What Is Vulnerability Scanning in Cybersecurity?
Vulnerability scanning is the process of scanning your digital infrastructure to identify any weak spots (vulnerabilities) that can be an entry point for threat actors. The scans are carried out through software known as vulnerability scanners.
Key Functions of Vulnerability Scanning:
- Identifies Vulnerabilities: Detects weak points in systems and applications.
- Prioritizes Risks: Helps organizations focus on the most critical vulnerabilities.
- Automates Assessment: Streamlines the scanning process for efficiency.
- Enhances Security Posture: Provides insights to strengthen network defenses.
- Facilitates Compliance: Aids in meeting industry regulations and standards.
By regularly conducting vulnerability scans, organizations can proactively address potential threats, minimizing the risk of exploitation and ensuring a more secure network environment.
| Read more: Do you wish to learn more about vulnerability management? Read our exclusive article about Vulnerability Management. |
What Are Security Vulnerabilities?
Building on the insights gained from vulnerability scanning, it’s essential to understand what security vulnerabilities are. Simply put, security vulnerabilities are flaws or weaknesses in software, hardware, or processes that could be exploited by attackers. These weaknesses can stem from coding errors, misconfigurations, or even outdated systems.
Types of Security Vulnerabilities:
- Software Bugs: Mistakes in code that can be exploited.
- Misconfigurations: Incorrectly set security settings that create risks.
- Unpatched Software: Programs that haven’t been updated to fix known flaws.
- Weak Passwords: Easily guessable passwords that provide easy access.
- Human Error: Mistakes made by users, such as clicking on malicious links.
| Read more: Don’t leave your systems vulnerable! Read about the top misconfigurations that could put your organization at risk. |
Why Vulnerability Scanning is Crucial?
Often, hackers are quick to identify weaknesses in a system, giving them the upper hand and leaving businesses scrambling to respond. This is why adopting a proactive security stance is essential.
To tackle these challenges head-on, many IT teams implement vulnerability management programs. These programs are all about continuously identifying and fixing security risks before they can be exploited. Vulnerability scanning is typically the starting point in this journey, shining a light on the weak spots that need attention.
Here’s why vulnerability scanning tools are an essential part of your company’s cybersecurity strategy:
Spotting Weaknesses Early: Regular scans help catch vulnerabilities before attackers do. This proactive approach means businesses can fix issues before they become major problems.
Validation of Security Measures: After teams implement new security measures, running a follow-up scan is a smart move. It not only verifies that vulnerabilities are patched but also ensures that new changes haven’t unintentionally created other issues.
Prioritizing What Matters: Vulnerability scanning helps organizations focus on the most critical risks, making it easier to allocate resources where they’re needed most.
Building a Stronger Defense: By staying on top of vulnerabilities, companies can develop strategies to quickly respond to potential attacks, helping to minimize damage.
Meeting Compliance Requirements: Many industries have specific regulations that mandate regular vulnerability assessments, making scanning not just a best practice but a legal necessity.
Saving Costs: From allotment of resources for damage control to legal damages from customers suing the company, a single vulnerability in your environment can be fatal. Vulnerability scanning, however, helps save your company money as well as time. As per the report by IBM, companies that use security tools can save up to $1.76 Million.
What are the Common Issues Uncovered by Vulnerability Scanning
When a vulnerability scan is run, it dives into several layers of your digital environment to detect weak points. Here are some of the critical areas that scans often expose:
Network Access Points and Entry Routes
A scan will look at access points in your network to detect issues like unsecured open ports, loose access permissions, and overlooked connections. Identifying unauthorized devices and strengthening firewall configurations help close gaps that attackers might exploit.
Device and System Health
Outdated software versions, unpatched systems, and insecure operating system setups are common risks. Vulnerability scans identify these weak spots, focusing on system configurations and any software left exposed to known threats.
Code Vulnerabilities and Application Layers
Applications often contain vulnerabilities in their underlying code. Scans identify issues like unprotected API endpoints, coding flaws, and misconfigured security settings that might allow for data manipulation or injection attacks. With application-specific scans, even hidden risks in backend code or user interfaces are brought to light.
Cloud Infrastructure and Permissions Management
Cloud settings can expose sensitive data if left unprotected. Scans check for misaligned user permissions, inadequate identity access management, and settings that may expose data to unauthorized users or excessive access within cloud-based resources.
