What is DSPM?
DSPM is a relatively new cybersecurity technique that enables organizations to protect their sensitive data across various environments, including multi-cloud platforms. It is designed to help organizations understand their data landscape and figure out where their most critical data is, who can access it, and how secure it is.
First coined by market researcher Gartner in its Hype Cycle for Data Security 2022, DSPM is sometimes referred to as a “data-first” approach, meaning it prioritizes protecting the data itself rather than just focusing on securing the systems and applications that access it. It helps you identify where sensitive data resides, who has access to it, in what way it’s being used, and most importantly, how secure it is.
Imagine it like a security map, illuminating all corners of your cloud infrastructure and pointing out the precise places where data is at risk so you can take steps to defend them properly. This is crucial in today’s world, where data is scattered across diverse environments and constantly on the move.
Why is DSPM important?
Cloud environments are storing more data than ever, and with that comes a serious risk. In 2023, a survey found that 75% of businesses had over 40% of their cloud data classified as sensitive—a massive jump from just 26% the year before. This sharp increase means traditional security methods just aren’t cutting it anymore, leaving sensitive data exposed.
That’s where DSPM (Data Security Posture Management) comes in. It’s designed to tackle these challenges head-on, helping businesses keep tabs on their sensitive data, whether it’s spread across one cloud or multiple.
Instead of relying on outdated methods that struggle to keep up, DSPM gives companies the tools to see what’s happening with their data in real time, spot vulnerabilities, and lock things down before something goes wrong. It’s not just about security—it’s about staying ahead of a growing problem in a fast-changing landscape.
| “Did you know? In 2024, it took an average of 194 days just to identify a data breach and another 64 days to contain it. That’s over 8 months of exposure!” |
How Does DSPM Work?
Data Security Posture Management helps companies protect their important information by knowing the way data moves inside their systems and finding possible security dangers. It operates through a well-defined cycle, ensuring continuous monitoring and improvement of data security posture.
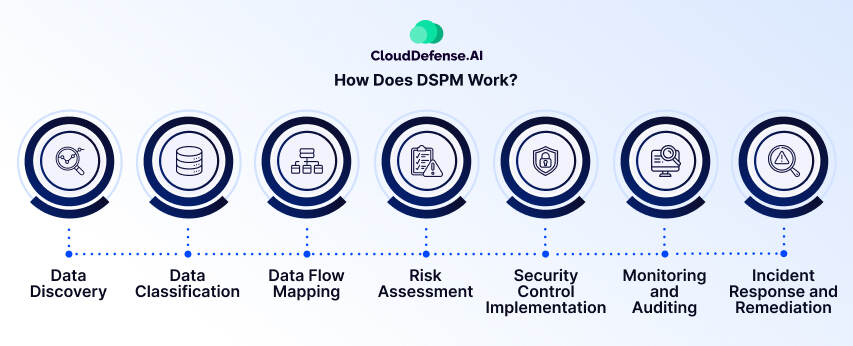
1. Data Discovery
The process starts by finding and listing all data sources in the company – this includes databases, systems for files, storage in the cloud, and applications from outside parties. The detailed map shows where important and private data is kept, such as personal details, money records, business ideas, or intellectual property.
2. Data Classification
Once discovered, data is categorized based on its sensitivity and importance. This classification, often aligned with regulatory compliance requirements, helps to decide which data protection actions are most important. High-risk data, such as medical records or credit card numbers, demands more stringent safeguards than less sensitive information.
3. Data Flow Mapping
DSPM goes beyond static data location, visualizing how it moves within the infrastructure. It maps how sensitive data flows between servers, databases, and software, revealing potential weak points and access paths. This visual representation helps us understand the patterns of data transfer and possible areas that are not strong enough.
4. Risk Assessment
Armed with data flow insights, DSPM identifies potential risks and vulnerabilities—think unauthorized access, data leaks, or even the lack of encryption.
It looks for:
- Misconfigurations: Missing security settings, leaving data vulnerable (unsecured cloud storage, unpatched systems, weak encryption).
- Overentitlements: Users have more access than needed, increasing the attack surface.
- Data flow/lineage issues: Tracking data movement to identify potential attack paths.
- Policy/regulatory violations: Finding gaps between data protection and security policies/regulations.
This evaluation of risk lets companies arrange their security tasks by importance, giving attention first to the most serious dangers and dealing with them before they happen.
