In 2025, developers are always finding ways to speed up their development process. With the rapid adoption of AI code editors, organizations are achieving unprecedented development speed. However, it is also creating attack vectors in the development pipeline, and a vulnerability in the codebase can hamper the whole application.
Thus, securing the codebase is no longer optional- it has become more important than ever. Code security scanning is the answer for all organizations. It is a continuous and integrated code security approach that helps organizations in maintaining a high-speed development cycle while maintaining DevSecOps practice.
Modern organizations are adopting code security scanning tools as it can make a difference in shipping robust applications without facing the risk of a security breach. This article will be your practical guide to code security scanning in 2025 and the best practices to follow.
Code Security Scanning: A Brief Overview
Code security scanning is a specialized approach where code bases are continuously analyzed to identify and remediate security threats before they hit production. Code security scanning gets integrated into the CI/CD pipeline and automates the process of continuous scanning of the codebase or source code.
It utilizes code scanning tools and advanced techniques to assess the codebase. As a result, it helps in identifying vulnerabilities, bugs, data privacy issues, and many other common threats. Most modern tools for code security scanning hold the capability to detect:
- SQLi
- XSS forgery.
- Buffer overflow.
- Authentication management issue.
- Zero-day vulnerabilities.
- Hardcoded secrets
- RCE
Just like any other error assessment tool, code security scanning helps in uncovering all the potential vulnerabilities in the code before they are committed. In 2025, attackers are using advanced techniques to exploit code vulnerabilities, secret exposure, and misconfiguration to gain access.
Nowadays, a lot of developers rely on AI code editors to generate code, and this increases the chance of vulnerabilities and security threats in the codebase. Thus, proactive code security scanning has become a necessity for every team.
Primary Components of Code Security Scanning
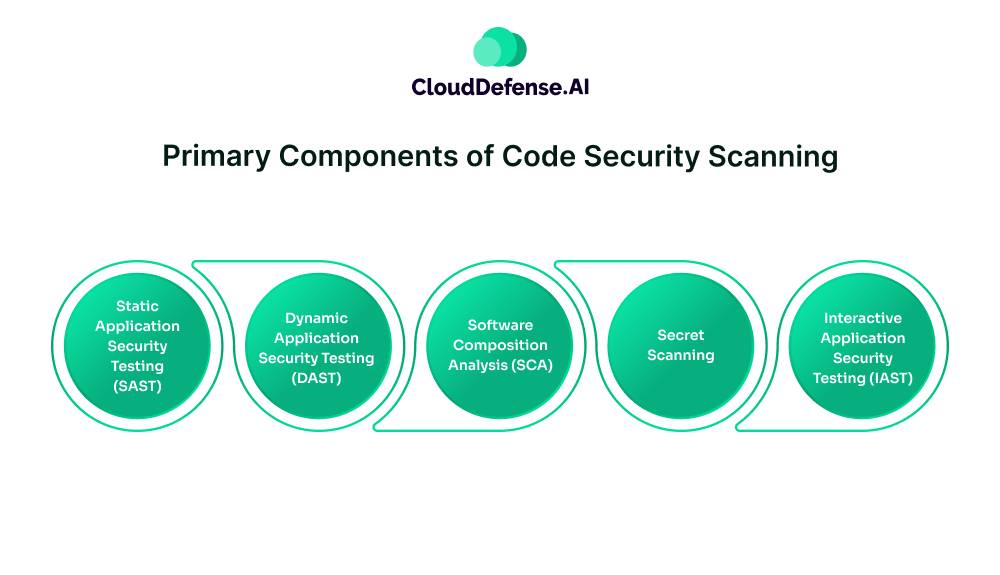
Modern code security scanning is a comprehensive approach that combines multiple code scanning tools to identify all the security threats in the codebase. Tools like SAST, DAST, SCA, IAST, and Secret Scanning serve as the foundation of the code security scanning approach.
Each tool has specific benefits and has significantly advanced through the infusion of AI and ML.
