What is CIEM?
Cloud Infrastructure Entitlement Management (CIEM) is a security process for managing and controlling access rights to cloud resources.
It provides organizations with a complete view of cloud entitlements, which are permissions granted to cloud identities—whether they are human users, machine accounts, or services.
Properly managing these entitlements is essential, as unnecessary or outdated permissions can lead to security vulnerabilities.
CIEM helps identify and minimize risks by monitoring access permissions across cloud and multi-cloud environments, ensuring users have only the necessary privileges.
By enforcing the principle of least privilege, CIEM reduces the cloud attack surface, enhancing security.
Integrating CIEM into a broader security strategy, such as a Cloud-Native Application Protection Platform (CNAPP), offers a holistic approach to managing cloud identities and entitlements.
What Cloud Challenges Does CIEM Help Address?

Managing access and entitlements in cloud environments is no small feat. As cloud infrastructure grows more complex, so do the challenges around securing access. CIEM is a key solution to these pressing issues, helping organizations to operate and control the complexity of cloud access within their reach.
- Identity Sprawl: As organizations adopt more cloud services and automate processes, they face a rapid increase in identities, including users, service accounts, and bots. CIEM centralizes the management of this sprawl, ensuring all cloud identities are properly monitored and controlled, reducing the risk of security oversights.
- Limited Visibility: Many organizations need a clearer view of who has access to which cloud resources, creating hidden security gaps. CIEM provides in-depth visibility into access entitlements, offering insights into cloud resources’ access and use. This visibility helps identify risky access patterns and make informed security decisions.
- Excessive Permission Risks: Users and services are often granted more permissions than necessary, leading to security vulnerabilities. CIEM helps pinpoint and eliminate these excessive permissions, aligning access with the principle of least privilege. This minimizes the risk of unauthorized actions and potential breaches.
- Multi-Cloud Complexity: Managing access across cloud providers, like AWS, Azure, and Google Cloud, can lead to inconsistent access control policies. CIEM unifies access management across these diverse environments, simplifying policy enforcement and ensuring consistent security practices, regardless of the cloud platform.
- Compliance Challenges: Regulatory standards often demand strict access controls and thorough auditing. CIEM supports compliance efforts by offering automated policy enforcement, detailed audit logs, and reporting tools. This helps organizations stay compliant and provides the documentation needed for audits.
What are the Components of CIEM
Cloud computing has seen increased acceptance in companies mainly due to the bucketload of advantages it brings to the table. However, these advantages are not enough to hide the number of security risks that businesses can face while operating on the cloud.
A report by CyberArk highlights that 93% of organizations had two or more identity-related breaches in the past year. Identity-related breaches should not be a reason to rethink your presence on the cloud.
With the capabilities of CIEM by your side, you can reduce such risks by integrating it into your overall cloud security infrastructure. Let’s check out some of the core cloud security components that CIEM plays a major role in.
| Component | Description |
| Entitlement Visibility | CIEM tools automatically scan cloud environments to provide a comprehensive view of existing entitlements. They identify which identities have access to specific resources and the level of access granted. This visibility helps to understand and mitigate potential security risks. |
| Rightsizing Permissions | CIEM assesses entitlements to ensure they align with the principle of least privilege. It identifies overly permissive access rights and recommends adjustments to reduce the attack surface by alerting administrators or automated remediation. |
| Advanced Analytics | Using machine learning and user and entity behavior analytics (UEBA), CIEM tools detect anomalies in access patterns. They analyze entitlements in real-time to identify and respond to potential threats, providing intelligent insights for proactive security measures. |
| Policy Enforcement | CIEM enables the definition and automation of security policies across the cloud environment. It applies granular controls based on user roles, geographical location, and time, ensuring consistent enforcement of access rules. |
| Automated Remediation | Automated CIEM mechanisms give recommendations allowing teams to quickly address risky entitlements and revoke unnecessary permissions, streamlining the process of securing cloud access. This automation is particularly vital in large-scale environments. |
| Compliance Management | CIEM helps you with complying with industry regulations, such as GDPR, HIPAA, and CCPA. It ensures that access policies conform to compliance needs and provides auditing capabilities to detect and rectify compliance drift over time. |
Benefits of CIEM
We believe we have answered your question, “What is CIEM?” and how it addresses identity management challenges on the cloud! Let’s now move forward to exploring the heap of benefits that CIEM can bring to the table.