5. Security Control Implementation
Based on the identified risks, organizations can implement the necessary security controls to protect their data. This might involve encryption to scramble sensitive information, access control to restrict unauthorized users, or data loss prevention (DLP) techniques to monitor and block unauthorized data transfers.
6. Monitoring and Auditing
Constant vigilance is key. DSPM continuously monitors data flow to detect anomalies, potential threats, and policy violations. Regular audits ensure the effectiveness of security controls and compliance with data protection regulations, preventing issues before they escalate.
7. Incident Response and Remediation
In the case of a security issue, DSPM provides crucial information for rapid response. It helps identify affected data, assess the breach’s scope, and implement remediation measures to minimize the impact. This swift action can significantly reduce the damage caused by data breaches.
| “Did you know? In 2024, the United States saw the highest average cost of a data breach at a staggering $9.36 million. The Middle East followed closely at $8.75 million – Source: IBM.” |
Benefits of DSPM for Cloud Data Security:
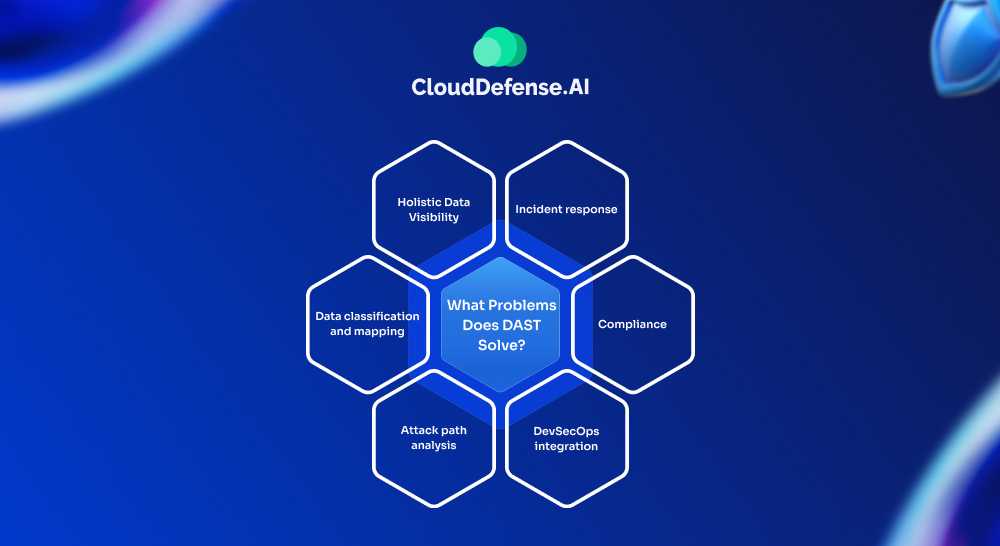
Holistic Data Visibility: Identify all sensitive data (structured and unstructured) residing in your cloud environments, including forgotten databases and shadow data stores. This comprehensive view eliminates blind spots and empowers informed security decisions.
Data classification and mapping: Classify sensitive data and map it to relevant regulations, revealing exposure areas and tracking data lineage (origin and access history).
Attack path analysis: Discover potential attack vectors or paths leading to sensitive data by looking at how sensitive the data is, who can access it, what weak spots there are, and how things are set up. This helps prioritize risks based on their severity.
DevSecOps integration: Integrate with DevSecOps workflows to address risks early in the application development lifecycle, promoting proactive security throughout the development process.
Compliance: Simplify compliance with data protection regulations like GDPR, HIPAA, and PCI-DSS by identifying and closing security gaps that could lead to non-compliance and reputational damage.
Incident response: Leverage built-in incident response plans offered by most DSPM solutions to accelerate recovery from security incidents and minimize potential harm.
In a nutshell, when you use a DSPM solution, your security team, IT operations group, and DevOps unit get a full picture of what’s happening with data in the cloud. This helps them to:
- Proactively identify and mitigate security risks before they can be exploited.
- Prioritize remediation efforts based on data sensitivity and potential impact.
- Demonstrate compliance with data privacy regulations.
- Respond quickly and effectively to security incidents.
Key Considerations When Choosing a DSPM Solution:
Here are the key points to look for in a Data Security Posture Management (DSPM) solution:
Visibility and Monitoring:
- Rapid, agentless data discovery: The solution should quickly scan your infrastructure for sensitive data without requiring agent installation, ensuring efficient discovery and minimal disruption.
