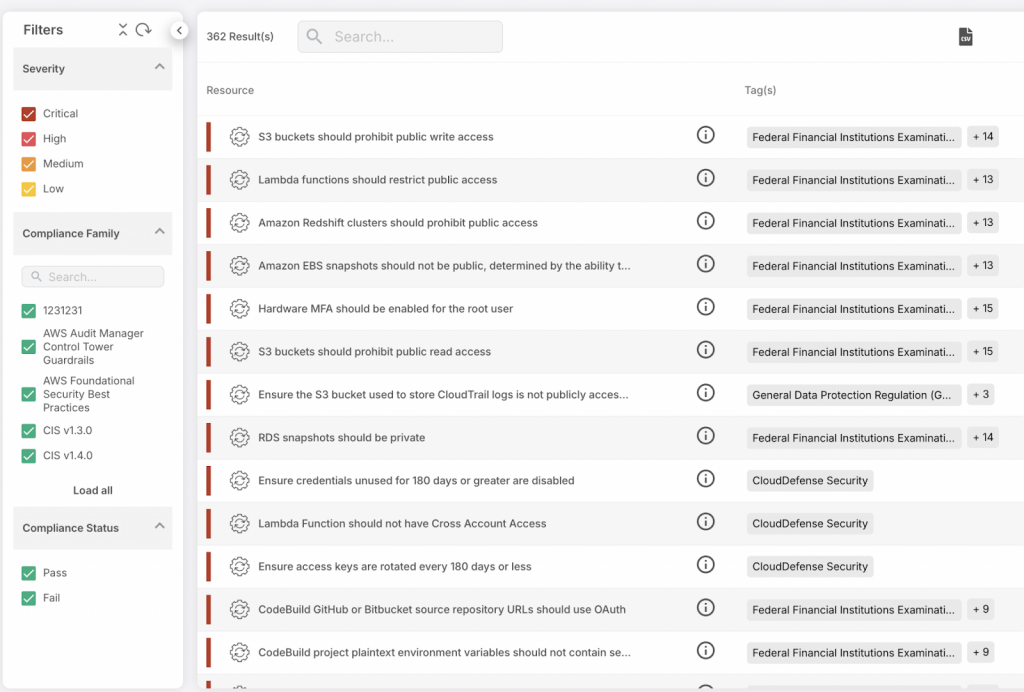
Its primary role is to identify and rectify misconfigurations, ensure compliance with industry standards, and mitigate security risks across various cloud services, including IaaS, PaaS, and SaaS.
Key Features of CSPM
- Continuous Monitoring of Cloud Configurations: CSPM solutions provide ongoing surveillance of cloud settings to detect security gaps and vulnerabilities promptly. This proactive monitoring helps in maintaining a robust security posture by ensuring that configurations adhere to best practices and organizational policies.
- Detection of Misconfigurations and Compliance Violations: CSPM tools help prevent potential security incidents by automatically identifying misconfigurations and compliance issues. They assess cloud environments against established benchmarks and regulatory requirements, alerting organizations to deviations that could lead to vulnerabilities.
- Automated Remediation Processes: CSPM solutions often include automated remediation capabilities, which allow for swift correction of identified issues. This automation reduces the reliance on manual intervention, decreasing the likelihood of human error and enhancing response times to security threats.
Benefits of Implementing CSPM
- Enhanced Visibility: CSPM provides comprehensive insights into cloud infrastructures, allowing organizations to understand their security posture fully.
- Improved Compliance: By continuously monitoring and enforcing compliance policies, CSPM assists organizations in adhering to industry standards and regulatory frameworks.
- Reduced Attack Surfaces: Identifying and remediating misconfigurations minimizes potential entry points for attackers, thereby strengthening the overall security of cloud environments.
Read more about ‘What is CSPM?’ in our comprehensive blog.
What is DSPM?
Data Security Posture Management (DSPM) is a security approach that enables organizations to assess, manage, and enhance the security of their data across various environments, including cloud services, on-premises systems, and hybrid infrastructures.
By providing continuous visibility and control over data assets, DSPM ensures the confidentiality, integrity, and availability of sensitive information.
Key Features of DSPM
- Data Discovery and Classification: DSPM solutions automatically and continuously identify and catalog data across diverse environments, including managed and shadow data resources. They classify data based on sensitivity and compliance requirements, providing a clear understanding of where sensitive data resides.
- Access Controls and Encryption: Implementing robust access controls ensures that only authorized personnel can access sensitive data. DSPM enforces policies that restrict data access based on roles and responsibilities. Additionally, it applies encryption mechanisms to protect data at rest and in transit, safeguarding it from unauthorized access and breaches.
- Monitoring Data Flows and User Activities: Continuous monitoring of data flows and user activities is essential for detecting anomalies and potential security incidents. DSPM solutions track how data moves within the organization and monitor user interactions with data, enabling the identification of suspicious behaviors that may indicate security threats.