CIEM provides a strategic advantage by automating cloud entitlement management, reducing risk, and enabling organizations to focus on their core business objectives.
Here are 4 benefits that a robust CIEM implementation can offer to you.
1. Enhanced Security Posture
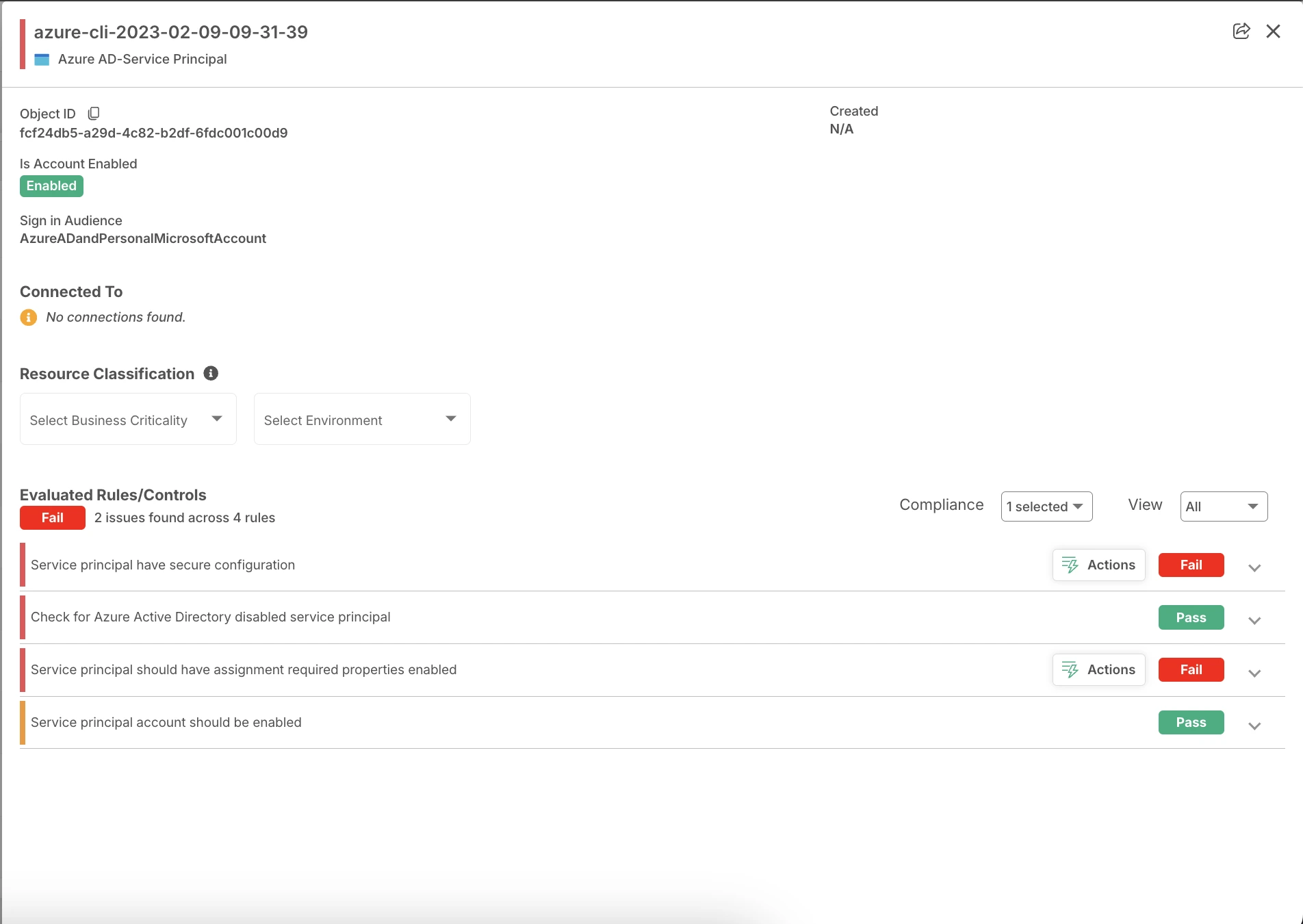
By strictly enforcing the principle of least privilege, CIEM ensures that digital identities only possess necessary access to critical cloud resources. This strengthens security by minimizing exposure to potential breaches and unauthorized access attempts.
