What is Attack Path Analysis (APA)? Attack Path Analysis Explained
Attack path analysis offers a visual representation of the routes attackers can exploit to navigate both on-premise and cloud environments. These “paths” enable malicious actors to access sensitive data by using vulnerable configurations or resources.
In large enterprises, the number of potential attack paths can be overwhelming. However, by utilizing attack graphs, security teams can gain real-time insights into risks and understand how compromised resources could impact the broader network.
Most security teams are effective at quickly identifying and remediating attack paths, with 75% of exposures found to be non-exploitable dead ends. Choke points, where multiple attack paths converge, are key areas to monitor, as they often lead to sensitive data.
These chokepoints simplify threat detection by allowing centralized logging and the establishment of baseline behaviors, helping teams to identify and investigate anomalies efficiently.
By visualizing these attack paths, you can:
- Fix the potential vulnerabilities before attackers find them.
- Focus your defenses on the most critical areas.
- Predict and prevent the next cyberattack.
It’s not just about finding vulnerabilities, but understanding how they connect and can be exploited – making your network and its resources much harder to reach.
Attack Path vs. Attack Vector vs. Attack Surface
| Aspect | Attack Path | Attack Vector | Attack Surface |
| Definition | The specific route an attacker follows to exploit vulnerabilities and navigate a system. | The method or technique used by attackers to gain initial access. | The total number of potential entry points or vulnerabilities in a system. |
| Focus | Steps taken to move through and escalate within a system. | How attackers first infiltrate or inject malware into the system. | The overall exposure of a system to attack opportunities. |
| Example | Compromising a low-privilege account, then escalating access to sensitive data. | Phishing emails, malware injection, or software exploitation. | Unsecured APIs, exposed databases, or unpatched software. |
| Purpose | To map the sequence of actions attackers take, identifying key vulnerabilities. | To highlight the attacker’s initial entry method. | To assess and reduce the number of exploitable vulnerabilities in a system. |
| Mitigation Approach | Analyzing and disrupting potential attack paths before they are exploited. | Securing entry points and preventing common attack methods. | Minimizing the number of exposed services, applications, and devices. |
While they all relate to cybersecurity vulnerabilities, attack paths, attack vectors, and the attack surface have distinct meanings:
What is an Attack Path?
An attack path refers to the specific sequence of steps an attacker takes to exploit vulnerabilities and navigate through a system or network. It maps the journey of an attacker, from initial access to the ultimate target, highlighting how various weaknesses can be chained together to achieve their goal.
What is an Attack Vector?
An attack vector is the technique or method an attacker uses to infiltrate a system. This is the initial point of entry, whether through phishing emails, malware, or exploiting unpatched software vulnerabilities. The attack vector is crucial in determining how attackers first gain access to an environment.
What is an Attack Surface?
The attack surface encompasses the total sum of all potential entry points or vulnerabilities in a system that an attacker could exploit. It includes exposed devices, applications, and any weaknesses that could be targeted. Reducing the attack surface is key to limiting opportunities for malicious actors.
Types of attack path analysis
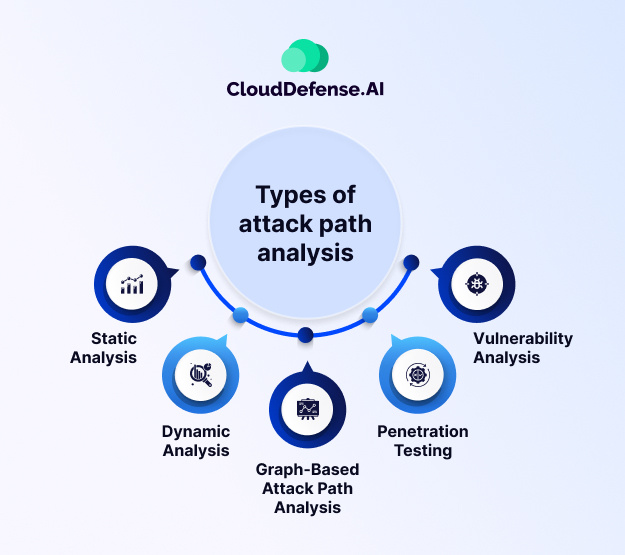
Understanding the ways that attackers can get into your network is very important for keeping it safe. When you analyze attack paths, you look at the various ways someone could find and exploit vulnerabilities to reach critical assets. Here’s a breakdown of common approaches:
- Static Analysis: Static analysis examines code and configurations without actually executing them to find security vulnerabilities that someone could take advantage of. This helps in understanding the inherent vulnerabilities in the system design and dependencies.
- Dynamic Analysis: It involves running the system and monitoring its behavior to detect vulnerabilities that emerge during operation. It complements static analysis by uncovering runtime issues too.