Scan-Specific Focus Areas
Different types of scans—such as those focused on networks, applications, or specific databases—reveal distinct risk areas. Network scans might flag rogue devices, while application scans delve into software logic flaws. Additionally, internal scans often target insider threats, while external scans address vulnerabilities visible from outside the network.
Different Types of Vulnerability Scans
When it comes to safeguarding your organization, understanding the different types of vulnerability scans is crucial. But what are they, and how do they work?
Active Scanning
Think of this as a hands-on approach. Active scanning sends direct requests to your systems, probing for vulnerabilities. It digs deep, revealing details about open ports and services that might be misconfigured. The catch? It can slow things down and use bandwidth, so it’s best suited for periodic checks rather than constant monitoring.
Passive Scanning
Now, what if you want to keep things low-key? That’s where passive scanning comes in. This method observes network traffic without poking at the systems directly. It picks up on outdated software or insecure connections just by watching data flow. The bonus? It can run continuously without impacting system performance. However, it might miss some internal issues that aren’t visible through network traffic alone.
Internal Scanning
Internal scans are all about your organization’s internal network. They shine a light on vulnerabilities that internal threats could exploit—think of compromised employees or lurking malware. By checking out devices and applications behind your firewall, internal scans help uncover risks that external scans might miss.
External Scanning
What about the threats coming from the outside? External scanning focuses on systems that face the internet, like web servers and cloud services. This type of scan looks for vulnerabilities that external attackers could exploit. It’s critical for understanding how exposed you are to online threats.
Authenticated Scanning
Want a more detailed picture? Authenticated scanning uses administrative credentials to access systems. This deeper analysis can reveal vulnerabilities in configurations and permissions that unauthenticated scans might overlook. It’s all about getting the full scoop on potential security issues.
Unauthenticated Scanning
On the flip side, unauthenticated scanning simulates an outsider’s perspective. It checks for visible vulnerabilities without needing login credentials. While it can highlight issues like open ports, it might not catch deeper problems tied to user permissions. So, it provides valuable insights but isn’t as comprehensive as authenticated scans.
API Scanning
This type of scan is dedicated to evaluating the security of APIs. APIs often serve as gateways to an organization’s data and services, making them prime targets for attackers. API scanning tests for vulnerabilities like improper authentication, insecure data exposure, and insufficient rate limiting. Unlike general external scanning, API scanning dives into how well APIs handle requests and data transactions, ensuring they are secure against potential exploitation.
How Does Vulnerability Scanning Work?
Vulnerability scanners run automatically by first making an inventory of all assets connected to a network. This inventory map contains the device ID and each device’s operating system on the network, which is further analyzed to pinpoint probable vulnerabilities.
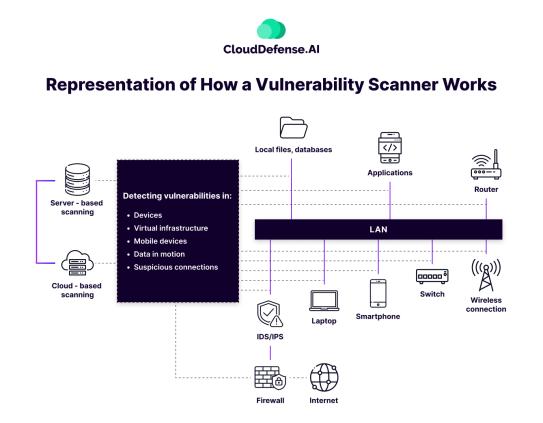
Vulnerability scanners are connected to a database of known vulnerabilities that they use to check for all the weaknesses in your system. The continuous process of scanning for vulnerabilities, identifying them, and then patching them up is cumulatively known as Vulnerability Management.
Vulnerability scanning can be carried out in two ways, depending on what infrastructure the company is using.
- Server-Based Vulnerability Scanning involves assessing and identifying security weaknesses within the infrastructure of an individual server or a local network. It typically relies on on-premises solutions and tools to scan and analyze system configurations, applications, and services for potential vulnerabilities, providing insights into areas that require patching or remediation.
- Cloud-Based Vulnerability Scanning extends the scanning process to cloud environments. Leveraging online tools and services, it assesses the security posture of virtual machines, cloud servers, and associated services. It offers a scalable and dynamic approach to identifying and addressing vulnerabilities within cloud-based infrastructures.