Integrating CIEM with CNAPP further strengthens security by swiftly identifying vulnerabilities and mitigating risks in real-time.
2. Complete Visibility
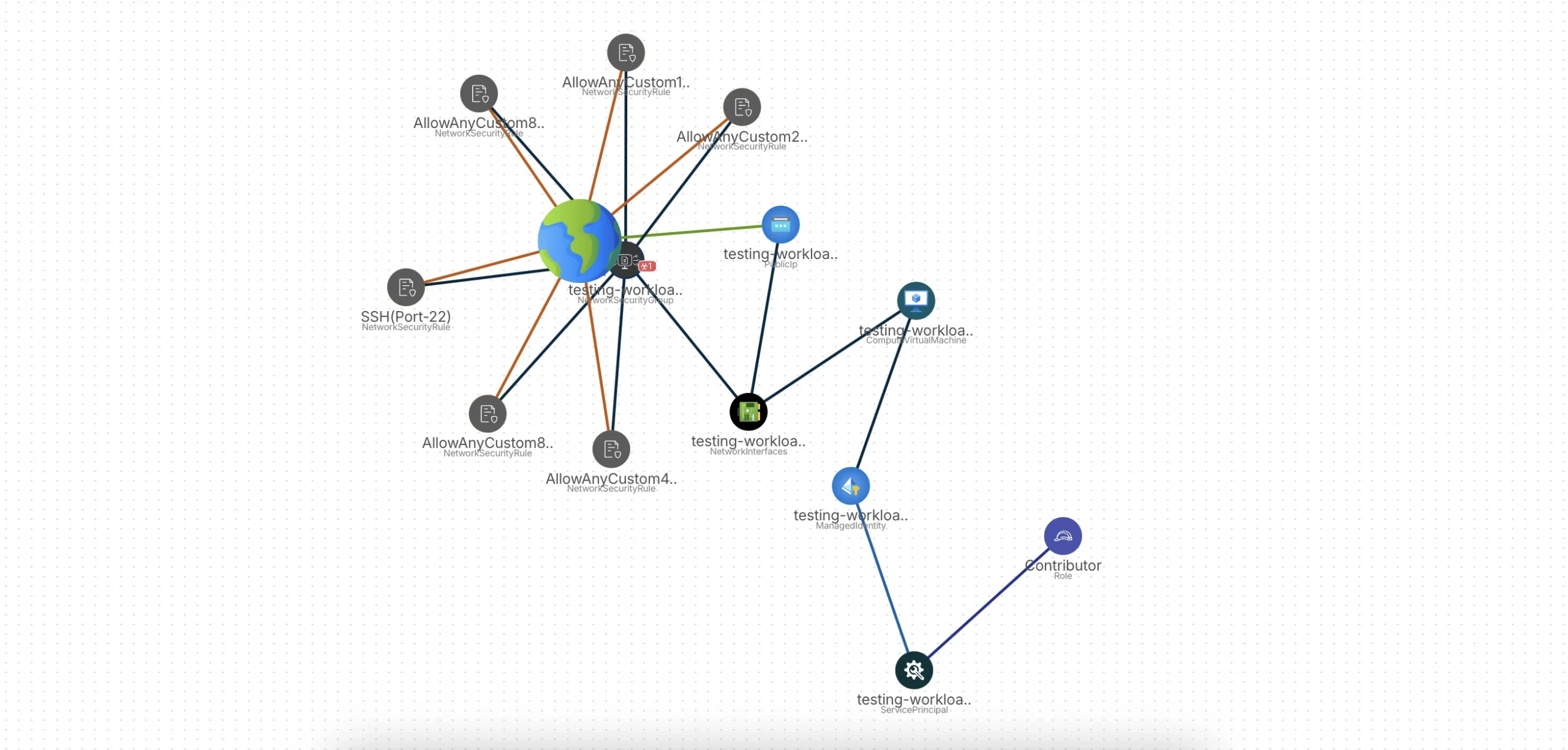
CIEM provides a centralized platform for managing entitlements and identities across complex multi-cloud environments. By offering deep visibility into user access rights and privileges, CIEM helps organizations identify and mitigate security risks associated with excessive or dormant accounts.