- Centralized dashboard and reporting: A central dashboard with comprehensive reports, real-time monitoring, and customizable visualizations is crucial for gaining insights into your data security posture.
Threat Detection and Prioritization:
- Continuous monitoring and detection: Opt for a solution that continuously monitors for critical data exposure and offers automated data classification to prioritize the most critical risks.
- Data lineage mapping: Look for a solution that implements data lineage mapping to understand the data lifecycle and detect potential backdoors or compliance issues.
Remediation and Automation:
- Real-time remediation: Choose a solution that allows for automatic or low-touch remediation of identified security issues, ensuring prompt response and reduced manual effort.
- CI/CD integration: Prioritize a DSPM solution that integrates with CI/CD pipelines to automatically scan code, infrastructure, and dependencies for vulnerabilities, offering comprehensive coverage.
- Automated compliance assessments: The solution should scan for compliance violations, generate reports, and provide recommendations for addressing non-compliance.
Advanced Features:
- AI security: Look for a solution that extends to AI environments, automatically detecting sensitive training data and proactively removing attack paths, addressing the emerging risks of AI data security.
- Scalability and performance: For large organizations, ensure the solution scales efficiently to handle massive datasets without performance lags.
Use Cases of DSPM
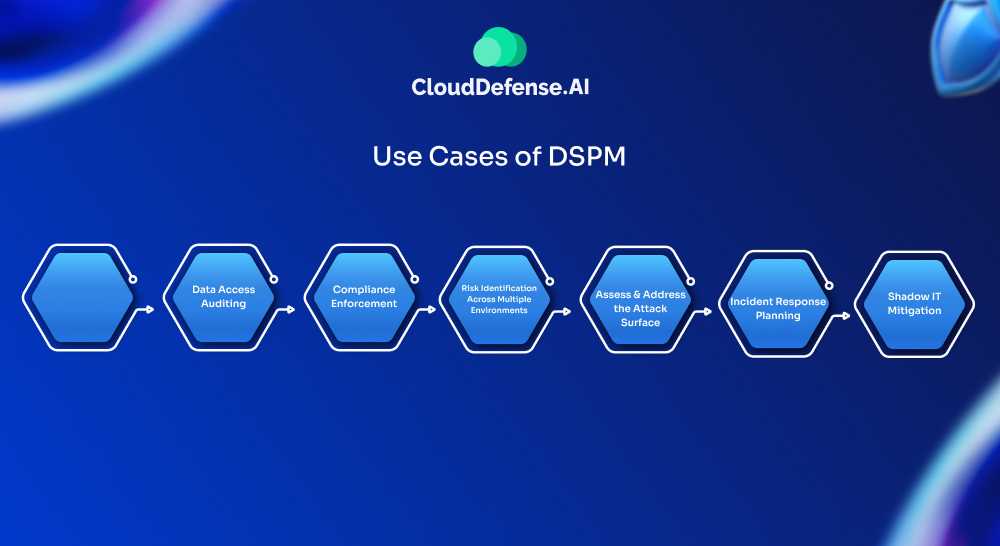
Data Discovery in Cloud Environments: Given the dynamic nature of the cloud, it’s easy for sensitive data to get scattered across different cloud services. DSPM steps in to help organizations automatically find and keep track of that important information, like customer details or proprietary data, no matter where it’s stored in the cloud.
Data Access Auditing: Knowing who has access to your critical data is crucial. With DSPM, companies can monitor who’s accessing sensitive information—whether it’s internal staff or external partners—and ensure that the permissions they have are appropriate for their roles.
Compliance Enforcement: Keeping up with regulations like GDPR or HIPAA can be a headache. DSPM simplifies this by continuously checking whether sensitive data is being handled according to the necessary legal standards, making compliance much easier to manage.
Risk Identification Across Multiple Environments: For organizations juggling both on-premise and cloud setups, DSPM provides a clear picture of potential risks. It helps track which sensitive data might be vulnerable due to misconfigurations or weak access controls, ensuring everything is as secure as possible.
Assess and Address the Attack Surface: Understanding where your data might be exposed is vital for security. DSPM helps organizations get a handle on their attack surface by identifying potential entry points for attackers and offering insights on how to close those gaps and strengthen defenses.
Incident Response Planning: When a data breach or anomaly occurs, quick action is essential. DSPM is a valuable resource for pinpointing where sensitive data may have been compromised and helps trace back to what might have caused the issue.