The Vulnerability Scanning Process
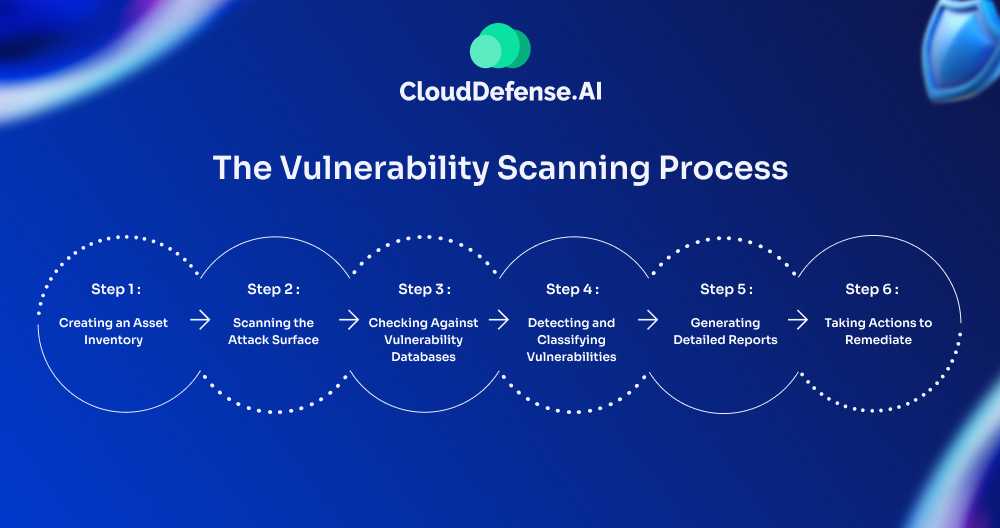
Vulnerability scanning process isn’t just a one-time task; it’s a continuous process that helps organizations stay on top of new threats and vulnerabilities.
But how does it actually work? Let’s break it down step by step.
Step 1: Creating an Asset Inventory
It all starts with taking inventory. Think of this as your security foundation—a scanner maps out every device linked to your network. It picks up on operating systems, software, open ports, and user accounts, giving you a full picture of what’s in your environment. This inventory is essential because knowing exactly what’s on your network is the first line of defense.
Step 2: Scanning the Attack Surface
Once everything is mapped out, the scanner gets to work probing your network, devices, and software. Imagine this as a security sweep, looking for any cracks or potential entry points an attacker could exploit. The goal here is to identify risks early—before they turn into real problems. This way, you can address vulnerabilities proactively.
Step 3: Checking Against Vulnerability Databases
After the initial sweep, the scanner starts comparing its findings against trusted vulnerability databases, like the Common Vulnerabilities and Exposures (CVE) list. This step helps pinpoint specific risks by matching known vulnerabilities with the assets in your inventory. If there’s a path leading to sensitive data, this cross-check will flag it, making sure nothing is left exposed.
Step 4: Detecting and Classifying Vulnerabilities
With the vulnerabilities identified, the scanner then classifies them based on severity. It highlights areas where hackers could strike, giving you a sense of what needs immediate action. This step is key because it’s not just about spotting risks but understanding which ones require your urgent attention.
Step 5: Generating Detailed Reports
After completing the scan, the scanner generates a set of reports that lay out its findings in clear detail. These reports don’t just tell you what’s wrong; they guide you on how to fix the issues, helping your team prioritize which vulnerabilities to tackle first. Think of these as your roadmap for closing security gaps.
Step 6: Taking Actions to Remediate:
Now, with the insights from your scanner’s reports, it’s time to take action. This might mean applying patches, updating software, adjusting configurations, or even adding new security layers. Each step brings your organization one step closer to a stronger, more resilient defense, sealing off vulnerabilities before attackers can find them.
Example Of Vulnerability Scanning
Let’s consider a simple example to understand what a comprehensive vulnerability scanning process looks like. Let’s imagine TechCo, a growing tech company, recently moved a lot of its operations to the cloud.
To keep its sensitive data safe, the IT team decides it’s time for a vulnerability scan. They start by using a scanner to take stock of everything connected to their network—like identifying all the devices and checking which operating systems and software are in use.
As the scanner works, it explores TechCo’s network and cloud services, looking for any weak spots where attackers might sneak in. It then checks against a list of known vulnerabilities and flags a few outdated software versions that could be risky.