This detailed oversight enables businesses to simplify access control processes, reduce the risk of unauthorized access, and ensure compliance with industry regulations.
3. Automated Identification and Remediation of Identity-related Threats
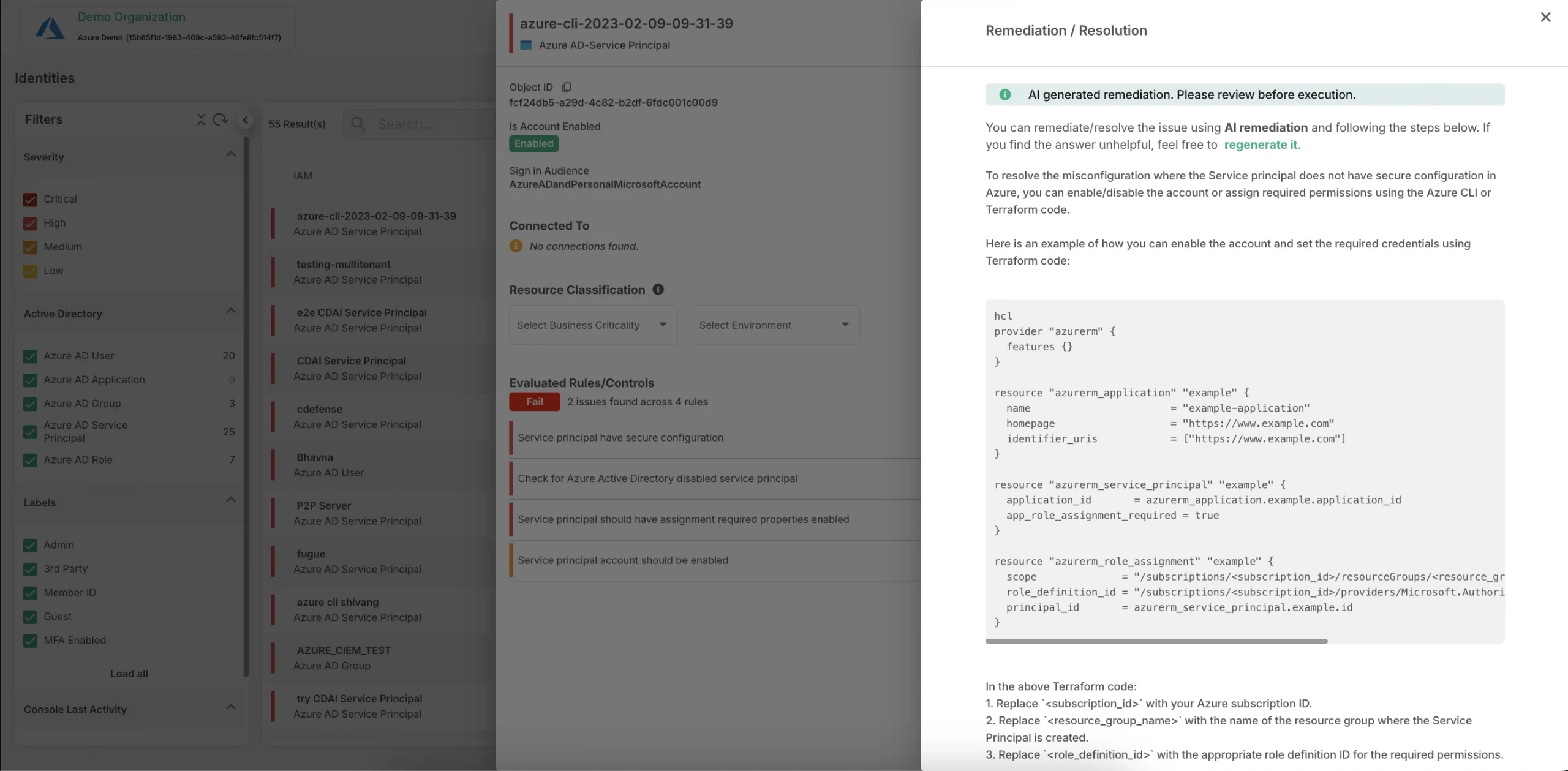
CIEM provides granular visibility into the activities of IAM user accounts, enabling early detection of identity-related risks such as unnecessary privileges or configuration errors. Advanced CIEM solutions automate the identification, prioritization, and resolution of these risks, protecting enterprises against potential financial and operational disruptions.