Benefits of Implementing DSPM
- Comprehensive Protection of Sensitive Information: By providing a holistic view of data assets and their security posture, DSPM enables organizations to implement targeted security measures, ensuring that sensitive information is adequately protected against unauthorized access and breaches.
- Assistance in Meeting Data Privacy Regulations: DSPM helps organizations comply with data protection laws and industry standards by continuously monitoring data security controls and providing automated compliance assessments. This proactive approach ensures that data handling practices align with regulatory requirements, reducing the risk of non-compliance penalties.
- Early Detection of Potential Data Breaches: DSPM solutions can quickly identify unusual patterns or unauthorized access attempts through continuous monitoring and real-time analysis of data activities. Early detection allows organizations to respond promptly to potential data breaches, minimizing damage and reducing recovery costs.
Read more about ‘What is DSPM?’ in our comprehensive blog.
CSPM vs DSPM: Key Differences
Understanding the key differences between CSPM vs DSPM is very important for all organizations looking to strengthen their cloud security strategy. While both play vital roles, they focus on different aspects of security. Let’s learn more about the differences.
Scope of Protection
CSPM ensures comprehensive cloud security by continuously monitoring configurations and detecting misconfigurations. It enforces compliance with industry standards and guidelines to maintain secure cloud infrastructure. While it helps reduce the risk of data exposure by maintaining a secure cloud environment, it does not directly protect data.
However, DSPM, on the other hand, focuses on securing sensitive data, protecting it across various environments such as databases, cloud storage, and SaaS applications, and preventing unauthorized access.
Approach to Security
CSPM secures the environment by identifying misconfigured cloud assets, enforcing security policies, and preventing unauthorized access to cloud services. It maintains a secure cloud posture through real-time monitoring. DSPM emphasizes securing the data itself, utilizing encryption, strict access controls, and data classification to mitigate exposure risks, detect shadow data, and ensure compliance.
Use Cases
CSPM is ideal for organizations that use cloud services extensively and aim to maintain a strong security posture. It ensures that cloud resources adhere to best practices and comply with industry regulations. DSPM is crucial for organizations that deal with sensitive data, such as healthcare or financial institutions, and ensures data privacy and compliance across cloud environments.
Both CSPM and DSPM complement each other, and organizations aiming for a robust cloud security strategy may benefit from implementing both solutions to secure both their cloud infrastructure and sensitive data.
CSPM vs DSPM: Comparison Table
| Factor | CSPM | DSPM |
| Primary Focus | Securing cloud configurations, identity management, and detecting misconfigurations. | Protecting sensitive data across structured and unstructured environments. |
| Best for | Organizations concerned about cloud security posture, misconfigurations, and access control. | Companies prioritizing data security, classification, and governance. |
| Compliance Role | Ensures cloud infrastructure settings align with compliance frameworks like GDPR, HIPAA, and PCI DSS. | Provides visibility into sensitive data storage, access, and compliance adherence. |
| Security Risks Addressed | Prevents unauthorized access, insecure configurations, and cloud service vulnerabilities. | Mitigates data exposure, insider threats, and compliance violations. |
| Resource Considerations | Requires cloud security expertise and continuous monitoring of cloud settings. | Needs strong data security capabilities, including encryption and access control. |
| When to Choose | If cloud misconfigurations and security posture are your primary concerns. | If protecting and managing sensitive data is your highest priority. |
| Ideal for Teams With | Cloud security teams focused on infrastructure security. | Data security teams managing classification, encryption, and governance. |
| Integration | Often part of broader cloud security solutions like CNAPP. | Can be integrated with CSPM or as part of a CNAPP for complete protection. |
| Unified Approach | Many organizations use CSPM and DSPM together for end-to-end security. | Often combined with CSPM to ensure holistic cloud and data security. |
How to Choose Between CSPM and DSPM?
Choosing between CSPM vs DSPM depends on your organization’s cloud environment, security priorities, and compliance needs. While both solutions are essential, understanding your specific requirements can help you determine whether you need one or both for a comprehensive security strategy.
Assessing Organizational Needs
The first step in deciding between CSPM vs DSPM is evaluating the nature of your cloud infrastructure and data assets. If your primary concern is securing cloud configurations, identity management, and detecting misconfigurations that could expose your environment to risks, then CSPM is a must.
However, if your focus is on protecting sensitive data across structured and unstructured environments, DSPM ensures that your critical information is properly classified, monitored, and secured.
Compliance Requirements
Regulated industries such as healthcare, finance, and government services must comply with stringent data protection laws, such as GDPR, HIPAA, and PCI DSS. CSPM plays a critical role in ensuring cloud compliance by continuously assessing infrastructure settings against compliance benchmarks.
On the other hand, DSPM strengthens data governance by providing visibility into where sensitive data resides, how it is accessed, and whether it aligns with regulatory requirements. If compliance is a driving factor for your organization, integrating both CSPM and DSPM can provide complete security coverage.