After this, the scanner puts together a report highlighting the vulnerabilities and suggests how to fix them. The IT team reviews the report, rolls up their sleeves, and gets to work applying the necessary patches and updates.
With this proactive approach, TechCo strengthens its defenses and feels more secure against potential threats. And by making vulnerability scanning a regular habit, they stay ahead of any new risks that pop up.
| Read More: Consider reading our article on building a vulnerability management program next to get more insight into threat mitigation. |
Difference Between Vulnerability Scanning and Penetration Testing
Penetration testing is another method used to find vulnerabilities in a system. However, some differences help in telling it apart from vulnerability scanning.
| Vulnerability Scanning | Penetration Testing | |
| Purpose of The Tool | Vulnerability scanning simply works as a security tool that helps scan for any system vulnerabilities. | Penetration testing imitates an actual cyber attack to identify any vulnerabilities that can be used to bring harm to the system. Penetration testing also helps judge the amount of damage a hacker can cause. |
| Scope of the Tool | A vulnerability scanner uses a database of known vulnerabilities and marks all the entry points in your system based on their severity. | Penetration testing has a broader scope as it allows you to create a cyber attack comprising several different attack methods manually. |
| Is Automation Available? | Yes, automation is available. It is very effective in carrying out routine check-ups of your system. | Yes, automation is available; however, a large portion of the testing requires you to create the scenarios manually. Effective penetration testing requires manual intervention over automation. |