Shadow IT Mitigation: Many businesses face challenges with Shadow IT, where employees use unapproved cloud services. DSPM helps identify these unauthorized platforms, ensuring that sensitive data isn’t accidentally exposed in places that aren’t officially sanctioned by the organization.
Should DSPM Operate Independently as a Solution?
Considering today’s cloud security front, organizations are keen on ensuring the security of cloud-native applications and their associated data throughout the entire development process. The aim is to have a unified platform that caters to the needs of various teams, including security, DevOps, and data protection.
That’s why relying solely on DSPM as a standalone solution might not be the best approach. Although it brings valuable data protection features, incorporating it into broader CNAPPs like CloudDefense.AI offers numerous benefits. Here’s why:
The Trend Towards Consolidation:
- Security teams are facing tool sprawl and alert fatigue, making unified platforms with integrated solutions increasingly desirable.
- Organizations strive for holistic security across the cloud-native application lifecycle, encompassing development, deployment, and operations. A single platform catering to security, DevOps, and data protection teams build better collaboration and efficiency.
Benefits of Integrating DSPM with CNAPP:
- Unified Risk View: CNAPP combines CSPM, CIEM, and CWPP functionalities, already providing a comprehensive security posture picture. Adding DSPM creates a unified risk list prioritizing both data and cloud security vulnerabilities, streamlining remediation efforts.
- Enhanced Data Security: CNAPP with DSPM tracks data origin and flow within cloud storage and application networks, enabling efficient data movement protection.
- Reduced Alert Fatigue: CNAPP solutions correlate and prioritize security risks, minimizing alerts. When coupled with DSPM, the number of alerts is further reduced, allowing security professionals to focus on critical vulnerabilities.
While a stand-alone DSPM can offer data protection, its true potential unfolds when integrated within a CNAPP platform. This holistic approach streamlines security operations, prioritizes risks effectively, and empowers teams with a unified view of cloud and data security posture.
Best practices for implementing DSPM

Know Your Data: Start by getting a clear picture of what sensitive data you have and where it lives. Take the time to map out your data landscape, whether it’s in the cloud or on-premises. This foundational step helps you understand the scope of what you need to protect.
Regular Audits and Assessments: Make it a habit to conduct regular audits of your data access and security measures. This isn’t just a one-and-done task. Periodically checking in helps you catch any vulnerabilities or compliance issues before they become bigger problems.
Limit Access: Practice the principle of least privilege—only give people access to the data they absolutely need to do their jobs. Regularly review access permissions to ensure they’re still appropriate, especially when roles change or employees leave.
Invest in Automation: Take advantage of automated tools to help with data discovery and monitoring. Automating these processes can save you time and reduce the chances of human error, allowing you to focus on more strategic security efforts.
Stay Compliant: Keep up with the latest regulations and standards that affect your industry. Compliance is an ongoing journey, not a destination. Regularly update your policies and procedures to align with any changes in the legal landscape.
Use Data Encryption: Ensure that sensitive data is encrypted both at rest and in transit. This adds an additional layer of protection and helps secure data even if unauthorized access occurs.
Monitor for Threats: Set up continuous monitoring for any unusual activity related to your sensitive data. Having real-time alerts can help you respond quickly to potential breaches or unauthorized access attempts.
Establish an Incident Response Plan: Prepare for the unexpected by having a solid incident response plan in place. This should outline how to respond to data breaches or security incidents, ensuring everyone knows their role when things go wrong.
Continuously Improve: Data security is not static. Regularly review and update your DSPM practices to adapt to new threats and changes in your organization. Embrace a culture of continuous improvement to stay ahead in the security landscape.