4. Improved Compliance
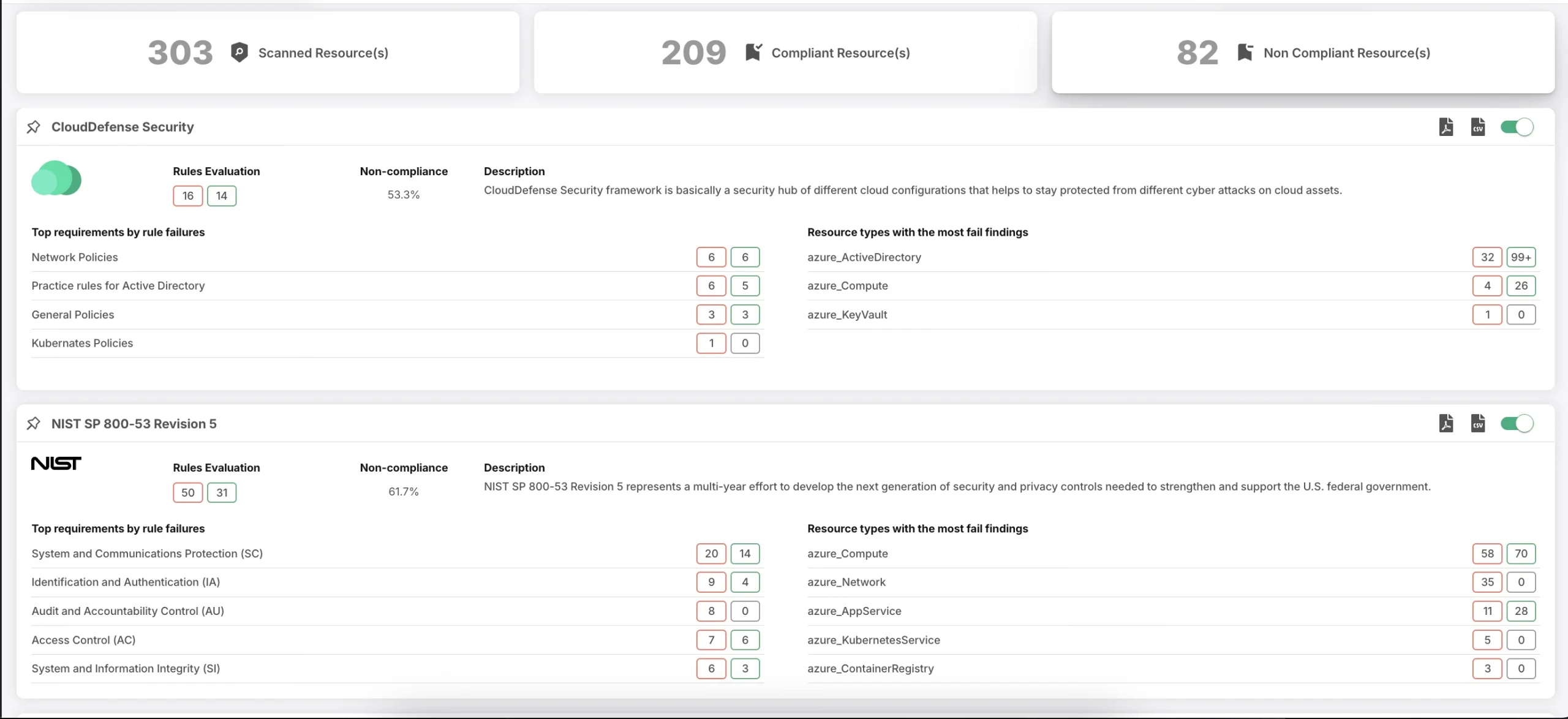
CIEM is a game-changing tool for organizations seeking to comply with strict regulatory requirements, such as GDPR, CCPA, HIPAA, PCI DSS, and FedRAMP. By providing a centralized platform for managing entitlements and identities, CIEM helps businesses automate the detection and remediation of identity-related risks.
