Given the ever-expanding digital landscape and the increasing reliance on personal devices, cybersecurity has become a paramount concern. From laptops and desktops to tablets and smartphones, these endpoints—access points to a network—are prime targets for cyberattacks.
Here’s where Endpoint Protection Platforms (EPPs) come in as your digital shield. Imagine a comprehensive security suite specifically designed to safeguard these endpoints, acting as a vigilant defender against a multitude of threats. That’s the essence of an EPP—a unified platform that goes beyond traditional antivirus software, offering a layered defense to keep your devices and data secure.
Keep reading as we explore what is an endpoint protection platform in detail and discuss what they are, how they work, and the key features they offer to strengthen your digital security.
What is an Endpoint?
In cybersecurity terms, an endpoint refers to any device that connects to a computer network. These devices act as entry points, allowing users to access and exchange information within the network.
Think about it this way – your desktop computer at work, your personal laptop, that company-issued smartphone, even your tablet at home, they’re all considered endpoints. These access points, if you will, serve as gateways into the broader infrastructure.
And herein lies the problem. As the number of connected devices continues to skyrocket in our increasingly digitized world, the attack surface for crafty cybercriminals has expanded exponentially. Employees working remotely or accessing sensitive data from personal devices only compound the issue, as these endpoints may lack the robust security layers in place within the corporate network.
So you see, these endpoints—they’re the seemingly vulnerable components of cybersecurity. They represent vulnerabilities that malicious actors can exploit to gain that all-important foothold and wreak havoc. That’s why endpoint Protection Platforms have become so paramount in safeguarding organizations against the ever-evolving tactics of cybercriminals.
What is an Endpoint Protection Platform (EPP)?
An Endpoint Protection Platform (EPP) is your one-stop shop for securing the ever-growing army of endpoints in your digital ecosystem. It is a unified suite that combines the strengths of various security tools under one roof. This powerhouse goes far beyond the capabilities of traditional antivirus software, offering a layered defense against a constantly evolving threat landscape.
EPPs act as a shield, safeguarding your devices from malware, ransomware, phishing attacks, and other malicious activities. They employ a multi-pronged approach, including:
- Anti-malware protection: Blocking and removing harmful software like viruses and worms.
- Intrusion prevention: Detecting and stopping unauthorized attempts to access your device.
- Application control: Managing which applications can run on your device, preventing unauthorized software from wreaking havoc.
- Device control: Restricting access to external devices like USB drives to prevent data breaches.
- Data encryption: Securing sensitive information even if your device falls into the wrong hands.
EPPs frequently use cloud intelligence to detect threats as they happen and provide up-to-date information. This ensures that your security measures are constantly improved for dealing with new online risks. Securing all devices from one main place makes the process better and gives important insights about your network’s total condition.