Difference Between DSPM, CSPM, and CIEM
While all three acronyms – DSPM, CSPM, and CIEM – deal with cloud security, they each focus on different aspects and serve distinct purposes. Here’s a breakdown:
| Tool Acronym | Focus | Function | Key Capabilities |
| CSPM | Secures the overall cloud environment | Identifies and addresses misconfigurations, compliance issues, and security risks in your cloud infrastructure and resources. | Continuously monitors cloud configurations for deviations from security best practices. Detects potential threats and vulnerabilities. Ensures compliance with industry standards and regulations. Provides insights and recommendations for improving cloud security posture. |
| DSPM | Protecting sensitive data in the cloud | Discovers, classifies and monitors sensitive data across your cloud environment to prevent unauthorized access or breaches. | Identifies and classifies sensitive data types (e.g., PII, financial data). Tracks data movement and access attempts. Detects suspicious activity related to sensitive data. Helps ensure compliance with data privacy regulations. |
| CIEM | Managing user access and entitlements in the cloud | Provides centralized control over user access to cloud resources, enforcing the principle of least privilege and preventing unauthorized access. | Discovers and inventories all users and devices accessing cloud resources. Tracks user activity and entitlements. Provides granular control over user permissions and access. Helps prevent insider threats and privilege escalation attacks. |
CloudDefense.AI’s DSPM Approach
At CloudDefense.AI, we believe in simplifying the complexities of data security, not complicating them. Our DSPM approach is designed to give you the speed, clarity, and control you need to protect your critical data—without unnecessary complexity. We focus on what matters most to you: visibility, compliance, threat detection, and automated response, all within a streamlined, human-friendly platform.
1. Instant Data Insights
One of the biggest challenges in securing cloud data is knowing exactly where your critical information resides. Our solution eliminates the need for clunky agents or complex installation processes. In just a few moments, you get full visibility into your cloud environment, helping you quickly locate and assess your most sensitive data.
No more worrying about blind spots or spending hours manually mapping data flows. Our agentless approach means you can be up and running in no time, with minimal impact on your infrastructure.
2. Unified Dashboard for Seamless Monitoring
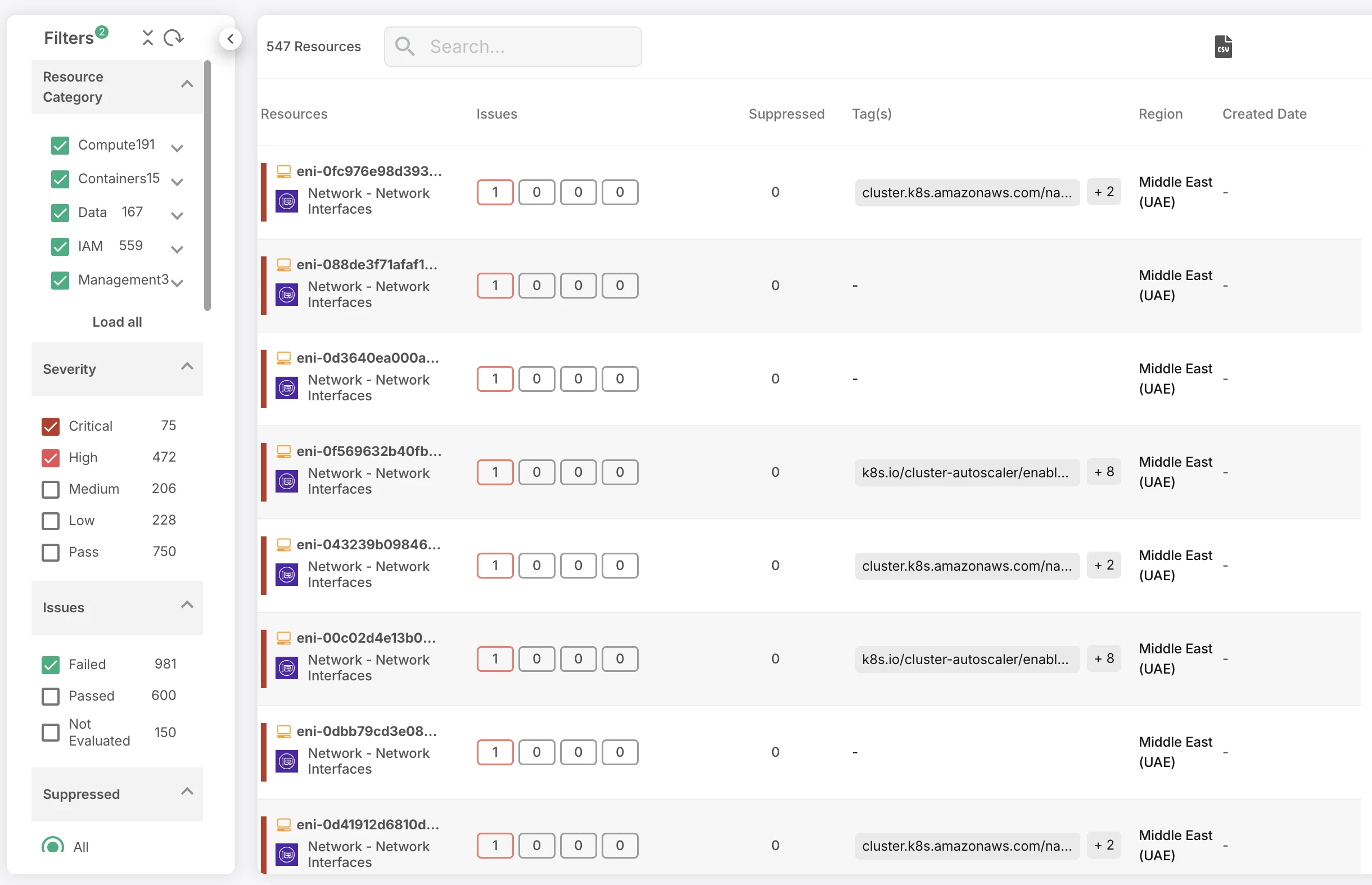
Visibility is great, but knowing what to do with it is even better. That’s why our intuitive, centralized dashboard brings all your data insights together in one place. From security posture to data health, compliance status, and more, you can monitor every aspect of your cloud environment from a single interface.