- Static Application Security Testing (SAST) – The SAST tool is a key pillar of all code scanning pipeline approaches. It thoroughly analyzes the source code and binary code without executing them. Modern SAST tools like QINA Clarity AI integrate into the CI/CD pipeline to identify vulnerabilities in the code before they are committed. It not only identifies threats like SQLi, XSS, or validation issues but also eliminates false positives.
- Dynamic Application Security Testing (DAST) – DAST tools utilize blackbox testing methodology where it assess a running application by simulating attacks. It focuses on runtime behavior to identify vulnerabilities in the codebase that may have been missed by SAST. AI-powered DAST tools can even assess the underlying structure and simulate advanced attacks to uncover many unknown threats. It is useful for uncovering misconfigurations, authentication issues, and vulnerabilities in third-party components.
- Software Composition Analysis (SCA) – SCA is an automated process that analyzes and identifies dependencies and open-source components that are part of application development. It examines all the findings against vulnerability databases to identify all the security threats. It performs analysis not only to assess code security but also code quality and supply chain risk.
- Secret Scanning – It is an automated security scanning process that identifies secrets such as API keys, access tokens, and other sensitive information within the code repositories. It is a continuous security practice that minimizes unauthorized access to resources that can originate from unintentional exposure of secrets.
- Interactive Application Security Testing (IAST) – IAST analyzes the codebase of an application to identify and manage vulnerabilities within the application. It analyzes the code while the application is running through automated tests. It combines the capabilities of SAST and DAST to uncover vulnerabilities in real-time. A speciality of IAST is that it conducts context-aware scanning to provide accurate and immediate information. It plays a major role in code security scanning as it can identify exact vulnerable code lines.
Why is Code Security Scanning Important?
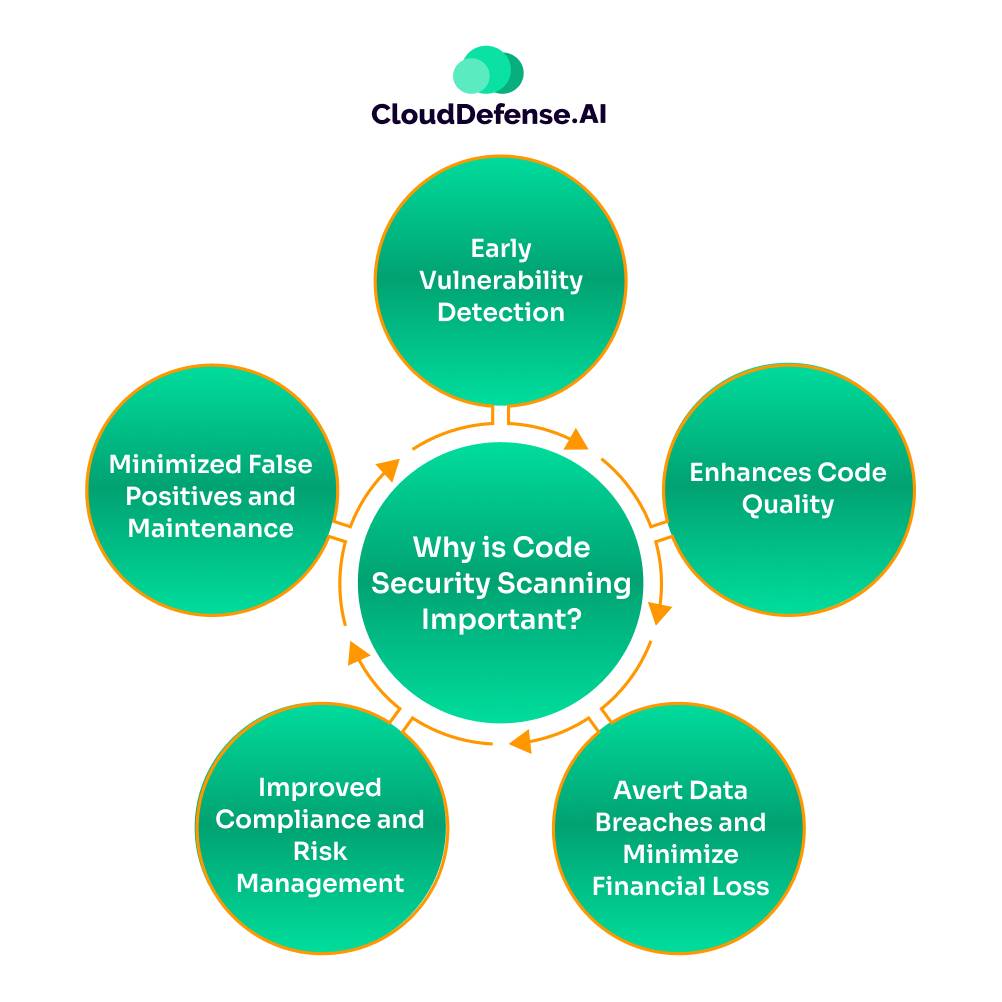
With time, application development is getting more complex, and the need for a faster dev cycle is also increasing. Thus, code security scanning becomes inevitable for every developer. It helps them in identifying and fixing all types of security issues in the codebase or source code.