Endpoint Protection Platform (EPP) Features
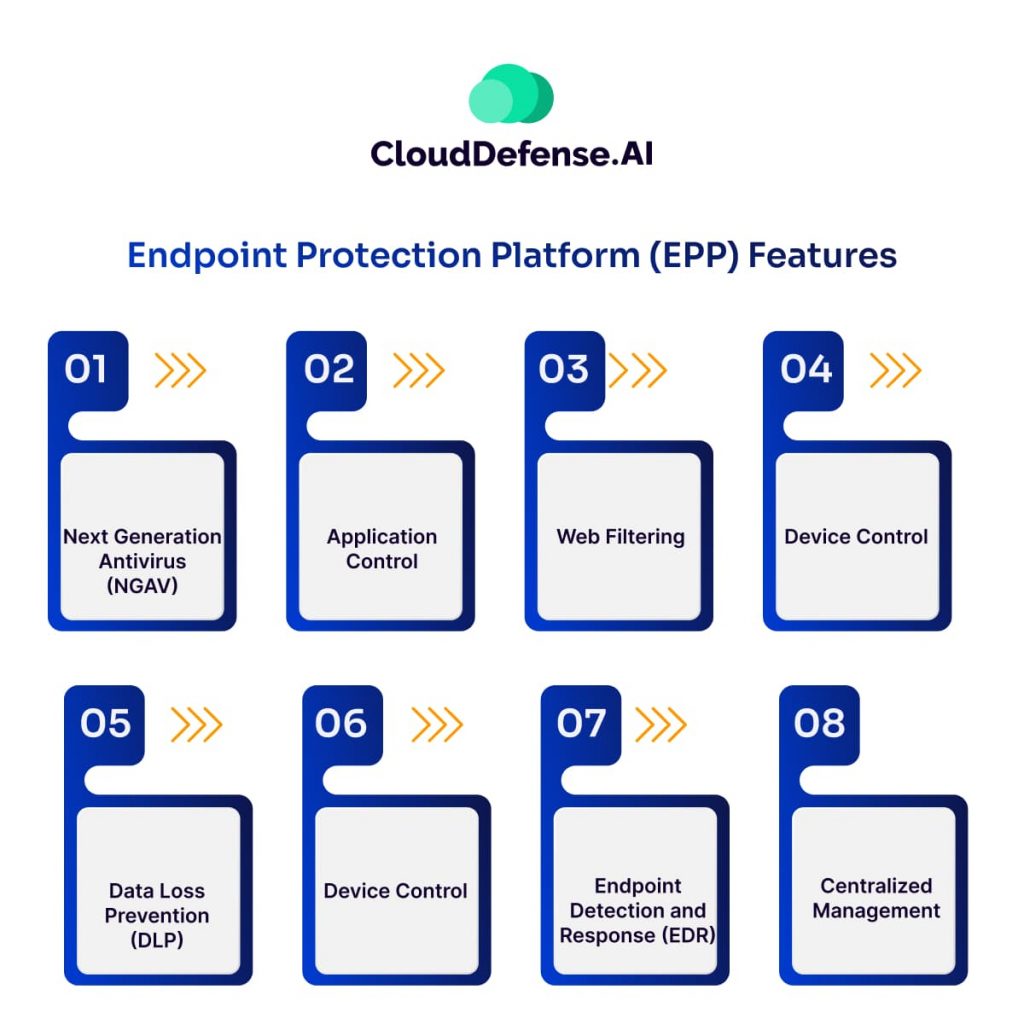
EPPs go beyond basic antivirus protection, offering a comprehensive security toolkit to safeguard your devices. Here’s a breakdown of some key features to look for:
Next-Generation Antivirus (NGAV): Unlike traditional antivirus that relies on signature-based detection, NGAV utilizes behavioral analysis to identify and block even unknown threats like zero-day attacks.
Application Control: EPPs allow you to whitelist approved applications and restrict unauthorized programs from running on your devices. This prevents malware disguised as legitimate software from infiltrating your system.
Web Filtering: By blocking access to malicious websites known for phishing attacks or malware distribution, EPPs help prevent users from unwittingly compromising their devices.
Device Control: EPPs can restrict the use of external devices like USB drives or external hard drives. This helps prevent data breaches or the introduction of malware through removable storage.
Data Loss Prevention (DLP): EPPs with DLP capabilities can recognize and block sensitive data from being moved outside of authorized routes. This stops confidential information from getting out by accident or without permission.
Endpoint Detection and Response (EDR) (often integrated): While not a core feature of all EPPs, EDR capabilities are becoming increasingly important. Even if it is not necessary for every EPP, the feature of EDR has more significance now. EDR does not just find threats, but also provides resources to study doubtful actions, locate why an attack happened and manage response to incidents quickly.
Centralized Management: EPPs provide a central console for managing security across all your endpoints. This simplifies security administration, allowing you to deploy policies, monitor device health, and manage updates from a single platform.
EPP vs. EDR: Understanding the Difference in Endpoint Security
EPP and EDR, while both crucial for endpoint security, serve distinct purposes. EPP acts as a proactive shield, focusing on preventing threats from ever reaching your devices. It employs tools like antivirus, application control, and intrusion prevention to block malicious software, unauthorized programs, and suspicious network activity.
Think of EPP as your castle’s strong walls and vigilant guards. They deter attackers and make infiltration difficult. However, even the most formidable defenses can sometimes be breached. That’s where EDR comes in. EDR functions as your internal security force, constantly monitoring your devices for signs of intrusion.
If a threat manages to bypass EPP, EDR can detect its presence, investigate its origin, and take swift action to contain the damage. EDR can isolate infected devices, quarantine suspicious files, and even terminate malicious processes to prevent the attack from spreading. It also provides valuable insights to security teams, helping them identify the root cause of the breach and patch vulnerabilities to prevent future attacks.
In essence, EPP focuses on prevention, while EDR excels at detection and response. By working together, they create a layered security approach, significantly bolstering your defenses against cyber threats.