Reporting is equally simple, with automated reports that give you a clear snapshot of your security landscape. Whether you’re tracking trends, identifying weaknesses, or making data-driven decisions, everything you need is right there—at your fingertips.
3. Compliance Made Effortless
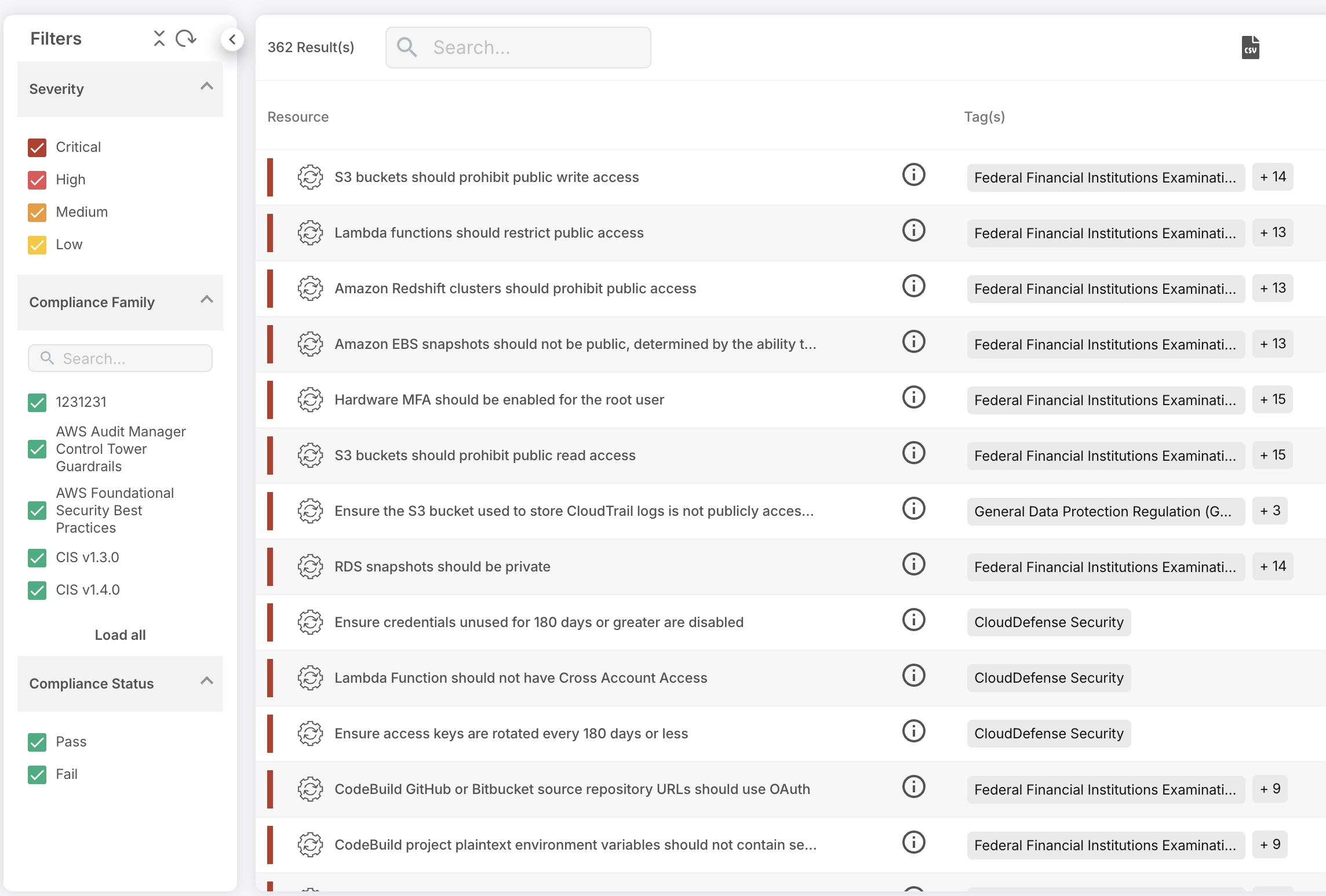
Navigating the ever-changing regulatory landscape is a constant challenge. Compliance with industry standards and regulations doesn’t have to feel like a burden. CloudDefense.AI automatically ensures your cloud data is aligned with key compliance frameworks, from GDPR to CCPA, HIPAA, and beyond.