Here are some key reasons that make it important:
- Early Vulnerability Detection: Code security scanning by integrating early in the CI/CD pipeline continuously assesses the codebase and source to identify security threats. It utilizes different code scanning pipeline tools to find and fix vulnerabilities in the development phase so that it doesn’t reach the deployment stage.
- Enhances Code Quality: The code scanning doesn’t uncover vulnerabilities, but it also assesses the code quality in the pipeline. It helps developers identify issues like poor code designs, unused code, duplicate functions, code with outdated dependencies, and others. Invariably, it helps in promoting DevSecOps culture in the development workflow, making everyone responsible for code security.
- Avert Data Breaches and Minimize Financial Loss: Security flaws in the code have a significant impact, as a security breach leads to huge financial loss. Code security scanning continuously looks for security threats in the code and associated dependencies. It prevents all the security threats from reaching deployment environments and saves the organization from millions in settlements and regulatory fines.
- Improved Compliance and Risk Management: Continuous scanning of the codebase in the CI/CD pipeline helps the organization meet most regulatory industries. From GDPR and SOC 2 to ISO27001, it provides all the necessary compliance logs for auditing. Thus, it makes sure the organization’s code security is always aligned with regulatory requirements.
- Minimized False Positives and Maintenance: Code security scanning combines SAST, DAST, and many others. Modern SAST tools like QINA Clarity AI utilize intelligent threat prioritisation through a 4-stage process and highlight which alerts are false positives. Importantly, an automated scan also ensures that all the code changes are continuously checked and there is no risk associated with their dependence on libraries.
Best Practices for Code Security Scanning in 2025
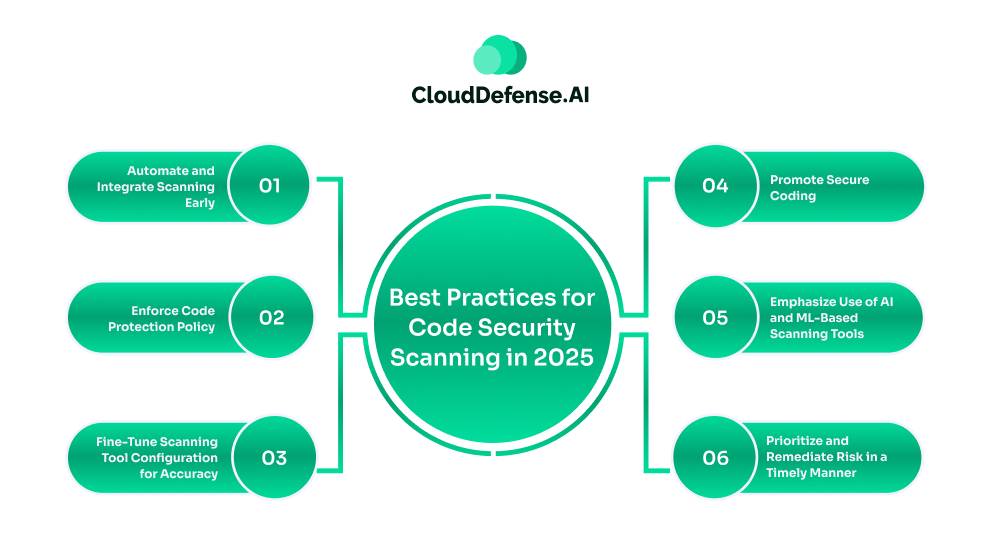
To ensure effective code security scanning, organizations need to properly execute it. Proper implementation of best practices will not only ensure seamless code scanning for vulnerability but also enhance the dev cycle and reduce false positives.