| Reporting Capabilities | Provides a report with all the identified vulnerabilities, their severity, and tips for mitigating them. | Provides a more detailed report, including what methods were used to carry out the attack. |
How Frequently Should You Scan Your Systems?
The frequency of system scans should align with your company’s risk tolerance, compliance requirements, and the dynamic nature of your IT environment. Regular automated scans, conducted daily, weekly, or monthly, help identify known vulnerabilities. Critical systems or those in high-risk environments may require more frequent analysis.
Companies should scan after significant changes, comply with industry regulations, and adapt to emerging threats. Continuous monitoring tools and a risk-based approach ensure an active stance against evolving security challenges. You can tailor the scanning frequency to balance security needs with available resources, promoting a resilient and adaptive security posture.
Essential Features to Look for in a Vulnerability Scanning Tool
When it comes to choosing the best vulnerability scanning tool, it’s essential to look for features that will effectively enhance your security posture and streamline the scanning process. Here are some crucial elements to consider:
1. Continuous Vulnerability Monitoring
A top-notch vulnerability scanning tool should provide continuous monitoring capabilities. This feature ensures that new vulnerabilities are detected as they arise, allowing your organization to stay ahead of potential threats and maintain a secure environment at all times.
2. No Agent Installation Required
Consider selecting a tool that operates without requiring the installation of agents on your systems. An agentless approach simplifies deployment and reduces the overhead on system resources, while also eliminating potential compatibility issues that can arise with agent-based solutions.
3. Prioritization Based on Risk
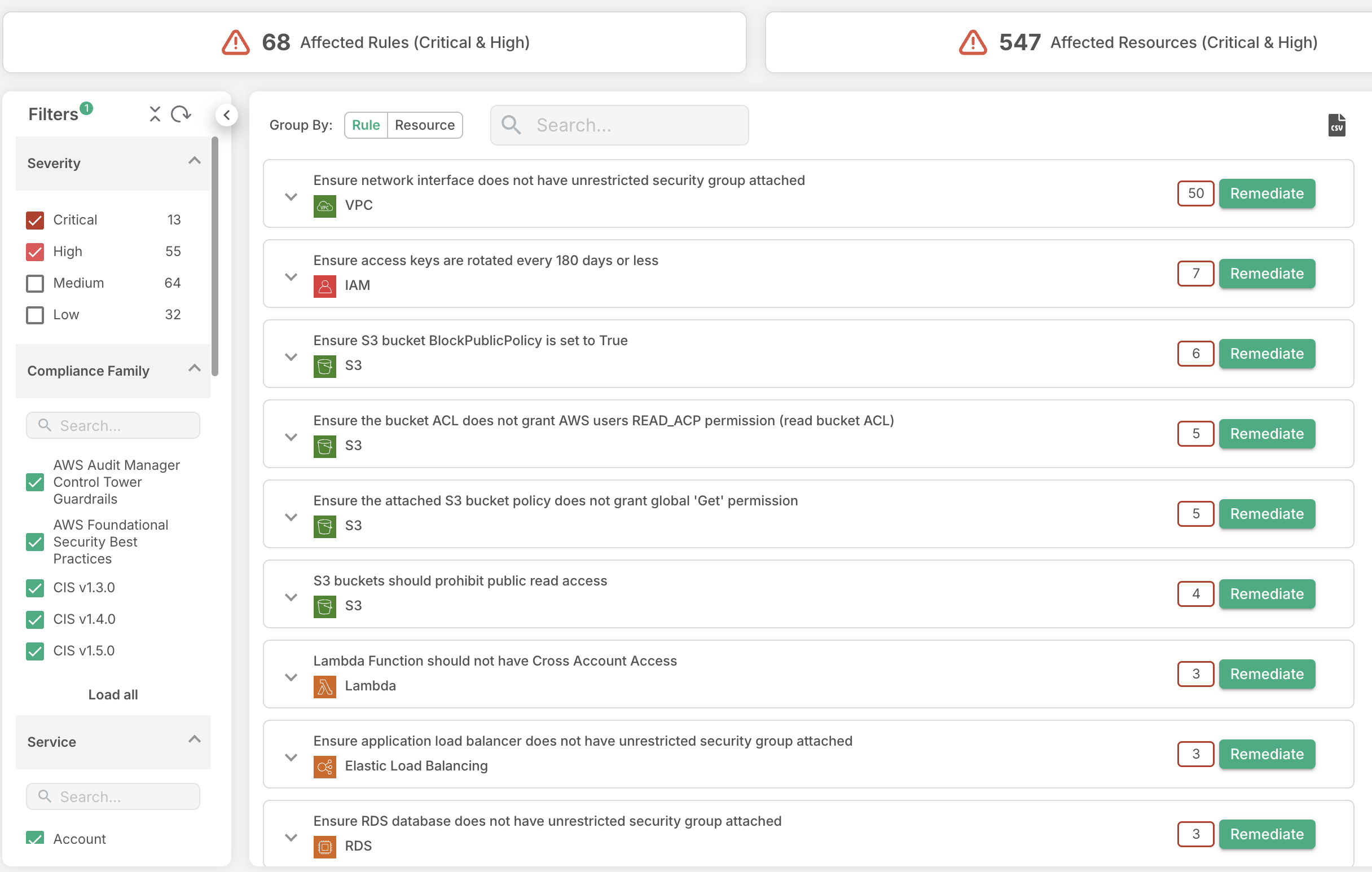
Look for tools that offer risk-based prioritization for vulnerabilities. This means the tool evaluates vulnerabilities not only by their severity but also by factors like potential exploitability and the criticality of the affected assets. Such a feature helps your team focus on the vulnerabilities that pose the greatest risk, minimizing alert fatigue in the process.
4. Versatile Multi-Cloud Support
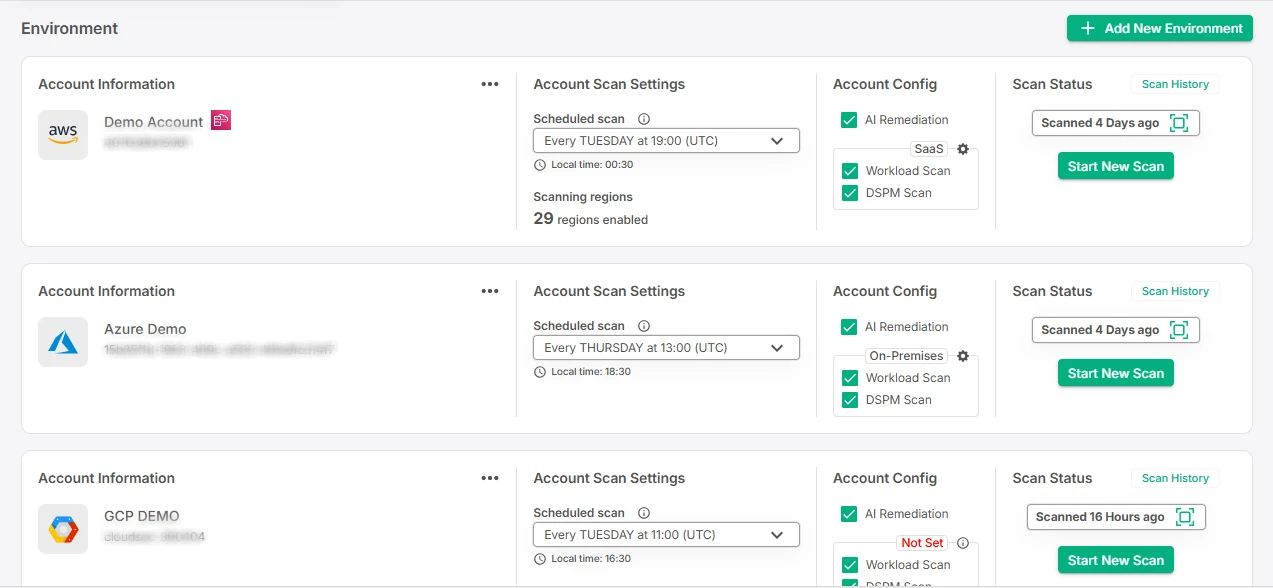
As environments become more complex and hybrid, it’s essential to choose the best vulnerability management tool that can seamlessly work across different technologies and cloud platforms. A versatile tool should be capable of scanning assets in various cloud environments—like AWS, GCP, and Azure—regardless of the underlying operating systems or programming languages in use.
5. Comprehensive Reporting
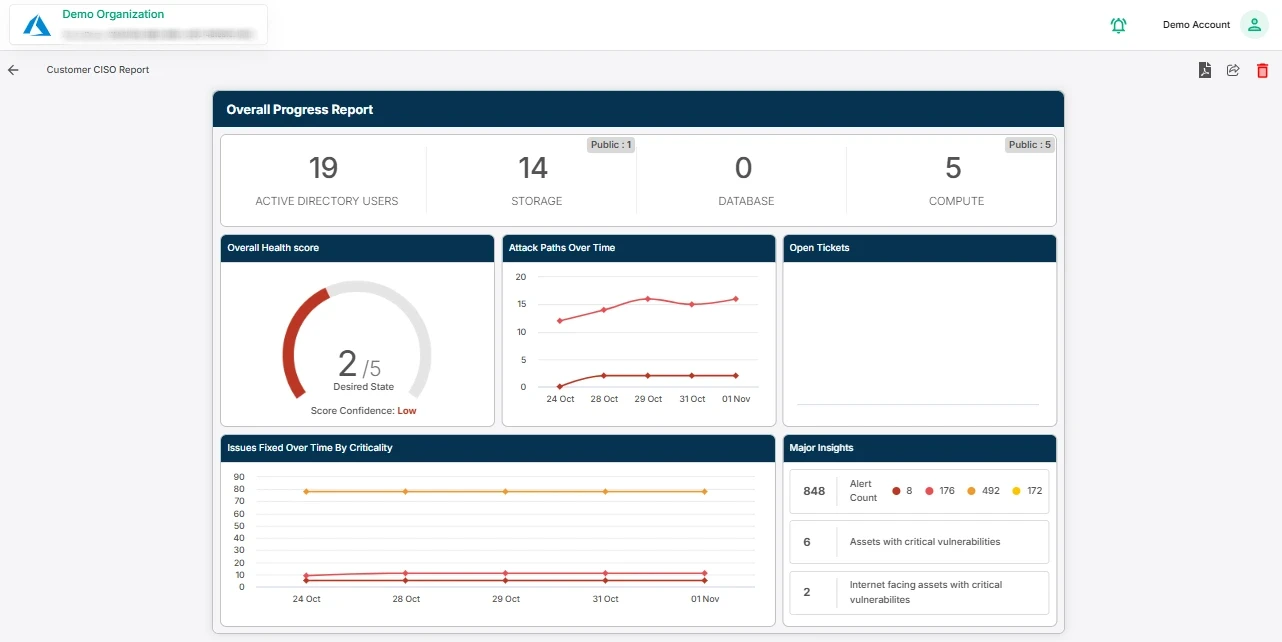
A reliable vulnerability scanning tool should generate comprehensive reports that not only highlight identified vulnerabilities but also provide context around them. These reports should detail the potential impact of each vulnerability, helping your team understand the urgency and importance of remediation efforts.