Choosing the Right Endpoint Protection Platform (EPP)
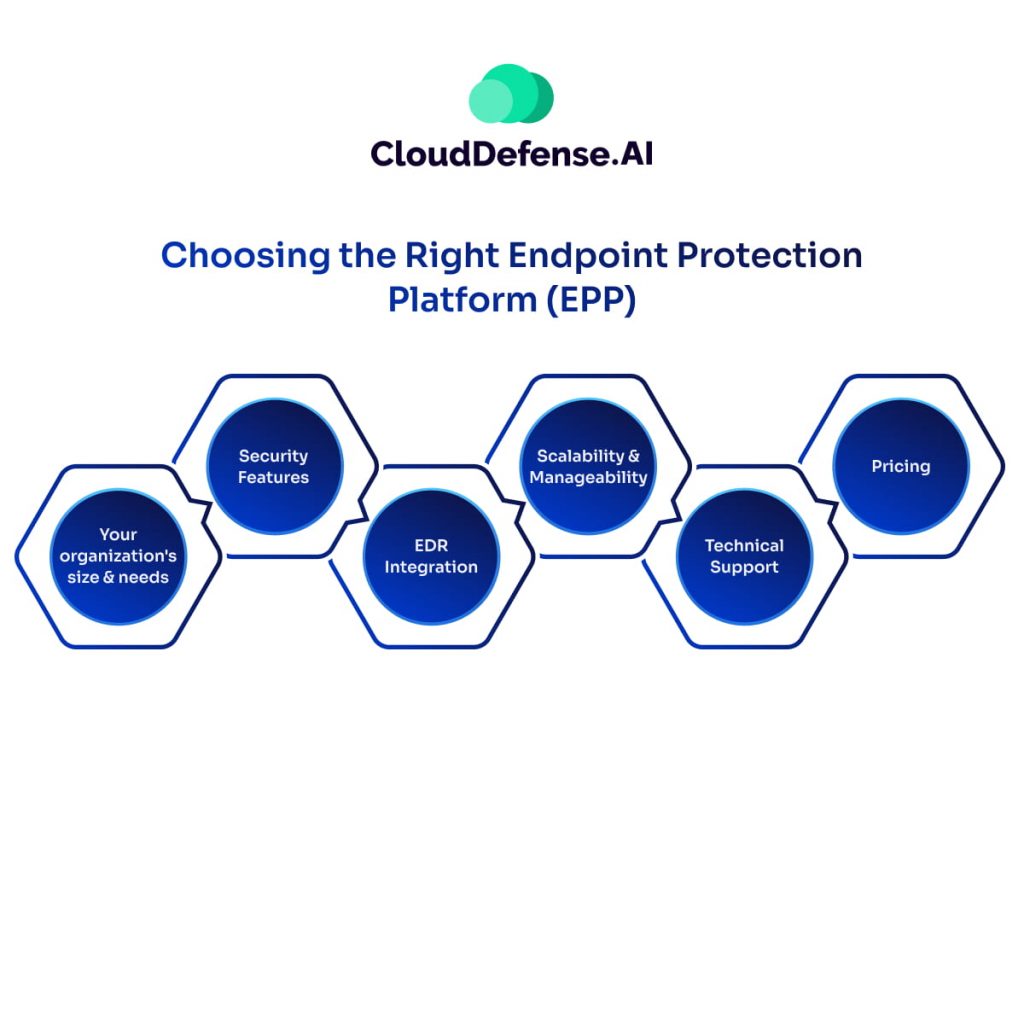
Selecting the ideal EPP for your needs requires careful consideration. Here are some key factors to evaluate:
- Your organization’s size and needs—Consider the number and types of devices you need to protect. Do you have a mix of desktops, laptops, tablets, and mobile devices? The size of your organization will also influence your budget and feature requirements.
- Security Features—Prioritize features that align with your security needs. Look for EPPs with robust NGAV, application control, web filtering, and device control capabilities. Consider features like Data Loss Prevention (DLP) if handling sensitive data is a concern.
- EDR Integration—While not all EPPs have built-in EDR functionalities, having EDR capabilities can be a valuable asset. EDP allows for deeper investigation and faster response to security incidents.
- Scalability and Manageability—If you manage a large number of devices, choose an EPP with a centralized management console for easy deployment, policy enforcement, and security monitoring across all endpoints.
- Technical Support—Reliable technical support is crucial for any security solution. Evaluate the vendor’s support options, response times, and expertise to ensure you have access to help when needed.
- Pricing—EPP pricing models can vary. Consider features offered, number of devices supported, and any additional costs like per-user licensing or subscription fees.
Beyond these factors, explore these additional tips:
- Read user reviews and industry reports—Gain insights from real-world experiences and expert opinions.
- Free trials—Many vendors offer free trials, allowing you to test-drive the EPP and assess its suitability for your environment.
- Ongoing support—Evaluate the level of support offered by the vendor. Reliable and responsive support is crucial for timely assistance with any security issues.
Final Words
Don’t let your devices be the open door for a cyber invasion. Traditional defenses are struggling against evolving threats. EPPs offer a last line of defense, safeguarding your data and systems from malware, phishing, and more. But time is running out! Cybercriminals are relentless, and the consequences of a successful breach could be catastrophic – from crippling downtime and compliance violations to reputational ruin and financial devastation. The time to act is now before it’s too late.
While this article focused on Endpoint Protection Platforms, CloudDefense.ai recognizes the ever-evolving threat landscape and the need for comprehensive security solutions. We are a frontrunner in cloud and application security, offering cutting-edge solutions to safeguard your applications and data in the cloud. Book a free demo with CloudDefense.AI today and see how we can help you build a stronger security posture for your organization.