Here are some of the best practices that will maximize the effectiveness of code security scanning:
Automate and Integrate Scanning Early
Security teams should automate security checks for every code commit, pull/merge request, and release. Tools like QINA Clarity AI are lightweight and fast, and quickly scan code during pre-commit or before it is merged.
Automation will ensure all the code scanning in GitHub and other third-party sources is consistent and scalable. It helps in catching vulnerabilities without interrupting the dev workflow. Organizations should integrate code scanning tools in the testing phase for deeper analysis of the code security.
Enforce Code Protection Policy
Organizations, in association with security experts, should create and enforce a code protection policy. The policy should define how, the number of times, and when the source code should be scanned.
The policy must also indicate which roles the code scan should run and who will have the authorization to access the codebase in the CI/CD pipeline. An organization can also implement policy as code, which will prevent developers from committing code with critical vulnerabilities.
Fine-Tune Scanning Tool Configuration for Accuracy
When it comes to code security, teams should fine-tune all the code scanning tools at regular intervals. All the tool’s configuration should be fine-tuned at every interval to comply with the organization’s code security policies, sensitivity settings, and risk priorities.
Security teams can add exceptions and whitelists depending on security policies and define specific rules. Regularly adjusting the configuration will not only help better code security but also reduce false positives and yield accurate results.
Promote Secure Coding
Developers should be empowered and trained to follow secure coding practices and foster a developer-first culture. Every developer must be trained to follow secure coding principles that will significantly minimize the chance of vulnerabilities in the codebase.
Security teams must embed code security scanning tools in the IDE that will provide real-time code scanning and feedback regarding the code. It will also help them in remediating vulnerabilities as they code without switching the IDE. Developers should be encouraged to commit clean code and share code security responsibility.
Emphasize Use of AI and ML-Based Scanning Tools
As the number of threats is increasing, traditional code scanning tools won’t be able to cope. Organizations should emphasize using ML and AI-based scanning tools that can go beyond standard vulnerability databases and identify zero-day attacks.
An organization integrating SAST into a CI/CD pipeline can consider QINA Clarity AI, which is a next-gen AI SAST. It performs advanced vulnerability scanning in the codebase and provides a prioritized security alert, eliminating all false positives.
It provides alerts along with contextual information to the IDE to prevent developers from committing flawed code. An organization can utilize a specialized platform that will consolidate all the security findings from different scanning tools and provide a unified view.
Prioritize and Remediate Risk in a Timely Manner
Developer and security teams should address all the security risks, especially high-impact alerts, as quickly as possible. According to reports, a lot of security alerts are often overlooked and lead to severe risks.
Modern code scanning pipeline tools provide developers with remediation steps containing contextual information and options to automate remediation processes. Developers should capitalize on such tools to quickly remediate the issues and keep the codebase from threats.
Bottom Line
In 2025, secure code scanning has become an indispensable part of the modern application development process. It introduces code scanning early, providing early vulnerability detection, compliance alignment, and code quality improvement.
Proactive scanning across CI/CD pipelines through AI-based code scanning tools will help organizations to drastically reduce vulnerabilities in the codebase. Organizations should focus on integrating their code security scanning approach with AI-based tools, which will enhance the overall security posture of the development environment.