6. Automated Remediation Guidance
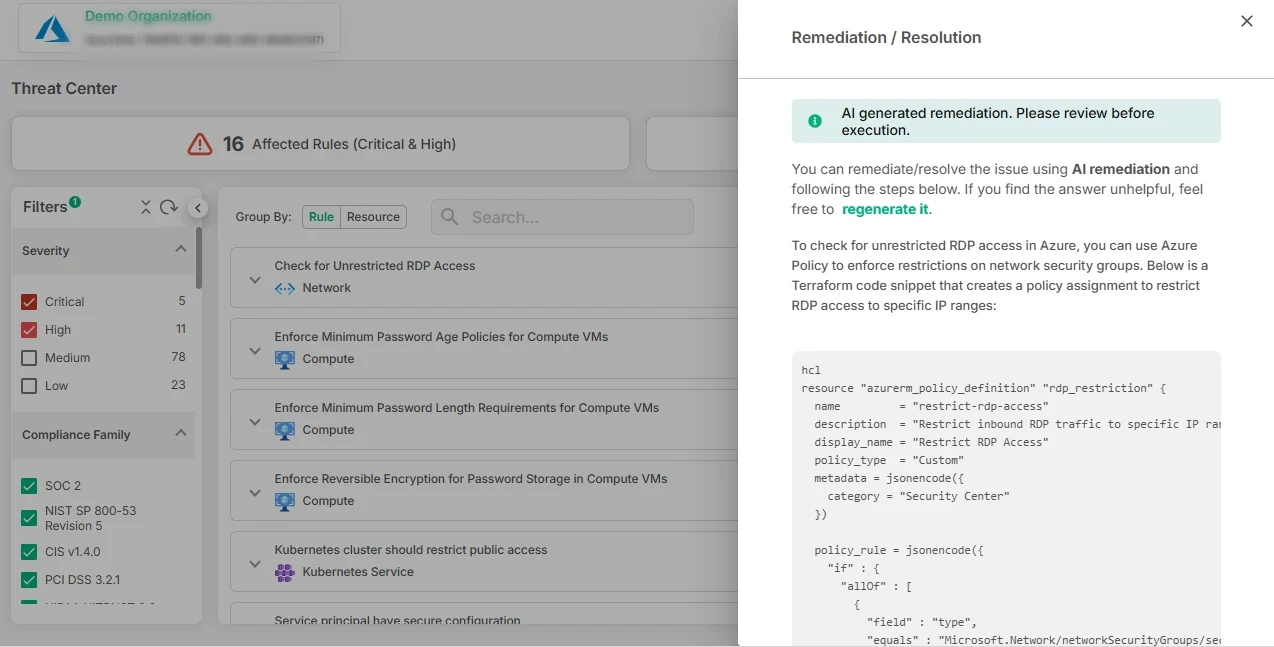
Look for tools that offer automated remediation guidance alongside their findings. This feature streamlines the process of addressing vulnerabilities by providing actionable steps that teams can follow to resolve issues quickly and effectively, ultimately enhancing your security management efforts.
7. Contextual Graph-based Analysis for Better Understanding
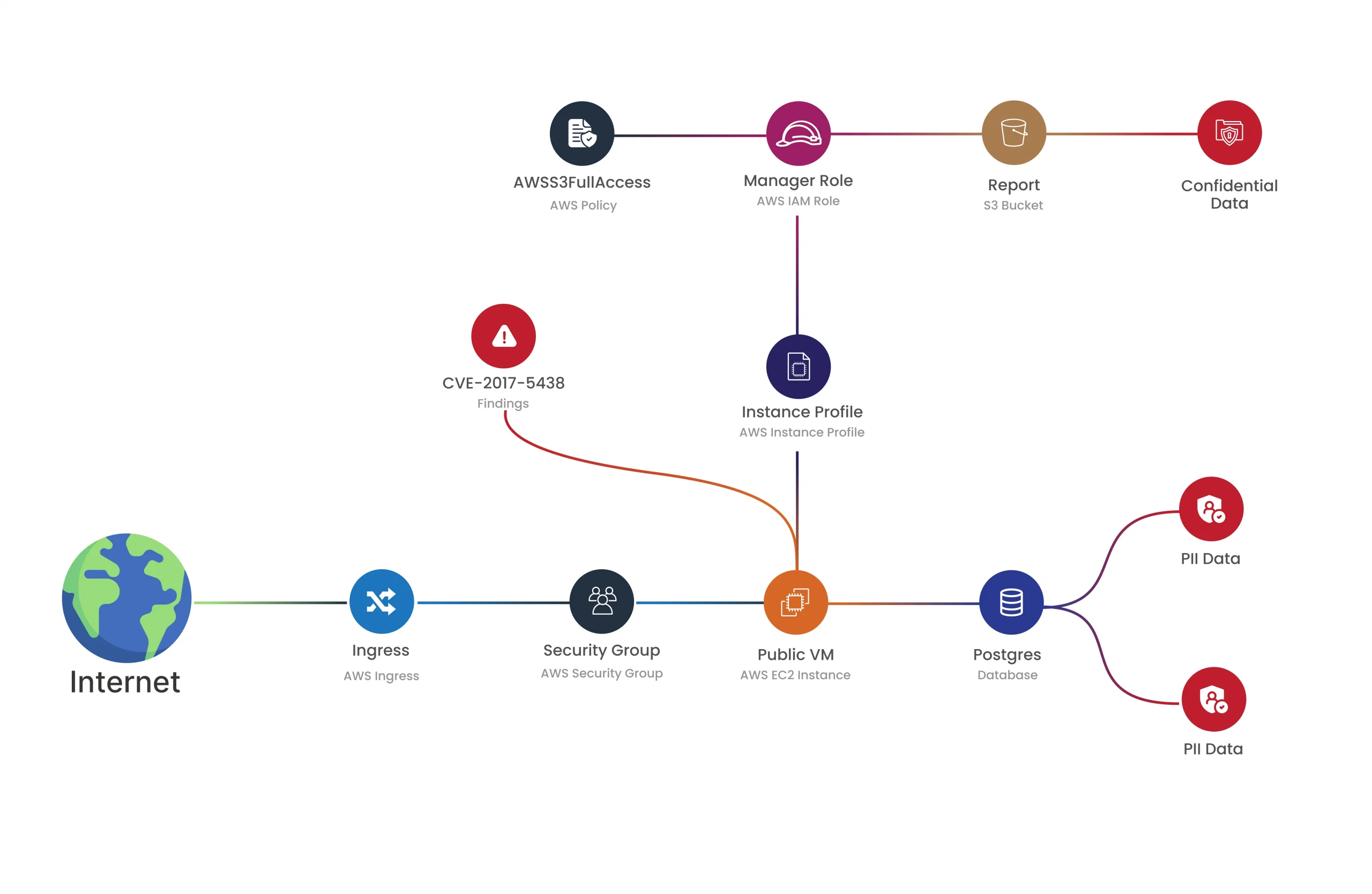
Another outstanding feature to look for is contextual graph-based analysis, which visually maps out the relationships between various assets and vulnerabilities. This would be able to give a clear intuitive sense of how the elements in your environment interact and will highlight the risk paths or areas of concern that could be of interest to the organization.
By visualizing vulnerabilities in the context of your network architecture, your team can make more informed decisions regarding prioritization and remediation strategies.
Wrapping up: CloudDefense.AI’s Approach to Vulnerability Scanning
If you’re looking for a comprehensive solution that encompasses all the key features outline above for effective end-to-end vulnerability management, look no further than CloudDefense.AI’s Vulnerability Management tool. This powerful tool offers:
Agentless Scanning: Operates seamlessly across various cloud environments without the need for installing agents.
Comprehensive Detection: Utilizes multiple updated vulnerability databases and public sources to ensure accurate and current vulnerability identification.
Broad Coverage: Scans both cloud resources and code repositories without requiring elevated privileges, making it user-friendly.
Contextual Risk Prioritization: Prioritizes vulnerabilities based on contextual risk factors, such as, external exposure and cloud entitlements
Attack Path Analysis: CloudDefense.AI provides detailed attack path analysis to visualize potential routes that an attacker might take to exploit vulnerabilities. This feature helps in understanding the broader implications of identified vulnerabilities and planning effective mitigation strategies.
However, a scan is only the starting point. CloudDefense.AI’s comprehensive CNAPP not only identifies vulnerabilities within your cloud and application infrastructure but also guides you through the entire remediation process. This lets you improve your defenses and make sure your systems are safe end to end.
So, are you ready to enhance your overall security posture? Book a free demo today to see how CloudDefense.AI can redefine your vulnerability management approach!