- Graph-Based Attack Path Analysis: It shows the network or system as a graph, where nodes represent assets or components, and lines show how they connect. It provides a holistic visual representation of attack paths, aiding in better understanding and communication of security risks.
- Penetration Testing: Penetration Testing involves ethical hackers simulating real-world attacks, attempting to break in and uncover vulnerabilities. This hands-on approach provides valuable insights into how well your system can defend itself and where it might be attacked.
- Vulnerability Analysis: This method focuses on pinpointing specific vulnerabilities within your systems, such as outdated software or misconfigured settings. When you know what these weak spots are, you can think about how someone who wants to attack could use them to get further into your network.
How does Attack Path Analysis Work?
Many businesses build interconnected systems to enhance functionality and efficiency. However, these connections can create “toxic combinations,” where a vulnerability in one system becomes a gateway to exploit other critical systems. Attack Path Analysis (APA) helps identify, visualize, and understand these potential risks.
Example: IAM Breach and Escalating Access
Consider an Identity and Access Management (IAM) breach. If an attacker gains access to a single user’s credentials, APA would simulate how that breach could evolve into a more significant threat:
- Expanding access: The attacker could use stolen credentials to access internal directories, exploiting misconfigurations to infiltrate a broader user group within IT or security teams.
- Lateral movement: With access to more accounts, the attacker might explore other systems, identifying vulnerabilities to escalate their privileges further.
- Targeting sensitive data: The attacker could aim to steal valuable assets, such as financial data or intellectual property, before detection.
How Does Attack Path Analysis Help?
APA helps prevent such breaches through the following key steps:
- Mapping your network connections: APA visualizes all connections between resources in your cloud environment, creating a comprehensive view of your digital infrastructure.
- Identifying vulnerabilities: It analyzes these connections, pinpointing weaknesses like unpatched vulnerabilities, weak access controls, or misconfigurations.
- Simulating attacker movements: By using these vulnerabilities, APA simulates how an attacker might move through the network, chaining together exploits to form potential attack paths.
- Guiding remediation:
- Patch vulnerabilities before attackers can exploit them.
- Strengthen access controls to limit lateral movement within the network.
- Set up alerts to detect suspicious activities early.
- Implement security measures to block identified attack paths.
Ongoing Protection with APA
Attack path analysis is an ongoing process. As your network grows and the threat landscape evolves, continuous monitoring and updating are essential for effective protection. It’s crucial to maintain the accuracy of your network data and vulnerability assessments for the tool to work optimally.
Choosing the Right Attack Path Analysis Tool
Not all APA tools are the same. Different tools use varying methodologies, so selecting a solution that aligns with your organization’s specific needs and resources is key to maintaining robust security.
By using APA, businesses gain a bird’s-eye view of potential attack routes, enabling them to focus on the most critical areas to defend and actively mitigate risks.
Benefits of Conducting Attack Path Analysis
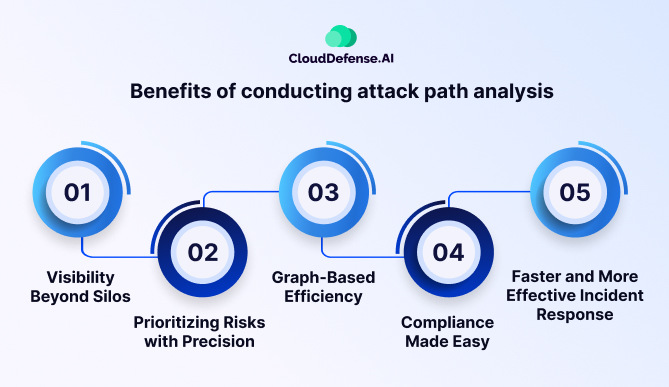
The advantages of attack path analysis go far beyond just identifying vulnerabilities, which makes it a potent weapon for contemporary security teams. Here’s a closer look at the key advantages, including newly added aspects:
1. Visibility Beyond Silos:
Attack path analysis tools illuminate the complex interconnections among vulnerabilities, and misconfigurations and disclose how potential attackers could manipulate these elements to achieve their objectives. This interconnected web visualization helps security professionals spot hidden risks that might go unnoticed in siloed assessments.
2. Prioritizing Risks with Precision:
Cloud environments are dynamic and hence require accurate prioritization of risks. Attack path analysis tools provide risk scoring and utilize node visualization to guide teams toward the most vulnerable points. This way, it simplifies IT and security initiatives efforts to prioritize actions on the mitigation of those threats with the most impact first.
3. Graph-Based Efficiency:
Manually dissecting attack paths can be a bit overwhelming. Graph-based algorithms tackle this challenge by effectively modeling activity and behavior within the cloud environment. They pinpoint critical nodes and potential attack routes, especially in sprawling multi-cloud setups. Visualizing these attack paths on a broader cloud canvas gives you context and a deeper understanding of potential threats.