Our system continuously monitors your environment and alerts you if something is out of compliance, making it easy to stay ahead of audits. With real-time compliance tracking, you can confidently report to stakeholders without the stress of last-minute scrambling.
4. Attack Path Analysis
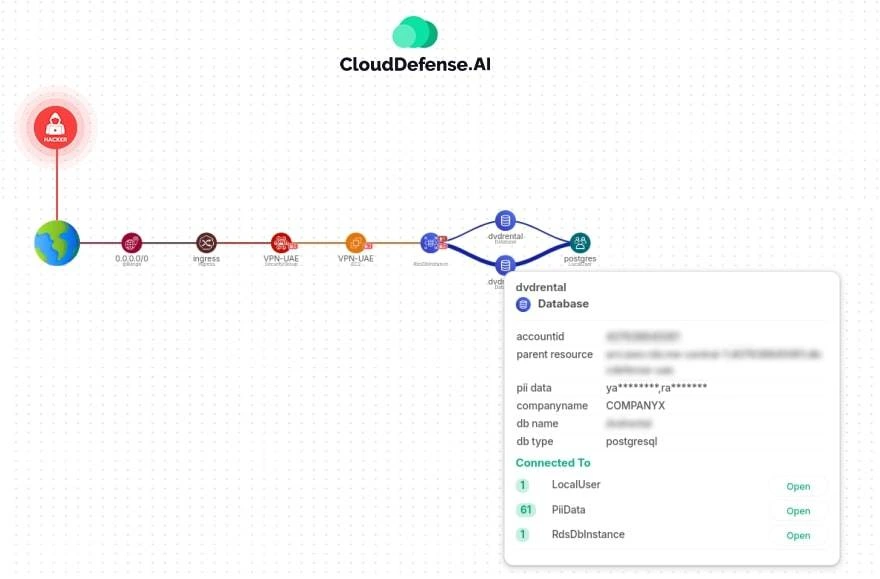
It’s not enough to know that a threat exists—you need to know exactly how an attack could unfold. CloudDefense.AI’s attack path analysis helps you understand potential entry points and routes that cybercriminals could use to target your sensitive data. By mapping out these attack paths, we give you actionable insights into how to fortify your defenses and stop threats before they even reach your data.
5. Auto Remediation
Security threats can strike at any moment, and waiting for a manual response can leave you vulnerable. CloudDefense.AI’s auto-remediation takes immediate action when security issues are detected. Whether it’s isolating a breach, applying patches, or correcting misconfigurations, our system reacts in real-time to contain the problem and minimize damage. No need to wait for an IT team to intervene—your data stays secure automatically, so you can focus on growing your business without interruptions.
Conclusion
To sum up, CloudDefense.AI’s CNAPP empowers your security team by adopting a unified and data-driven approach to DSPM. Proactively handle data security risks, effectively prioritize tasks, and make well-informed decisions across your entire cloud setup. By unifying data from various sources and utilizing advanced analytics, CloudDefense.AI offers a comprehensive overview of your cloud security stance. This grants you real-time insights into potential threats and allows you to prioritize efficiently and make informed decisions.
Don’t wait for a breach to expose your vulnerabilities. Take control of your cloud security today. Book a free demo and experience the power of CloudDefense.AI’s CNAPP firsthand. See how it can transform your security posture and empower your team to thrive in the cloud.