Resource Availability
Security solutions require dedicated teams, expertise, and tools for effective implementation and management. If your organization has a strong cloud security team but limited resources to monitor and secure vast amounts of data, CSPM might be the priority. Conversely, if your team is well-equipped to handle data classification and encryption but struggles with cloud misconfigurations, DSPM can offer better protection.
A fully integrated CNAPP solution, such as CloudDefense.AI, can help streamline security operations by providing a unified platform for both CSPM and DSPM without overwhelming your security teams.
Risk Tolerance
Understanding your organization’s risk appetite is crucial when choosing between CSPM vs DSPM. If your primary security concern is cloud misconfigurations leading to unauthorized access, CSPM should be a priority. However, if data exposure, insider threats, or compliance violations pose greater risks, DSPM becomes critical.
Many modern security teams opt for a CNAPP solution that integrates CSPM, DSPM, and other security measures. This eliminates the need to choose between them and ensures end-to-end security across cloud environments.
Why not Choose Both?
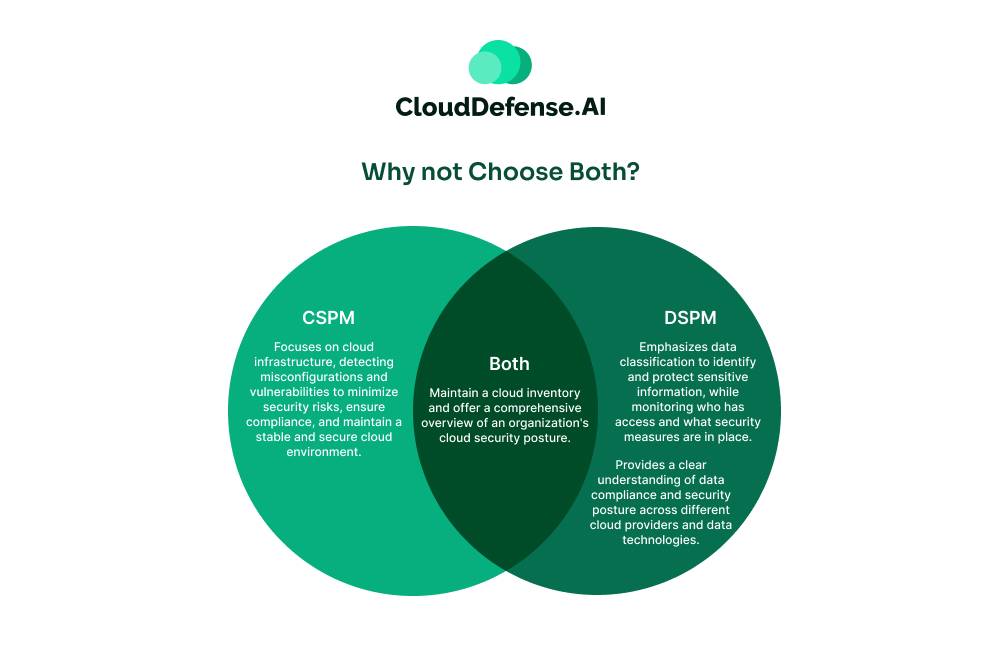
CSPM (Cloud Security Posture Management)
- Focuses on cloud infrastructure, detecting misconfigurations and vulnerabilities to minimize security risks, ensure compliance, and maintain a stable and secure cloud environment.
BOTH
- Maintain a cloud inventory and offer a comprehensive overview of an organization’s cloud security posture.
DSPM (Data Security Posture Management)
- Emphasizes data classification to identify and protect sensitive information, while monitoring who has access and what security measures are in place.
- Provides a clear understanding of data compliance and security posture across different cloud providers and data technologies.
CSPM and DSPM complement each other in securing cloud environments. CSPM protects cloud infrastructure, detecting misconfigurations and ensuring compliance, while DSPM focuses on data security, identifying sensitive information and enforcing access controls.
Using both provides comprehensive protection, minimizing risks across infrastructure and data. Instead of choosing one, integrating CSPM and DSPM enhances visibility, compliance, and security, creating a robust cloud security strategy against evolving threats.
CNAPP: Integrating CSPM and DSPM for Complete Security
Not all CNAPPs are created equal, making it essential to evaluate your options carefully. Some CNAPP solutions lack DSPM, leaving critical data vulnerabilities unaddressed.
While CSPM focuses on securing cloud infrastructure, DSPM specifically targets data security risks. It ensures sensitive information is protected from misconfigurations, unauthorized access, and potential breaches.
Choosing a CNAPP, like CloudDefense.AI, that integrates both CSPM vs DSPM, along with other Cloud Security solutions such as CIEM, CWPP, and Runtime Security, gives your organization end-to-end security coverage, protecting both your cloud environment and the data within it.
Simplify and strengthen your security with CloudDefense.AI. Our agentless, all-in-one security platform simplifies cloud security, reduces complexity, and lowers costs while empowering your teams to focus on what matters most. Request a CloudDefense.AI demo today and experience the power of complete cloud security.