4. Compliance Made Easy:
Adhering to security regulations can be a complex task. Attack path analysis steps in to provide the insights necessary to showcase compliance to regulators and the public. Since APA helps to seamlessly identify and address vulnerabilities proactively, organizations can steer clear of potential regulatory penalties and safeguard their reputation.
5. Faster and More Effective Incident Response:
When a security incident happens, time is critical. Attack path analysis is a process in which teams formulate incident response plans by predicting probable scenarios of attacks and actions to be taken. This preemptive strategy enables quicker containment, investigation, and recovery, minimizing damage and downtime.
Top Use Cases of Attack Paths
Attack Path Analysis is an essential tool for identifying potential routes that attackers might exploit to compromise a network or system. By using attack path analysis, organizations can gain valuable insights into their security weaknesses across various scenarios, such as:
- Vulnerability Identification: Detect weak points in network structures or infrastructure that malicious actors could exploit.
- Compliance Verification: Demonstrate adherence to regulatory standards by identifying and addressing potential attack paths before they’re exploited.
- Penetration Testing: Simulate real-world attacks to assess the strength of an organization’s defenses and uncover any exploitable vulnerabilities.
- Risk Evaluation: Assess the potential impact of attacks and prioritize the most critical vulnerabilities for remediation.
- Incident Analysis: Investigate the routes attackers used during a breach, guiding the development of stronger mitigation strategies.
- Policy Enforcement: Validate that security policies and access controls are effective by analyzing potential paths attackers could use to bypass them.
- Network Segmentation: Ensure that network segmentation strategies effectively prevent unauthorized lateral movement within the system.
- Security Training: Enhance employee awareness and training by highlighting potential attack paths and risks.
- Third-Party Risk Management: Evaluate potential risks from external vendors and partners integrated into the organization’s network.
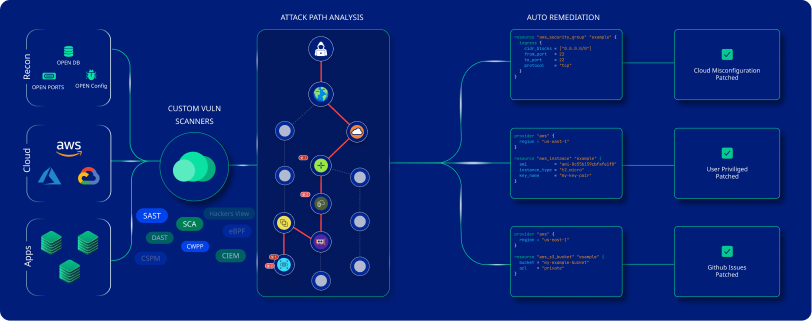
CloudDefense.AI Attack Path Analysis in a Glance
CloudDefense.AI utilizes attack path analysis in a multi-pronged approach to boost your cloud security posture. Here’s how it works and the benefits it offers:
How it does it:
- Mapping your attack surface: CloudDefense.AI meticulously scans your cloud infrastructure, applications, and configurations, identifying all potential entry points and attack vectors. This includes vulnerabilities, misconfigurations, exposed assets, and weaknesses in access controls.
- Building the attack graph: By analyzing the interconnectedness of these vulnerabilities and assets, CloudDefense.AI constructs a comprehensive attack graph. This visualizes the potential pathways attackers could exploit to move laterally within your cloud environment and reach critical data or systems.
- Prioritizing threats: The attack graph doesn’t just show the paths; it also assesses the likelihood and potential impact of each attack scenario. This helps you prioritize remediation efforts, focusing on vulnerabilities that pose the most significant risk based on their exploitability and potential damage.
- Continuous monitoring and updates: CloudDefense.AI doesn’t stop at a one-time analysis. It continuously monitors your environment for new vulnerabilities, misconfigurations, and changes, updating the attack graph in real time. This ensures you always have the most up-to-date picture of your security posture.
How it helps:
- Proactive threat detection: By understanding potential attack paths before attackers do, you can proactively implement security measures to mitigate risks and prevent breaches.
- Prioritized remediation: The attack graph helps you focus your limited resources on the most critical vulnerabilities, maximizing the effectiveness of your security efforts.
- Improved decision-making: Visualizing attack paths provides clear insights into your security posture, enabling informed decisions about security investments and strategies.
- Reduced risk of breaches: Addressing the most exploitable vulnerabilities first, allows you to significantly reduce the likelihood of successful attacks and data breaches.
- Enhanced compliance: Understanding your attack surface and prioritizing vulnerabilities helps you comply with various security regulations and standards.
CloudDefense.AI’s attack path analysis empowers you to shift from reactive to proactive security. By anticipating attacker strategies and prioritizing vulnerabilities, you can significantly strengthen your cloud defenses and stay ahead of evolving threats.