This ensures compliance with data privacy and security standards. This approach minimizes the risk of legal liabilities, encourages audits, and demonstrates a commitment to data protection.
How does CIEM Work?
CIEM’s benefits have made it quite popular among companies on the cloud. Before you can reap these benefits, you would need to understand how CIEM works.
1. Understanding Access Patterns
CIEM analyzes your organization’s access patterns to create a detailed map of who has access to what resources across your multi-cloud environment. This helps you identify potential security risks and vulnerabilities.
2. Optimizing Permissions
Top CIEM solutions can automatically monitor cloud identities and adjust permissions to ensure that users only have the access they need (the principle of least privilege). This reduces your organization’s attack surface and helps prevent unauthorized access.
3. Detecting Accidental Exposure
Even brief instances of accidental exposure can lead to serious security breaches. CIEM can detect when sensitive information or credentials are accidentally exposed, allowing you to take immediate action to mitigate the risk.
4. Providing Remediation Guidance
CIEM doesn’t just identify problems; it also offers step-by-step guidance on how to fix them. This helps your team address security vulnerabilities and incidents efficiently, minimizing potential damage.
Is CIEM Integrated into your Security Stack?
Choosing the right cloud security solutions can be overwhelming for many companies. With a range of cybersecurity threats and a growing market of CIEM vendors and platforms, it’s challenging to determine which CIEM tool best fits your needs. The key lies in finding a solution that smoothly integrates CIEM with other cloud security measures for an all-in-one approach.
CloudDefense.AI’s CNAPP demo offers a hands-on experience to see how combining CIEM with other cloud security tools into a unified platform can transform your cloud security strategy. You can learn how CloudDefense.AI’s CIEM tool supports Zero Trust by enforcing least privilege, continuously optimizing cloud permissions to prevent excessive access.
It automates the detection and remediation of misconfigurations, reducing the attack surface. This enhances security by restricting lateral movement and minimizing risks within the cloud infrastructure.
Book a free demo now to witness it firsthand!
Frequently Asked Questions (FAQs)
Is CIEM a category of IAM?
CIEM solution serves as the main platform for implementing IAM in cloud deployment and helps- in applying consistent security policies across the cloud. It enforces the least privileged access to all the entitlements and ensures all the risks are mitigated.
What is the Difference between CIEM and SIEM?
CIEM manages cloud identities and permissions, ensuring users have only the necessary access to reduce security risks. SIEM, in contrast, collects and analyzes security events across the network for real-time threat detection and incident response, offering broader security monitoring.
What is the primary difference between CIEM and PAM?
CIEM serves as the management of entitlements and identities in the cloud environment. At the same time, PAM refers to the tools suitable for controlling access to accounts, monitoring user activity, and enforcing password policies.
What are the three primary categories of IAM?
The three primary categories of IAM are:
- Access management
- Authentication
- Administration
Access management controls how users can access your enterprise system, whereas authentication determines whether you should access certain systems. Administration assists enterprises in creating governance around identity and access management.







